Configure an NGFW Cluster
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
PAN-OS 11.1 & Later
- PAN-OS 11.1 & Later
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- Cloud Management of NGFWs
-
- Management Interfaces
-
- Launch the Web Interface
- Use the Administrator Login Activity Indicators to Detect Account Misuse
- Manage and Monitor Administrative Tasks
- Commit, Validate, and Preview Firewall Configuration Changes
- Commit Selective Configuration Changes
- Export Configuration Table Data
- Use Global Find to Search the Firewall or Panorama Management Server
- Manage Locks for Restricting Configuration Changes
-
-
- Define Access to the Web Interface Tabs
- Provide Granular Access to the Monitor Tab
- Provide Granular Access to the Policy Tab
- Provide Granular Access to the Objects Tab
- Provide Granular Access to the Network Tab
- Provide Granular Access to the Device Tab
- Define User Privacy Settings in the Admin Role Profile
- Restrict Administrator Access to Commit and Validate Functions
- Provide Granular Access to Global Settings
- Provide Granular Access to the Panorama Tab
- Provide Granular Access to Operations Settings
- Panorama Web Interface Access Privileges
-
- Reset the Firewall to Factory Default Settings
-
- Plan Your Authentication Deployment
- Pre-Logon for SAML Authentication
- Configure SAML Authentication
- Configure Kerberos Single Sign-On
- Configure Kerberos Server Authentication
- Configure TACACS+ Authentication
- Configure TACACS Accounting
- Configure RADIUS Authentication
- Configure LDAP Authentication
- Configure Local Database Authentication
- Configure an Authentication Profile and Sequence
- Test Authentication Server Connectivity
- Troubleshoot Authentication Issues
-
- Keys and Certificates
- Default Trusted Certificate Authorities (CAs)
- Certificate Deployment
- Configure the Master Key
- Export a Certificate and Private Key
- Configure a Certificate Profile
- Configure an SSL/TLS Service Profile
- Configure an SSH Service Profile
- Replace the Certificate for Inbound Management Traffic
- Configure the Key Size for SSL Forward Proxy Server Certificates
-
- HA Overview
-
- Prerequisites for Active/Active HA
- Configure Active/Active HA
-
- Use Case: Configure Active/Active HA with Route-Based Redundancy
- Use Case: Configure Active/Active HA with Floating IP Addresses
- Use Case: Configure Active/Active HA with ARP Load-Sharing
- Use Case: Configure Active/Active HA with Floating IP Address Bound to Active-Primary Firewall
- Use Case: Configure Active/Active HA with Source DIPP NAT Using Floating IP Addresses
- Use Case: Configure Separate Source NAT IP Address Pools for Active/Active HA Firewalls
- Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT
- Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT in Layer 3
- HA Clustering Overview
- HA Clustering Best Practices and Provisioning
- Configure HA Clustering
- Refresh HA1 SSH Keys and Configure Key Options
- HA Firewall States
- Reference: HA Synchronization
-
- Use the Dashboard
- Monitor Applications and Threats
- Monitor Block List
-
- Report Types
- View Reports
- Configure the Expiration Period and Run Time for Reports
- Disable Predefined Reports
- Custom Reports
- Generate Custom Reports
- Generate the SaaS Application Usage Report
- Manage PDF Summary Reports
- Generate User/Group Activity Reports
- Manage Report Groups
- Schedule Reports for Email Delivery
- Manage Report Storage Capacity
- View Policy Rule Usage
- Use External Services for Monitoring
- Configure Log Forwarding
- Configure Email Alerts
-
- Configure Syslog Monitoring
-
- Traffic Log Fields
- Threat Log Fields
- URL Filtering Log Fields
- Data Filtering Log Fields
- HIP Match Log Fields
- GlobalProtect Log Fields
- IP-Tag Log Fields
- User-ID Log Fields
- Decryption Log Fields
- Tunnel Inspection Log Fields
- SCTP Log Fields
- Authentication Log Fields
- Config Log Fields
- System Log Fields
- Correlated Events Log Fields
- GTP Log Fields
- Audit Log Fields
- Syslog Severity
- Custom Log/Event Format
- Escape Sequences
- Forward Logs to an HTTP/S Destination
- Firewall Interface Identifiers in SNMP Managers and NetFlow Collectors
- Monitor Transceivers
-
- User-ID Overview
- Enable User-ID
- Map Users to Groups
- Enable User- and Group-Based Policy
- Enable Policy for Users with Multiple Accounts
- Verify the User-ID Configuration
-
- App-ID Overview
- App-ID and HTTP/2 Inspection
- Manage Custom or Unknown Applications
- Safely Enable Applications on Default Ports
- Applications with Implicit Support
-
- Prepare to Deploy App-ID Cloud Engine
- Enable or Disable the App-ID Cloud Engine
- App-ID Cloud Engine Processing and Policy Usage
- New App Viewer (Policy Optimizer)
- Add Apps to an Application Filter with Policy Optimizer
- Add Apps to an Application Group with Policy Optimizer
- Add Apps Directly to a Rule with Policy Optimizer
- Replace an RMA Firewall (ACE)
- Impact of License Expiration or Disabling ACE
- Commit Failure Due to Cloud Content Rollback
- Troubleshoot App-ID Cloud Engine
- Application Level Gateways
- Disable the SIP Application-level Gateway (ALG)
- Maintain Custom Timeouts for Data Center Applications
-
- Decryption Overview
-
- Keys and Certificates for Decryption Policies
- SSL Forward Proxy
- SSL Forward Proxy Decryption Profile
- SSL Inbound Inspection
- SSL Inbound Inspection Decryption Profile
- SSL Protocol Settings Decryption Profile
- SSH Proxy
- SSH Proxy Decryption Profile
- Profile for No Decryption
- SSL Decryption for Elliptical Curve Cryptography (ECC) Certificates
- Perfect Forward Secrecy (PFS) Support for SSL Decryption
- SSL Decryption and Subject Alternative Names (SANs)
- TLSv1.3 Decryption
- High Availability Not Supported for Decrypted Sessions
- Decryption Mirroring
- Configure SSL Forward Proxy
- Configure SSL Inbound Inspection
- Configure SSH Proxy
- Configure Server Certificate Verification for Undecrypted Traffic
- Post-Quantum Cryptography Detection and Control
- Enable Users to Opt Out of SSL Decryption
- Temporarily Disable SSL Decryption
- Configure Decryption Port Mirroring
- Verify Decryption
- Activate Free Licenses for Decryption Features
-
- Policy Types
- Policy Objects
- Track Rules Within a Rulebase
- Enforce Policy Rule Description, Tag, and Audit Comment
- Move or Clone a Policy Rule or Object to a Different Virtual System
-
- External Dynamic List
- Built-in External Dynamic Lists
- Configure the Firewall to Access an External Dynamic List
- Retrieve an External Dynamic List from the Web Server
- View External Dynamic List Entries
- Exclude Entries from an External Dynamic List
- Enforce Policy on an External Dynamic List
- Find External Dynamic Lists That Failed Authentication
- Disable Authentication for an External Dynamic List
- Register IP Addresses and Tags Dynamically
- Use Dynamic User Groups in Policy
- Use Auto-Tagging to Automate Security Actions
- CLI Commands for Dynamic IP Addresses and Tags
- Application Override Policy
- Test Policy Rules
-
- Network Segmentation Using Zones
- How Do Zones Protect the Network?
-
PAN-OS 11.1 & Later
- PAN-OS 11.1 & Later
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
-
- Tap Interfaces
-
- Layer 2 and Layer 3 Packets over a Virtual Wire
- Port Speeds of Virtual Wire Interfaces
- LLDP over a Virtual Wire
- Aggregated Interfaces for a Virtual Wire
- Virtual Wire Support of High Availability
- Zone Protection for a Virtual Wire Interface
- VLAN-Tagged Traffic
- Virtual Wire Subinterfaces
- Configure Virtual Wires
- Configure a PPPoE Client on a Subinterface
- Configure an IPv6 PPPoE Client
- Configure an Aggregate Interface Group
- Configure Bonjour Reflector for Network Segmentation
- Use Interface Management Profiles to Restrict Access
-
- DHCP Overview
- Firewall as a DHCP Server and Client
- Firewall as a DHCPv6 Client
- DHCP Messages
- Dynamic IPv6 Addressing on the Management Interface
- Configure an Interface as a DHCP Server
- Configure an Interface as a DHCPv4 Client
- Configure an Interface as a DHCPv6 Client with Prefix Delegation
- Configure the Management Interface as a DHCP Client
- Configure the Management Interface for Dynamic IPv6 Address Assignment
- Configure an Interface as a DHCP Relay Agent
-
- DNS Overview
- DNS Proxy Object
- DNS Server Profile
- Multi-Tenant DNS Deployments
- Configure a DNS Proxy Object
- Configure a DNS Server Profile
- Use Case 1: Firewall Requires DNS Resolution
- Use Case 2: ISP Tenant Uses DNS Proxy to Handle DNS Resolution for Security Policies, Reporting, and Services within its Virtual System
- Use Case 3: Firewall Acts as DNS Proxy Between Client and Server
- DNS Proxy Rule and FQDN Matching
-
- NAT Rule Capacities
- Dynamic IP and Port NAT Oversubscription
- Dataplane NAT Memory Statistics
-
- Translate Internal Client IP Addresses to Your Public IP Address (Source DIPP NAT)
- Create a Source NAT Rule with Persistent DIPP
- PAN-OS
- Strata Cloud Manager
- Enable Clients on the Internal Network to Access your Public Servers (Destination U-Turn NAT)
- Enable Bi-Directional Address Translation for Your Public-Facing Servers (Static Source NAT)
- Configure Destination NAT with DNS Rewrite
- Configure Destination NAT Using Dynamic IP Addresses
- Modify the Oversubscription Rate for DIPP NAT
- Reserve Dynamic IP NAT Addresses
- Disable NAT for a Specific Host or Interface
-
- Network Packet Broker Overview
- How Network Packet Broker Works
- Prepare to Deploy Network Packet Broker
- Configure Transparent Bridge Security Chains
- Configure Routed Layer 3 Security Chains
- Network Packet Broker HA Support
- User Interface Changes for Network Packet Broker
- Limitations of Network Packet Broker
- Troubleshoot Network Packet Broker
-
- Enable Advanced Routing
- Logical Router Overview
- Configure a Logical Router
- Create a Static Route
- Configure BGP on an Advanced Routing Engine
- Create BGP Routing Profiles
- Create Filters for the Advanced Routing Engine
- Configure OSPFv2 on an Advanced Routing Engine
- Create OSPF Routing Profiles
- Configure OSPFv3 on an Advanced Routing Engine
- Create OSPFv3 Routing Profiles
- Configure RIPv2 on an Advanced Routing Engine
- Create RIPv2 Routing Profiles
- Create BFD Profiles
- Configure IPv4 Multicast
- Configure MSDP
- Create Multicast Routing Profiles
- Create an IPv4 MRoute
-
-
PAN-OS 11.2
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
- Cloud Management and AIOps for NGFW
Configure an NGFW Cluster
Configure an NGFW cluster of two PA-7500 Series firewalls for node
redundancy.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following:
|
Before you configure an NGFW cluster, perform the following prerequisites:
- Confirm that Panorama and the PA-7500 Series firewalls that you will assign to an NGFW cluster are all running the same software version (PAN-OS 11.1.3 or a later 11.1 release).
- Install Panorama Clustering plugin 2.0.0 if you're using PAN-OS 11.1.3; refer to Install Panorama Plugins. For subsequent PAN-OS releases, you must install a compatible Panorama Clustering plugin release. Also refer to the Panorama plugin for Clustering in the VM-Series and Panorama Plugin Release Notes.
- Be familiar with Panorama tasks, such as managing devices and creating templates, template stacks, and device groups.
- Add the two PA-7500 Series firewalls as managed devices of Panorama so that they are communicating with each other over the management interface. Confirm by selecting PanoramaManaged DevicesSummary, and verify the two firewalls (nodes) have an IP address on their management interface and the Device State is Connected.
- Connect the PA-7500 Series firewalls back-to-back with 100G or 400G HSCI-A and HSCI-B links. (Verify the connections on each firewall by using the CLI command show interface all to see the hsci-a and hsci-b interfaces.)
- Familiarize yourself with NGFW Clusters.
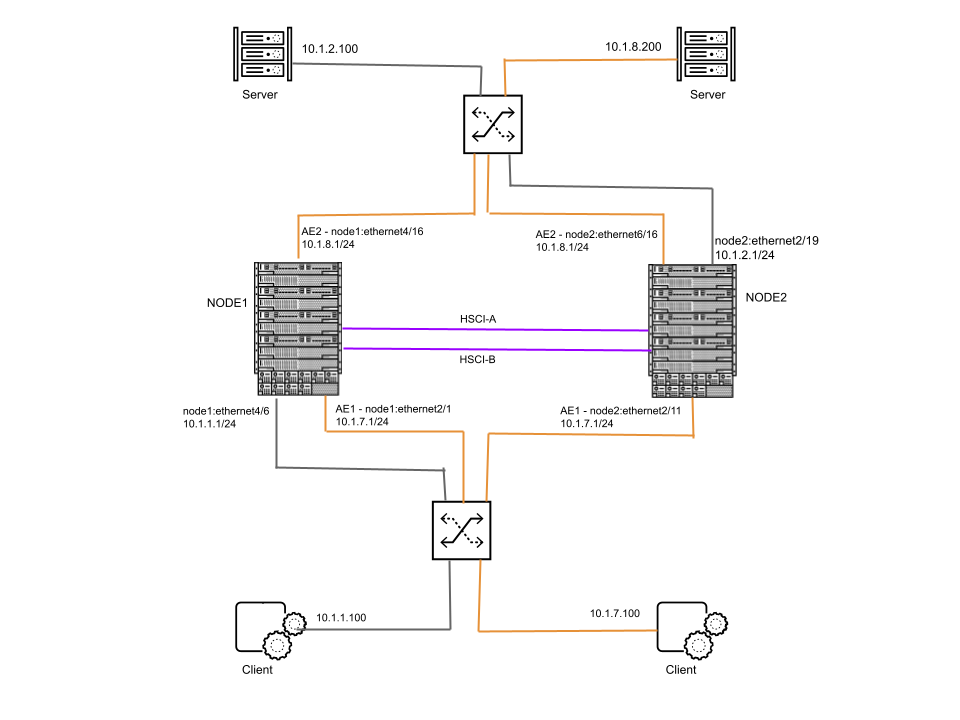
The steps in the example task to configure an NGFW cluster are based on this topology
example of two MC-LAGs. The orange links connected to Node 1 and Node 2 on the
client side belong to AE1 (an MC-LAG). The orange links connected to Node 1 and Node
2 on the server side belong to AE2 (another MC-LAG). Traffic from the client at
10.1.7.100 goes to the switch and is then divided between the two ingress AE1
interfaces and then egresses the two AE2 interfaces to the switch, and then goes
over the orange link to the server at 10.1.8.200.
The gray links connected Node 1 and Node 2 are orphan ports. Traffic from the client
at 10.1.1.100 goes to the switch, to Node 1, across an HSCI interface to Node 2,
egresses Node 2 to the switch, and then to the server at 10.1.2.100.
- Create an NGFW cluster.
- Select PanoramaFirewall ClustersCreate Cluster.
- Enter a Cluster Name containing zero or more alphanumeric characters, underscores (_), hyphens (-), dots (.), or spaces.
- Select Cluster Type as PA.
- Click OK.
- Add the firewalls to the cluster.
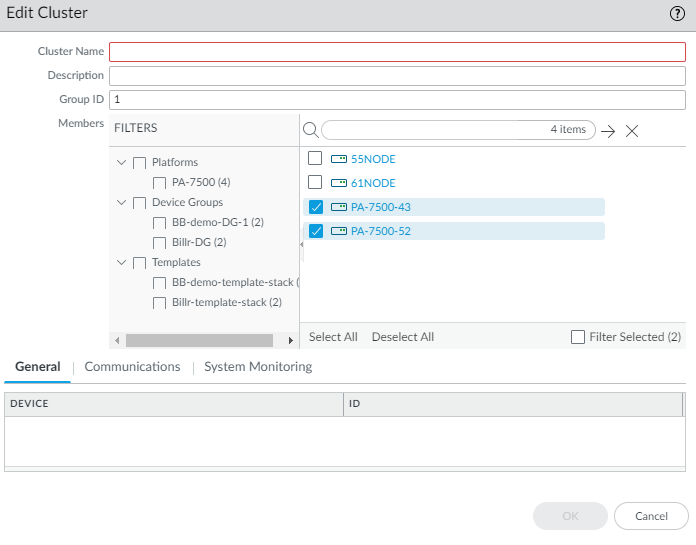
- Select PanoramaFirewall ClustersSummary View and select the cluster you created.
- Enter a Group ID in the range 1 to 63; the default is 1.
- Select the two PA-7500 Series firewalls to assign to the cluster. The first firewall you select automatically becomes Node 1.

- Click OK.
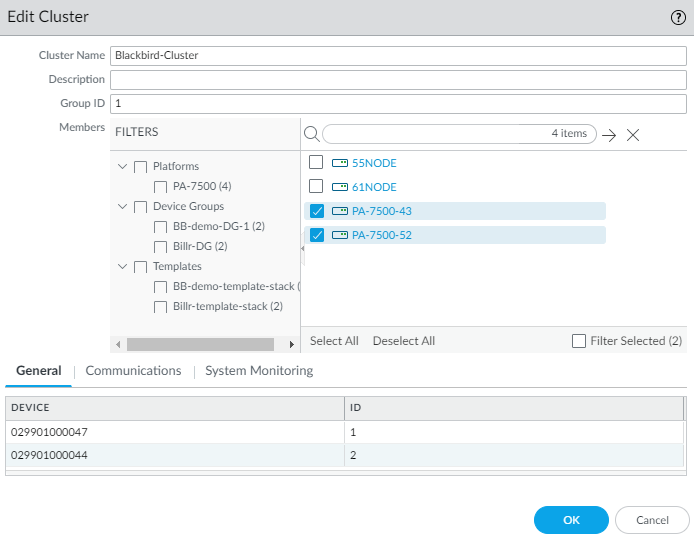
- View the firewalls in the cluster by selecting PanoramaFirewall ClustersSummary View and selecting the cluster you created. The General tab displays nonconfigurable fields: Device serial number and Node ID (1 or 2). Click OK to close the window.

- Select Commit to Panorama and Commit. Both firewalls are rebooted and get assigned a Node ID, the existing configuration (policy, network, etc.) is cleared, and the firewalls are connected back to Panorama.
- Select Push to Devices, select Push All Changes, select the newly created firewall cluster, and Push.
- (Optional) Verify the cluster state and node state.
- > show cluster leader
- > show cluster local node-id
- > show cluster local state
- > show cluster all
- > exit
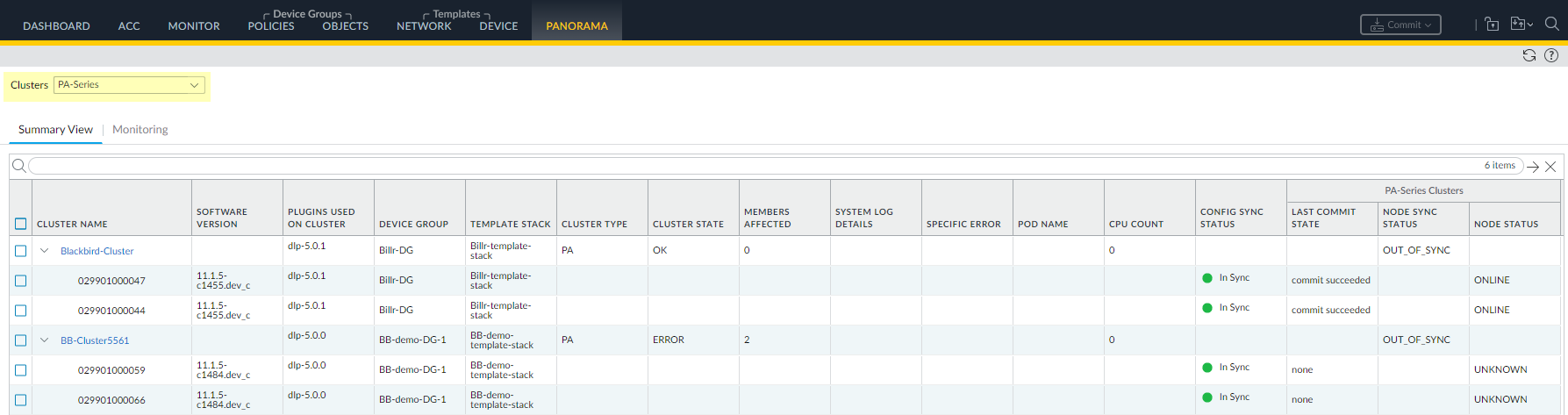
- View the Config Sync Status.
- Select PanoramaFirewall ClustersSummary View and select PA-Series.
- View the Config Sync Status. After the Commit All is successful, the firewalls have a Config Sync Status of In Sync.

- Add a cluster template.
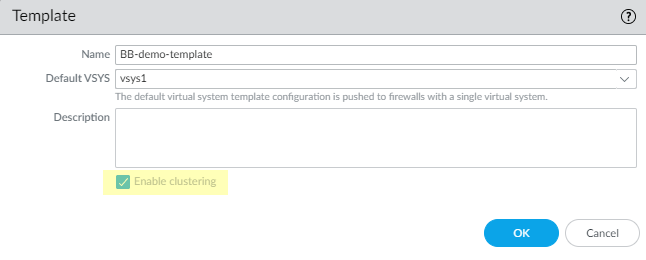
- Select PanoramaTemplates and Add a template.
- Enter a Name and Description of the template.
- Enable clustering. You must enable clustering when you first create the template; you can't go back to enable clustering later.
- Click OK.

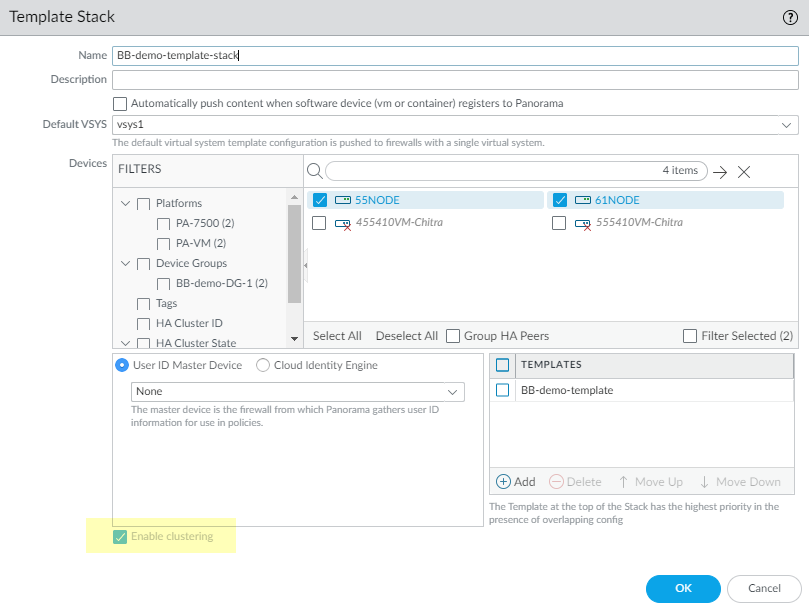
- Create a template stack.
- Select PanoramaTemplatesAdd Stack.
- Enter a Name for the template stack.
- In the Devices section, select the two firewalls in the cluster.
- In the Templates section, Add the template you created.
- Enable clustering. You must enable clustering when you first create the template stack; you can't go back to enable clustering later. (If you don't Enable clustering for the template stack now, it won't match the template and an Operation Failed message appears.)
- Click OK.

- Add a device group.
- Select PanoramaDevice GroupsAdd.
- Enter a Name for the device group.
- In the Devices section, select the Names of the two firewalls in the cluster.
- In the Reference Templates section, Add the template stack that you created.
- Click OK.
- Commit to Panorama and Commit to apply your configuration in Panorama.
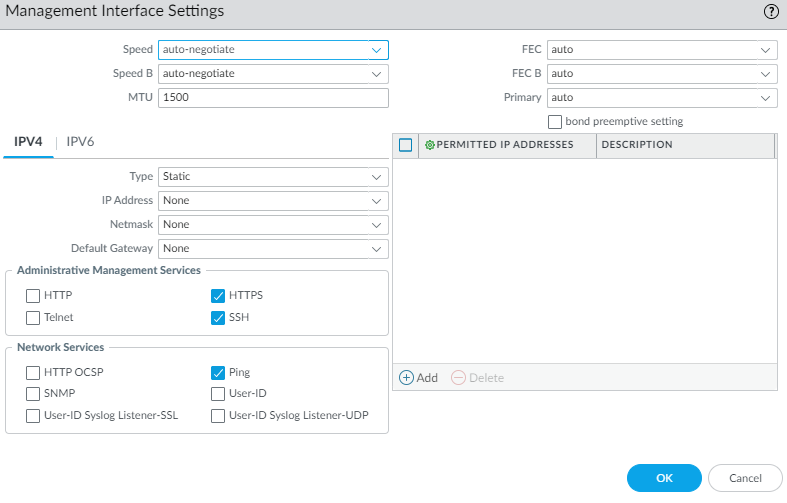
- (Two-node cluster only) Verify that the management interface permits the same IP addresses on the two nodes. The firewalls use the management interface to exchange heartbeats to detect and avoid a split-brain situation.
- Select DeviceSetupInterfaces.
- In the Template field, select your template.
- Select the Management interface.
- If you added Permitted IP Addresses on one of the nodes, you must also permit the same IP addresses on the peer node. Each node must be able to reach the management interface of the peer node. (If you deny the IP address or network of the peer, split brain detection won't work.)
- Click OK.

- Configure the template.
- Select Network
- In the Template field, select your template.
- To configure the orphan port, configure a Layer 3 interface on the firewall that connects to the client.
- Select NetworkInterfacesCluster Ethernet and Add Interface.
- Select the Node ID (1 for this example).
- Select the Slot (Slot 4).
- Select the Interface Name, for example, node1:ethernet4/6.
- Select the Interface Type as Layer3.
- On the Config tab, create a Logical Router by adding a Name; click OK.
- Create a Security Zone, such as client.
- Select IPv4, select the Type as Static, for example, and Add the IPv4 address with netmask (10.1.1.1/24 in this example).Alternatively, select IPv6, Enable IPv6 on the interface, select the Type as Static, and Add the IPv6 Address with network prefix length. This task example uses static IP addressing; NGFW clustering also supports DHCP, DHCPv6, PPPoE, and PPPoEv6.
- Select the Advanced tab and then the Other Info tab.
- For Management Profile, create a new Interface Management profile to allow access to the interface. Select the management and network services allowed (such as HTTPS, SSH, and Ping) and click OK.
- Click OK.
- Configure the other orphan port on node 2, Slot 2, node2:ethernet2/19, using IP address 10.1.2.1/24 for the interface that faces the server. Create a different security zone. The gray path in the example topology is configured.
- Configure the AE interface (MC-LAG) for the client-facing interface on Node 1.
- Select NetworkInterfacesCluster Ethernet and Add Aggregate Group.
- For Interface Name, next to ae, enter the interface number (in this example, 1).
- Select Interface Type as Layer3.
- On the Config tab, select the same Logical Router.
- Select the Security Zone.
- Click OK.
- Select IPv4, select the Type as Static, and Add the IPv4 address with netmask (10.1.7.1/24 in this example).
- (Optional) Configure LACP settings if you want to enable LACP for the aggregate group.
- Select the Advanced tab and then the Other Info tab.
- For Management Profile, create a new Interface Management profile to allow access to the interface. Select the services allowed and click OK.
- Click OK.
- Configure the AE interface (MC-LAG) for the server-facing interface for Node 1. For this interface, follow similar substeps as in the prior step, but configure AE2, add the IP address (10.1.8.1/24), the same logical router, and a server Security zone.
- Add an interface member to the MC-LAG on the client side.
- Select NetworkInterfacesCluster Ethernet and Add Interface.
- On the Cluster Ethernet Interface, select the Node ID Node 1.
- Select the Slot (Slot 2).
- Select the Interface Name, for example, node1:ethernet2/1.
- Select the Interface Type as Aggregate Ethernet.
- Select the Aggregate Group, such as ae1.
- Click OK.
- Add a second interface member to the MC-LAG on the client side, assigning Node ID as Node 2, Slot 2, node2:ethernet2/11. Select the same Aggregate Group (ae1).
- Add an interface member to the MC-LAG on the server side. Select Node 1, Slot 4, node1:ethernet4/16. Select the Aggregate Group, ae2.
- Add a second interface member to the MC-LAG on the server side, assigning it to Node 2, Slot 6, node2:ethernet6/16. Select the Aggregate Group, such as ae2.
- (PAN-OS 11.1.5 and later releases) Prepare to configure MACsec for the HSCI ports by creating a MACsec profile.IMPORTANT: When you migrate from a non-MACsec cluster to a MACsec cluster, you must do so during a maintenance window.
- Select NetworkNetwork ProfilesMACsec Profile and select MACsec Policy.
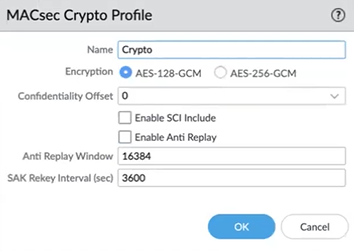
- Add a MACsec crypto profile by Name, which contains zero or more alphanumeric characters, underscores (_), hyphens (-), or dots (.). The Name is a maximum of 31 characters.
- Select the Encryption type: AES-128-GCM (default) or AES-256-GCM.
- Select the Confidentiality Offset to specify a number of bytes (starting from the frame header), after which MACsec encrypts the bytes in a frame. Values are 0 (default), 30, or 50.
- Enable SCI Include to include the Secure Channel Identifier (SCI) tag in the Security Tag field of the MACsec header. The default is disabled.
- Enable Anti Replay to enable replay protection. This allows a MACsec port to accept frames out of order if they are within the Anti Replay Window. The default is disabled.
- Specify the Anti Replay Window size in the range 0 to 65,535; the default is 16,384. This value determines the range of packet numbers that the port will accept, for packets that might be out of order. The port will accept packets with a packet number greater than or equal to the last packet number minus the window size. For example, after the port receives packet number 12, if the window is 5, the port will subsequently accept only packets numbered 7 or higher.Specify an Anti Replay window size based on the traffic rate because the HSCI ports will likely experience packets arriving out of order due to prioritization or load balancing in the network.
- Specify the SAK Rekey Interval (sec) in seconds; range is 60 to 86,400; default is 3,600. Connectivity Association participants negotiate a Secure Association agreement, which includes a cipher suite and keys. A Key Server generates a Secure Association Key (SAK) from the Connectivity Association Key (CAK); the SAK is refreshed at the SAK rekey interval. The end-to-end nodes use the SAK to encrypt traffic for a given session. To avoid the SAKs of all interfaces being refreshed at the same time, MACsec might spread the rekeying actions evenly by subtracting a small random number from the SAK rekey interval.
- Click OK.

- (PAN-OS 11.1.5 and later releases) Create a MACsec Pre Shared Key Profile.
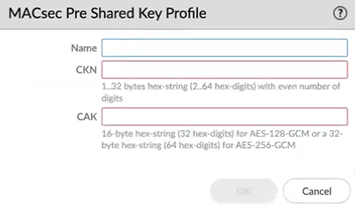
- Select NetworkNetwork ProfilesMACsec Profile and select Pre Shared Key.
- Add a MACsec Pre Shared Key Profile by Name, which contains zero or more alphanumeric characters, underscores (_), hyphens (-), dots (.), or spaces. The Name is a maximum of 31 characters.
- Enter the CKN (Connectivity Association Key Name) that identifies the Connectivity Association Key. The CKN is 1 byte to 32 bytes of hexadecimal string (2 to 64 hex digits) with an even number of digits; for example, 1234.
- Enter the CAK (Connectivity Association Key), which is a 16-byte hexadecimal string (32 hex digits) for AES-128-GCM, or a 32-byte hexadecimal string (64 hex digits) for AES-256-GCM. The CAK is used to generate all other keys used for MACsec. An example CAK for AES-128-GCM is 12345678912345678912345678912345. A CAK for AES-256-GCM is twice as long as a CAK for AES-128-GCM.The Pre Shared Key, CKN, and CAK must match on the two ends of the HSCI-A link. Likewise, the Pre Shared Key, CKN, and CAK must match on the two ends of the HSCI-B link.
- Click OK.

- (PAN-OS 11.1.5 and later releases) Commit to Panorama.
- (PAN-OS 11.1.5 and later releases) Push to Devices and Push Templates so that the devices have the MACsec profiles, thus allowing you to later push the cluster configuration with MACsec enabled.
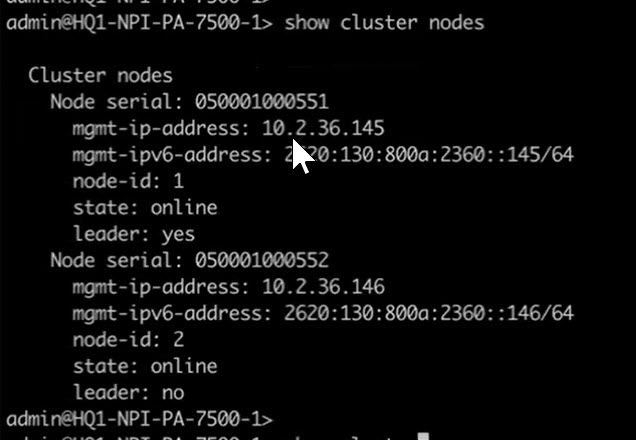
- (PAN-OS 11.1.5 and later releases) Identify the leader node and nonleader node.
- Access the CLI on one of the firewall nodes. (If you already know which node is the nonleader, access the CLI on the nonleader node.)
- >show cluster nodes

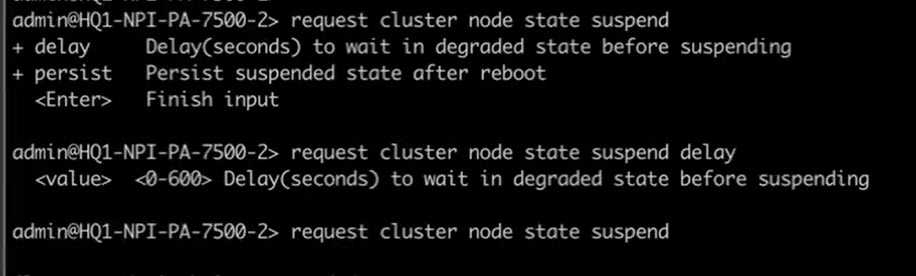
- (PAN-OS 11.1.5 and later releases) Suspend the nonleader node.
- Access the CLI on the nonleader node.
- >request cluster node state suspendThe suspension takes approximately 120 seconds (the default delay value).

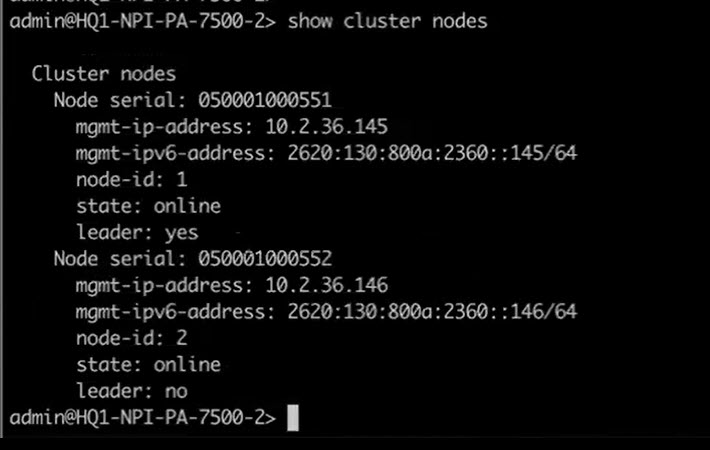
- (PAN-OS 11.1.5 and later releases) Confirm the nonleader node is suspended.
- >show cluster nodes

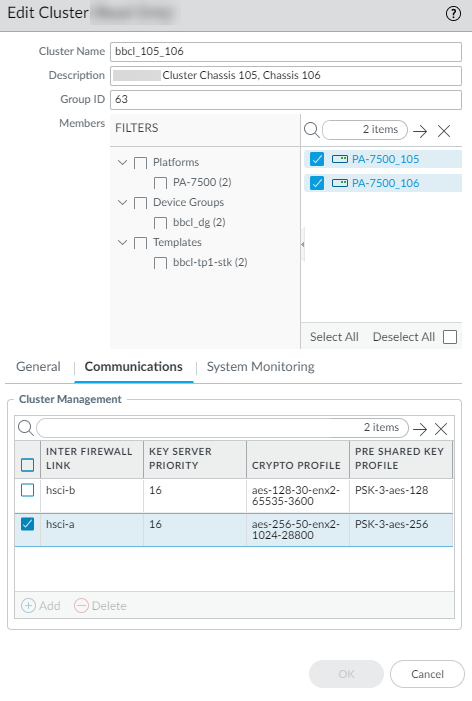
- (PAN-OS 11.1.5 and later releases) Apply your MACsec profiles to the HSCI-A and HSCI-B ports.
- Select PanoramaFirewall Clusters and select Summary View.
- Select PA-Series or All Clusters.
- Select a Cluster Name to edit the cluster.
- Select Communications.
- Select hsci-a and enter the Key Server Priority in the range from 0 to 255; the default is 16. The lower the value, the higher the priority of the Key Server.If the priority values for the HSCI-A links on the two nodes are equal, the node with the lower MAC address is the Key Server. The Key Server (one of the nodes in the cluster) selects and advertises a cipher suite, and also generates the SAK from the CAK.
- For Crypto Profile, select the MACsec crypto profile you created or select the default profile.
- For Pre Shared Key Profile, select the profile you created.
- Select hsci-b and perform the same steps to assign a Key Server Priority and apply the crypto profile and pre-shared key Profile to the port.
- Click OK.

- (PAN-OS 11.1.5 and later releases) Commit, Commit to Panorama, and Commit.
- (PAN-OS 11.1.5 and later releases) Push to Devices and Push , which enables MACsec on the ports.
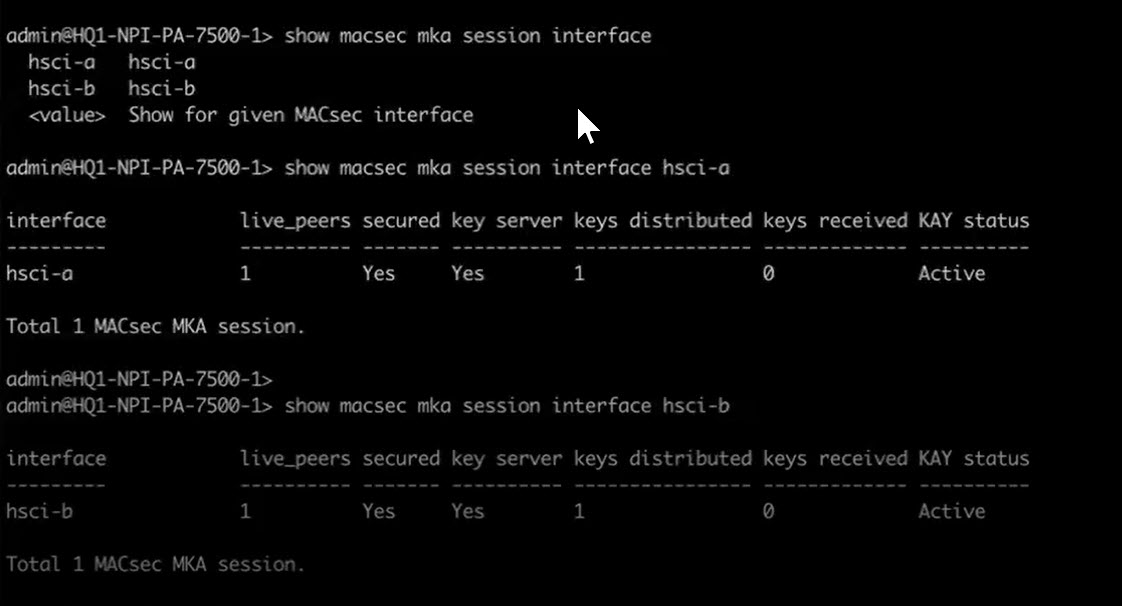
- (PAN-OS 11.1.5 and later releases) Confirm MACsec is enabled on both ports.
- >show macsec mka session interface hsci-a
- >show macsec mka session interface hsci-b

- (PAN-OS 11.1.5 and later releases) Unsuspend the nonleader node.
- Access the CLI on the nonleader node.
- >request cluster node state unsuspendIt takes a few minutes to unsuspend the nonleader node; the length of time depends on the traffic level.
- (PAN-OS 11.1.5 and later releases) Verify that both nodes are online.
- >show cluster nodes

- (PAN-OS 11.1.7 and later releases) (Optional) Enable multiple virtual systems for the firewalls in the template.
- Select DeviceVirtual Systems and select the Template by name.
- For Mode, select Multi VSYS.
- Create Security policy rules.
- Select Policies and select the Device Group.
- Create Security policy rules to control access, such as allowing a specific source zone, destination zone, address, user, device, application, and service.
- Configure routing and other features your firewalls require (except for HA). Refer to the PAN-OS Administrator's Guide and the PAN-OS Networking Administrator's Guide.
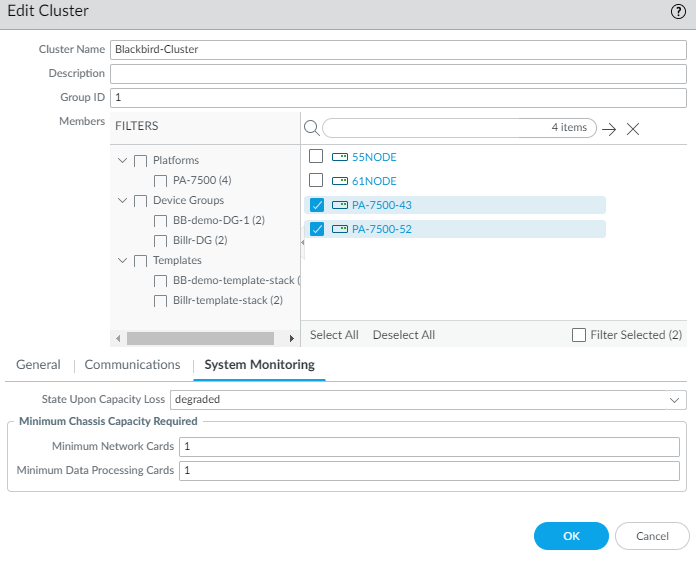
- Configure system monitoring for the NGFW cluster.
- Select PanoramaFirewall ClustersSummary View and select a cluster or a single firewall in the cluster.
- Select System Monitoring.

- Select the State Upon Capacity Loss:
- degraded—Specifies that the firewall will
be in a DEGRADED state if the count of functional network cards
or data processing cards goes below the configured Minimum
Network Cards or Minimum Data Processing Cards, respectively.
Furthermore:
- A cluster node in DEGRADED state has traffic ports down, but is still a part of the sharded (fragmented) member table.
- Data processing card resources of a DEGRADED cluster node can be used to process traffic and for Layer 7 processing.
- A cluster node in INIT or ONLINE state transitions to DEGRADED state when a soft fault is reported to the cluster node state machine.
- A cluster node in ONLINE state transitions to DEGRADED state (and a node in DEGRADED state remains in DEGRADED state) if you suspend the cluster node after a delay (using the CLI operational command: request cluster node state suspend). A delay allows data planes to gracefully complete Layer 7 processing or other processes that were underway.
- If all soft faults are cleared, the cluster node transitions to INIT state.
- If a hard fault occurs, a cluster node in DEGRADED state transitions to FAILED state.
- A cluster node in DEGRADED state transitions to SUSPENDED state if the maximum number of state flaps is seen or you suspend the cluster node.
- If a chassis has no functional data processing cards remaining (all DPC slots are powered off or in a FAILED state), the cluster node state will be FAILED, even if you configured degraded, because having no functional DPC is a hard fault.
- failed—Specifies that the firewall will
be in a FAILED state if the count of functional network cards or
data processing cards goes below the configured Minimum Network
Cards or Minimum Data Processing Cards, respectively.
Furthermore:
- A cluster node in FAILED state has traffic ports down and isn't part of the sharded member table.
- Data processing card resources of a FAILED cluster node can't be used to process traffic or for Layer 7 processing.
- A cluster node in INIT, ONLINE, or DEGRADED state transitions to FAILED state when a hard fault is reported to the cluster node state machine.
- A cluster node in FAILED state transitions to INIT state if all hard faults are cleared.
- A cluster node in FAILED state transitions to SUSPENDED state if the maximum number of state flaps is seen or you suspend the cluster node.
NGFW Clusters provides a list of hard faults and soft faults. - degraded—Specifies that the firewall will
be in a DEGRADED state if the count of functional network cards
or data processing cards goes below the configured Minimum
Network Cards or Minimum Data Processing Cards, respectively.
Furthermore:
- In the Minimum Chassis Capacity Required section, enter the Minimum Network Cards required; range is 1 to 7, default is 1. When fewer Network Cards than the configured value are functional, the firewall in the cluster goes to the State Upon Capacity Loss that you configured (degraded or failed).
- Enter the Minimum Data Processing Cards required; range is 1 to 7, default is 1. When fewer Data Processing Cards than the configured value are functional, the firewall in the cluster goes to the State Upon Capacity Loss that you configured (degraded or failed).
- Click OK.
- (Optional) Configure Log Forwarding for the PA-7500 Series firewall.
- Push the configuration from Panorama to the PA-7500 Series firewalls in the cluster.
- Commit and Commit and Push and Commit.
- Commit and Push to Devices, Push All Changes, select the cluster, and Push the configuration to both nodes.
- (PAN-OS 11.1.7 and later releases) If you enabled multiple virtual systems for the Panorama device template, enable multiple virtual systems for an individual PA-7500 Series firewall.
- Log on to an individual PA-7500 Series firewall (not Panorama).
- Select DeviceSetupManagement.
- In General Settings, select Multi Virtual System Capability.
- Click OK.
- Repeat this step for the other PA-7500 Series firewall in the cluster.
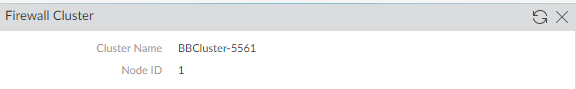
- View NGFW cluster information for an individual firewall on its Dashboard.
- Log on to an individual PA-7500 Series firewall (not Panorama).
- Select Dashboard and for Widgets, select System Firewall Cluster to view the Firewall Cluster card, which displays the Cluster Name and Node ID.

- View NGFW Cluster Summary and Monitoring information and health for the cluster.