Strata Cloud Manager
New NetSec Platform Features on Strata Cloud Manager (May 2025)
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
New NetSec Platform Features on Strata Cloud Manager (May 2025)
See all the new features made available for Strata Cloud Manager in May 2025.
These new features follow the Strata Cloud Manager release model of continuous feature deployment; as they're ready, we make them available to ensure the latest support for all products and subscriptions across the NetSec platform. There's no Strata Cloud Manager upgrade or management version requirement associated with these features; however, check if they have version or license dependencies associated with other parts of the NetSec platform (like a cloud-delivered security service subscription, or a Prisma Access version, for example).
Granular File Transfer Control in Remote Browser Isolation
|
Granular File Transfer Control in Remote Browser Isolation
May 30, 2025
|
Previously, Remote Browser Isolation (RBI) limited administrators to allowing or
blocking all downloads or all uploads during isolation, regardless of file type.
This lack of flexibility forced administrators to choose between allowing all file
transfers, which could lead to security issues, or blocking all file transfers,
which could result in usability issues and user dissatisfaction.
You can now use isolation profiles in RBI to specify the types of files users can upload or
download, enabling more granular control over data transfers during
isolated browsing sessions. The new capability helps to enhance the security posture
by reducing the attack surface and preventing various types of cybersecurity
threats. It also helps in data exfiltration by controlling which categories of file
types a user is able to upload.
Key use cases include permitting users to download only document files, blocking
downloads of executable files, or permitting transfers of only specific approved
file types. The granular controls enable you to balance security and usability by
tailoring allowed file types to your organization's needs. Configuring file type
filtering enhances your data loss prevention capabilities and provides an additional
layer of protection against potential threats introduced through file transfers.
Strata Copilot: New Region Support
|
Strata Copilot: New Region Support
May 22, 2025
|
Strata Copilot now extends its reach to new regions, enhancing global
accessibility. This expansion brings the powerful AI-driven assistance to users in
China, Qatar, and Saudi Arabia. By increasing geographical coverage, Strata Copilot
offers more organizations the opportunity to streamline their security operations,
leverage intelligent insights, and improve overall efficiency in managing their Palo
Alto Networks solutions in Strata Cloud Manager across these diverse locations.
Update:
Strata Copilot now supports the following additional regions:
- China
- Qatar
- Saudi Arabia
Customizable Prisma Access Agent Session Timeout Settings
|
Customizable Prisma Access Agent Session Timeout Settings
May 20, 2025
|
Unexpected session timeouts and inactivity logouts can significantly disrupt user
productivity and lead to increased helpdesk tickets. Prisma® Access Agent addresses
this issue by introducing configurable notifications that alert users before their
sessions expire or terminate due to inactivity. You can now set up timely warnings
and custom messages to keep your users informed and provide them with the option to
extend their sessions when needed.
You can customize sessions by setting their
duration, scheduling logout notifications, and creating custom expiration messages.
You can set the duration a user can stay logged in to a session, and also set the
amount of time to wait before the agent session ends due to user inactivity. The
ability to customize session timeouts and notifications helps balance user access
needs with network security. It enables you to control session timeouts, keep users
informed about their session status, and communicate important information.
Disable Prisma Access Agent with One-Time Password
|
Disable Prisma Access Agent with One-Time Password
May 20, 2025
|
To address the potential risks of end users disabling the Prisma® Access Agent, your
users can now use a one-time password (OTP) system to
securely disable the agent. With the OTP system, Prisma Access Agent can generate
unique, single-use codes for agent disabling, enhancing security and administrative
control. You can configure the OTP system on a per-user or per-user group basis,
providing granular control over who can disable agents and when. When users enter
the correct OTP, the agent verifies it locally and disables itself, ensuring
functionality even in offline scenarios. This feature also improves auditing
capabilities by logging all OTP-related activities, helping you track and monitor
agent disabling events across your network. By implementing this OTP system, you can
meet compliance requirements, align with industry standards, and provide a more
secure and flexible solution for managing Prisma Access Agents.
IPv6 Sinkholing for Prisma Access Agent
|
IPv6 SInkholing for Prisma Access Agent
May 20, 2025
|
While the Prisma® Access Agent routes mobile user IPv4 traffic through a protected
tunnel to Prisma Access, IPv6 traffic is conventionally sent to the local network
adapter on an endpoint. Prisma Access offers the ability to enhance security for
dual-stack endpoints by sinkholing IPv6 traffic.
By enabling IPv6 sinkholing, you can
effectively mitigate risks associated with IPv6-based threats, thus reducing your
overall attack surface. This feature is valuable in scenarios where you need to
maintain a secure environment for mobile users accessing the internet. As endpoints
can automatically fall back to IPv4 addresses, you can ensure a continuous and
protected user experience without compromising on security. By implementing this
capability, you strike an optimal balance between robust threat prevention and
uninterrupted connectivity for your mobile workforce.
LDAP Support for Prisma Access Agent
|
Granular File Transfer Control in Remote Browser Isolation
May 20, 2025
|
Organizations transitioning to Prisma® Access Agent face challenges when their
existing authentication infrastructure uses LDAP/LDAPS, as Prisma Access Agent
previously only supported SAML and certificate authentication through Cloud Identity
Engine (CIE). This can create significant adoption barriers, especially in regions
where LDAP usage is prevalent. LDAP support for Prisma Access Agent addresses this
challenge by enabling you to leverage your existing GlobalProtect® portal LDAP
authentication infrastructure, eliminating the need to reconfigure authentication
methods when migrating to Prisma Access Agent.
With LDAP authentication support, you can now
configure your Prisma Access Agent to authenticate users against your existing
directory services through the GlobalProtect portal. This integration provides a
seamless authentication experience for your users while maintaining your existing
security policies. The feature supports all standard LDAP configuration options,
including Base DN, Bind DN, multiple LDAP servers, SSL/TLS secure connections, and
server certificate verification for SSL sessions. You can also combine LDAP
authentication with client certificate authentication using AND/OR logic to meet
your specific security requirements.
The enhanced user experience includes support for saved user credentials, enabling
seamless authentication across device states such as sleep-wake cycles, hibernation,
and network transitions. When properly configured, users won't need to repeatedly
enter their credentials after logging into their operating system.
By supporting LDAP authentication through the GlobalProtect portal, Prisma Access
Agent provides you with a smoother migration path from GlobalProtect to Prisma
Access Agent, preserving your authentication setup while enabling you to transition
to a newer access agent. This feature is valuable for existing deployments where
reconfiguring authentication methods would otherwise increase deployment complexity
and time.
Pre-Logon for Prisma Access Agent
|
Pre-Logon for Prisma Access Agent
May 20, 2025
|
To avoid delays in critical device updates and maintain security, you need a way to
connect remote corporate-owned machines to the network before users log in. The
pre-logon feature for Prisma® Access Agent
addresses this challenge by establishing a secure device-level connection before
user authentication occurs.
This feature improves IT productivity and enhances your overall security posture by
ensuring all managed devices receive essential updates and configuration changes,
regardless of the user's login status. You can now perform critical management
tasks—such as applying group policies, installing software updates, and
synchronizing roaming profiles—without waiting for a user to log in.
Pre-logon is designed to provide consistent connectivity for your managed devices
across system restarts and sleep-wake cycles. By utilizing this capability, you
significantly improve the management of your remote assets and enhance security by
ensuring devices are properly configured and updated before users gain full network
access.
Prisma Access Agent Captive Portal Support
|
Prisma Access Agent Captive Portal Support
May 20, 2025
|
Mobile users often struggle to connect securely when working from locations with
captive portals, such as hotels, cafes, and airports. These captive portals require
authentication before allowing internet access. Prisma® Access Agent automatically
detects when a user has connected to a network with a captive portal and opens the
captive portal authentication page in its embedded browser, enabling users to
authenticate without bypassing security policies. This approach enhances security by
containing the captive portal interaction within the controlled environment of the
embedded browser, mitigating risks associated with external browser use.
By using captive portal support with Prisma Access
Agent's embedded browser functionality, you ensure that your mobile workforce
maintains secure access to corporate resources across diverse network environments.
It prevents scenarios where employees are unable to access the internet or corporate
resources due to undetected captive portals, while also addressing security concerns
related to captive portal interactions. This solution significantly reduces
connectivity-related support tickets, improves overall user productivity, and
provides an integrated, secure experience for your remote and traveling employees
while maintaining the stringent security standards your organization requires.
Prisma Access Agent Embedded Browser Support for SAML Authentication
|
Prisma Access Agent Embedded Browser Support for SAML Authentication
May 20, 2025
|
Managing SAML authentication across various web browsers poses significant challenges
for administrators, often resulting in a cumbersome user experience with annoying
pop-ups and redirection issues between the access agent and browser.
The Prisma® Access Agent embedded browser addresses this issue by
integrating a dedicated browser directly into the agent, providing your users with a
consistent in-app experience for Prisma Access Agent logins, simplifying
administration, and significantly enhancing security posture. By keeping the
authentication process within the application, you eliminate the need for external
browser interactions, reduce the risk of user confusion, and mitigate potential
security vulnerabilities associated with browser redirections. This internal
processing environment ensures strict adherence to conditional access policies,
which also simplifies administrative overhead.
With support for various authentication methods and compatibility with existing
Prisma Access Agent features, the embedded browser significantly improves both
security and usability in your remote access infrastructure.
Transparent Proxy Support for Prisma Access Agent
|
Transparent Proxy Support for Prisma Access Agent
May 20, 2025
|
Prisma® Access Agent now supports transparent proxy connections, offering
always-on internet security and private app access for your mobile users. This
feature enables seamless coexistence with third-party VPN agents, enhancing your
organization's security posture. You can use it to secure all internet traffic from
browser and nonbrowser apps, even when users are disconnected from the tunnel. The
solution forwards internet traffic to Prisma Access, preventing users from bypassing
Prisma Access.
You can support various scenarios including users connecting from home, branch
offices, or public Wi-Fi. It's compatible with endpoints running third-party VPNs in
full or split tunnel modes. The feature prevents conflicts on endpoints and offers
admin controls to maintain smooth operation. You will find this useful for
maintaining consistent security across diverse networks. It supports continuous
trust verification for mobile users through device posture checks. By implementing
this functionality, you can enforce security policies regardless of user location or
connection method, strengthening your overall security stance and strengthening your
overall security posture with always-on connectivity.
Extend Prisma Access User Group Policy Support with Short Form Format
|
Extend Prisma Access User Group Policy Support with Short Form Format
May 16, 2025
|
We introduced the ability to extend Prisma Access user group policy
with the short form format. Migrating security policies from NGFW to Prisma Access
requires policy elements standardization. Prisma Access only supports long-form DN
entries for group-based policies, while the NGFW allows using other formats such as
SAML account name/Common Name and email address. This feature enables customers to
define the group format choice for security policy creation, allowing standardized
policy creation across Prisma Access and NGFW.
IP Capacity Planning
|
IP Capacity Planning
May 16, 2025
|
Use IP capacity planning to streamline the Prisma® Access tenant onboarding process
by automating and simplifying egress IP address capacity planning. You can
quickly allocate egress IP addresses for your mobile users based on the city and
user count, significantly reducing the time it takes to allow list the IP addresses
in your network. This feature provides an intuitive workflow for adding locations
individually or through bulk upload, visualizing your global deployment on an
interactive map, and automatically suggesting optimal Prisma Access locations based
on your input. You can easily review and adjust these recommendations, ensuring that
your deployment aligns with your specific needs.
The IP address capacity planner also offers a comprehensive view of your egress IP
address allocations and user distributions, enabling you to make informed decisions
about your network resources. By using this feature, you can expedite your Prisma
Access deployment, and ensure a smooth end-user experience. The automated process
lets you optimize your deployment and make it easier to scale your network as your
needs evolve. This feature is valuable if you have a large, geographically diverse
user base or need to frequently adjust your network capacity to meet changing
demands.
Simplified Onboarding Workflow for Prisma Access
|
Simplified Onboarding for Prisma Access
May 16, 2025
|
Organizations often face complex, manual setup processes when deploying SASE
solutions, leading to delayed security protection. The Prisma® Access onboarding
workflow addresses this challenge by providing a simplified initial setup process
for new deployments. This guided workflow rapidly deploys and configures the
necessary components for securing mobile users (via GlobalProtect® and Explicit Proxy) and for securing private
applications (via Service Connection). By incorporating
best-practice defaults, automating backend tasks, and seamlessly integrating the
Cloud Identity Engine and Strata Cloud Manager with Prisma Access,
this intuitive, action-oriented approach accelerates time-to-value and significantly
reduces onboarding complexity.
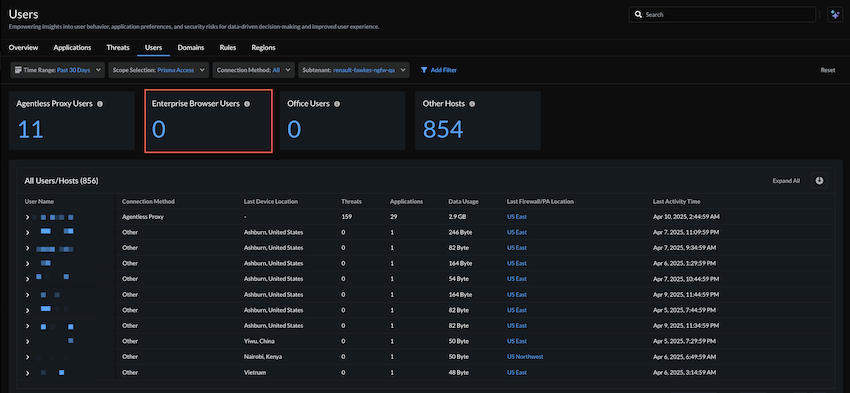
Visibility for Enterprise Browser
|
Visibility for Enterprise Browser
May 13, 2025
|
Achieving granular visibility into user activity across various enterprise browsers
was previously a challenge. Now, depending on your license, Strata Cloud Manager
offers the following new features for advanced monitoring:
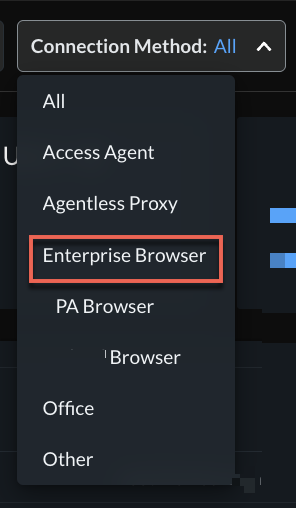
- Activity InsightsUsersNew Connection Method = Enterprise BrowserEnterprise Browser is now available as a Connection Method to filter user activity by Enterprise Browsers in Prisma® Access. You can view the following details:
- Active Users trend chart
- Current Active User count and list
- Risky Users
- Active Users list including User Name, Browser Type, Browser Version, Last Source IP, Last Source Location, Last Used PA Location, and Last Activity Time
![]() If you have multiple enterprise browsers, you can switch to Prisma® Access Browser or any other supported third-party enterprise browser using Connection Method.
If you have multiple enterprise browsers, you can switch to Prisma® Access Browser or any other supported third-party enterprise browser using Connection Method.![]()
- Subscription Usage for Mobile Users: MonitorSubscription UsageMobile UsersYou can see the usage count under Total Unique Users.
- Prisma® Access locations: MonitorPrisma Access LocationsNew widget for Explicit Proxy locations, status, and connectivity to Strata Logging Service.
CVE Threat Research for Strata Copilot
|
CVE Threat Research for Strata Copilot
May 9, 2025
|
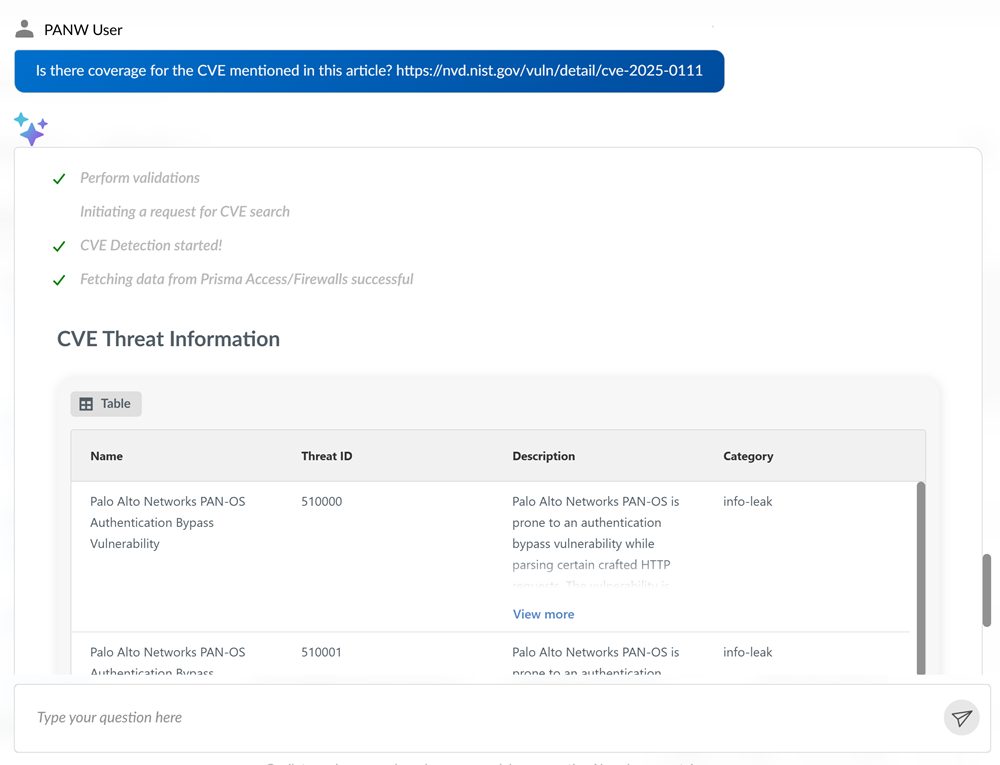
You can now quickly determine if Palo Alto
Networks provides protection against specific vulnerabilities using Strata
Copilot. When investigating specific CVEs, Strata Copilot searches
comprehensive data sources to provide detailed protection information including
unique threat IDs, descriptions, categories, compatible PAN-OS versions, release
dates, and current status.
To receive information about available safeguards for deeper investigation,
you can simply ask questions like:
"Is there coverage for the CVE mentioned in this article?
<articleURL>"
"Does Palo Alto Networks protect against
<CVE>?"
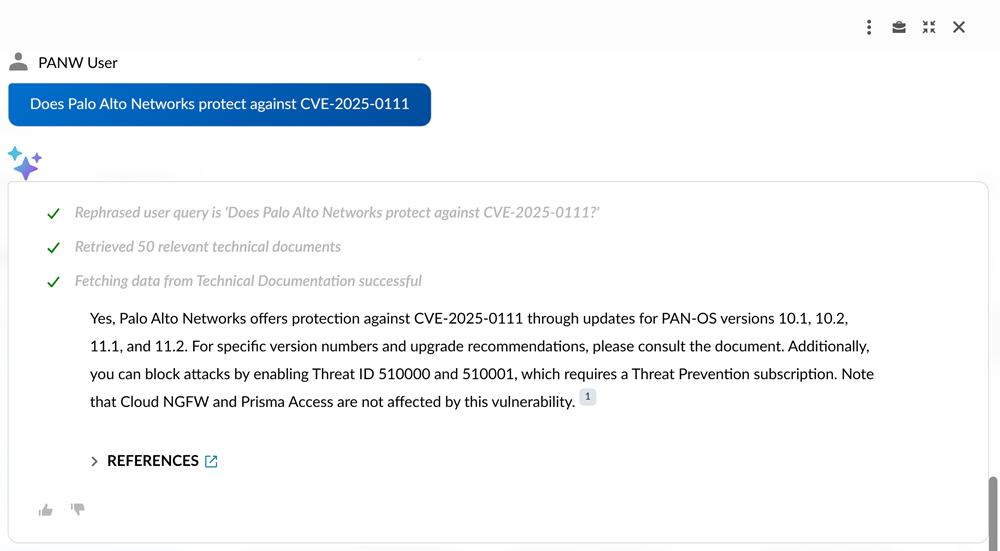
Designed for enterprise-scale performance, Strata Copilot handles large
datasets related to Threat Detection and Prevention data while delivering responses
in under 5 seconds for most threat intelligence queries. Strata Copilot minimizes
latency between data updates and availability to ensure you always receive the most
current information about CVE protection status and potential threat actor
exploitation activity in your environment.
Strata Copilot: Device Quarantine
You can now quarantine Prisma Access directly
through Strata Copilot, enhancing your security management capabilities. This
feature is conveniently accessible across key areas of the platform, including from
the Strata Cloud Manager Summary, NGFW and
Prisma Access Configuration Overview, and Devices management pages. There, you
have the flexibility to initiate device quarantine in Strata Copilot by providing
either the host ID alone or both the host ID and device serial number.
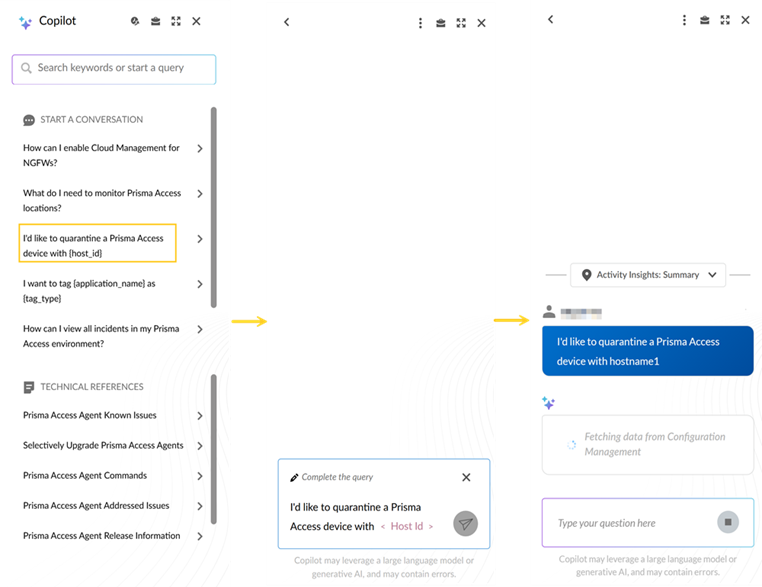
When Strata Copilot processes your request to add the specified device to the
quarantine list, you will see immediate feedback including a convenient link to view
more details in the relevant sections of the platform. This streamlined process,
allows you to quickly isolate potentially compromised or problematic devices,
thereby improving your overall network security posture and operational
efficiency.
June 23, 2025
Supported on Strata Cloud Manager for Prisma Access and NGFW