Table of Contents
Expand all | Collapse all
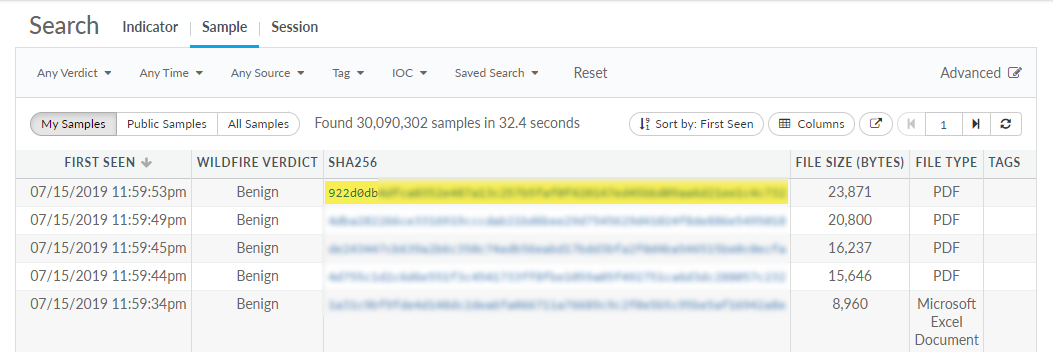
Sample
The Sample tab in the AutoFocus
search editor displays all samples that match the conditions of
the search. Click the column headers for the sample details to sort
samples in ascending (up arrow) or descending (down arrow) order.
By default, the most recently detected samples are displayed. You
can choose to view only My Samples, only Public Samples, or All
Samples. All Samples includes both public and private samples; however,
private samples submitted by firewalls or sample sources other than
those associated with your support account display with an obfuscated
hash.
Set a default scope for search results to
choose which samples are displayed immediately when you launch a
search. Navigate to the AutoFocus portal Settings and
select a Preferred Scope. You must click Save
changes to save the new default scope.
To examine Sample
Details, click on a sample hash after initiating a search:
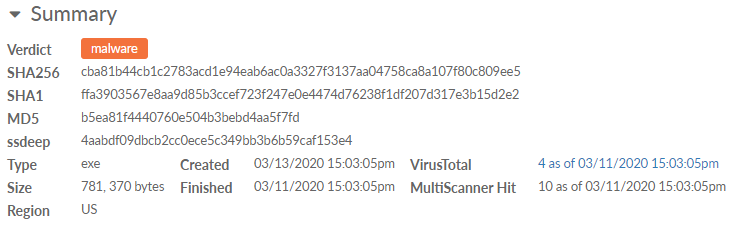
Sample Details | |
|---|---|
| |

| Make a sample Public to
share the sample with other AutoFocus security experts. You can
also revert the status of the sample to Private at
any time. |

| Lists the tags the sample is associated
with, and you can also add a new tag. (For details on tags and how
tagging works, see AutoFocus
Tags). Hover over a tag to view
more tag information in a popup. You can click on the linked tag
name to Vote
for, Comment on, and Report Tags. |

| Shows the WildFire analysis report sample
details based on the virtual environment(s) used to analyze the
file. This includes comprehensive information about how the sample
verdict was determined, including specific behaviors and system
process changes, as well as associated IoCs and causality chain,
to help you visualize how the sample infiltrated your network.
Select a drop down to view specifics
for each WildFire report context:
|

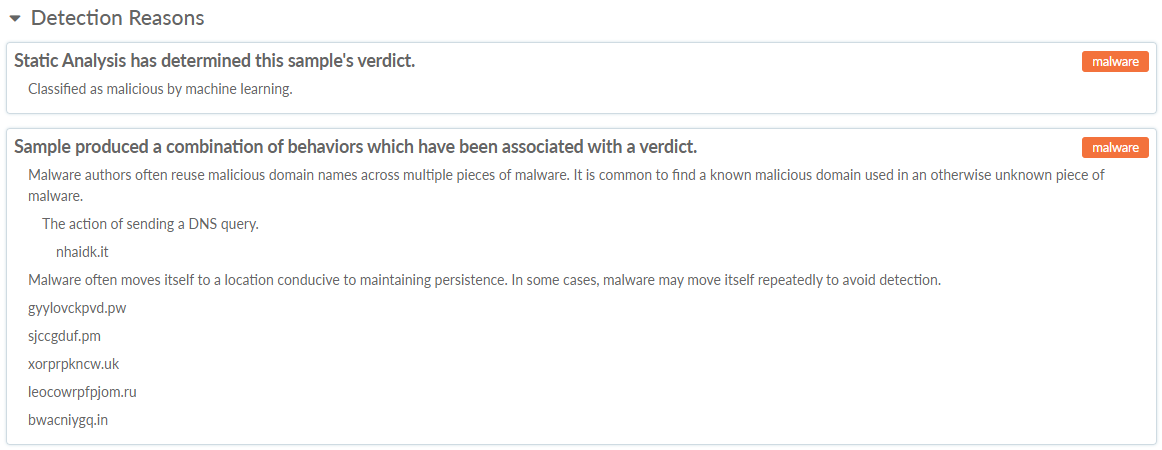
| Lists the sample details and properties.
The nested WildFire Dynamic Analysis section describes the sample’s
observed behavior and lists each activity the sample performed when
executed in the WildFire analysis environment. You can view sample
details that WildFire detected in environments running different
operating systems. If you have any reason to believe the verdict
is a false positive or a false negative, click Report
as Incorrect to submit the sample to the Palo Alto Networks
threat team. The threat team performs additional analysis on the
sample to determine and verify the verdict. Select a method
of viewing the WildFire dynamic analysis of the sample:
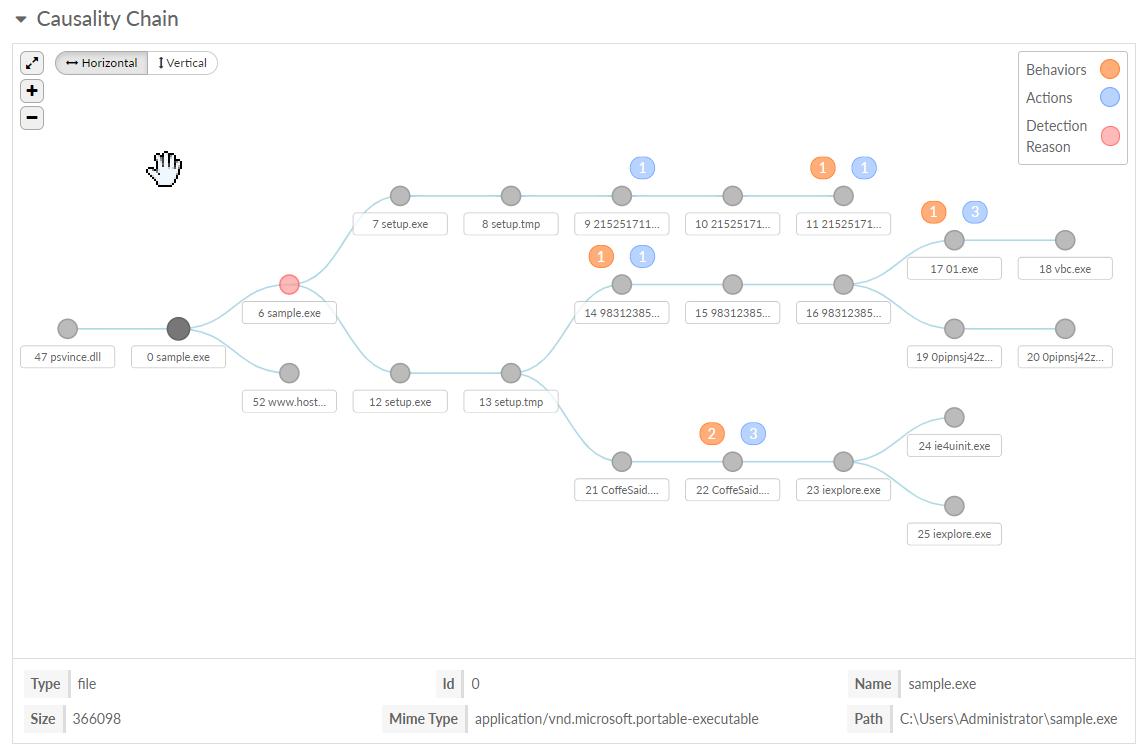
In
Sequence and Tree view, you can see the activities that occurred in
the operating system kernel space and user space:
As you drill
down in the Wildfire Dynamic Analysis details for a sample, high-risk
artifacts associated with the sample are marked for easy identification.
You can add artifact evidence and observed behavior to a new or
existing search. |
File Analysis (continued) | The Observed
Behavior section displays the total number of activities
that are Evidence of a specific behavior. Each behavior has an associated
risk level, and you can expand a single behavior to see the matching
sample activities. You can also expand an activity section
to see all of the specific sample activities that fall under it.
For each activity artifact, the total number of times the artifact
has been found with benign ( Depending
on the artifact, you can:
If
an artifact is evidence of an observed behavior, the behavior risk level
is indicated with this icon: A gray icon
indicates a low risk behavior, a yellow icon indicates a medium
risk behavior, and a red icon indicates the artifact is evidence
of a critical, and high-risk behavior. Based on the sample
artifacts, AutoFocus highlights high-risk indicators as Suspicious or Highly
Suspicious. See Artifact
Types for a detailed and expanded description of the WildFire
analysis sections and the artifacts they contain. |

| Lists all sessions during which samples
with the same SHA256 hash were detected. The sessions displayed
are all WildFire sessions submitted from your Palo Alto Networks
firewall or another Upload
Source associated with your support account. Select a single session
for session details. Click the File Analysis tab
to navigate back to the sample details. |

| Lists the WildFire signatures that match
to the sample. Check signature coverage to assess the level of protection
in place against malware. Depending on the sample, all or some of
the following signature types provide coverage:
For each
of these signature types, the date that WildFire created the signature
is listed. You can toggle between daily, 15 minute, and 5 minute content
updates to see the versions that included the signature. The first content
version that included the signature is listed, as well as the last content
version to include an update to the signature. The table also indicates
whether a signature is included in the most current content version. |

| Lists Threat
Indicators that AutoFocus detected in the sample’s WildFire
analysis details. The list consists of only artifacts that AutoFocus
considers indicators based on the tendency of the artifact to be seen
predominantly in malware samples. AutoFocus uses a statistical algorithm
to determine which artifacts are indicators. |
Next Steps... |
|