Deploy Client Credential Flow for Okta
Table of Contents
Expand all | Collapse all
-
- Cloud Identity Engine Attributes
- Collect Custom Attributes with the Cloud Identity Engine
- View Directory Data
- Cloud Identity Engine User Context
- Create a Cloud Dynamic User Group
- Configure Third-Party Device-ID
- Configure an IP Tag Cloud Connection
- Configure Dynamic Privilege Access in the Cloud Identity Engine
-
-
- Configure Azure as an IdP in the Cloud Identity Engine
- Configure Okta as an IdP in the Cloud Identity Engine
- Configure PingOne as an IdP in the Cloud Identity Engine
- Configure PingFederate as an IdP in the Cloud Identity Engine
- Configure Google as an IdP in the Cloud Identity Engine
- Configure a SAML 2.0-Compliant IdP in the Cloud Identity Engine
- Configure a Client Certificate
- Set Up an Authentication Profile
- Configure Cloud Identity Engine Authentication on the Firewall or Panorama
- Configure the Cloud Identity Engine as a Mapping Source on the Firewall or Panorama
- Configure Dynamic Privilege Access in the Cloud Identity Engine
-
- Get Help
Deploy Client Credential Flow for Okta
By granting a few read-only permissions for
your Okta directory in advance, the Client Credential Flow option
for Okta in the Cloud Identity Engine allows you to use a service account
to log in to your Okta directory in the Cloud Identity Engine. Using
a service account is strongly recommended, as this is a more secure
method for directory access and does not require the account to
be associated with a specific user.
You must obtain a
new client ID and secret if you have an existing Okta directory
configuration. The client ID and secret for the Okta directory auth
code flow (the existing method) are not compatible with the API
service integration that the client credential flow method uses.
- Download the Okta integration app from the Okta Integration Network.
- In the Okta Administrator Portal, select.ApplicationsAPI Service Integrations
![]()
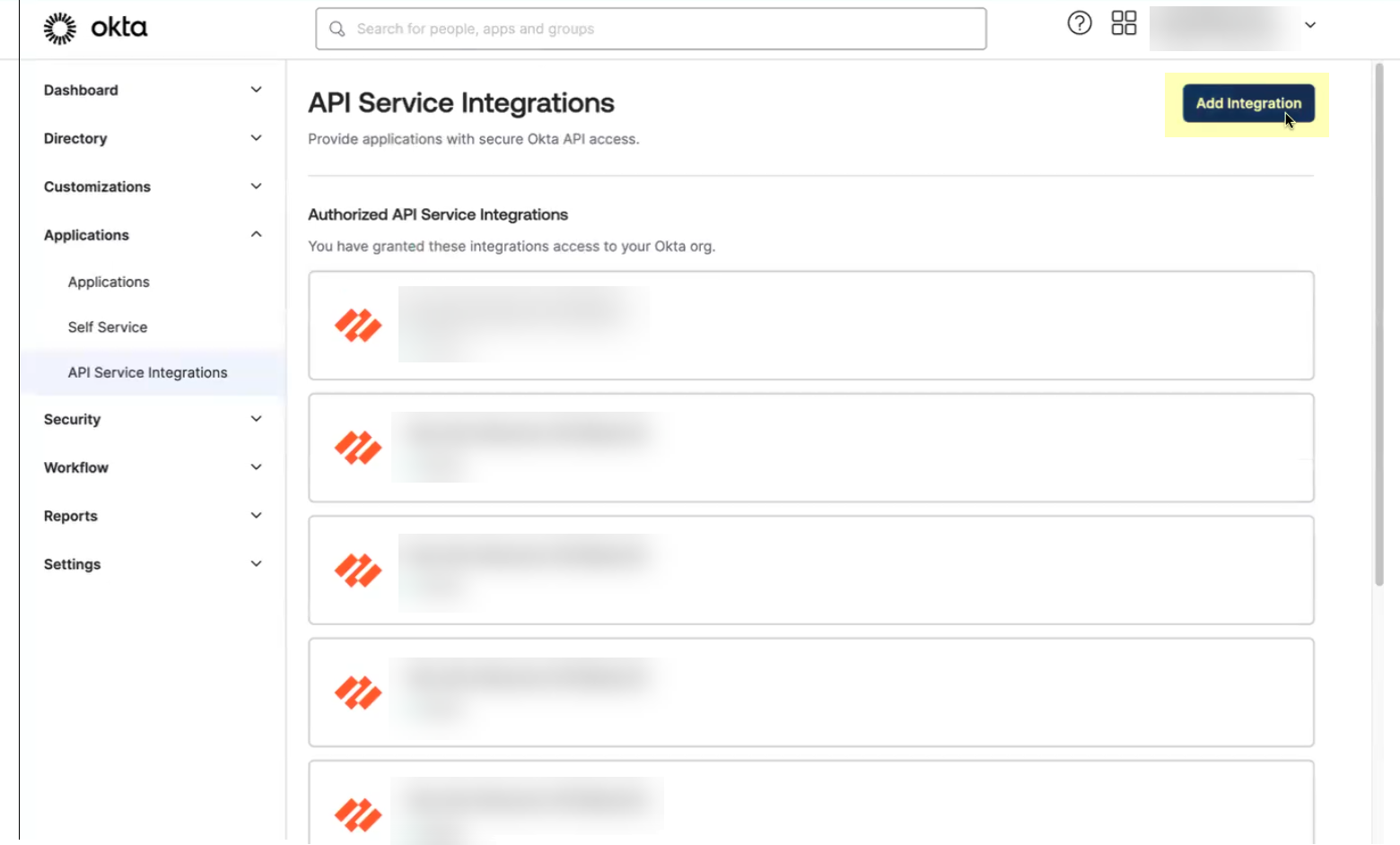
- ClickAdd Integration.
![]()
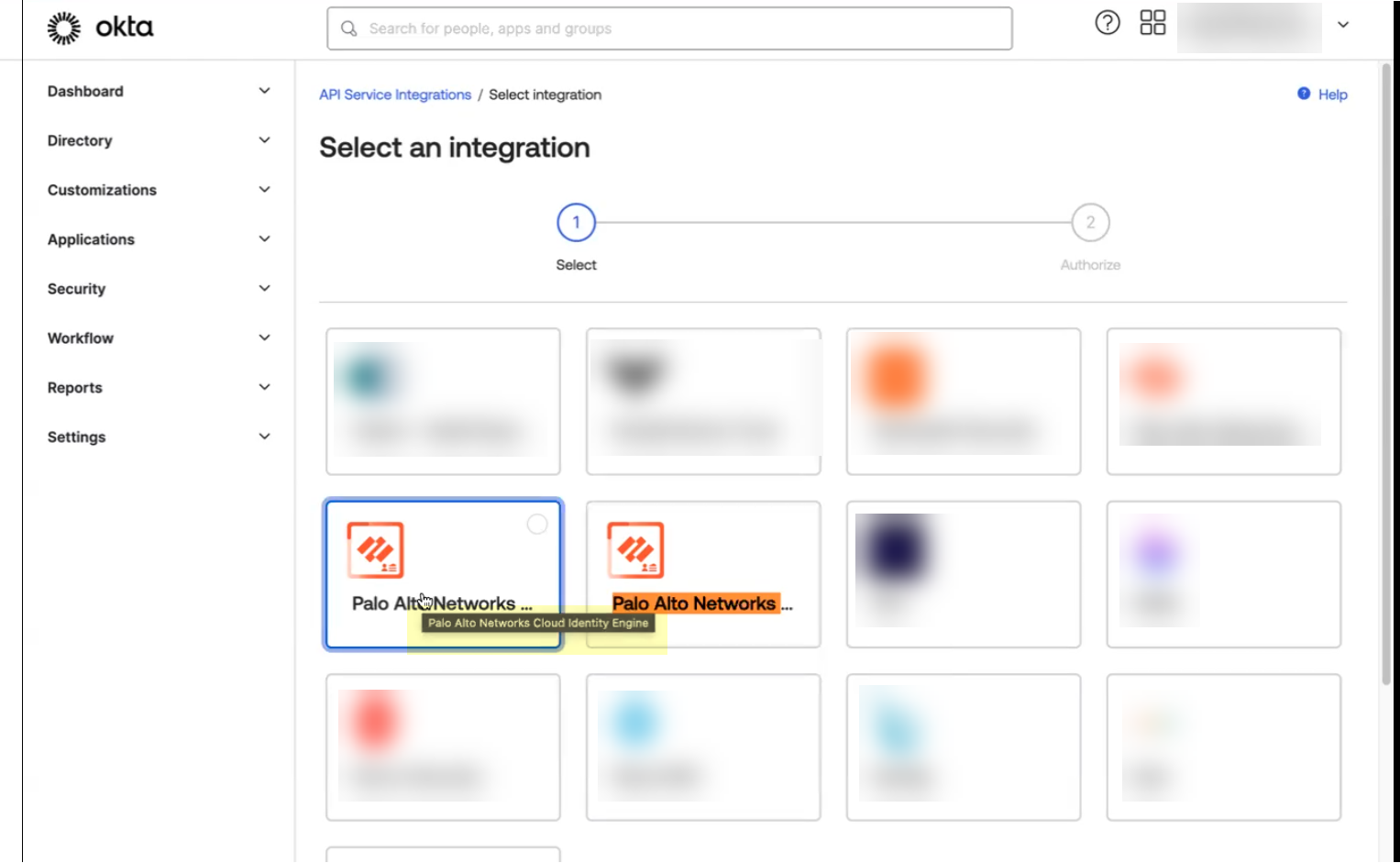
- Select the app integration you want to use based on whether you want to enable app data and clickNext.
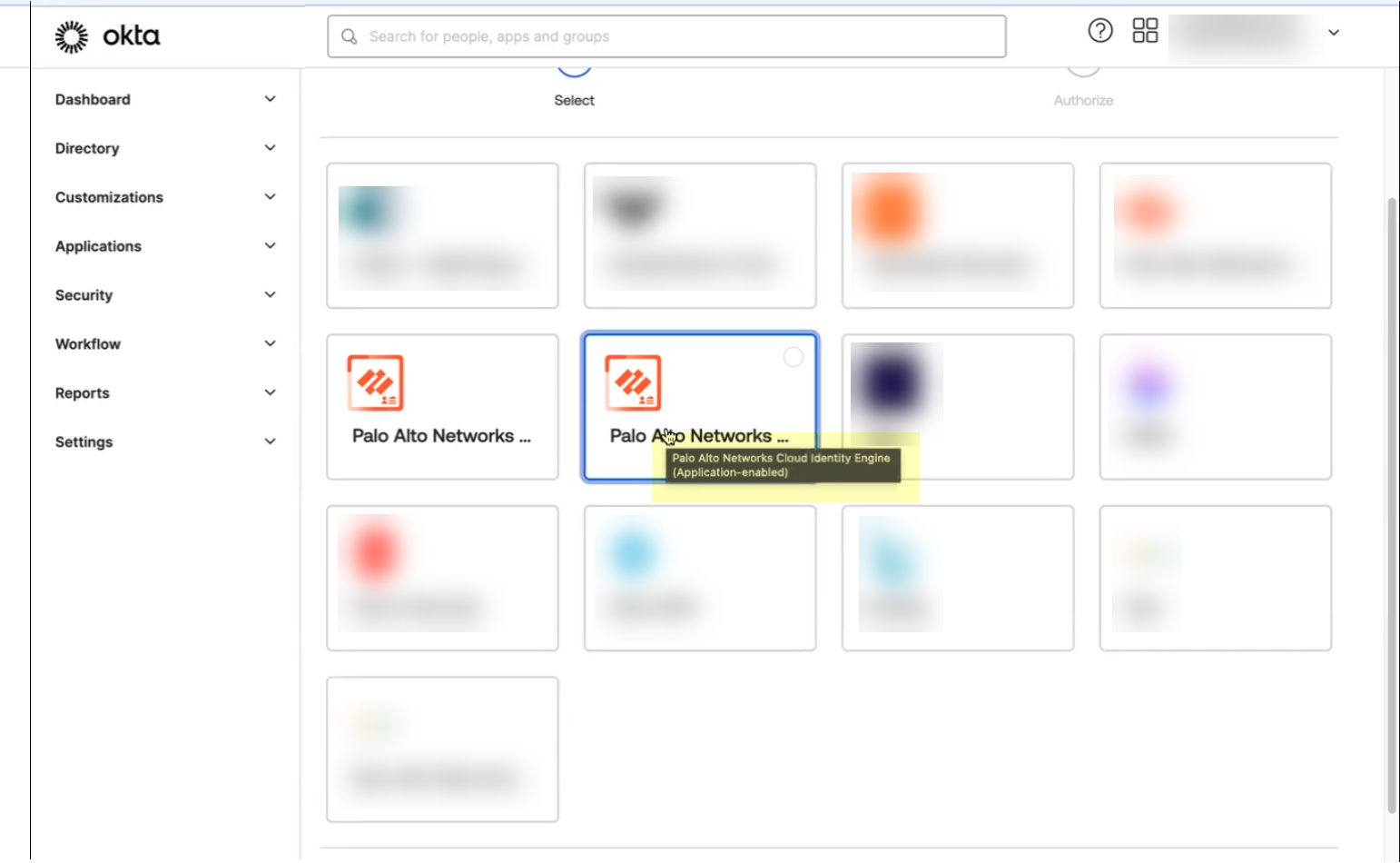
- If you use application data in your security policy, select thePalo Alto Networks Cloud Identity Engine (Application-enabled)app. For more information on collecting application data, see Step 9 in Configure Okta Directory.
![]()
- If you do not use application data in your security policy, select thePalo Alto Networks Cloud Identity Engineapp.
![]()
To ensure that you select the correct app, either useFindin your browser (Ctrl+F) to search for the app you want to use or hover over the app to display the full app name.
- Install and configure the API service integration.
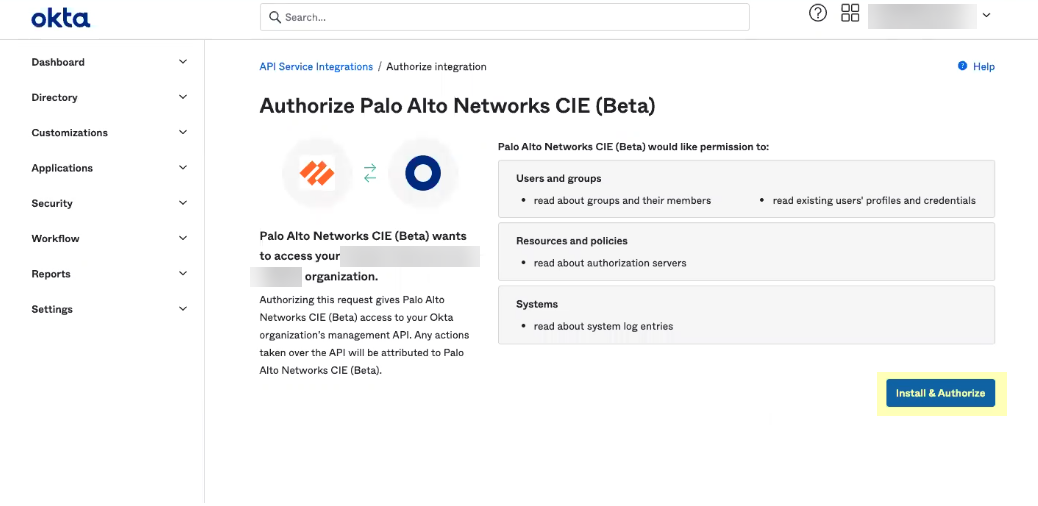
- Install & Authorizethe API service integration.
![]() The Okta API service integration automatically configures the following required API scopes:
The Okta API service integration automatically configures the following required API scopes:- Users and groups—Read existing users’ profiles and credentials. Read about groups and their members. Read the signed-in user's profile and credentials.
- Authorization servers—Read about authorization servers.
- (Application-enabled app only)Apps—Read about apps.
- Logs—Read about system log entries.
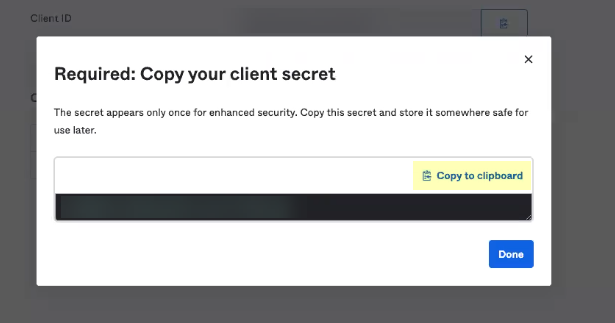
- ClickCopy to clipboardto copy the client secret and store it in a secure location, then clickDone.
![]() The client secret displays only once, so make sure to copy it and store it securely before clickingDone.
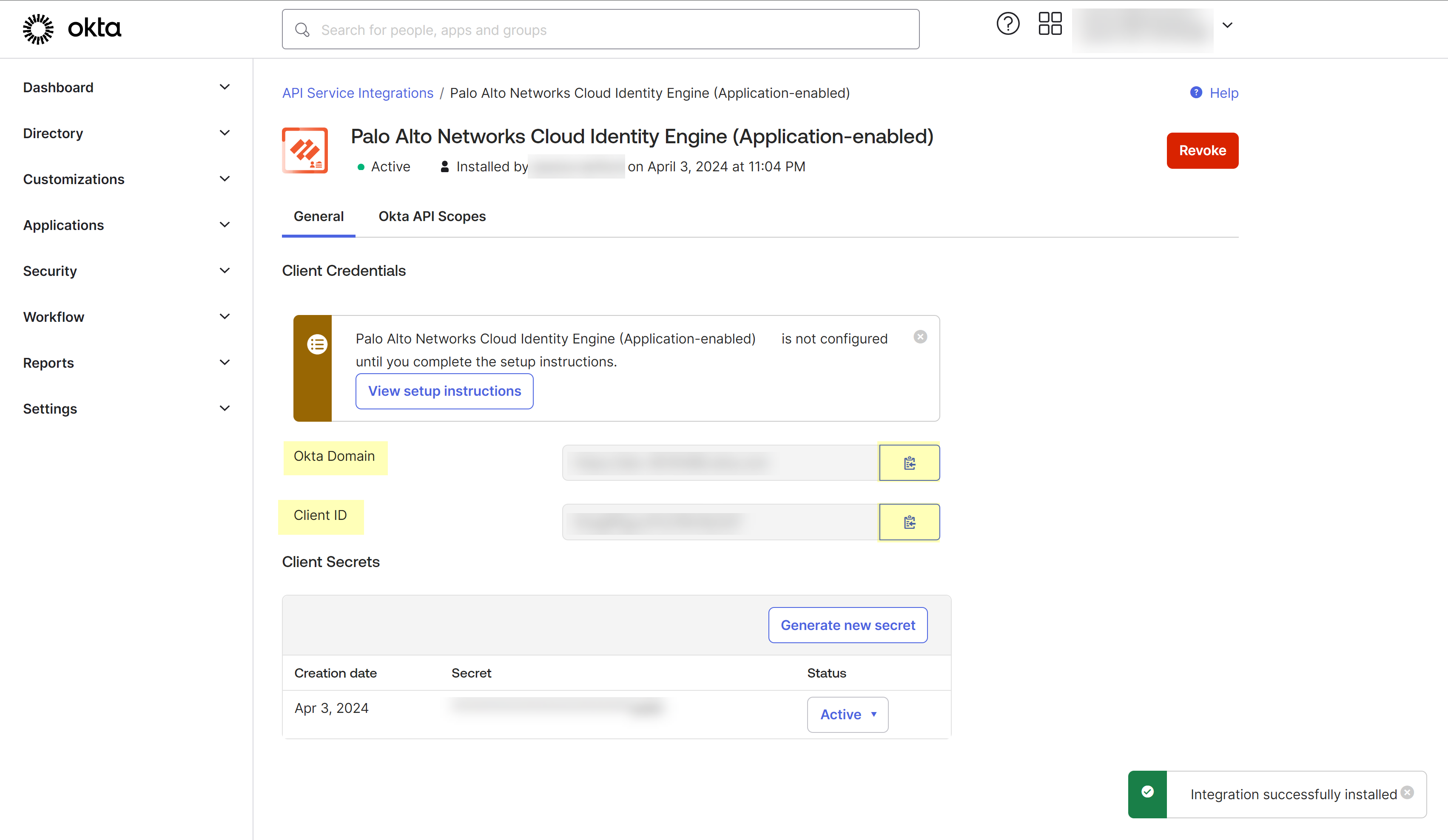
The client secret displays only once, so make sure to copy it and store it securely before clickingDone. - Copy theOkta Domainand theClient IDand store them in a secure location.You must edit the domain by removing thehttps://before pasting it.
![]()
- If you have not already done so, activate your Cloud Identity Engine tenant.
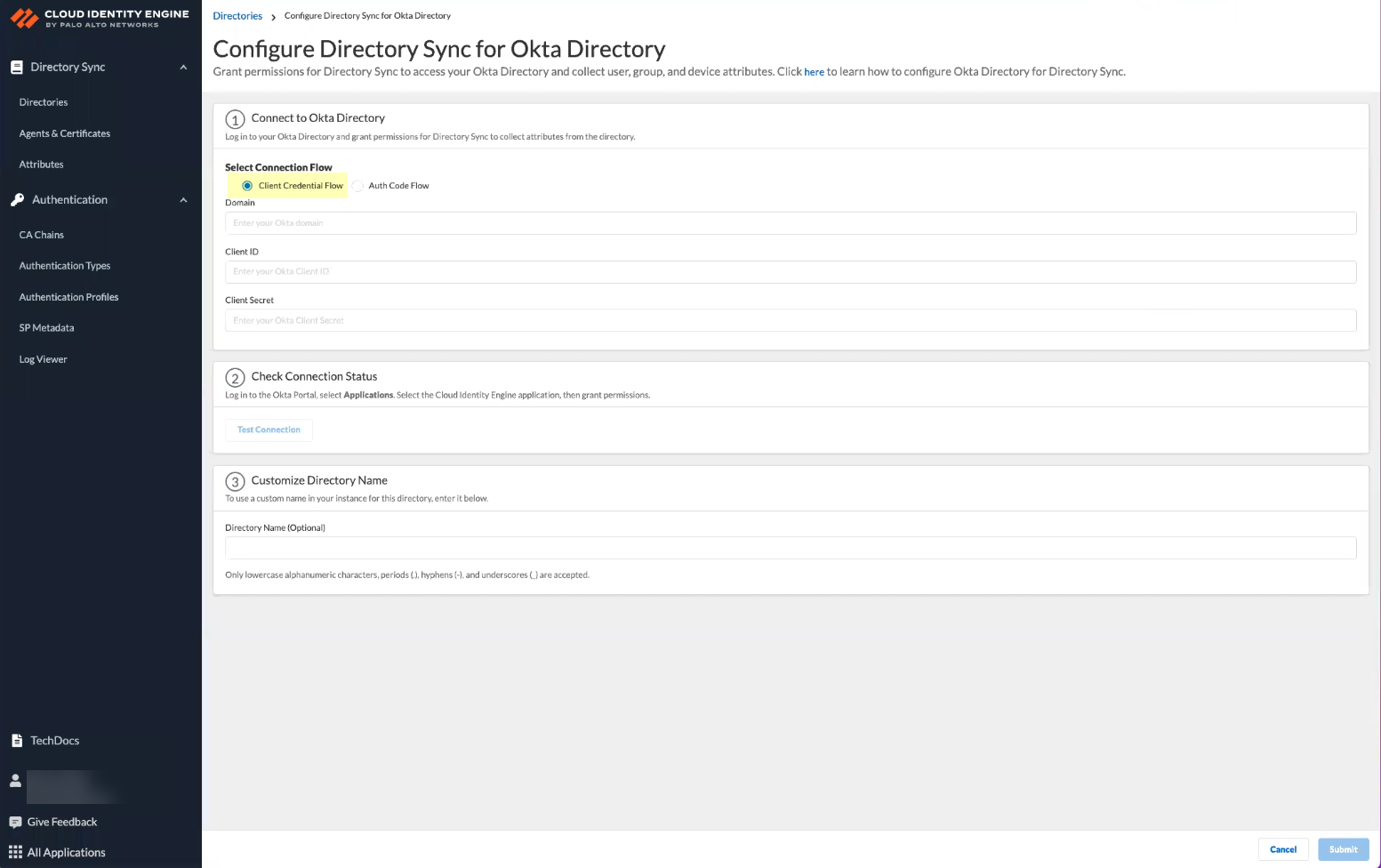
- Set upaCloud Directoryand selectOkta.
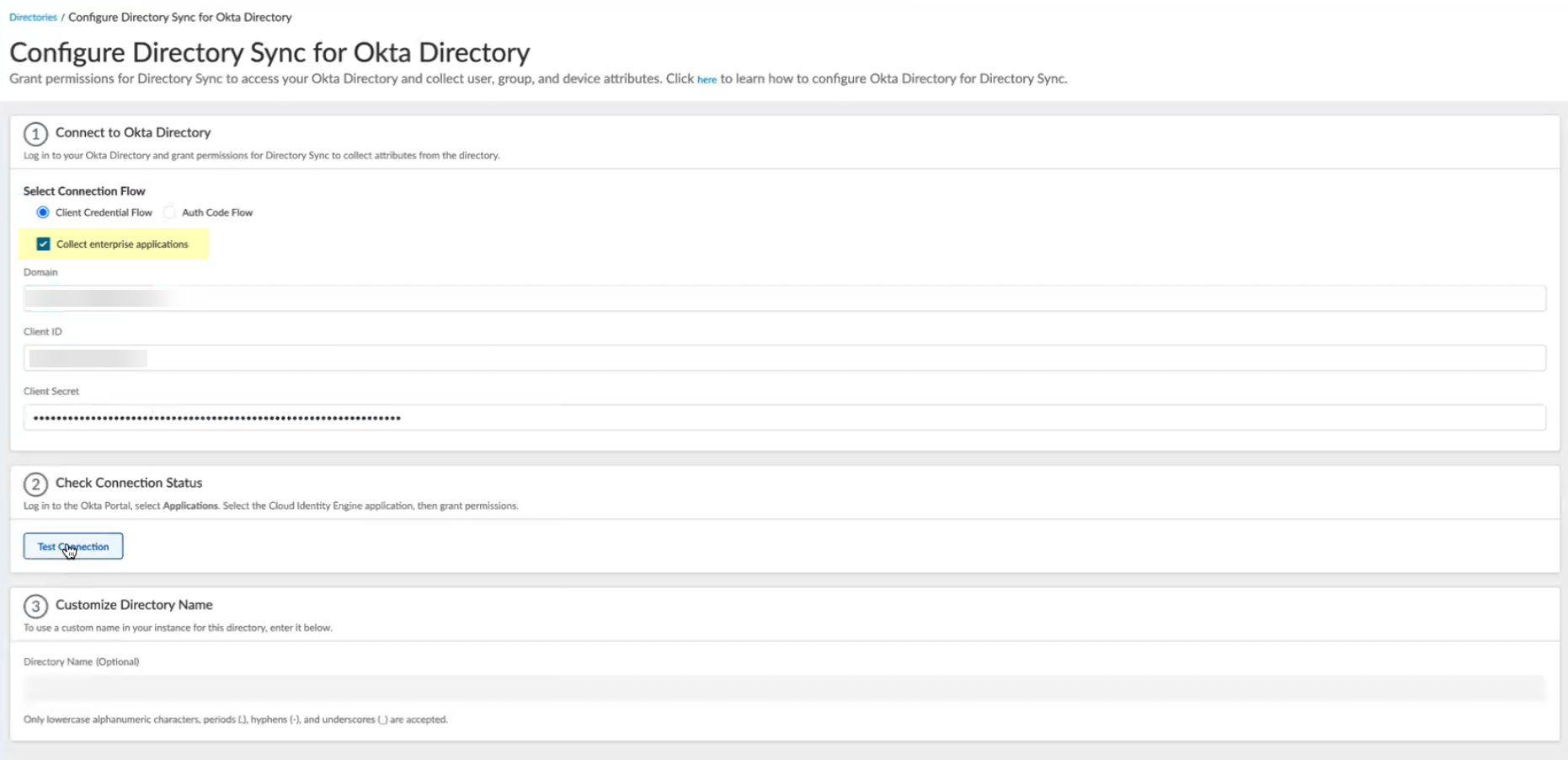
- UnderSelect Connection Flow, selectClient Credential Flow.
![]()
- SelectCollect enterprise applicationsto display application data when you view directory data.If you select this option, you must use thePalo Alto Networks Cloud Identity Engine (Application-enabled)to ensure the correct permissions.
![]()
- Paste the information you copied from the Okta management console into the fields as indicated in the following table.
![]() Okta Managment Console FieldCloud Identity Engine App FieldOkta DomainDomainClient IDClient IDClient SecretClient Secret
Okta Managment Console FieldCloud Identity Engine App FieldOkta DomainDomainClient IDClient IDClient SecretClient Secret - ClickTest Connectionto verify the Cloud Identity Engine can successfully communicate with your Okta directory.You must test the connection to submit the configuration.
- (Optional) Customize the name of the directory that displays in the Cloud Identity Engine.If you want to use a custom name for this directory in the Cloud Identity Engine, enter the custom name as theDirectory Name (Optional).
- Submityour changes and verify your directory information when theDirectoriespage displays.