Reconnect Okta Directory
Table of Contents
Expand all | Collapse all
-
- cloud-identity-engine-attributes
- Collect Custom Attributes with the Cloud Identity Engine
- View Directory Data
- Cloud Identity Engine User Context
- Create a Cloud Dynamic User Group
- Configure Third-Party Device-ID
- Configure an IP Tag Cloud Connection
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Configure Security Risk for the Cloud Identity Engine
- Send Cortex XDR Risk Signals to Okta
-
-
- Configure Azure as an IdP in the Cloud Identity Engine
- Configure Okta as an IdP in the Cloud Identity Engine
- Configure PingOne as an IdP in the Cloud Identity Engine
- Configure PingFederate as an IdP in the Cloud Identity Engine
- Configure Google as an IdP in the Cloud Identity Engine
- Configure a SAML 2.0-Compliant IdP in the Cloud Identity Engine
- Configure a Client Certificate
- Configure an OIDC Authentication Type
- Set Up an Authentication Profile
- Configure Cloud Identity Engine Authentication on the Firewall or Panorama
- Configure the Cloud Identity Engine as a Mapping Source on the Firewall or Panorama
- Configure Dynamic Privilege Access in the Cloud Identity Engine
-
- Get Help
Reconnect Okta Directory
If there’s a connection loss between the Cloud Identity Engine and your Okta Directory,
follow these steps to reconnect your directory.
If the connection between your Okta directory and the Cloud Identity Engine isn’t active or you
want to make changes to your Okta directory configuration, you can reconnect your
Okta directory to the Cloud Identity Engine.
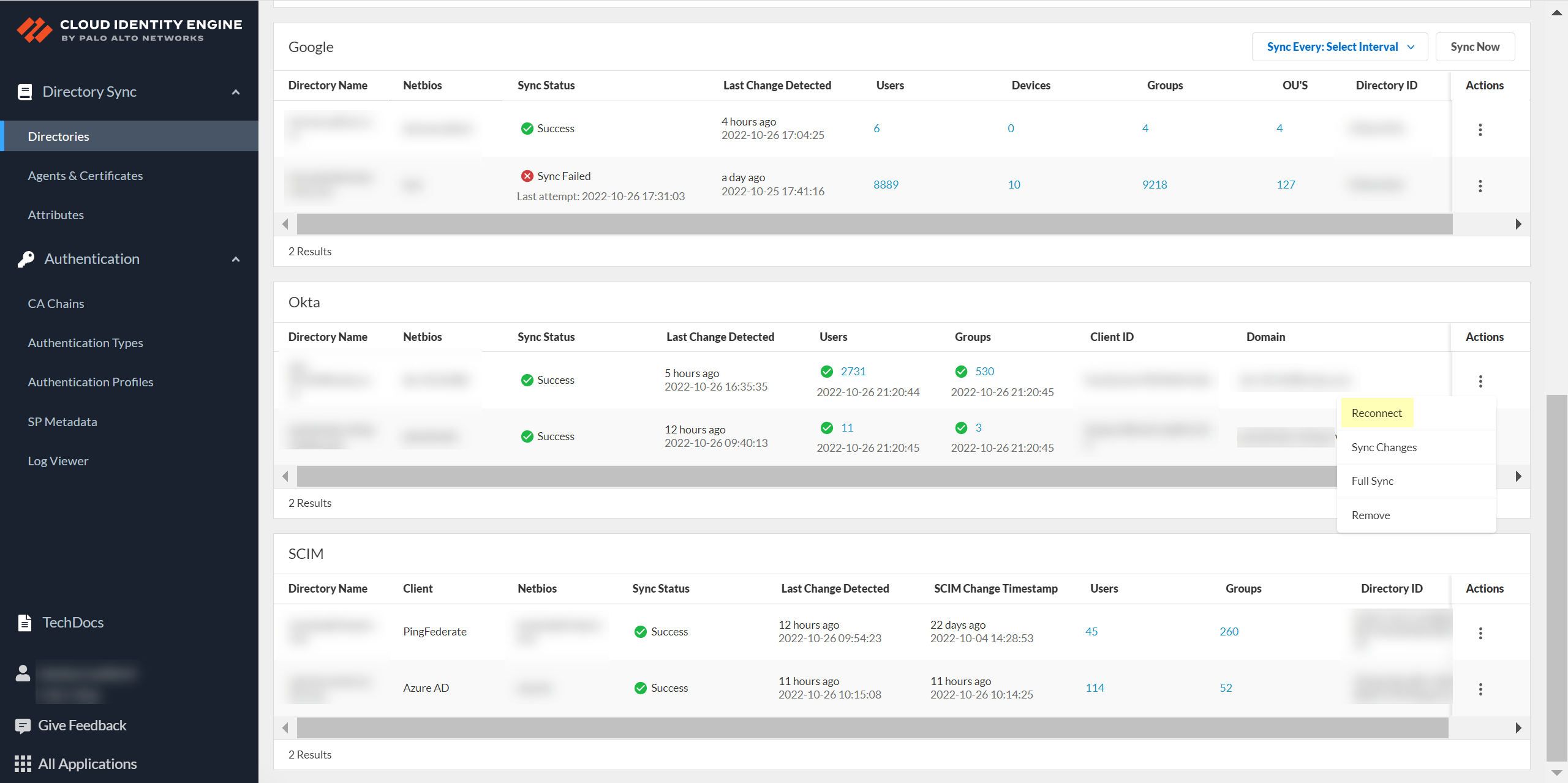
- Log in to the hub and select the Cloud Identity Engine tenant that contains the Okta directory you want to reconnect.Select Directories.Select ActionsReconnect for the directory you want to reconnect.
![]() Select whether you want to make any changes to your configuration.
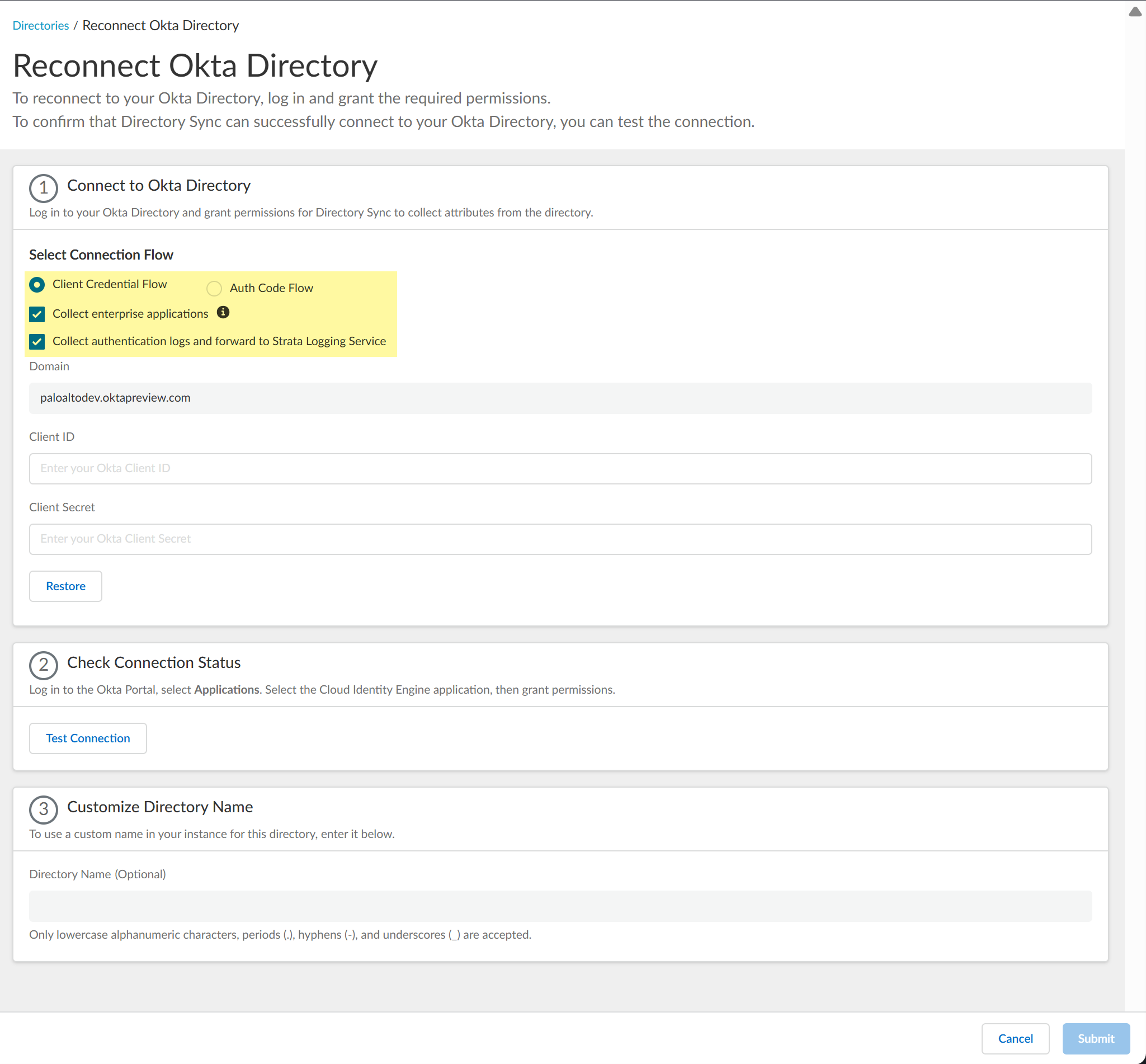
Select whether you want to make any changes to your configuration.- If you want to use a service account to log in to the Okta directory,
select the Client Credential Flow. For more
information, refer to step 8 in the documentation on
how to Configure Okta Directory for the Cloud Identity
Engine.
![]()
- If you want the Cloud Identity Engine to Collect enterprise applications data so that it is included when you View Directory Data, select the checkbox. If you don't use enterprise application data in your security policy or you don't want to collect the data, deselect the checkbox.
(Auth Code Flow only) Sign in with Okta using your Okta administrator credentials and grant permissions for the Cloud Identity Engine to access the directory information.(Client credential flow only) Enter the Client ID and Client Secret (or click Restore to restore the current client secret).You cannot change the Domain. If you need to change the domain, you must create a new Okta directory configuration in the Cloud Identity Engine.Click Test Connection to confirm the Cloud Identity Engine can access your Okta directory.(Optional) Customize Directory Name if you want to change the name that the Cloud Identity Engine displays for this directory in your tenant.You can use up to 15 lowercase alphanumeric characters (including hyphens, periods, and underscores) for the directory name in the Cloud Identity Engine. You don't need to change the name of the directory itself, only the name of the directory in the Cloud Identity Engine app. If your directory name contains more than 15 characters, you must change the directory name to contain a maximum of 15 characters.Submit your configuration.