AI Access Security
Discover Risks Posed by GenAI Apps by Risky Apps
Table of Contents
Expand All
|
Collapse All
AI Access Security Docs
Discover Risks Posed by GenAI Apps by Risky Apps
Discover risky generative AI (GenAI) apps accessed on your network.
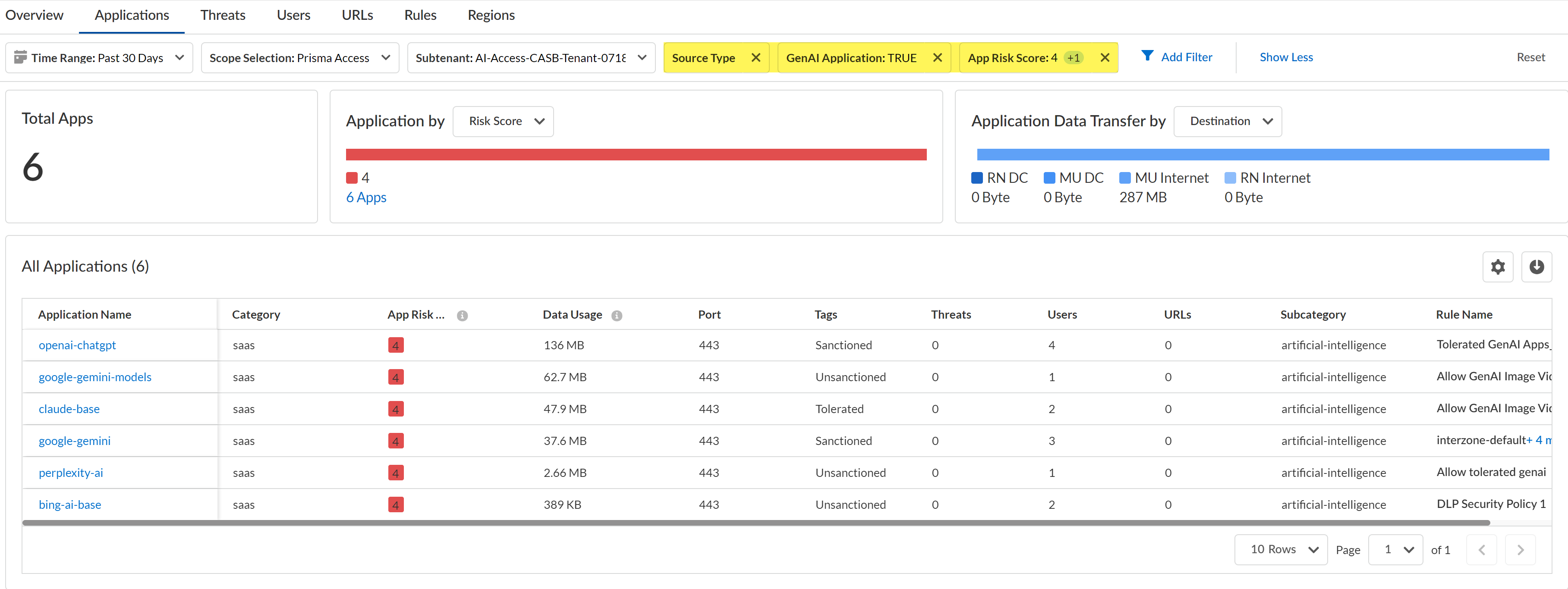
- Log in to Strata Cloud Manager.Select InsightsActivity InsightsApplications.Configure the filters for the app list to narrow down the GenAI apps you want to investigate.
- Configure the Time Range and Scope Selection to filter for the specific time range and enforcement point you want to investigate.Add Filter and add the following filters.
- Source Type - Users—Filters the list of apps to only display GenAI apps accessed by users in your organization. This is a required filter.
- GenAI Application - TRUE—Filters the list of app to only display GenAI apps. This is a required filter.
- App Risk Score—For the App Risk Score filter, select the specific risk score you want to investigate. All GenAI apps are displays if you don't select at least one risk score.In this example, we are investigating apps with a risk score of 4 and 5 because these are the risk scores attributed to the riskiest apps.
Review the list filtered GenAI apps.Some important information to review is:- Application Name—App-ID of the GenAI app.
- Data Usage—Amount of data uploaded to or downloaded from the GenAI app. This can help you understand the GenAI app usage; a GenAI app with a large volume of data usage could mean that this app is widely used and might need strict controls to prevent exfiltration of sensitive data and malicious actors.
- Tags—Current app tag for the GenAI app. If some of the listed GenAI apps are approved for use, you can modify the tag to Tolerated or Sanctioned.Palo Alto Networks groups the child App-IDs for app functionality in a container App-ID. However, tagging an App-ID container is not supported. You must individually tag the specific child App-ID that are sanctioned, unsanctioned, or tolerated within your organization.
![]() Create a custom Security policy rule to control access to a GenAI app for specific users.For example, based on your investigation you discover that there are multiple unsanctioned GenAI apps with a large volume of data usage. This poses a security risk because there are users accessing an unapproved app on the network and you don't know what data is being downloaded or uploaded. Until you can perform proper due diligence to understand the GenAI app purpose and who is permitted to use the GenAI app, you can Block the GenAI app for all users.Conversely, you notice there are some Unsanctioned GenAI apps listed that but they are GenAI apps approved for use on your network by specific users with a large volume of data usage. In this case, you can change the tag to Sanctioned and write a policy rule to Allow usage of the app but only for users in specific roles or departments. In the policy rule you can associate an Enterprise Data Loss Prevention (E-DLP) data profile to prevent exfiltration of sensitive data and a Vulnerability profile to stop attempts to exploit system flaws or gain unauthorized access to systems.
Create a custom Security policy rule to control access to a GenAI app for specific users.For example, based on your investigation you discover that there are multiple unsanctioned GenAI apps with a large volume of data usage. This poses a security risk because there are users accessing an unapproved app on the network and you don't know what data is being downloaded or uploaded. Until you can perform proper due diligence to understand the GenAI app purpose and who is permitted to use the GenAI app, you can Block the GenAI app for all users.Conversely, you notice there are some Unsanctioned GenAI apps listed that but they are GenAI apps approved for use on your network by specific users with a large volume of data usage. In this case, you can change the tag to Sanctioned and write a policy rule to Allow usage of the app but only for users in specific roles or departments. In the policy rule you can associate an Enterprise Data Loss Prevention (E-DLP) data profile to prevent exfiltration of sensitive data and a Vulnerability profile to stop attempts to exploit system flaws or gain unauthorized access to systems.