AI Access Security
Enable the Gen-AI-Best-Practice Snippet
Table of Contents
Expand All
|
Collapse All
AI Access Security Docs
Enable the Gen-AI-Best-Practice Snippet
Associate the Gen-AI-Best-Practice snippet to implement out of the box best practices
for GenAI app adoption recommended by Palo Alto Networks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
And one of the following:
|
Activating
AI Access Security gives you access to the predefined
Gen-AI-Best-Practice
snippet. This snippet gives your
organization a starting point to implement Security policy rules that use best
practices for GenAI app adoption recommended by Palo Alto Networks. This snippet
allows you to quickly allow access to Sanctioned GenAI apps and blocks a wide
range of potentially risky GenAI apps by default. This helps your organization
maintain control over GenAI app usage while still enabling productivity-enhancing
tools. AI Access Security associates the
Gen-AI-Best-Practice snippet with the default
Global configuration folder by default.
Review the two Security policy rules associated with the predefined
Gen-AI-Best-Practice snippet for details about what
each includes.
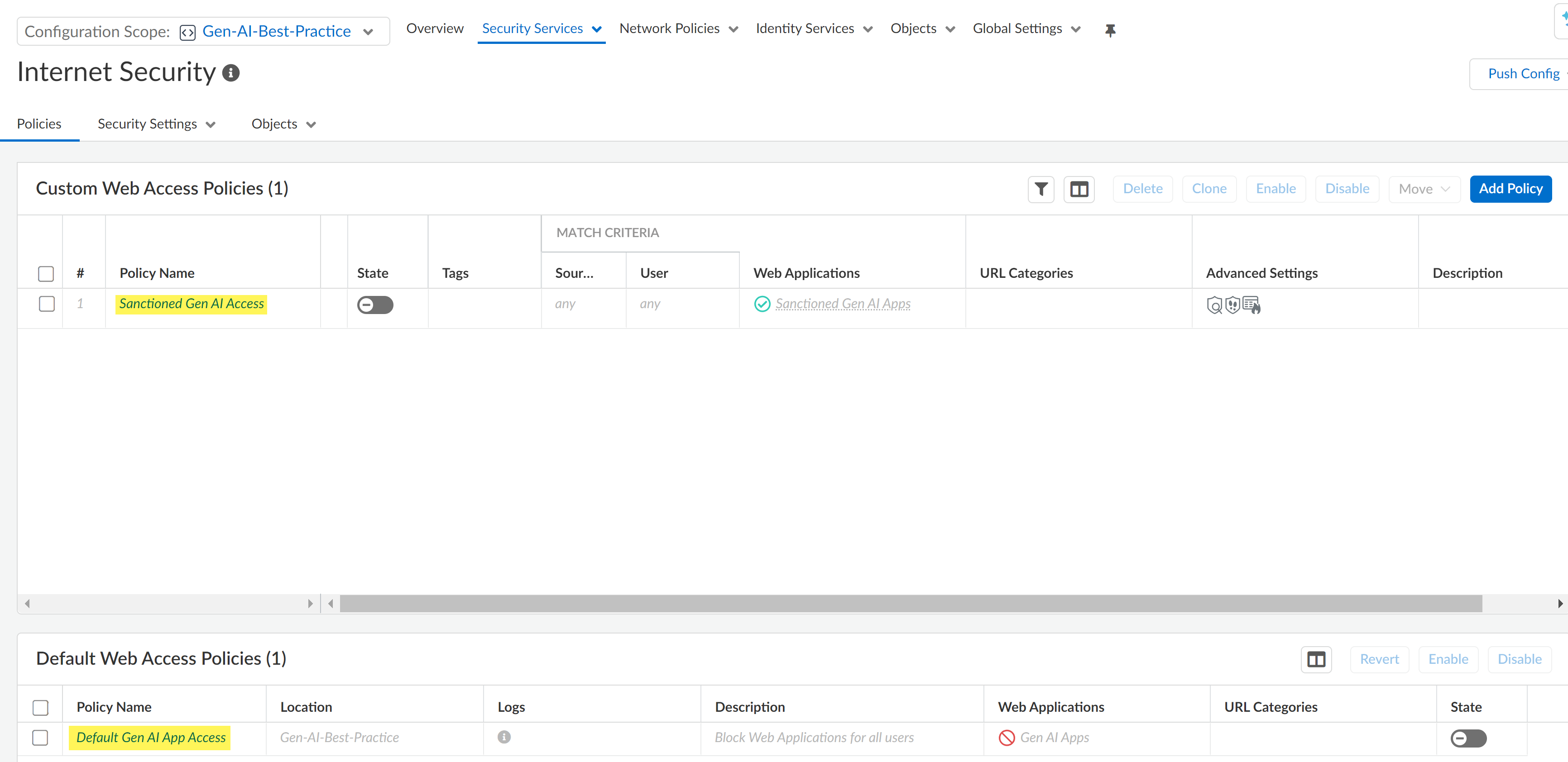
- Sanctioned GenAI AccessThe Sanctioned GenAI Access Security policy rule allows access to all GenAI apps classified as a Sanctioned app. The Sanctioned GenAI Access policy rule is part of the pre-rule rulebase so policy rule evaluation takes precedence over deployment-specific policy rules and the post-rule rulebase.
- Location—ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity PolicyInternet Security.
- Allows access to Sanctioned GenAI apps.
- Disabled by default. You need to manually enable this Security policy rule.
- Applies the predefined Sanctioned GenAI Apps application filter.This application filter groups GenAI apps based on their classification to dynamically enforce Security policy rules without the need to modify the Security policy rule.
- Applies to any source and destination address and user.
- Default GenAI App AccessThe Default GenAI Access Security policy rule blocks access to all GenAI apps classified not classified as a Sanctioned or Tolerated app. The Default GenAI App Access policy rule is part of the post-rule rulebase so policy rule evaluation occurs after deployment-specific policy rules and the pre-rule rulebase.
- Location—ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity PolicyInternet Security.
- Disabled by default. You need to manually enable this Security policy rule.
- Blocks access to Tolerated or Unsanctioned GenAI apps, or to any GenAI not explicitly allowed by a Security policy rule evaluated before the Default GenAI App Access policy rule in the policy rulebase hierarchy.
- The application filter groups GenAI apps based on the GenAI Apps classification tag to dynamically enforce Security policy rules without the need to modify the Security policy rule. All traffic from GenAI apps have this classification tag applied by default.
- Applies to any source and destination address and user.
Snippets are not available in Panorama. However, policies
within the snippet can be created on Panorama manually. Contact your account team
for more information.
- Log in to Strata Cloud Manager.Select ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity PolicyInternet Security.Toggle the setting in the State column for both the Sanctioned GenAI Access and Default GenAI App Access policy rules to enable.(Optional) Create and apply Security Profiles to the Sanctioned GenAI Access policy rule.Security Profiles allow you to apply additional security settings to allowed traffic to strengthen your security posture. For example, you can associate a DLP rule with the Sanctioned GenAI Access policy rule to prevent exfiltration of sensitive data to Sanctioned GenAI apps. Alternatively, you can use the AI Access Security Recommendations to enable your network security admins to quickly address gaps and strengthen your security posture when adopting GenAI apps.
