Configure 4G Subscriber ID Security
Table of Contents
11.0 (EoL)
Expand all | Collapse all
End-of-Life (EoL)
Configure 4G Subscriber ID Security
Secure your 4G traffic with Security policy rules that
specify source subscriber identifiers.
Configure network security based on the subscriber
identity of a user who is trying to access your 4G network.
Before
you begin configuring 4G Subscriber ID Security, gather
the IP addresses of the following devices in your topology so that
you can use them as source and destination addresses in Security
policy rules controlling traffic to and from these devices:
- eNodeB (eNB)
- Mobility Management Entity (MME)
- Serving Gateway (SGW)
- Packet Gateway (PGW)
- Enable GTP Security.
- Select DeviceSetupManagementGeneral Settings. Select GTP Security.Click OK.Commit the change.Select DeviceSetupOperations and Reboot Device.Enable inspection of 4G GTPv2-C control packets and content inspection of GTP-U packets; create a Mobile Network Protection profile.
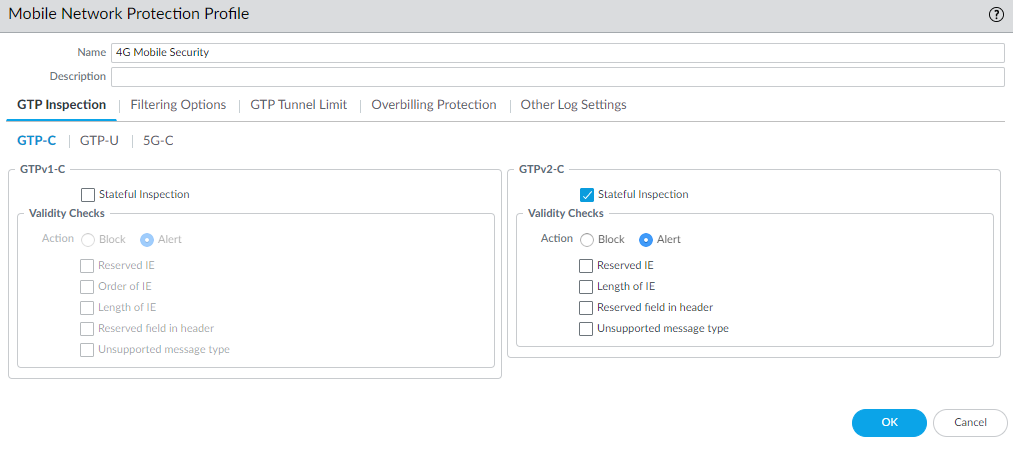
- Select ObjectsSecurity ProfilesMobile Network Protection.Add a profile by Name, for example, 4G Mobile security.Enter a Description.On the GTP Inspection tab, select GTP-C.Enable GTPv2-C Stateful Inspection to enable inspection of GTPv2 control packets.
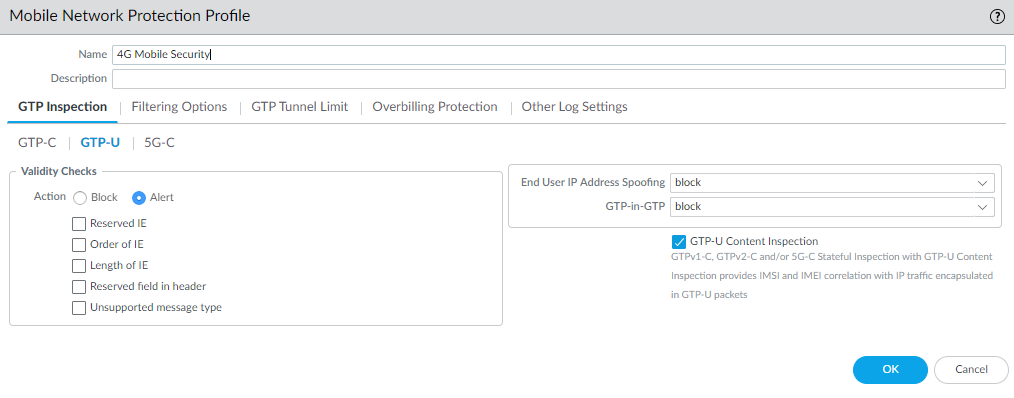
![]() Select GTP-U and enable GTP-U Content Inspection to correlate context from 4G GTPv2-C control packets (Subscriber IDs and Equipment IDs) to IP user traffic inside a GTP-U tunnel.
Select GTP-U and enable GTP-U Content Inspection to correlate context from 4G GTPv2-C control packets (Subscriber IDs and Equipment IDs) to IP user traffic inside a GTP-U tunnel.![]() Select Filtering Options and RAT Filtering; for example, you can allow UTRAN, GERAN, HSPA EVOLUTION, EUTRAN, EUTRAN-NB-IOT, and LTE-M and block other RATs.
Select Filtering Options and RAT Filtering; for example, you can allow UTRAN, GERAN, HSPA EVOLUTION, EUTRAN, EUTRAN-NB-IOT, and LTE-M and block other RATs.![]() (Optional) Select Other Log Settings and Log User Location.(Optional) To troubleshoot, select Other Log Settings and select GTPv2-C Allowed Messages for Tunnel Management, Path Management, and Others. You can also enable GTP-U Allowed Messages for Tunnel Management, Path Management, and G-PDU.Click OK.Create address objects for the IP addresses assigned to the network elements in your topology, such as in deployment option 1: the MME on the S11 interface, the eNB on the S1-U interface, and the SGW on the S1-U and S11 interface; or deployment option 2: the SGW on the S5/S8 interface and PGW on the S5/S8 interface.(Optional) Create an External Dynamic List (EDL) of Type Subscriber Identity List; the Source of the list provides access to a server that provides identifiers of users connected to the 4G network, for which you want to allow traffic.Create a Security policy rule that applies your Mobile Network Protection profile to application traffic.
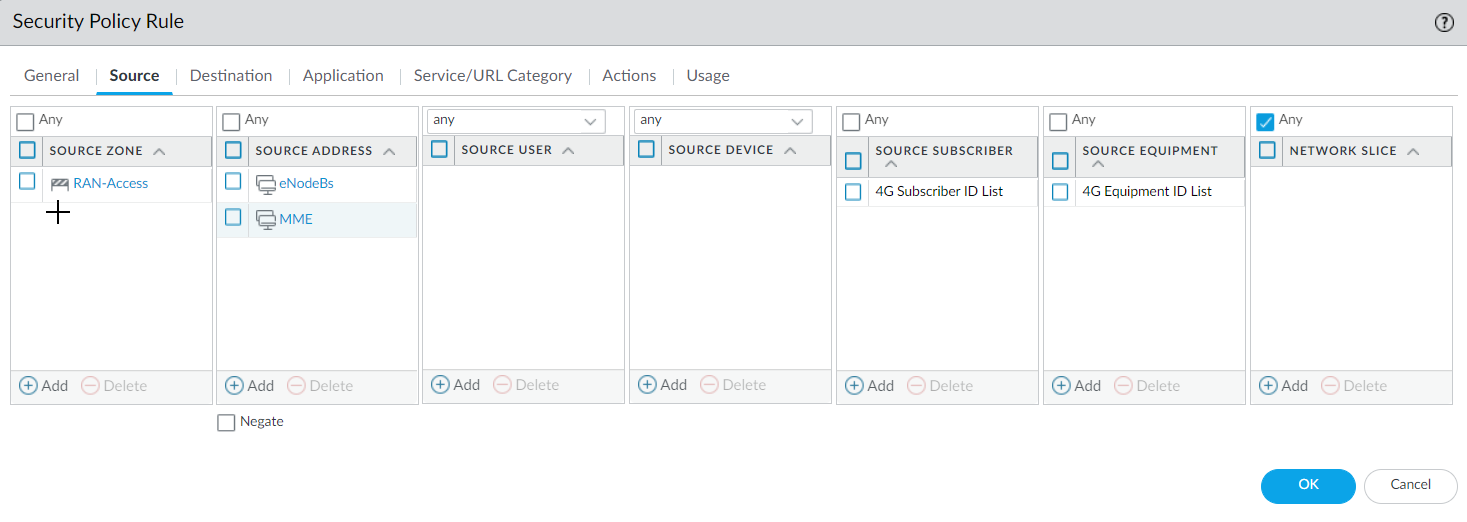
(Optional) Select Other Log Settings and Log User Location.(Optional) To troubleshoot, select Other Log Settings and select GTPv2-C Allowed Messages for Tunnel Management, Path Management, and Others. You can also enable GTP-U Allowed Messages for Tunnel Management, Path Management, and G-PDU.Click OK.Create address objects for the IP addresses assigned to the network elements in your topology, such as in deployment option 1: the MME on the S11 interface, the eNB on the S1-U interface, and the SGW on the S1-U and S11 interface; or deployment option 2: the SGW on the S5/S8 interface and PGW on the S5/S8 interface.(Optional) Create an External Dynamic List (EDL) of Type Subscriber Identity List; the Source of the list provides access to a server that provides identifiers of users connected to the 4G network, for which you want to allow traffic.Create a Security policy rule that applies your Mobile Network Protection profile to application traffic.- Select PoliciesSecurity and Add a Security policy rule by Name.Select Source tab and Add a Source Zone or select Any.For Source Address, Add the address objects for the 4G network elements that you want to allow.
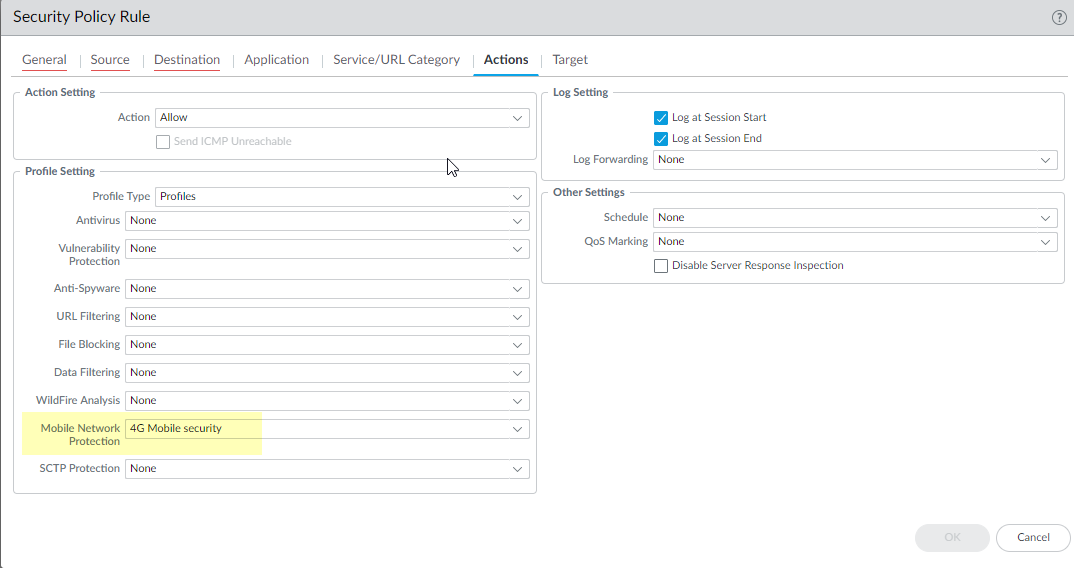
![]() For Destination, Add the Destination Address address objects for the 4G network elements that you want to allow.Add the Applications to allow, such as gtp-u for user plane and gtpv2-c for control plane traffic.On the Actions tab, select the Action, such as Allow.Select the Mobile Network Protection profile you created.
For Destination, Add the Destination Address address objects for the 4G network elements that you want to allow.Add the Applications to allow, such as gtp-u for user plane and gtpv2-c for control plane traffic.On the Actions tab, select the Action, such as Allow.Select the Mobile Network Protection profile you created.![]() Select Log Settings, such as Log at Session Start and Log at Session End.Click OK.Create another Security policy rule based on Subscriber ID.
Select Log Settings, such as Log at Session Start and Log at Session End.Click OK.Create another Security policy rule based on Subscriber ID.- Select PoliciesSecurity and Add a Security policy rule by Name, for example, Subscriber ID Security.Select Source tab and Add a Source Zone or select Any.Add one or more Source Subscriber IDs in any of the following formats (if you configured an EDL, specify that EDL in this step):
- IMSI (14 or 15 digits)
- Range of IMSI values separated by a hyphen. In a range, only the 11th digit through the 15th digit of the IMSI can change from the start of the range to the end of the range; for example, 111111111111122-111111111119999.
- IMSI prefix of six digits, with an asterisk (*) as the wildcard after the prefix; for example, 926789*
- External dynamic list (EDL) that specifies IMSIs
(Optional) You can add Source Equipment identities to this Security policy rule to make the rule more restrictive.Specify Destination Zone, Destination Address, and Destination Device as Any.Add the Applications to allow, for example, youtube, facebook, linkedin, and twitter.![]() On the Actions tab, select the Action, such as Allow.Select profiles you want to apply, such as Antivirus, Vulnerability Protection, and Anti-Spyware.Select Log Setting, such as Log at Session End.Click OK.Commit.
On the Actions tab, select the Action, such as Allow.Select profiles you want to apply, such as Antivirus, Vulnerability Protection, and Anti-Spyware.Select Log Setting, such as Log at Session End.Click OK.Commit.