HTTP/HTTPS Alerts
Table of Contents
Expand all | Collapse all
HTTP/HTTPS Alerts
HTTP and HTTPS alerts are notifications that AutoFocus
generates in JavaScript Object Notation (JSON) data format. In an
HTTP/HTTPS alert, information about the samples are formatted as
JSON name-value pairs separated by colons. For example, the name-value
pair date: 'March 19, 2016 05:56 PM' describes
the date and time that a sample was detected for the alert. All
alerts use the same set of field names, but their values vary depending
on the samples detected in the alert period.
You can configure AutoFocus HTTP/HTTPS alerts to send notifications
as plain text to a web server using standard HTTP requests or within
a secure communications channel using HTTPS requests. Additionally,
AutoFocus can authenticate a user on the web server receiving the
HTTPS alerts with basic user authentication, providing another layer
of security. All HTTPS requests use TLS 1.2 ciphers to negotiate
security settings.
Use HTTP alerts to publish information about
detected samples on a web page or a threat feed.
When creating an HTTP/HTTPS alert, provide the URL of a server
that has been preconfigured to parse the name-value pairs from the
alert. If you are configuring an HTTPS alert with basic authentication,
provide the user credentials of an account on the server receiving
the notifications. Refer to the following table of field names and
possible data types for the field values. The data type describes
how a value should be interpreted and stored by the server.
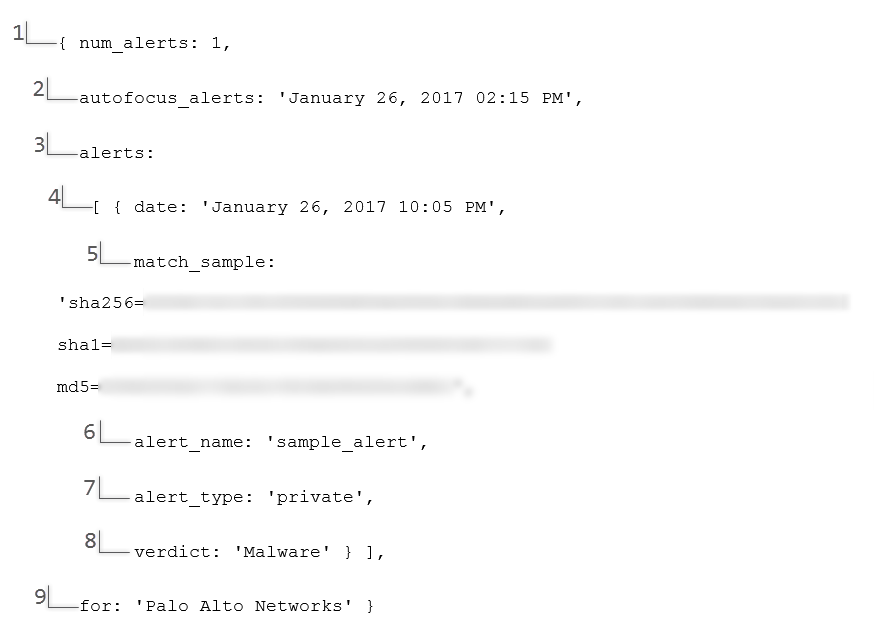
Field Name | Description | Data Type |
|---|---|---|
(1) num_alerts | The number of unique samples detected within
the alert period | number |
(2) autofocus_alerts | The date and time that the alert was sent
in the following format: Month DD, YYYY hh:mm [AM/PM] | string |
(3) alerts | A list of each sample detected and the details
associated with it | array |
(4) date | The date and time that the sample was detected
in the following format: Month DD, YYYY hh:mm [AM/PM] | string |
(5) match_sample | The SHA256, SHA1, and MD5 hashes of the sample | string |
(6) alert_name | The specific tag that triggered the alert
for the sample | string |
(7) alert_type | The tag type that triggered the alert. The different alert_type values
that can be displayed are:
| string |
(8) verdict | The WildFire verdict assigned to the sample: malware or grayware. To
focus your attention on samples that exhibit malicious behavior,
AutoFocus does not send alerts for benign samples. | string |
(9) for | The name of the support account that created
the alert | string |

