Strata Logging Service
Onboard Firewalls to Strata Logging Service
Table of Contents
Expand All
|
Collapse All
Strata Logging Service Docs
Onboard Firewalls to Strata Logging Service
Learn how to onboard firewalls to Strata Logging Service.
| Where Can I Use This? | What Do I Need? |
|---|---|
| One of these:
|
After activating Strata Logging Service license, the next step is to onboard
firewalls to Strata Logging Service. You must have a license to onboard firewalls
to your CSP account. You can also associate a Panorama device, Prisma Access to Strata Logging Service instance.
- Panorama- Palo Alto Networks firewalls send logs directly to Strata Logging Service. However, you can use Panorama™ to provision the certificates that firewalls need to securely connect to Strata Logging Service, configure device groups and templates with the right settings, and then push those settings to managed firewalls. When you’re done, you can use Panorama to view records for the logs that are stored in Strata Logging Service (or you can use the Explore app to view and interact with your logs). You can onboard up to 20 Panorama appliances to a Strata Logging Service instance.
- Prisma Access - Prisma Access stores logs in Strata Logging Service. If you’re using Prisma Access (Managed by Panorama), only one Panorama appliance that is managing Prisma Access can be associated with a Strata Logging Service instance at a time. If such a Panorama appliance is already associated with your instance when you add a Panorama appliance, you will not be able to select another appliance that is managing Prisma Access. If you're using Prisma Access (Managed by Strata Cloud Manager), associate Strata Cloud Manager to the Strata Logging Service instance.
Before you begin, ensure that you meet these requirements. You’ll need:
- A Panorama virtual appliance or hardware-based Panorama appliance running a supported PAN-OS version.
- A Panorama device management license.
- A supported version of the Cloud Services plugin.
- Next-generation firewalls with a valid support license that are managed by Panorama and that are running a supported PAN-OS version.
- A Strata Logging Service license (in addition to the device management license for Panorama). When you license Strata Logging Service, all firewalls registered to your support account receive a Strata Logging Service license. You can then use Panorama templates and device groups to configure the firewalls to forward logs to Strata Logging Service.The Strata Logging Service license provisions the service in one theater or region only. If you want the firewalls that belong to one template to send logs to one theater and the firewalls that belong to another template to send logs to a different theater, you need two Panorama appliances and two Strata Logging Service licenses.
- Consider that a Panorama™ appliance or firewall running PAN-OS® 9.1 and earlier versions cannot connect to Strata Logging Service from behind a proxy (Strata Logging Service requires mutual authentication). You can, however, enable proxy communication on PAN-OS 10.0 and later versions:
Panorama
This is how you onboard firewalls to Strata Logging Service using
Panorama.
If you’re using Panorama™ to manage Prisma Access or on-premises firewalls, you
have some preliminary steps to onboard Panorama to Strata Logging Service
If you are onboarding a Panorama in high availability mode (HA), follow the steps for configuring an HA Panorama with
Prisma Access. Instead of the step where you install the Prisma Access components on Panorama, follow the steps for activating Strata Logging Service below.
Install and Register Panorama
- To set up Panorama, install the Panorama virtual appliance and perform initial configuration or set up an M-Series appliance.Register Panorama and activate the support license.
- Log in to the Customer Support Portal (CSP) and select AssetsDevicesRegister New Device.Select Register device using Serial Number or Authorization Code and then Submit.Enter the Panorama Serial Number provided in the email you received with your order fulfillment along with the required Location Information (as indicated by the asterisks) and then Agree and Submit the EULA.After you see the registration complete message, close the Device Registration dialog.Find the Panorama instance you just registered and click the corresponding edit (Actions column).To activate the Support license, select Activate Auth-Code and then enter the Support Authorization Code you received in your email and then Agree and Submit.
Enable Communication between Panorama and Strata Logging Service
- On your firewalls, allow access to the ports and FQDNs required to connect to Strata Logging Service. If you are using a proxy server, allow the same ports and FQDNs on the server without SSL decryption.Ensure that you are not decrypting traffic to Strata Logging Service.(Optional) To configure firewall to connect to Strata Logging Service through a proxy server:
- On firewall, select DeviceSetupServicesUse proxy to send logs to Strata Logging Service
- On Panorama, select SetupServicesUse proxy to send logs to Strata Logging Service
Configure NTP so that the firewall stays in sync with Strata Logging Service. Ignore this step if you have enabled proxy configuration.- On the firewall, select DeviceSetupServicesNTP and set it to the same NTP Server Address you configured on Panorama. For example: pool.ntp.org.
By default, the management interface is used to forward logs to Strata Logging Service. If you choose not to use the management interface, use a data interface by configuring destination service routes for the following FQDNs: api.paloaltonetworks.com, apitrusted.paloaltonetworks.com, lic.lc.prod.us.cs.paloaltonetworks.com,certificatetrusted.paloaltonetworks.com, certificate.paloaltonetworks.com.- Select DeviceSetupServicesGlobal. Global on a firewall without multiple virtual system (multi-vsys) capability.
- Under Services Features, click Service Route Configuration and click Customize.
- Under Service, select the following:
- Palo Alto Networks Services
- CRL status
- DNS
- HTTP
- NTP
- Set Selected Service Routes.
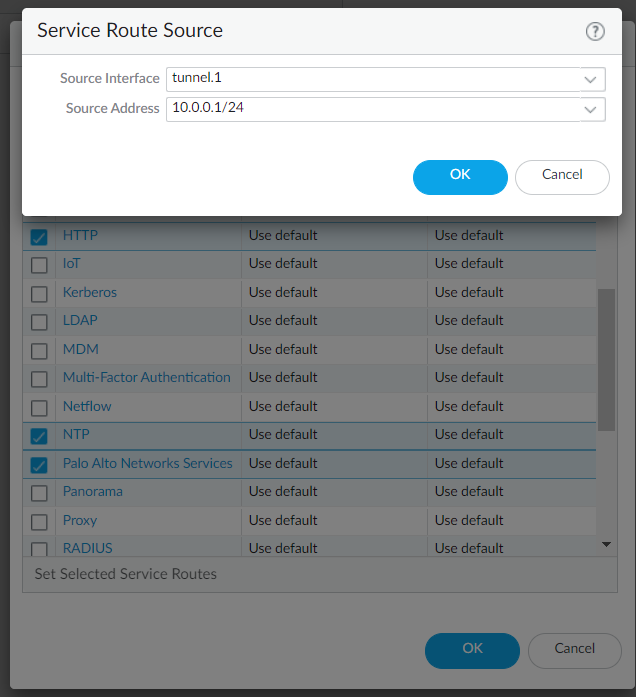
- Select the Source Interface you want to use for activation and then select a Source Address from that interface and click OK.
![]()
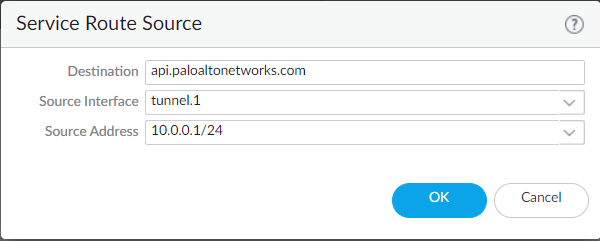
- Select Destination and Add a destination.
- Enter any of the FQDNs above as
Destination.
![]()
- Select the same Source Interface and Source Address that you selected for activation and click OK.
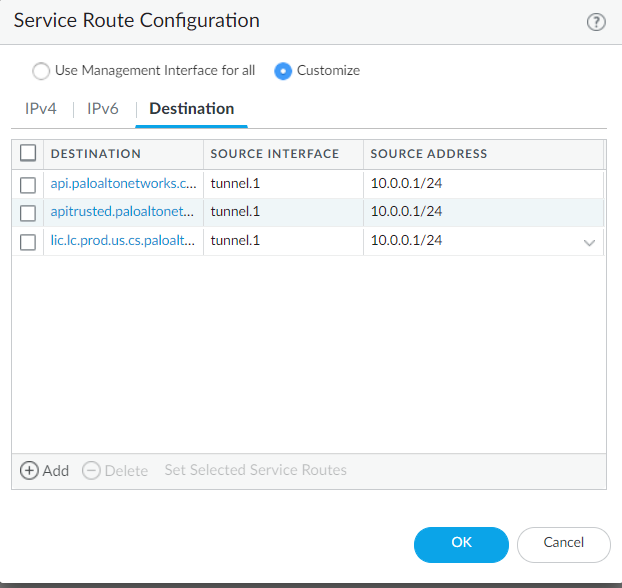
- Add two more destinations for the same
interface using the remaining two FQDNs.
![]()
- Click OK again to exit Service Route Configuration.
- Update the access rules required to connect to Strata Logging Service for the new interface IP address.
Install Device Certificate
- Install a device certificate for managed firewalls. If you're switching from Strata Logging Service certificate to device certificate, run the following command to restart the management server:
> debug software restart process management-server
- Restarting the management server process does not impact the packet forwarding except that the logged-in user will be signed out from the web interface and CLI.
- It's recommended to perform any process restart during nonpeak hours or during a maintenance window.
Add Panorama and Firewalls to Strata Logging Service
The procedure to add Panorama devices to your Strata Logging Service tenant depends on the device type and the Strata Logging Service license scheme you are using. You must have enough licenses to add devices to tenant.All the devices (except VM-Flex devices) are onboarded through the Device Associations page, which can be accessed in two ways:- From the standalone app Inventory menu
- From the Strata Cloud Manager System Settings > Device Associations menu.
Configure Panorama to Connect to Strata Logging Service
- Retrieve and push the Strata Logging Service licenses for managed firewalls. Ensure that you have subscribed to a valid support license of Strata Logging Service(90 days software warranty is not counted as a valid support license).
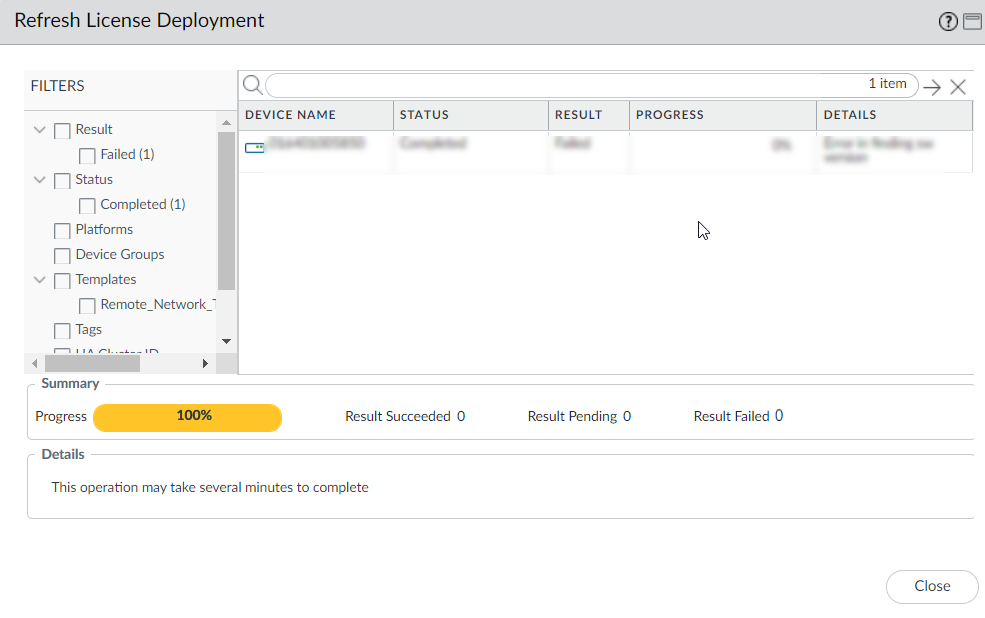
- From Panorama, select PanoramaDevice DeploymentLicense.First Refresh and then select the firewalls from the list. Panorama retrieves the licenses, deploys them to the selected firewalls, and updates the licensing status on the Panorama web interface. Make sure you see that Panorama successfully installed the Strata Logging Service license on the firewall.Do not Refresh again until the first refresh completes. When the refresh completes, you will see that Status shows Completed and Progress is 100%. There are also Details about whether the refresh succeeded.
![]() Download and install the Cloud Services plugin.You can either download the plugin from the CSP and then upload it to Panorama or you can check for plugin updates directly from Panorama as follows:
Download and install the Cloud Services plugin.You can either download the plugin from the CSP and then upload it to Panorama or you can check for plugin updates directly from Panorama as follows:- Select PanoramaPlugins and Check Now to display the latest Cloud Services plugin updates.
- Download a supported plugin version.Plugin 1.0 versions 1.0.x are no longer supported on any version of Panorama.
- After downloading the plugin, Install it.
Installing a newer version of the Cloud Services plugin overwrites the previously installed version. If you are installing the plugin for the first time, after you successfully install the plugin, Panorama will refresh and the Cloud Services menu will display on the Panorama tab.![]() Generate an OTP from the InventoryPanorama AppliancesGenerate OTP page in the Strata Logging Service app and copy it to your clipboard.You have ten minutes to enter the OTP before it expires.
Generate an OTP from the InventoryPanorama AppliancesGenerate OTP page in the Strata Logging Service app and copy it to your clipboard.You have ten minutes to enter the OTP before it expires.- Go back to Panorama and select PanoramaCloud ServicesStatus to display the Verify Account dialog.Paste the OTP you just generated and Verify it.If Verify is disabled, check that you have configured both a DNS server and an NTP server (PanoramaSetupServices).(Optional) If you have not created a template and a device group, from Panorama create a template and a device group to push log forwarding settings to the firewalls from which you want to forward logs to Strata Logging Service.Enable the firewalls in the template to send logs to Strata Logging Service and select the region where you want the logs stored.
- If some firewalls in your deployment are sending logs to dedicated Log Collectors or to Panorama with a local Log Collector, only firewalls that belong to the template with the Enable Strata Logging Service option selected can send logs to Strata Logging Service.
- You cannot onboard firewalls to send logs to Strata Logging Service hosted in China region.
- Select DeviceSetupManagement.Select the Template that contains the firewalls from which you want to forward logs to Strata Logging Service.Edit the Strata Logging Service settings.
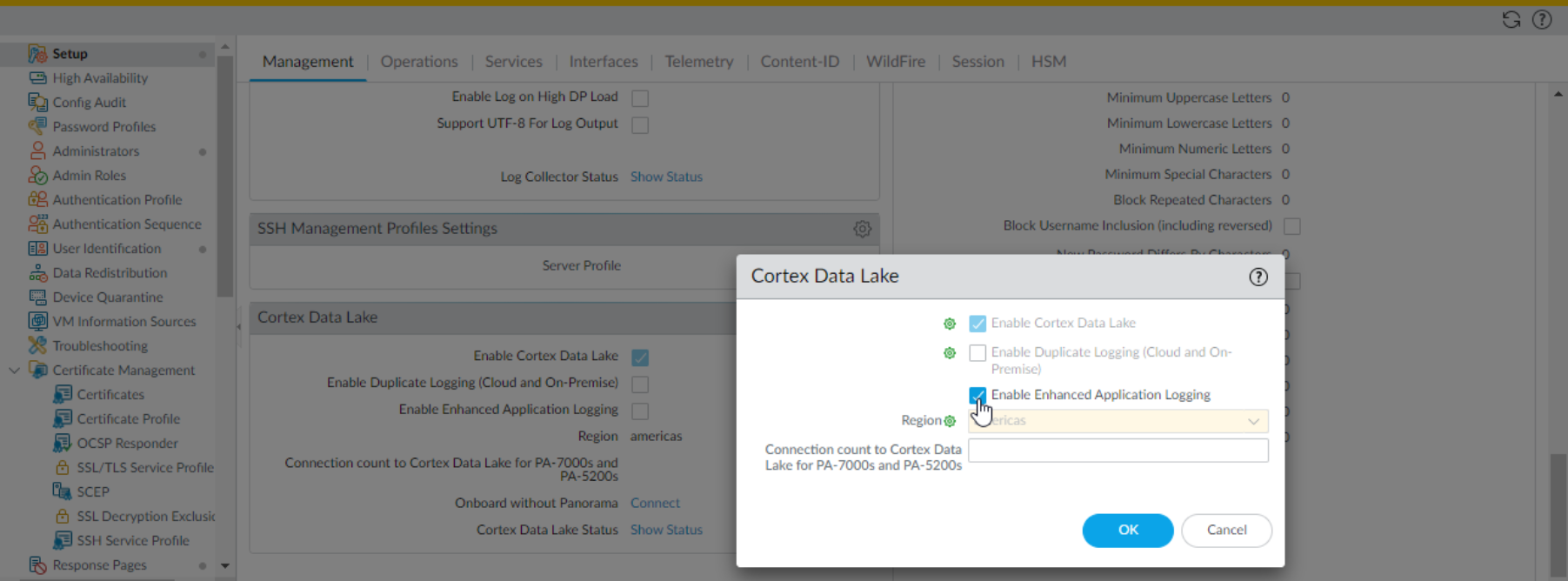
![]() Edit the Cloud Logging settings. Enable either of the two following options:
Edit the Cloud Logging settings. Enable either of the two following options:- Enable cloud logging—Send and save logs to Strata Logging Service only. With this option, use Explore or Panorama to see and interact with your log data.
- Enable duplicate logging (cloud and on-premise)—You can send and save logs both to Strata Logging Service and to your Panorama and log collection setup. Firewalls save a copy of all log data to both Panorama and Strata Logging Service except for system and config logs, which are sent to Panorama only.
To forward logs to Strata Logging Service with duplicate logging enabled, you must add the firewalls with the option enabled to a Collector Group.(Optional)Enable Enhanced Application Logging to allow the firewall to collect data for apps running the Palo Alto Networks Cloud Services environment. These logs provide Palo Alto Networks Cloud services apps increased visibility into network activity and, in some cases, are required to support app features.Select the Region where you want to forward logs for the firewalls associated with this template and then click OK.This region is not necessarily where your firewalls are located but the location of the Strata Logging Service instance. They will send logs to the region of the instance to which you onboarded them.The option to Onboard Without Panorama is used only for firewalls that are not managed by Panorama; there’s no need to populate it when you’re enabling Panorama-managed firewalls to forward logs to Strata Logging Service.Specify the Connection count to Strata Logging Service for PA-7000s and PA-5200s.Specify the number of connections that are established between the firewalls and Strata Logging Service for forwarding logs to Strata Logging Service (range is 1 to 20; default is 5).(Optional) Configure interfaces and zones in the template.Commit and push the configuration to the firewalls.Verify the Connection Status
- Firewall fetches a certificate automatically after pushing the configuration. To check the certificate status:
- On Panorama, click Panorama > Managed Devices > Troubleshooting > Test Cloud Logging Service Status.
- On firewall, click Device > Setup > Management and find the Cloud Logging > Show Status to check Strata Logging Service status.
- Run the command locally:
request logging-service-forwarding statusIf a certificate was not fetched for a firewall, run this command locally to fetch a certificate:request logging-service-forwarding certificate fetchVerify the connection status between Panorama and Strata Logging Service.You can use the Panorama CLI or the Panorama web interface with the Cloud Services plugin to verify that the connection is successful.
- Use the following CLI command:
admin@Panorama> request plugins cloud_services logging-service status
pass{"@status": "success", ..... - Select PanoramaCloud ServicesStatus and view details to verify that Panorama was able to successfully retrieve the Strata Logging Service certificate, fetch the Customer Identification number and the region in which your Strata Logging Service instance is deployed, and confirm that the Panorama appliance is connected to Strata Logging Service. If any of these checks fail, the Status is reported as an Error.
On the hub, View Strata Logging Service Status to verify that Strata Logging Service is provisioned successfully.
PAN-OS
Directly onboard your firewalls running PAN-OS to Strata Logging Service.Enable Communication Between Firewall and Strata Logging Service
- On your firewalls, allow access to the ports and FQDNs required to connect to Strata Logging Service. If you are using a proxy server, allow the same ports and FQDNs on the server without SSL decryption.Ensure that you are not decrypting traffic to Strata Logging Service.(Optional) To configure firewall to connect to Strata Logging Service through a proxy server, select DeviceSetupServicesUse proxy to send logs to Strata Logging Service.By default, the management interface is used to forward logs to Strata Logging Service. If you choose not to use the management interface, use a data interface by configuring destination service routes for the following FQDNs: api.paloaltonetworks.com, apitrusted.paloaltonetworks.com, lic.lc.prod.us.cs.paloaltonetworks.com,certificatetrusted.paloaltonetworks.com, certificate.paloaltonetworks.com.
- Select DeviceSetupServicesGlobal. Global on a firewall without multiple virtual system (multi-vsys) capability.
- Under Services Features, click Service Route Configuration.
- Select Customize.
- Under Service, select the following:
- Palo Alto Networks Services
- CRL status
- DNS
- HTTP
- NTP
- Set Selected Service Routes.
- Select the Source Interface you want to use for activation and then select a Source Address from that interface and click OK.
![]()
- Select Destination and Add a destination.
- Enter any of the FQDNs above as
Destination.
![]()
- Select the same Source Interface and Source Address that you selected for activation and click OK.
- Add two more destinations for the same
interface using the remaining two FQDNs.
![]()
- Click OK again to exit Service Route Configuration.
- Update the access rules required to connect to Strata Logging Service for the new interface IP address.
Configure NTP so that the firewall stays in sync with Strata Logging Service. Ignore this step if you have enabled proxy configuration:- On firewall, click DeviceSetupServicesand set the NTP Server Address. For example: pool.ntp.org.
![]()
Install Device Certificate
- Install a device certificate on the firewalls that you want to connect to Strata Logging Service. If you are switching from Strata Logging Service certificate to device certificate, run the following command to restart management-server:
> debug software restart process management-server
- Restarting the management server process does not impact the packet forwarding except that the logged-in user will be signed out from the web interface and CLI.
- It is recommended to perform any process restart during non-peak hours or during a maintenance window.
Add Firewalls to Strata Logging Service
The procedure to add firewalls to your Strata Logging Service tenant depends on the device type and the Strata Logging Service license scheme you are using. You must have enough licenses to add devices to tenant.All the devices (except VM-Flex devices) are onboarded through the Device Associations page, which can be accessed in two ways:- From the standalone app Inventory menu
- From the Strata Cloud Manager System Settings > Device Associations menu.
Configure Firewalls to Connect to Strata Logging Service
- Select DeviceLicenses and confirm that the Strata Logging Service license is active. Ensure that you have subscribed to a valid support license of Strata Logging Service(90 days software warranty is not counted as a valid support license).When you purchased your Strata Logging Service license, all firewalls registered to your support account received a Strata Logging Service license. If you don’t see the Strata Logging Service license, Retrieve license keys from license server to manually refresh the firewall licenses.Set up the connection to Strata Logging Service and check connection status:
- Select DeviceSetupManagement and find the Cloud Logging settings.Enable Cloud Logging to connect the firewall to Strata Logging Service. If you want the firewall to collect data that increases visibility for Palo Alto Networks applications, you can also Enable Enhanced Application Logging.Strata Logging Service logging doesn’t start until after you’ve specified the log types you want to forward. Complete these steps and then start sending logs to Strata Logging Service.Do not Enable Duplicate Logging. This option applies only to Panorama-managed firewalls.Select the Region where you want to forward logs for the firewalls associated with this template and then click OK.This region is not necessarily where your firewalls are located but the location of the Strata Logging Service instance. They will send logs to the region of the Strata Logging Service instance to which you onboarded them.Specify the Connection count to Strata Logging Service for PA-7000s and PA-5200s.Specify the number of connections that are established between the firewalls and Strata Logging Service for forwarding logs to Strata Logging Service (range is 1 to 20; default is 5).Commit and push the config to firewalls.Click DevicesSetupManagementCloud LoggingShow Status to check the connection status. The status for License, Certificate, and Customer Info should be green.You can also use this command to check the certificate status along with other details related to Strata Logging Service:request logging-service-forwarding status
Verify the Connection Status
- Firewall fetches a certificate automatically after pushing the configuration. To check the certificate status:
- On firewall, click Device > Setup > Management and find the Cloud Logging > Show Status to check Strata Logging Service status.
- Run the command locally:
request logging-service-forwarding statusIf a certificate was not fetched for a firewall, run this command locally to fetch a certificate:request logging-service-forwarding certificate fetchOn the hub, View Strata Logging Service Status to verify that Strata Logging Service is provisioned successfully.
Strata Cloud Manager
This is how you onboard firewalls to Strata Logging Service using Strata Cloud Manager.- On your firewalls, allow access to the ports and FQDNs required to connect to Strata Logging Service. If you are using a proxy server, allow the same ports and FQDNs on the server without SSL decryption.Ensure that you are not decrypting traffic to Strata Logging Service.To onboard firewalls to Strata Cloud Manager, install device certificate for firewalls to connect to Strata Logging Service.Onboard the firewalls to a Strata Logging Service instance.Click Strata Cloud ManagerSystem SettingsStrata Logging ServiceOverview to verify that Strata Logging Service is provisioned successfully for the firewalls.Forward logs from firewalls managed by Strata Cloud Manager to Strata Logging Service. Firewalls that are managed by Strata Cloud Manager, will automatically get default Log forwarding profiles to Strata Logging Service and have Cloud logging enabled.