Strata Logging Service
New Features in Strata Logging Service
Table of Contents
Expand All
|
Collapse All
Strata Logging Service Docs
New Features in Strata Logging Service
Here are the new features in Strata Logging Service.
Welcome to Strata Logging Service! Strata Logging Service centralizes log
collection from cloud apps, firewalls (on-prem, public, private), and Prisma Access.
With a cloud-based infrastructure available across multiple regions, it integrates
seamlessly with Panorama, allowing you to view firewall logs in one place.
Here's an overview of the new features introduced to enhance your logging capabilities
within Strata Logging Service.
Manage Log Storage in Strata Cloud Manager
|
February, 2026
|
Strata Cloud Manager® now provides a streamlined way to manage firewall log
storage through the Device Associations page. This update
centralizes onboarding and storage management, ensuring a more efficient
administrative experience.
Streamlined Log Retention Management
|
February, 2026
|
Strata Cloud Manager® now provides a simplified way to manage log retention through 6 predefined
time period options. This update improves administrative efficiency by replacing
custom day-range entries with standard, optimized configurations. To ensure a
seamless transition, the system automatically migrates your existing custom
retention settings to the closest available predefined option. Once you select
an option, the system automatically purges logs after the specified period.
SaaS Security Logs
|
November, 2025
|
SaaS Security log types are now centrally routed to Strata Logging Service, offering unified visibility for SaaS applications and streamlining security
configurations. The following log type is introduced in SaaS Security:
Detection Logs
Detection logs record the results of security detectors running on agents during
scheduled scans. These logs capture and store specific security detections,
significantly enhancing the ability to monitor and investigate SaaS application
security posture. The logs provide critical security insights, detailing the
application, the type of detector triggered, and a risk score to prioritize
vulnerabilities.
See the Log Reference for more information
about the Detection log fields.
SD-WAN Traffic Logs
|
November, 2025
To view the SD-WAN Traffic logs, you must
have an active Prisma SD-WAN SLS license.
|
Prisma SD-WAN now offers the capability to log traffic and security records to
Strata Logging Service, enabling centralized log visibility across
NGFW, Prisma Access, and Prisma SD-WAN. This capability unifies logs for
efficient security operations and also powers the Activity
Insights dashboards delivering a comprehensive network and
security visibility.
The logs provide a record of network activity, showing what's happening across
the Prisma SD-WAN fabric. Each entry details the security action taken, the
specific application or service, relevant user information, and network
characteristics (e.g., IP addresses and ports).
See the Log Reference for more information
about the SD-WAN Traffic log fields.
SLS Log Export for China
|
November, 2025
|
You can now export retrieved log records directly from the Explore or Log Viewer interface in the
Strata Logging Service from the China region. Previously, enterprise customers
with globally distributed tenants could not export logs from their China-based
environments for external processing.
Use the Explore tab to view and interact with logs. You can
retrieve desired log records using the query builder and time-range filters.
Once the records are ready, you can export them to a compressed CSV file
in GZ format and save it to your downloads folder. Exported logs are always in
UTC time. The columns in the CSV file are named according to the field names
used in queries (e.g., dest_user), not the column headers. Exports are limited
to a maximum of 1.5 million rows or 1 GB of total data. For larger datasets,
refine your query to return fewer records.
Log Viewer Enhancements in Strata Logging Service
|
August, 2025
|
The Log Viewer in Strata Logging Service is now enhanced
to improve both query performance and user experience by limiting predefined and
custom time ranges to a maximum of 30 consecutive days. While you can still
access logs going back up to a year in history, your selected range must not
exceed this 30-day limit.
This change streamlines the log viewer for immediate troubleshooting, as our data
shows that the 60- and 90-day options are accessed far less frequently. If you
previously had one of the longer ranges selected, the system will automatically
default to Past 60 minutes on your next visit. For
getting logs out of the system for long-term log analysis and compliance
purposes, we recommend using the log forwarding feature, which handles
large datasets more efficiently.
Migration of Existing Strata Logging Service License to New License
|
March, 2025
|
If you currently use Strata Logging Service
licenses with predefined, sized storage,
you can now gain greater flexibility in managing long-term data retention and
storage limits. Starting from March 2025, Palo Alto Networks is simplifying this
process by automatically migrating all existing Strata Logging Service licenses to a
new model.
This new license model provides unlimited storage and a guaranteed one year log
retention period. The migration preserves your existing entitlements while enabling
you to take advantage of these updated capabilities like expanded log retention.
The automatic migration occurs at the Customer Support Portal account level, with
different paths based on your current End-Of-Sale (EoS) licensed products. You
will receive a notification before and after the migration is complete for your
tenants. If you are already using our new Strata Logging Service licensing
model, there is no change for you.
Log Forwarding from Strata Logging Service in China to AWS S3 Storage
|
November, 2024
You can now forward logs from Strata Logging Service
deployed in China to the external AWS S3 storage hosted in China
or Singapore region.
|
Organizations operating in China face strict data residency and compliance
requirements for security logs. To support your legal compliance needs and
streamline log management, Strata Logging Service hosted in China now enables
forwarding firewall logs stored locally to
external destinations for long-term storage, monitoring, and analysis. Log
forwarding allows you to export logs to an external destination to support your
organization’s legal compliance requirements. Configure Strata Logging Service to
forward logs to a syslog server, HTTPS server, email server, or a third-party SIEM
in multiple formats. You can also set the
type of logs you want to forward and apply filters to specify precisely which logs
are forwarded to the destination server. During configuration, be aware that sending
logs to servers outside China requires acknowledging that personally identifiable
information may leave the country.
New License for Strata Logging Service
|
October, 2024
|
Strata Logging Service now supports a new license tier that comes with one year
of log retention and unlimited storage space for logs. The new license tier
simplifies the complexities involved in estimating the sizing requirement for your
deployment. The new license tier is applicable only to first time users of Strata Logging Service. The existing users of Strata Logging Service
license with sized storage can retain their current license without any impact and
can continue to amend, extend, or renew. You can purchase the new license separately
as a standalone Strata Logging Service license. If you are managing your Palo
Alto Networks products using Strata Cloud Manager, you can opt for the new license tier of Strata Cloud Manager
that includes the new Strata Logging Service license.
Centralized Device Onboarding to Strata Logging Service
|
October, 2024
|
Previously, managing devices across different management interfaces introduced
inconsistency during device onboarding. Now, you can use centralized Device Associations management to
streamline this workflow and gain a unified view of all onboarded devices. This
feature allows you to quickly add firewall and Panorama® devices
to a tenant service group (TSGs) and
automatically associate them with Strata Logging Service. The centralized
Device Associations management view ensures a more efficient and consistent
onboarding experience, regardless of whether you onboard a device from the Strata Logging Service standalone app or from Strata Cloud Manager. This
approach provides a consistent experience of onboarding devices across various Palo
Alto Networks products.
Log Forwarding Support for Amazon Security, AWS S3, and Snowflake
|
August, 2024
You can now forward events and audit browser logs in Strata Logging Service to external security data storage
services like Amazon Security Lake, AWS S3, and Snowflake. To
enable this, create a log forwarding profile in either a
standalone Strata Logging Service instance or Strata Cloud Manager. Strata Logging Service forwards
logs to Amazon Security Lake in PARQUET format and to AWS S3 and
Snowflake warehouse in JSON format.
|
Prisma Access Secure Enterprise Browser Logging
|
August, 2024
You can view Prisma Access Secure
Enterprise Browser logs in Explore and Log Viewer. See the
Log Reference for more
information about the log fields.
|
The Prisma Access Secure Enterprise Browser (Prisma
Access Browser) is a browser designed specifically for enterprise use and
is fortified with security features to protect users and organizations against
cyberthreats like phishing, malware, eavesdropping, and data exfiltration.
The initial release of Prisma Access Browser includes the following:
- Third-Party Access: contractors, partners, consumers, or students needing secure access to SaaS or private web apps on their unmanaged devices.
- Bring Your Own Device Access: employees using personal devices (mostly mobile) for work.
- Temporary Secure Access: employees needing access to critical apps, such as Human Resources and Payroll, during agent rollouts or network merges.
- Secure Access for managed devices: employees using work devices accessing highly sensitive data.
AI Runtime Security Logging
|
July, 2024
You can view AI Runtime Security logs in Explore and Log Viewer. See the
Log Reference for more
information about the log fields.
Log Forwarding is
not supported for AI Security logs. |
Prisma AIRS helps you to discover, protect, and
defend your enterprise traffic flows against all potential threats by including a
focus on addressing AI-specific vulnerabilities such as prompt injection, and
denial-of-service (DoS) attacks on AI models. Prisma AIRS
combines continuous runtime threat analysis of your AI applications, models, and
data sets with AI powered security to stop attackers in their tracks. Prisma AIRS leverages real-time AI-powered security to
protect your AI application ecosystem from both AI-specific and conventional network
attacks.
Prisma AIRS leverages critical anomaly detection
capabilities to protect AI models from manipulation and to ensure the reliability
and integrity of AI output data. It rejects prompt injections, malicious responses,
training data poisoning, malicious URLs, command and control traffic, embedded
unsafe URLs, and lateral threat movement.
Prisma AIRS uses Palo Alto Networks Strata Cloud
Manager (SCM) as the primary configuration and management service. To begin with,
activate and onboard your cloud service
provider account on SCM. The AI Security Profile imports security capabilities from
Enterprise DLP and URL Filtering for inline detection of threats in AI application
traffic.
Prisma AIRS is powered by four key components:
- Discover- Prisma AIRS automatically discovers your enterprise AI applications and non-AI applications. The Prisma AIRS dashboard provides complete visibility and security insights for applications in just a few clicks. You can use the dashboard to review actionable intelligence on AI traffic flows covering your applications, models, user access, and infrastructure threats.
- Deploy- Prisma AIRS deployment using Terraform templates automates the deployment procedure, which lowers the human error, lowering the time required for manual configuration tasks and for protecting your enterprise AI applications. Deploy your Prisma AIRS instance by downloading the Terraform templates and permissions to your cloud service provider account projects to analyze flow logs and DNS logs.
- Detect- Prisma AIRS identifies unprotected traffic flows that contain potential security threats to the cloud network and detect the potential security risks based on logs and recommended actions for remediation.
- Defend- Prisma AIRS shields your organization’s AI application ecosystem from AI-specific and conventional network attacks by leveraging real-time AI-powered security. This will provide you with continuous discovery of the AI network traffic on your containers and namespaces.
Local Deep Learning for Advanced Threat Prevention Logging
|
July, 2024
You can view Local Deep Learning log in Explore and Log Viewer. See the
Log Reference for more
information about the log fields.
|
When handling high volumes of evasive threats or operating under challenging network
conditions, relying solely on cloud-based threat analysis can introduce unwanted
latency. Local Deep Learning for Advanced Threat
Prevention solves this challenge by providing fast, local deep
learning-based analysis for zero-day threats, complementing the cloud-based Inline Cloud Analysis
component of Advanced Threat Prevention.
With an active Advanced Threat Prevention license, the system quickly analyzes known
malicious traffic matching published signatures and applies the configured action,
such as dropping the session. For suspicious content, the Deep Learning Analysis
detection module reroutes the traffic locally for immediate analysis. Because this
module is based on the proven detection engines operating in the Advanced Threat
Prevention cloud, you gain the same zero-day and advanced threat detection
capabilities, but with the added benefit of processing a much higher traffic volume
locally. This allows you to inspect more traffic and receive rapid verdicts without
the lag associated with cloud queries. Content updates deliver the latest Local Deep
Learning models, ensuring your detection remains current.
Strata Logging Service in Strata Cloud Manager
|
June, 2024
In addition to the Strata Logging Service app available in
the hub to manage your instances, you can now also use Strata Cloud Manager to manage your Strata Logging Service instances.
Supported on Strata Cloud Manager with Strata Logging Service
license.
Strata Cloud Manager is not available to you to manage Strata Logging Service instances hosted in China or in
FedRAMP high regions. Continue to use the Strata Logging Service app to manage the instances in
these regions. |
You can now manage your Strata Logging Service instance with Strata Cloud Manager. The Strata Logging Service integration in Strata Cloud Manager provides a
single, unified interface to manage your log data, enhances operational efficiency
and compliance across your entire environment. This centralized management
capability allows you to:
- Gain unified visibility and onboard firewalls, Cloud NGFW, Prisma Access, or Panorama appliances
- View the allocated log storage quota, available storage space, and the number of days logs are retained
- Centrally configure log storage quota and retention policies
- Search, filter, and export log data directly from Strata Cloud Manager
- Forward log data to external servers for long-term storage, SOC, or internal audit
This integration ensures that you can efficiently monitor your log status and manage
data forwarding without switching between applications.
Log Forwarding from Strata Logging Service in China
|
May, 2024
You can forward firewall logs stored in Strata Logging Service hosted in China to external
destinations. Contact Palo Alto Networks to enable log
forwarding from Strata Logging Service China. In
addition, while configuring log forwarding
profiles acknowledge the notice that sending logs to
servers outside China can result in personally identifiable
information leaving China.
|
Organizations operating in China face strict data residency and compliance
requirements for security logs. To support your legal compliance needs and
streamline log management, Strata Logging Service hosted in China now enables
forwarding firewall logs stored locally to
external destinations for long-term storage, monitoring, and analysis. Log
forwarding allows you to export logs to an external destination to support your
organization’s legal compliance requirements. Configure Strata Logging Service to
forward logs to a syslog server, HTTPS server, email server, or a third-party SIEM
in multiple formats. You can also set the
type of logs you want to forward and apply filters to specify precisely which logs
are forwarded to the destination server. During configuration, be aware that sending
logs to servers outside China requires acknowledging that personally identifiable
information may leave the country.
Cortex Data Lake is Now Strata Logging Service
|
April, 2024
Strata Logging Service is the new name for the cloud-based
logging infrastructure that was previously called Cortex Data
Lake.
|
View Only Administrator User Role Support for Strata Logging Service
|
April, 2024
In addition to these user roles, Strata Logging Service now supports a View Only
Administrator role that provides read-only access to all
available system-wide functions in Strata Logging Service.
|
New Region Support: Saudi Arabia
|
March, 2024
You can now host Strata Logging Service in the Saudi
Arabia region. Refer to the region support
information before you set a host region when you activate Strata Logging Service.
|
You can host Strata Logging Service in multiple regions. To comply with data
privacy regulations that require you to keep data within a specific region, you can
select it as a host region when you activate Strata Logging Service. Strata Logging Service ensures data redundancy by storing your data in two
different zones in the region you choose. Therefore, in case of an outage, Strata Logging Service will failover to the secondary zone in an attempt to
prevent interruption of service. If you integrate a third-party application to
ingest your log data, ensure the third-party application supports the same
geographical region as your Strata Logging Service instance. This regional
alignment is crucial to prevent interruption of service and guarantee successful
access to your data. Here is the list of new regions supported for Strata Logging Service and their corresponding release dates:
- Saudi Arabia (March 2024)
- Korea (November 2023)
- Israel (November 2023)
- Indonesia (November 2023)
- United States Government (High) (November 2023)
- Poland (July 2023)
New Log Field Names
|
January, 2024
|
To simplify your logging experience, some log field names have changed. These
changes will affect how field names appear and how they are forwarded. To ensure a
smooth transition for your log forwarding profiles, support for the old names will
continue for the near future. Fields will be forwarded with both the new names and
old names, so you can choose whether to leverage the new names or continue with your
current configurations. Therefore, no action is required to maintain log
forwarding functionality.
References to logs that were forwarded
before these changes must use the old names.
Query Usability and Performance Enhancements in Explore
|
January, 2024
|
To maximize the efficiency of your log analysis and ensure comprehensive
visibility across all regions, Explore/ Log Viewer now provide advanced
query management and performance capabilities. Slow or complex queries no longer
consume unnecessary time or system resources. You can now abort long-running
queries, giving you direct control over execution time and minimizing resource
consumption. Furthermore, the query response time is improved, enabling rapid
exploration of vast log data sets. This feature also provides critical access to
view logs from Strata Logging Service hosted in the China region, ensuring
full regulatory and operational coverage for your global deployments. These
capabilities together accelerate your ability to analyze data and respond to threats
efficiently.
Forward Past Logs With Log Replay
|
January, 2024
|
Log replay profiles allow you to forward
past-dated logs (up to the past 3 days) from Strata Logging Service to
syslog, HTTPS, or email servers. This option is used to retrieve old logs in case of
connection failures or outages at the destination server.
To create the log replay profile:
- Clone the parameters from an existing log forwarding profile.
- Provide the specific date range for which logs must be forwarded.
Once created, the log replay profile can't be modified. Also, any changes made to the
existing log forwarding profile used to create the replay profile don't impact the
replay profile. The devices generating logs, such as NGFWs and Prisma Access, must
be forwarding logs to Strata Logging Service.
New Region Support: Korea, Israel, Indonesia, and United States Government (High)
|
November, 2023
You can now host Strata Logging Service in Korea, Israel,
Indonesia, and United States Government (FedRAMP high) regions.
Refer to the region support
information before you set a host region when you activate Strata Logging Service.
|
You can host Strata Logging Service in multiple regions. To comply with data
privacy regulations that require you to keep data within a specific region, you can
select it as a host region when you activate Strata Logging Service. Strata Logging Service ensures data redundancy by storing your data in two
different zones in the region you choose. Therefore, in case of an outage, Strata Logging Service will failover to the secondary zone in an attempt to
prevent interruption of service. If you integrate a third-party application to
ingest your log data, ensure the third-party application supports the same
geographical region as your Strata Logging Service instance. This regional
alignment is crucial to prevent interruption of service and guarantee successful
access to your data. Here is the list of new regions supported for Strata Logging Service and their corresponding release dates:
- Saudi Arabia (March 2024)
- Korea (November 2023)
- Israel (November 2023)
- Indonesia (November 2023)
- United States Government (High) (November 2023)
- Poland (July 2023)
Remote Browser Isolation Logging
|
November, 2023
You can view Remote Browser Isolation logs in Explore and Log Viewer. See the Schema Reference
for more information about the log fields.
|
Browser and web-based attacks are continuously evolving, resulting in security
challenges for many enterprises. Web browsers, being a major entry point for malware
to penetrate networks, pose a significant security risk to enterprises, prompting
the increasing need to protect networks and devices from zero day attacks. Highly
regulated industries, such as government and financial institutions, also require
browser traffic isolation as a mandatory compliance requirement.
While most enterprises want to block 100% of attacks by using network security and
endpoint security methods, such a goal might not be realistic. Most attacks start
with the compromise of an endpoint that connects to malicious or compromised sites
or by opening malicious content from those sites. An attacker only needs one miss to
take over an endpoint and compromise the network. When this happens, the
consequences of that compromise and the impact to your organization can be
damaging.
Remote Browser Isolation (RBI) creates a safe isolation
environment for your users' local browsers, preventing website code and files from
executing on their local browser. Unlike other isolation solutions, RBI uses
next-generation isolation technologies to deliver near-native experiences for users
accessing websites without compromising on security.

RBI is a service that transfers all browsing activity away from your users' managed
devices and corporate networks to an outside entity, such as Prisma® Access, which
securely isolates potentially malicious code and content within its platform.
Natively integrated with Prisma Access, RBI allows you to apply isolation profiles
easily to existing security policies. Isolation profiles can restrict many user
controls such as copy and paste actions, keyboard inputs, and sharing options like
file uploading, downloading, and printing files to keep sensitive data and
information secure. All traffic in isolation undergoes analysis and threat
prevention provided by Cloud-Delivered Security Services (CDSS), ensuring robust
security before content reaches the user.
Query Usability Enhancements
|
September 15, 2023
|
Searching and analyzing large volumes of relevant logs can be time-consuming. To help
you quickly investigate security events and streamline log analysis, 's
Log Viewer now includes advanced filtering
and viewing capabilities.
These enhancements simplify query construction and ensure you can search and view
relevant logs easily. The query builder provides autosuggestions most relevant to
your search string and suggests all supported values for fields to refine your query
precisely. You can search field names using substrings (for example, search with the
string ‘user’ returns suggestions such as source_user and destination_user).
Additionally, you can create a query using both the display name shown in the log
table and the actual field name in the log record.
All Previous New Features
|
Feature
|
Description
|
|---|---|
| Dynamic Sizing for Cloud NGFW for
AWS August 2023 |
To simplify storage allocation for your Cloud NGFW for AWS
resources, Strata Logging Service now automatically
scales your total allocated storage according to your Cloud NGFW
usage. As traffic throughput increases on the Cloud NGFW
resources, so does your available storage so that you don’t need
to worry about making manual adjustments for Strata Logging Service to save your log data.
|
| HTTPS Log Forwarding to
Exabeam August 2023 |
Strata Logging Service now supports forwarding logs to Exabeam
using HTTPS, so if you use Exabeam as your SIEM, you
can now seamlessly ingest firewall data from Strata Logging Service for a more complete picture of
your network activity.
|
| Log Forwarding Java 11
Upgrade August 2023 |
For more up-to-date and secure authentication, Log Forwarding now
uses Java 11. Please review the updated list of trusted
certificates to ensure your log receiver has the
correct certificates installed.
|
| Poland Regional Support July
2023 |
To comply with data privacy regulations that require you to keep
data within Poland, you can now select it as a host region when you
activate Strata Logging Service.
|
| Cloud NGFW for Strata Logging Service
Inventory Page Update July 2023 |
Strata Logging Service now displays key metrics for
your Cloud NGFWs to help you better monitor
ingestion rate, storage usage, and connection status for your
deployment.
|
| New Log Field for Cloud NGFW
Resources July 2023 | Strata Logging Service has a new log field (log_source_group_id) that identifies the Cloud NGFW resource to which your Cloud NGFWs belong. With this field, you can perform Explore/Log Viewer queries to zero in on logs generated by a specific Cloud NGFW resource. |
| Audit Logs for Cisco Meraki Integration with Prisma
Access May 2023 | To monitor the operation of your Prisma Access integration with Meraki SD-WAN, you can now view and query Audit logs stored in Strata Logging Service using Explore in the Strata Logging Service app or Log Viewer in other apps. These logs provide context for every Meraki configuration change executed through the Prisma Access integration, including such information as date and time of the change, the admin who performed it, and any errors or warnings encountered. |
| China Regional Support April
2023 |
To comply with data privacy regulations that require you to keep
data within China, you can now select it as a host region when you
activate Strata Logging Service.
|
| France Regional
Support February 2023 |
To comply with data privacy regulations that require you to keep
data within France, you can now select it as a host region when you
activate Strata Logging Service.
|
| Strata Logging Service Alerts in
AIOps for NGFW December
2022 | You can now view alerts about your Strata Logging Service instance within AIOps for NGFW. These alerts enable you to stay aware of the latest service availability, log storage, and connection issues affecting your Strata Logging Service instance, providing you with the context and recommendations necessary to take the appropriate actions against them. |
| Spain Regional
Support November 2022 |
To comply with data privacy regulations that require you to keep
data within Spain, you can now select it as a host region when
you activate Strata Logging Service.
|
| Italy Regional
Support November 2022 |
To comply with data privacy regulations that require you to keep
data within Italy, you can now select it as a host region when
you activate Strata Logging Service.
|
| Multiple Panorama
Support November 2022 | You can now add up to 20 Panorama
appliances to a single Strata Logging Service
instance. This simplifies licensing and monitoring by consolidating
all of your data in one Strata Logging Service instance. That
way, Palo Alto Networks security applications that analyze Strata Logging Service data, such as Cortex XDR, IoT
Security, and SaaS Security Inline, can provide you with more
centralized results. 
|
| Switzerland Regional
Support November 2022 |
To comply with data privacy regulations that require you to keep
data within Switzerland regional boundaries, you can now select
Switzerland as a host region when you activate Strata Logging Service.
|
| Log Forwarding API Access for
MSSPs September 2022 | To help you manage log forwarding profiles at scale, Log Forwarding APIs are now available for managed security service providers. |
| HTTPS Log Forwarding to Google
Chronicle August 2022 |
Strata Logging Service now supports forwarding logs to Google
Chronicle using HTTPS, so if you use Chronicle as
your SIEM, you can now seamlessly ingest firewall data from
Strata Logging Service for a more complete
picture of your network activity.
|
| Field Name Updates for GlobalProtect
CEF Logs August 2022 |
For an output that is more consistent with other log types, we’ve
updated the following field names for GlobalProtect logs sent from
(CEF):
|
| DNS Security Logging June
2022 | You can now send DNS Security logs to
Strata Logging Service to facilitate triage,
prioritization, and response to security incidents involving
DNS. This enables you to view DNS Security logs in Explore to
assess the details of a particular log and perform queries for
further investigation. To send DNS Security logs to Strata Logging Service, you must have a DNS Security
subscription on your firewalls, and you must configure log retention
for DNS Security logs.The Strata Logging Service Estimator does not yet
support DNS Security logs, so you must calculate log
storage manually. The average size of a DNS
Security log is approximately 833 bytes. |
| Subnet Search in Explore May
2022 |
In Explore, You can now
use the = or !=
operators to match IPv4 and IPv6 addresses and subnets that use
CIDR notation. This allows you to speed up your investigations
by quickly narrowing them down to logs from a section of your
network.
For example, this search identifies all logs with the
specified IPv4 address range in the source address field:
src_ip.value =
"192.168.30.51/24"
Similarly, this search identifies all logs that do not
have the specified IPv4 address range in the destination address
field:
dst_ip.value !=
“172.10.10.10/24”
|
| HTTPS Forwarding to Microsoft
Sentinel March 2022 | Strata Logging Service now supports forwarding logs through HTTPS to Microsoft Sentinel. |
| Forwarding for GlobalProtect Troubleshooting
Logs March 2022 |
To provide a more complete picture of your GlobalProtect
application behavior to external logging solutions, you can now
forward GlobalProtect Troubleshooting
logs from Strata Logging Service.
|
| License Information
Widget February 2022 |
On the Dashboard, you can
now
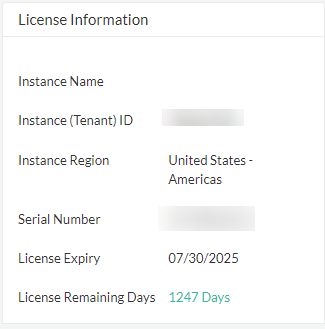
|
| Additional Hardware Models for Strata Logging Service Estimator January
2022 | To help you more accurately estimate the
amount of storage you will need, the Strata Logging Service now supports the following hardware models:
|
| Deployment
Monitoring December 2021 | The Strata Logging Service app now features a dashboard that enables you to view whether your devices are still sending logs to Strata Logging Service as well as view finer details about log transmission, such as storage, latency, ingestion, and log forwarding status. |
| Client Authentication Using
Certificates December 2021 | You can now use certificates to authenticate the log forwarding endpoint that is sending logs to your Syslog and HTTPS servers. This enables you to comply with any company or regulatory policy that may require client authentication. |
| Independent Log Forwarding
Profiles November 2021 |
Log forwarding profiles that send logs to different destinations
now work independently from each other, so if one destination
disconnects and stops ingesting logs, the other destinations
will remain connected and will continue sending logs to these
destinations.
If you are a managed security service provider overseeing the
syslog streams for multiple customers, this feature will ensure
that a problem with one stream will not affect the others.
Also, if you manage multiple syslog sinks for different purposes,
such as SOC investigation, network troubleshooting, and audit
and compliance this feature helps you maintain consistent
service in the event that one sink goes down.
|
| Easy Activation September
2021 |
Strata Logging Service now features a simplified activation
flow to help you get up and running with the product
quickly and easily. After you purchase a Strata Logging Service license, you now receive an email
with a link that takes you to a step-by-step process for
activating your product.
|
| India Regional Support August
2021 |
To comply with data privacy regulations that require you to keep
data within India regional boundaries, you can now select India
as a host region when you activate Strata Logging Service.
|
|
Saved and Shared Filters
August 2021
|
You can now save log queries and
share them with other users. Save log queries to avoid
re-entering long, complex, or frequently used queries each time
you want to see a particular set of logs. Share queries to
quickly present the logs to a team member, support technician,
or anyone whom you want to see them.

|
|
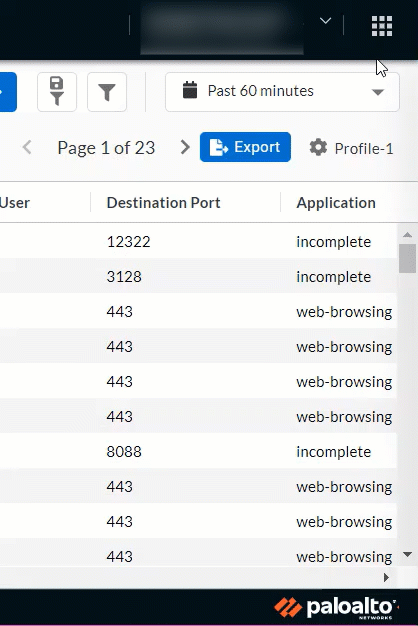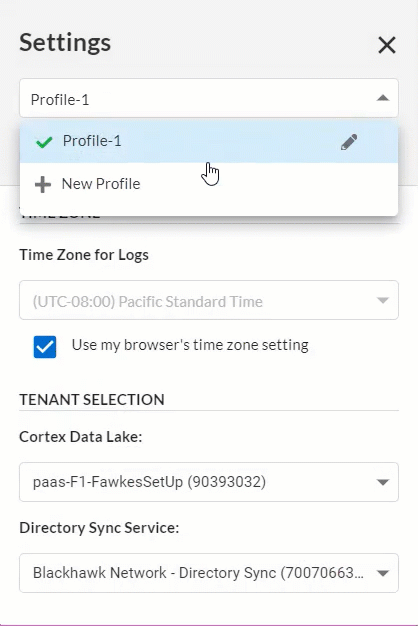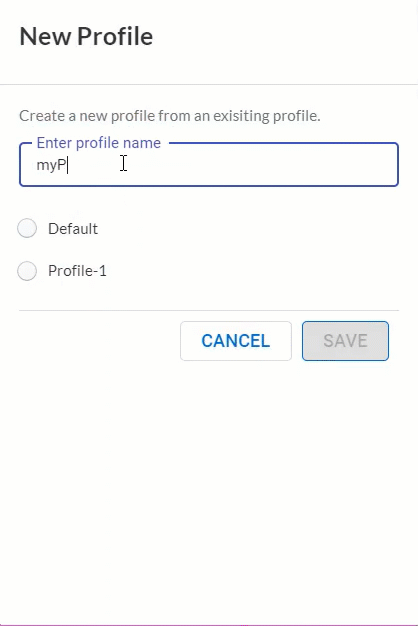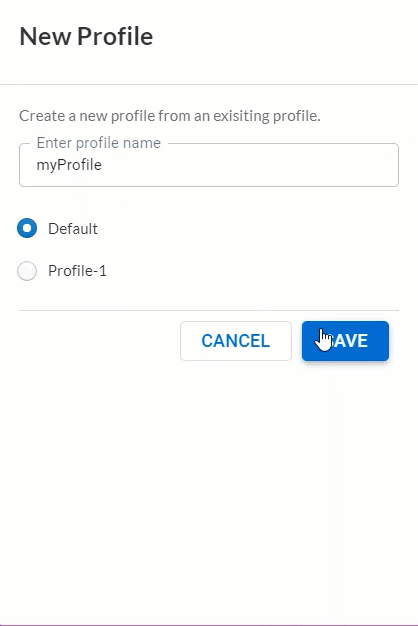
Saved Log Viewer Profiles
August 2021
|
In the log viewer, you can now create profiles that save
preferences so that you can quickly change to a set
of preferences for a particular use case or user.
These preferences include the Cloud Identity Engine (CIE) tenant,
the time zone in which logs appear, and the columns you’ve
chosen to display as well as their order.
|
|
Query Builder Enhancements
July 2021
|
The character limit for queries has increased to 4096, and
queries now wrap to the next line when the field is filled. This
enables you to form longer queries and view their contents at a
glance.
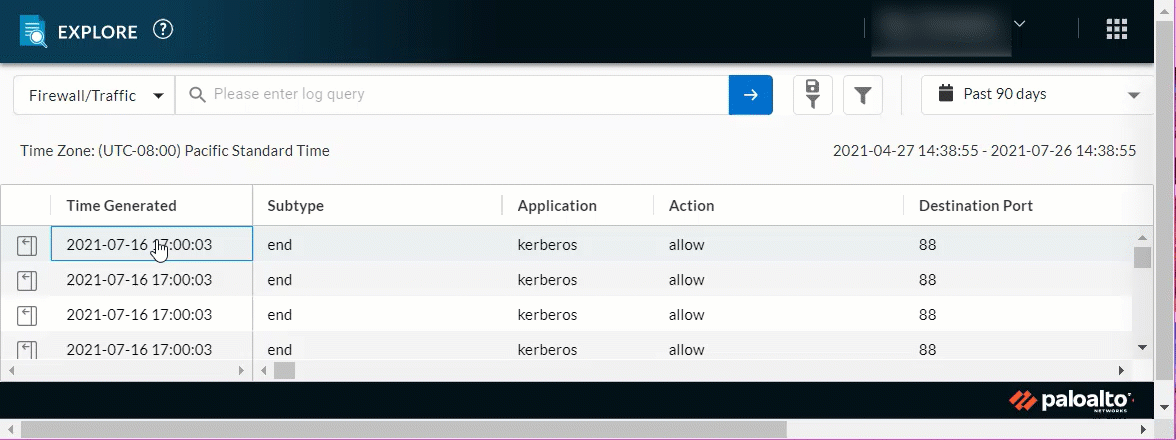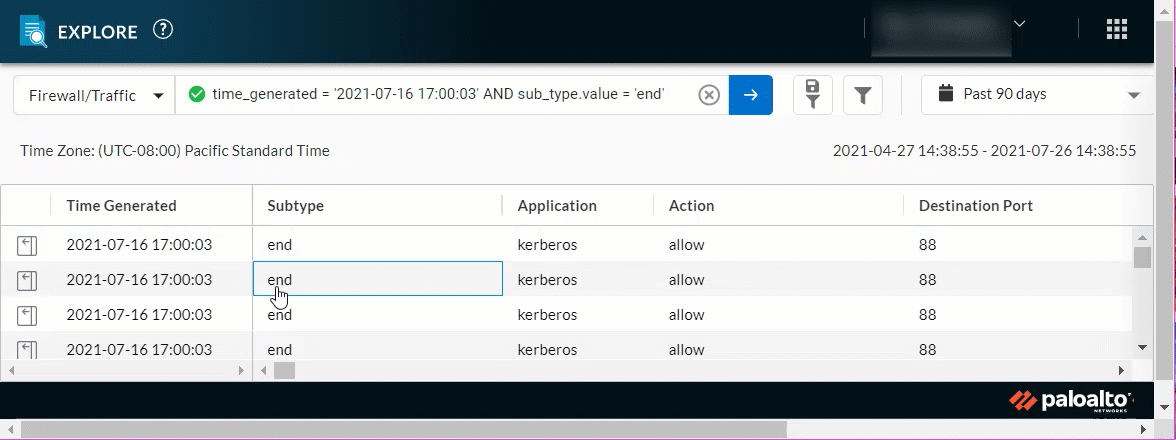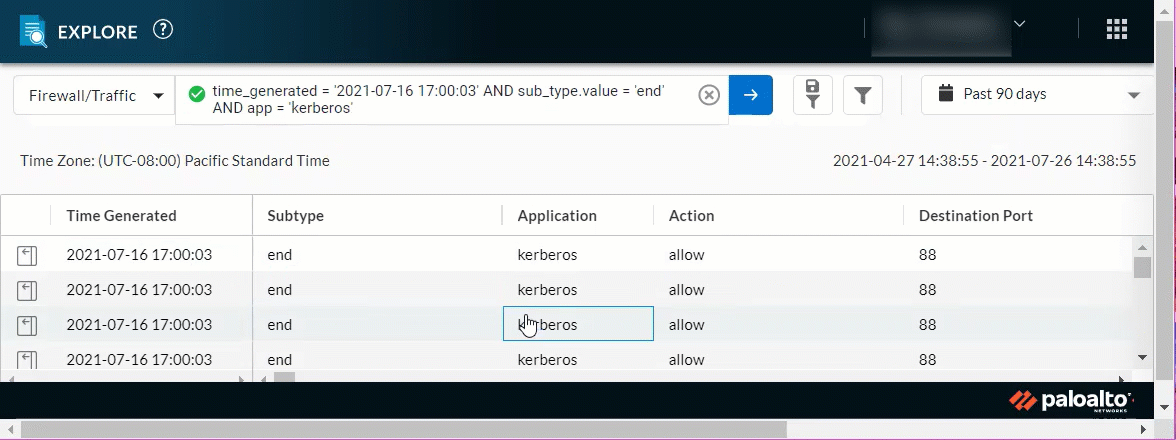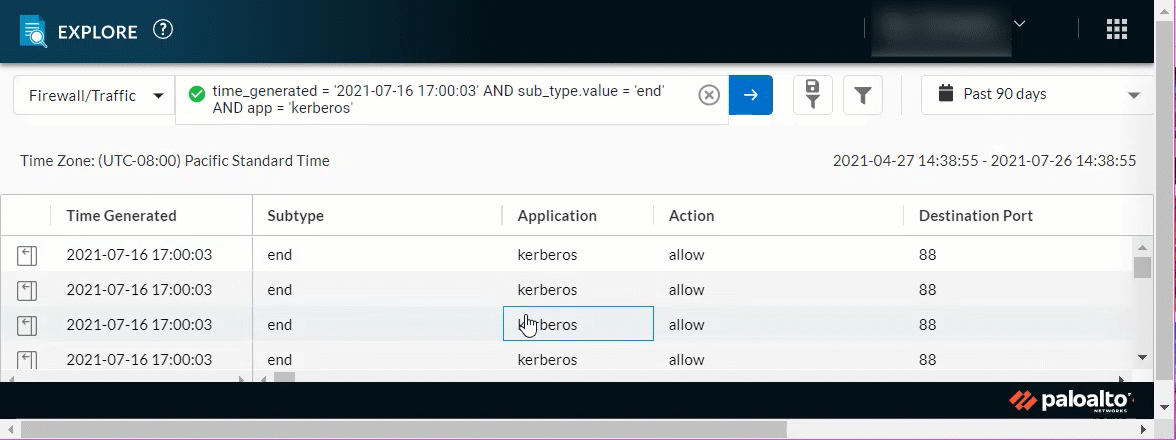
|
|
Time Zone Selection
July 2021
|
You can now choose to view logs in different time zones. This
helps you correlate logs generated by different products that
may use a different time zone from the timezone of your
browser.
|
|
Millisecond-Level Queries
July 2021
|
You can now create queries with the
time_generated_high_res field
equal_to a time in milliseconds. This
enables you to correlate logs with events from other systems at
a millisecond level.
|
|
Default User Preferences
July 2021
|
You can now restore preferences, such as column order and time
zone, to the preferences set when you first started the app.
This enables you to quickly undo any changes you’ve made if you
are no longer satisfied with your preferences.
|
| Log Viewer Admin Role July
2021 |
Strata Logging Service now has a new role that only
grants permission to view the Explore tab
and export log data. If one of your users only needs to view
logs, this enables you to maintain a good security posture by
only granting them the permissions they need.
|
| Germany Regional Support July
2021 |
To comply with data privacy regulations that require you to keep
data within German regional boundaries, you can now select
Germany as a host region when you activate Strata Logging Service.
|
|
Filter Query Parentheses Support
June 2021
|
The log viewer filter now supports parentheses to determine the
order in which it evaluates terms in queries so you can
more precisely identify the logs you’re looking for.
|
|
Firewall Data Retention Toggle
June 2021
|
For better control over your log data, you can now disable log retention for
each of your firewalls from the
Inventory tab in the Strata Logging Service app. To do this, set
Store Log Data to
Off for the firewalls whose data you
do not want to retain.
|
| Device Certificate for Strata Logging Service June
2021 |
(PAN-OS 10.1 or later) To reduce the number of
certificates you need to install and manage to connect to Palo
Alto Networks cloud services, you can now authenticate to Strata Logging Service using a device certificate.
This enables you to authenticate to Strata Logging Service using the same certificate that you would use to connect to
Cortex XDR, IoT Security, and Enterprise Data Loss
Prevention.
Devices using a device certificate follow a new process to
onboard to Strata Logging Service. Make sure to follow
the onboarding process appropriate for your PAN-OS version and deployment
style.
|
| Self-Signed Certificate
Support April 2021 |
You can now get started forwarding logs from Strata Logging Service more quickly, easily, and
cost-effectively by using a self-signed certificate to
authenticate your syslog or HTTPS receiver. After installing the
certificate on your receiver, you can upload the private CA or
self-signed certificate as part of your syslog or HTTPS forwarding
profiles.
|
| Log Forwarding Certificate Validation
Enhancement March 2021 |
To ensure your log data arrives safely to its intended
destination, Strata Logging Service now more rigorously
inspects the validity of
server certificates.
|
| Log Forwarding Connection
Check March 2021 |
To help you verify that you can connect to the syslog server to
which you want to forward logs, Strata Logging Service
Log Forwarding now features a Test
Connection button in Syslog and HTTPS profile
configuration. When you click this button, you will see that the
connection either succeeded or failed and why.
|
| HTTPS Log Forwarding March
2021 |
For compatibility with services that receive events through
HTTPS, such as Splunk HTTP Event Collector (HEC), Strata Logging Service now supports forwarding logs through
HTTPS.
|
|
Common Event Format (CEF) Support
March 2021
|
Enabling you to forward logs to Microfocus ArcSight Enterprise
Security Manager, Strata Logging Service now supports CEF
as an option when you select the log format for a syslog forwarding
profile.
|
|
No Data Retention
March 2021
|
For better control over your log data, Strata Logging Service now does not retain logs at all if
you set log storage
Quota or Max Retention
Days to 0 in Storage Configuration. If you do want to store logs, ensure that
Quota is greater than 0 and
Max Retention Days is not set to
0.
|
|
Related Log Events
February 2021
|
Certain network logs—Traffic, Threat, URL, File—now show you the
other events logged during the same session.
Without leaving the context of the
log you’re interested in, you can see the sequence of
related events for the session. Related logs are displayed
chronologically, top to bottom—the log with the earliest
timestamp is listed first.
Select a related log to investigate the details for that
event.

|
|
Log Format Updates
February 2021
To take advantage of these features, you must edit and
resubmit your log forwarding profiles. | New Log Fields—To support the transport of richer data about your network traffic, Strata Logging Service now processes new log fields from PAN-OS: device group (DG) hierarchy and secure web gateway (SWG) fields. The DG hierarchy field helps you identify which firewall Device Group generated a log, and SWG fields provide more detailed user Authentication information. |
|
New Email Log Format—For better consistency across log
outputs, the log fields in email log forwarding now more closely
resemble other supported formats, such as LEEF and the format
used in Explore. This does not affect email forwarding
profiles that were migrated from an older version of Log
Forwarding.
| |
|
Log Field Modification—For better consistency with other
log fields, the ProfileToken field
now has the first letter capitalized. If you reference this
field in automation scripts, ensure that it reads
ProfileToken.
| |
|
Log Forwarding Filter Updates
February 2021
To take advantage of these features, you must edit and
resubmit your log forwarding profiles. |
Editable Migrated Filters—You now have the flexibility to
modify the queries in log forwarding filters that you may have
retained from an earlier version of the Log Forwarding app.
Migrated filters will not tell you if a query that you
entered is valid. To validate a query, create a new filter
and test it there. When you determine the query works, then
paste it into the migrated filter. |
|
Filter Deletion Confirmation—To prevent you from
accidentally deleting log forwarding filters, filter deletion is
now a two-step process.
| |
In-App Device Connection
Management January 2021 |
For smoother device onboarding, you can now view a list of your available
Panorama and firewall devices and generate onboarding
keys for them within the app.
|
| Redesigned UI January
2021 |
To provide a more consistent experience across Palo Alto Networks
platforms, Strata Logging Service now features a new user
interface that you may recognize from products such as Prisma
Access.
|
| Explore Integration January
2021 | Instead of switching to a different app, you can now search, filter, and export logs directly within the Strata Logging Service app. Select Explore in the app’s new sidebar to get started. |
| Australia Regional
Support December 2020 | To comply with data privacy regulations that require you to keep data within Australian regional boundaries, you can now select Australia as a host region when you activate Strata Logging Service. |
| Log Forwarding
Integration November 2020 | You can now forward logs from within the Strata Logging Service app, enabling you to conveniently manage onboarding, storage, and log transmission in a single application. In moving to the Strata Logging Service app, the log forwarding interface now has a new, simplified design that makes it easier to begin configuring Syslog and email profiles to forward your Strata Logging Service log data. |
| Log Filter Query
Support November 2020 | When creating your log forwarding profiles in Strata Logging Service, you can now use the same query language from Explore to define precise log filters based on time, device serial number, IP address, and more. |
| LEEF Format Support for IBM
QRadar November 2020 | You can now forward logs in Log Extended Event Format (LEEF) for use with IBM QRadar SIEM. |
| Combined Log Types November
2020 |
To simplify the list of available log types for log forwarding,
the tunnel log type now includes
GTP logs, and
Threat logs now include
WildFire logs.
Because log forwarding profiles can only include one filter per
log type, if you had a log forwarding profile with a log filter
for both of the formerly separate log types, you will now see a
new log forwarding profile. This profile contains the log filter
that could not be duplicated in the original profile.
For example, a log forwarding profile with filters for both
tunnel and
GTP logs now appears as two
profiles, each with a tunnel
filter. One of the profiles will continue filtering
tunnel logs and the other will
filter GTP logs, which are now
included in tunnel logs. The new profile will be called
<original name> -
GTP or, in the case of
Threat and
WildFire,
<original name> -
WildFire.
|
| Non-Editable Log Forwarding
Filters November 2020 |
Some log filters created in the previous Log Forwarding app can
no longer be edited. If you would like to change such filters,
you must delete them and create new ones.
Because some fields in the migrated filters are no longer
available, you may not be able to recreate an identical
filter if you delete it. |
|
Scheduled Reports for Strata Logging Service
November 2020
|
(PAN-OS 10.0.2 or later and Cloud Services plugin 1.8.0 or
later) From Panorama, you can now generate scheduled
reports on Strata Logging Service data.
|
| Japan Regional
Support September 2020 | To comply with data privacy regulations that require you to keep data within Japanese regional boundaries, you can now select Japan as a host region when you activate Strata Logging Service. |
| Canada Regional Support July
2020 | To comply with data privacy regulations
that require you to keep data within Canadian regional boundaries,
you can now select Canada as a host region when you activate Strata Logging Service. To choose Canada as your host region, select Canada at
activation. The Americas region represents the United
States only. |
| Proxy Support July
2020 |
(PAN-OS 10.0 or later) You can now configure the
firewall to forward logs to Strata Logging Service
through a proxy server. This enables you to send log data to Strata Logging Service from a network without a default
gateway.
|
| UK and Singapore Regional
Support July 2020 |
For compliance with regulations that require you to keep data
within regional boundaries, you can now select the UK or
Singapore as a host region when you activate Strata Logging Service.
|
| Quota Manager
Enhancements June 2020 |
The quota manager now features a detailed breakdown of firewall
log types and a simpler method of allocating remaining storage
to help you more easily manage your .
Instead of a single Detailed log type, the quota manager now
displays the firewall log types
individually. The Infrastructure & Audit log type now
appears as System and Config logs.
To allocate all remaining storage to one or more log types, you
can now leave the quota percentage of log types blank and the
quota manager will automatically assign them the unallocated
space.
|
| New Quota Manager UI April
2020 |
To help you more easily allocate log storage
and visualize the data you're storing in Strata Logging Service, the Strata Logging Service
app now features a completely redesigned quota manager.
The quota manager now visually displays your total storage
capacity as a bar, with color-coded segments representing
different log sources so you can instantly identify how much
storage a service uses and adjust if necessary.
|
| New Minimum PAN-OS Version for Strata Logging Service Without Panorama March
2020 |
To authenticate using the new G2 certificate chain, firewalls
that you want to onboard to
must now run PAN-OS 9.0.6 or later.
|
| Strata Logging Service Without
Panorama July 2019 |
Until PAN-OS 9.0.3, Panorama was required to onboard firewalls to
Strata Logging Service, and to view logs stored in
Strata Logging Service. Now, firewalls running PAN-OS
9.0.3 and later can securely connect and log to Strata Logging Service, without Panorama. The new app,
Explore, allows you to see and interact with the log data stored
in Strata Logging Service.
|
| New App-ID for Palo Alto Networks Shared
Services May 2019 |
For better application visibility and control, you now have a new
App-ID for paloalto-shared-services, in addition to the App-ID
for the palo-alto-logging-service. The paloalto-shared-services
App-ID identifies traffic for any shared services that are used
by Palo Alto Networks including Directory Sync Service, Logging
Service, and Magnifier; any paloalto-shared-services traffic
that was earlier identified as ssl, web-browsing will now be
identified as paloalto-shared-services.
If you have a Palo Alto Networks next-generation firewall between
the Panorama appliance and the internet, you must add a security
policy rule on the firewall to allow the
paloalto-logging-service and paloalto-shared-services App-IDs
from the Panorama appliance to the internet. These applications
allow SSL-secured communication to the Strata Logging Service that the Panorama appliance uses
to query logs, and enable communication to the shared services
and the Strata Logging Service for performing certificate
status and revocation checks.
|
| Connection Status Reporting
Improvements September 2018 |
To help with visibility on the status and connectivity to the Strata Logging Service, the Cloud Services plugin 1.2
provides details on the connection status between Panorama and
the Strata Logging Service. On PanoramaCloud ServicesStatusStatus, you can now verify that Panorama appliance was
able to successfully retrieve the Logging Service certificate,
view the Customer Identification number and the region in which
your Strata Logging Service instance is deployed, and
confirm that the Panorama appliance is connected to the Logging
Service. If any of these checks fail, the Status is reported as
an error.

|
| New App-ID for Palo Alto Networks Shared
Services September 2018 |
For better application visbility and control, you now have a new
App-ID for paloalto-shared-services, in addition to the App-ID
for the palo-alto-logging-service. The paloalto-shared-services
App-ID identifies traffic for any shared services that are used
by Palo Alto Networks including Directory Sync Service, Logging
Service, and Magnifier; any paloalto-shared-services traffic
that was earlier identified as ssl, web-browsing will now be
identified as paloalto-shared-services.
If you have a Palo Alto Networks next-generation firewall between
the Panorama appliance and the internet, you must add a security
policy rule on the firewall to allow the
paloalto-logging-service and paloalto-shared-services App-IDs
from the Panorama appliance to the internet. These applications
allow SSL-secured communication to the Strata Logging Service that the Panorama appliance uses
to query logs, and enable communication to the shared services
and the Strata Logging Service for performing certificate
status and revocation checks.
|
| Expand Log Storage Capacity for Traps
Logs April 2018 |
You can now activate Strata Logging Service Auth code from
the cloud services portal to upgrade the Traps Included Storage
of 100GB to a Strata Logging Service license with larger
storage capacity.
|
| Log Quota Management on the hub March
2018 |
Starting March 19, 2018, you must use the cloud services portal
to manage the log quota for logs stored on the Strata Logging Service.
Log in to the cloud services portal using your Customer Support
Portal credentials, and then refer to the Logging Service
Getting Started Guide for instructions on activating licenses
and deploying this service.
|
