Network Security
Policy Object: Quarantine Device Lists
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Policy Object: Quarantine Device Lists
Identify and quarantine compromised devices that are connected with the GlobalProtect
app.
Quarantine Device Lists enable you to centrally manage and isolate potentially
compromised or non-compliant devices across your network. When you add devices to a
quarantine list, you can automatically apply restrictive security policies that limit
their network access while allowing essential remediation activities.
Devices can be added to quarantine lists manually by administrators or automatically
through integration with threat detection systems, endpoint protection platforms, or
compliance monitoring tools. Once quarantined, devices remain isolated until they're
explicitly removed from the list after successful remediation and validation.
A device appears in the quarantine list as a result of the following actions:
- The system administrator added the device to this list manually.
- The device was added to the quarantine list automatically: (Prisma Access Only)
- Using a log forwarding profile with a security rule whose match list had a built-in action set to Quarantine.
- Using HIP match log settings with built-in action set to Quarantine.
- The device was added to the quarantine list using an API. (Prisma Access Only)
- The quarantine list was received as a part of redistributed entry. (Prisma Access Only)
Here's how to get started with Quarantine Device Lists.
Policy Object: Quarantine Device Lists (Strata Cloud Manager)
Configure the quarantine list feature for Strata Cloud Manager Managed NGFWs and
Prisma Access mobile user (GlobalProtect) deployments.
Quarantine devices for cloud managed NGFWs and
Prisma Access using the Quarantine Device List in
Strata Cloud Manager. You can either manually or automatically (based on auto-tags)
add devices to a quarantine list. You can block quarantined devices from accessing
the network or restrict the device traffic based on a security rule.
Prisma Access allows you to identify and quarantine compromised devices with
the GlobalProtect app.
Set Up a Quarantined Device List
The Quarantined Device List screen is where
you identify devices you want to block from accessing your network.
Follow
these steps to add a device to the Quarantined Device List:
- Select ConfigurationNGFW and Prisma AccessObjectsQuarantined Device List.The Global configuration scope is already selected for you.You can modify the scope to your Prisma Access deployments or to your NGFW folders.Select Add Device.Fill in the Host ID and Serial Number fields.Select Save.Repeat steps 1-4 to add additional devices.
Use Quarantine Device List for Security Policy Enforcement
Prevent quarantined devices from sending or receiving traffic on the network by specifying options in a security rule.Follow these steps to configure Security Policy to use your Quarantined Device List to prevent quarantined devices from sending or receiving traffic on the network:- Select ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy from the sidebar.The Global configuration scope is already selected for you.You can modify the scope to your Prisma Access deployments or to your NGFW folders.Scroll down to Security Rules and select Add Rule.The Add Security Policy Rule screen appears.Scroll down to DEVICES under either Source or Destination and select Match Quarantined Devices.This tells your rule to use devices in the quarantine list as the match criteria, whether you specify Quarantine as the Source Device for Source traffic or the Destination Device for Destination traffic.Under Action and Advanced Inspection, specify an action that blocks the quarantined device, such as Deny as required by your rule.Select Save.
Configure Identity Redistribution for Prisma Access
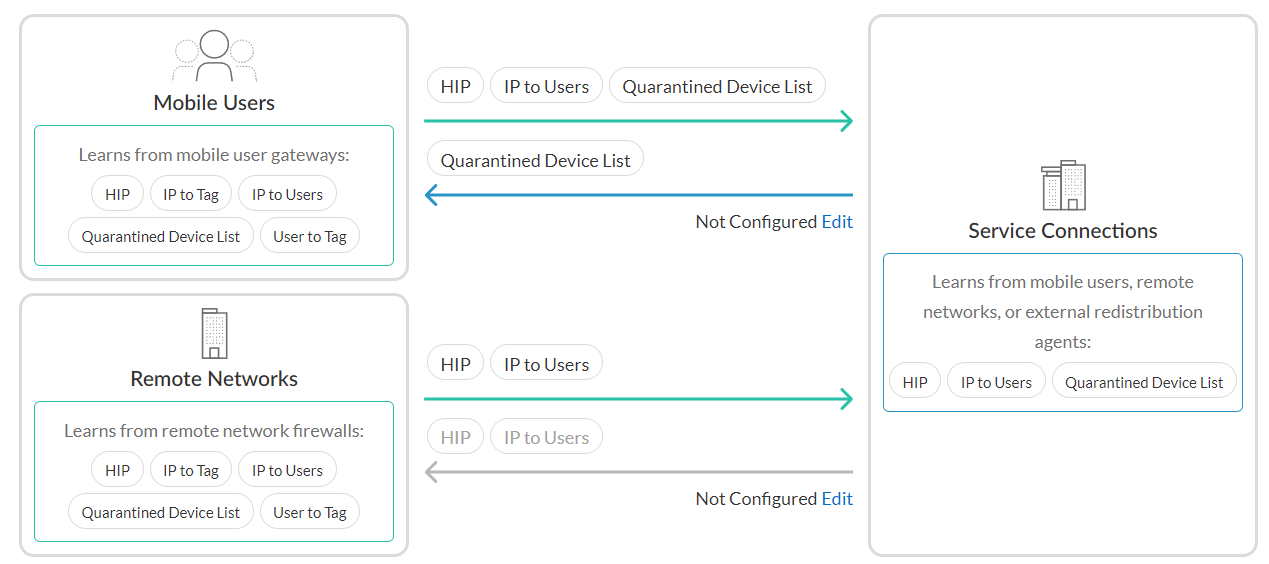
The Identity Redistribution screen is where you configure how identity information is redistributed in the Prisma Access Infrastructure. Configure identity redistribution to use the quarantined device list so that all devices on the network that enforce policy know to block the compromised devices.For more information on setting up Identity Redistribution for NGFWs, click here.Follow these steps to configure identity redistribution to use the Quarantined Device List you created:- Select ConfigurationNGFW and Prisma AccessIdentity ServicesIdentity Redistribution List.Select the appropriate configuration scope, Shared or Mobile Users.You can ignore Service Connections for now because Service connections learn from mobile users, remote networks, or external redistribution agents, as shown in the diagram. If you’re unsure about which to select, see Global and Local Policy. Shared is selected by default.
![]() Select Edit next to Mobile Users.Select the checkbox next to the Quarantined Device List.Select Save.Learn more about Identity Redistribution.
Select Edit next to Mobile Users.Select the checkbox next to the Quarantined Device List.Select Save.Learn more about Identity Redistribution.Block Login for Quarantined Devices for Prisma Access
Block quarantined devices from accessing the network, or block users from logging into the network from devices on the Quarantined Device List.Follow these steps to configure Authentication Settings to prevent users from logging into GlobalProtect from a quarantined device:- Select .Scroll down to User Authentications and select Authentication Settings.The Authentication Settings screen appears.Select the check box for Block Login for Quarantined Devices.Select Save.
Policy Object: Quarantine Device Lists (PAN-OS & Panorama)
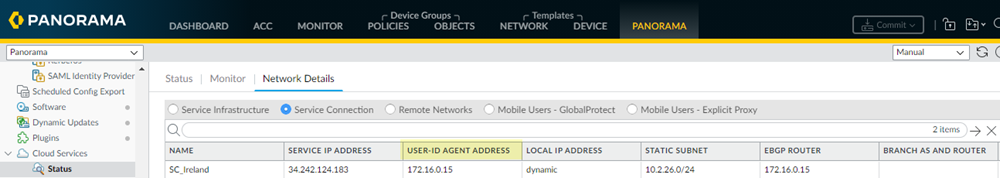
Configure the quarantine list feature for Panorama Managed Prisma Access mobile user (GlobalProtect) deployments.To redistribute quarantine information to and from service connections, the Panorama that manages Prisma Access, and next-generation firewalls, complete the following steps.- Make sure that the Panorama management IP address is able to communicate with the User-ID agent address for all service connections to which you want to redistribute quarantine list information.Communication between the User-ID Agent address of the service connection and the management IP address of Panorama is required for Prisma Access to send and receive quarantine list information between Panorama and the service connections.
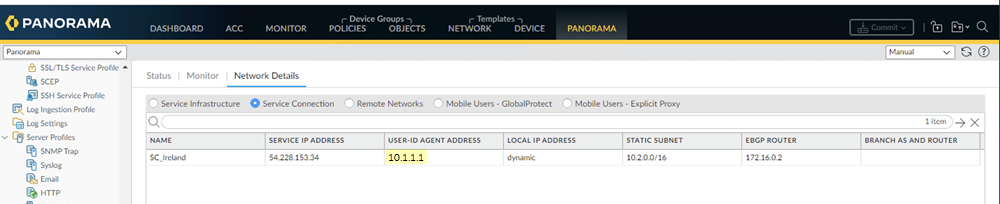
- To find the User-ID Agent Address, select PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address.
![]()
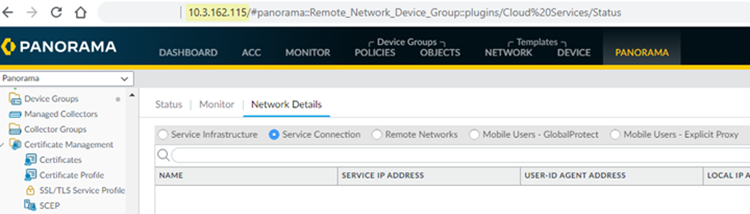
- To find the management IP address of the Panorama that manages Prisma Access, note the IP address that displays in the web browser when you access Panorama.
![]()
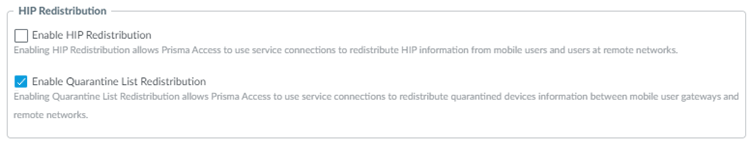
Allow Prisma Access to redistribute quarantine list information.- In Panorama, select PanoramaCloud ServicesConfigurationService Setup.Click the gear icon to edit the settings.In the Advanced tab, select Enable Quarantine List Redistribution.Enabling quarantine list redistribution allows Prisma Access to redistribute the quarantine list information received from one or more mobile user locations (gateways) to service connections.
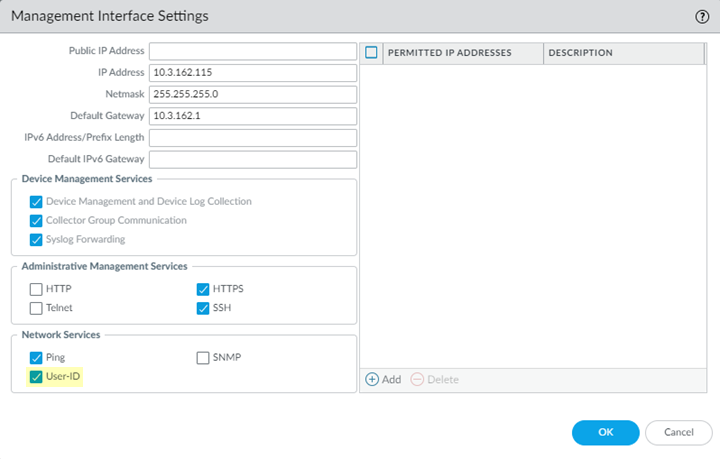
![]() Commit and Push your changes.Configure Panorama to receive quarantine list information from Prisma Access by configuring management interface settings.
Commit and Push your changes.Configure Panorama to receive quarantine list information from Prisma Access by configuring management interface settings.- In the Panorama that manages Prisma Access, select PanoramaSetupInterfaces.Select the Management interface.Select User-ID.
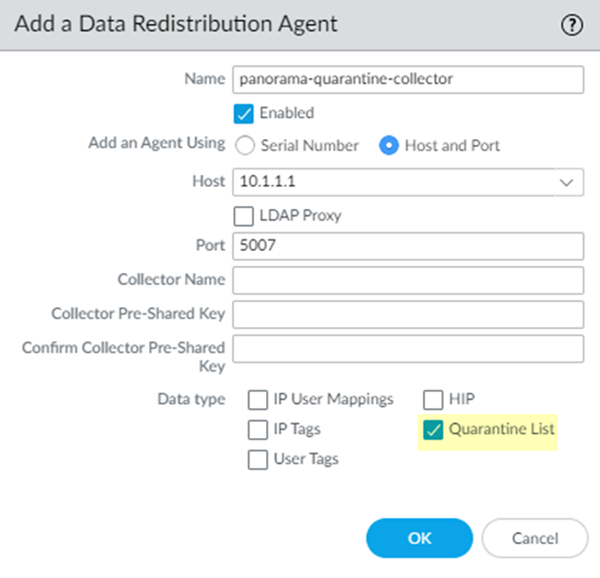
![]() Configure a data redistribution agent that redistributes quarantine list information from the service connections to Panorama.
Configure a data redistribution agent that redistributes quarantine list information from the service connections to Panorama.- From the Panorama that manages Prisma Access, select PanoramaCloud ServicesStatusNetwork DetailsService Connection.Make a note of the User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address) for each service connection.Select PanoramaData RedistributionAgents.Add a Data Redistribution agent, give it a Name and select Enabled.Enter the User-ID Agent Address of the service connection as the Host and 5007 as the Port.Make sure that your network does not block access to this port between Panorama and Prisma Access.(Optional) If you have configured this service connection as a Collector (DeviceData RedistributionCollector Settings), enter the Collector Name and Collector Pre-Shared KeySelect Quarantine List; then, click OK.
![]() Repeat Step 5 for all the service connections in your Prisma Access deployment.Select CommitCommit to Panorama to save your changes locally on the Panorama that manages Prisma Access.Configure a data redistribution agent that redistributes quarantine list information from Panorama to the service connections.
Repeat Step 5 for all the service connections in your Prisma Access deployment.Select CommitCommit to Panorama to save your changes locally on the Panorama that manages Prisma Access.Configure a data redistribution agent that redistributes quarantine list information from Panorama to the service connections.- Find the management IP address of the Panorama that manages Prisma Access.This address displays by in the web browser address bar when you access Panorama.
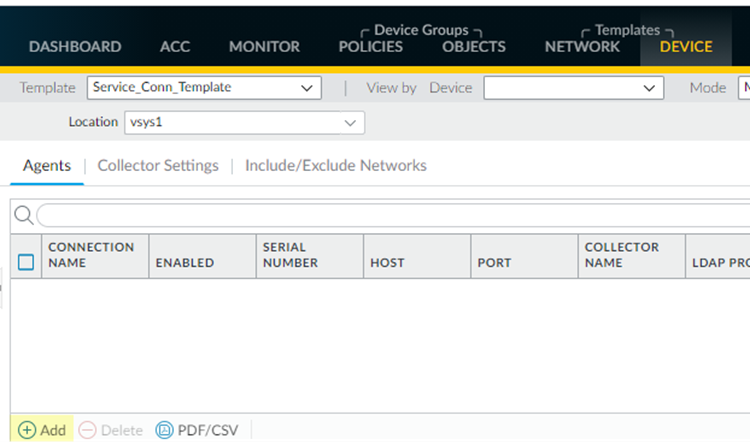
![]() Make sure that you are in the Service_Conn_Template template, then select DeviceData RedistributionAgents.
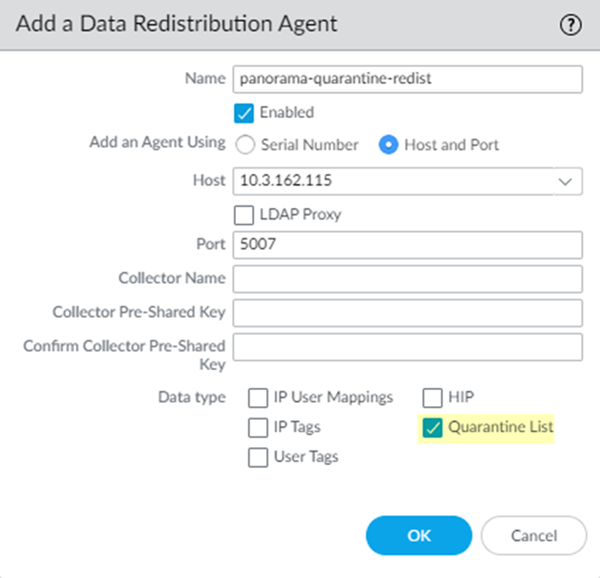
Make sure that you are in the Service_Conn_Template template, then select DeviceData RedistributionAgents.![]() Add a Data Redistribution agent, give it a Name and select Enabled.Enter the management IP address of the Panorama appliance. as the Host and 5007 as the Port.
Add a Data Redistribution agent, give it a Name and select Enabled.Enter the management IP address of the Panorama appliance. as the Host and 5007 as the Port.![]() Select Quarantine List; then, click OK.Configure a data redistribution agent that redistributes quarantine list information from the service connections to mobile user gateways.
Select Quarantine List; then, click OK.Configure a data redistribution agent that redistributes quarantine list information from the service connections to mobile user gateways.- From the Panorama that manages Prisma Access, select PanoramaCloud ServicesStatusNetwork DetailsService Connection.Make a note of the User-ID Agent Address of the service connection from which you want to redistribute quarantine list information.Since all service connections have the same redistributed quarantine list information, choose any service connection. You can also configure more than one service connection.
![]() Make sure that you are in the Mobile_User_Template, then select DeviceData RedistributionAgents.Add a Data Redistribution agent, give it a Name, and select Enabled.Enter the User-ID Agent Address of the service connection as the Host and 5007 as the Port.Make sure that your network does not block access to this port between Panorama and Prisma Access.(Optional) If you have configured this service connection as a Collector (DeviceData RedistributionCollector Settings), enter the Collector Name and Collector Pre-Shared Key.Select Quarantine List; then, click OK.
Make sure that you are in the Mobile_User_Template, then select DeviceData RedistributionAgents.Add a Data Redistribution agent, give it a Name, and select Enabled.Enter the User-ID Agent Address of the service connection as the Host and 5007 as the Port.Make sure that your network does not block access to this port between Panorama and Prisma Access.(Optional) If you have configured this service connection as a Collector (DeviceData RedistributionCollector Settings), enter the Collector Name and Collector Pre-Shared Key.Select Quarantine List; then, click OK.![]() Commit and Push your changes.View your quarantine list information by selecting PanoramaDevice Quarantine.See View Quarantined Device Information in the GlobalProtect Administrator’s Guide for details.
Commit and Push your changes.View your quarantine list information by selecting PanoramaDevice Quarantine.See View Quarantined Device Information in the GlobalProtect Administrator’s Guide for details.