Network Security
Policy Object: Quarantine Device Lists (PAN-OS & Panorama)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Policy Object: Quarantine Device Lists (PAN-OS & Panorama)
Configure the quarantine list feature for Panorama Managed Prisma Access mobile user
(GlobalProtect) deployments.
To redistribute quarantine information to and from service connections, the Panorama
that manages Prisma Access, and next-generation firewalls, complete the following
steps.
- Make sure that the Panorama management IP address is able to communicate with the User-ID agent address for all service connections to which you want to redistribute quarantine list information.Communication between the User-ID Agent address of the service connection and the management IP address of Panorama is required for Prisma Access to send and receive quarantine list information between Panorama and the service connections.
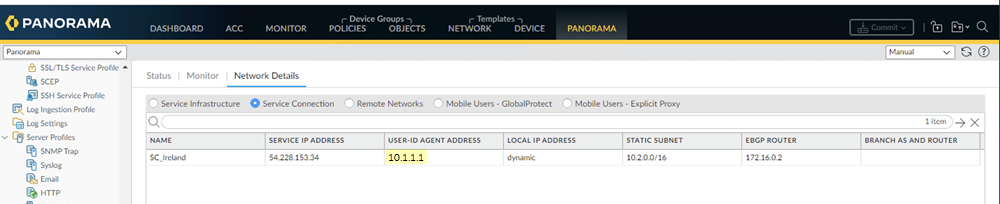
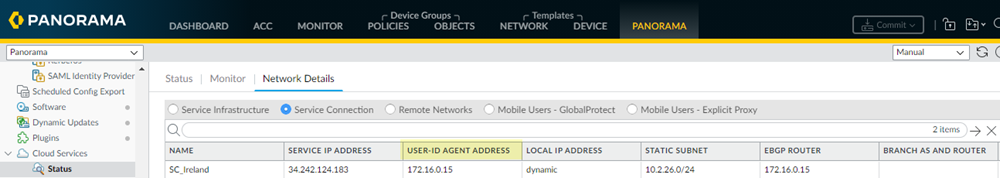
- To find the User-ID Agent Address, select PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address.
![]()
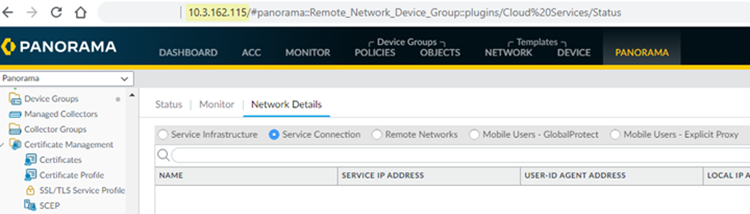
- To find the management IP address of the Panorama that manages Prisma Access, note the IP address that displays in the web browser when you access Panorama.
![]()
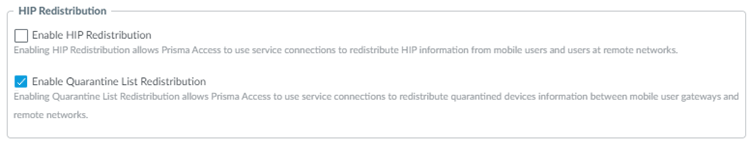
Allow Prisma Access to redistribute quarantine list information.- In Panorama, select PanoramaCloud ServicesConfigurationService Setup.Click the gear icon to edit the settings.In the Advanced tab, select Enable Quarantine List Redistribution.Enabling quarantine list redistribution allows Prisma Access to redistribute the quarantine list information received from one or more mobile user locations (gateways) to service connections.
![]() Commit and Push your changes.Configure Panorama to receive quarantine list information from Prisma Access by configuring management interface settings.
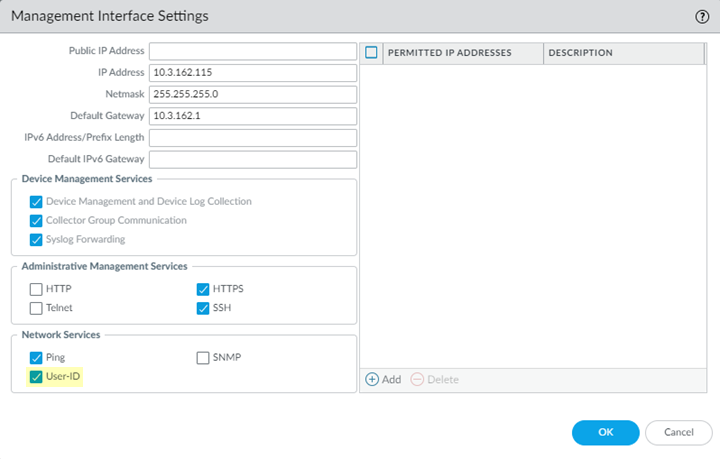
Commit and Push your changes.Configure Panorama to receive quarantine list information from Prisma Access by configuring management interface settings.- In the Panorama that manages Prisma Access, select PanoramaSetupInterfaces.Select the Management interface.Select User-ID.
![]() Configure a data redistribution agent that redistributes quarantine list information from the service connections to Panorama.
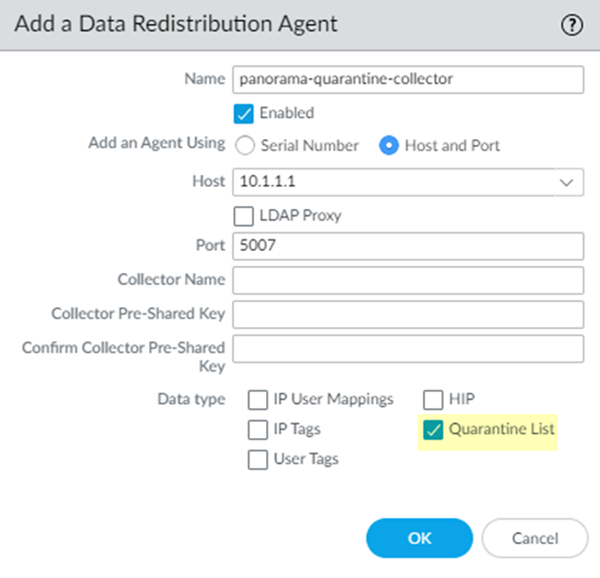
Configure a data redistribution agent that redistributes quarantine list information from the service connections to Panorama.- From the Panorama that manages Prisma Access, select PanoramaCloud ServicesStatusNetwork DetailsService Connection.Make a note of the User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address) for each service connection.Select PanoramaData RedistributionAgents.Add a Data Redistribution agent, give it a Name and select Enabled.Enter the User-ID Agent Address of the service connection as the Host and 5007 as the Port.Make sure that your network does not block access to this port between Panorama and Prisma Access.(Optional) If you have configured this service connection as a Collector (DeviceData RedistributionCollector Settings), enter the Collector Name and Collector Pre-Shared KeySelect Quarantine List; then, click OK.
![]() Repeat Step 5 for all the service connections in your Prisma Access deployment.Select CommitCommit to Panorama to save your changes locally on the Panorama that manages Prisma Access.Configure a data redistribution agent that redistributes quarantine list information from Panorama to the service connections.
Repeat Step 5 for all the service connections in your Prisma Access deployment.Select CommitCommit to Panorama to save your changes locally on the Panorama that manages Prisma Access.Configure a data redistribution agent that redistributes quarantine list information from Panorama to the service connections.- Find the management IP address of the Panorama that manages Prisma Access.This address displays by in the web browser address bar when you access Panorama.
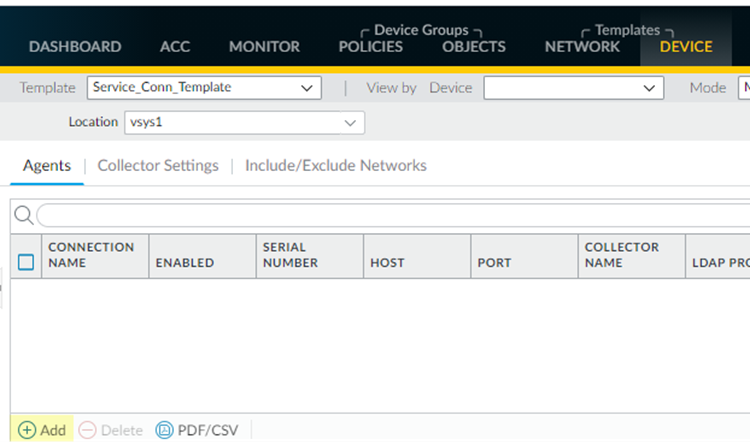
![]() Make sure that you are in the Service_Conn_Template template, then select DeviceData RedistributionAgents.
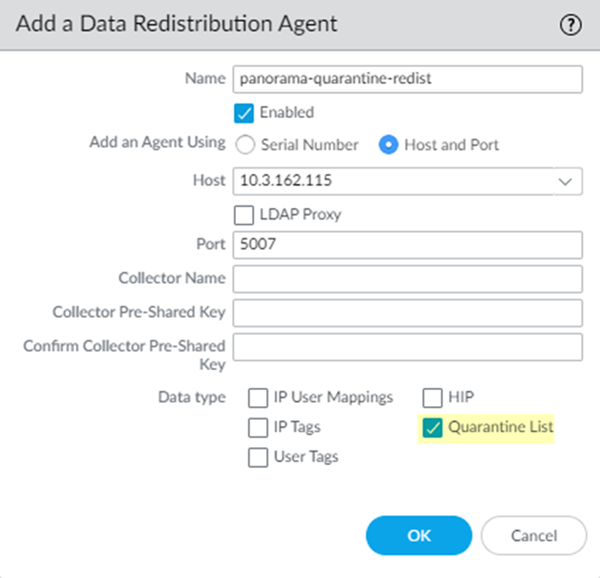
Make sure that you are in the Service_Conn_Template template, then select DeviceData RedistributionAgents.![]() Add a Data Redistribution agent, give it a Name and select Enabled.Enter the management IP address of the Panorama appliance. as the Host and 5007 as the Port.
Add a Data Redistribution agent, give it a Name and select Enabled.Enter the management IP address of the Panorama appliance. as the Host and 5007 as the Port.![]() Select Quarantine List; then, click OK.Configure a data redistribution agent that redistributes quarantine list information from the service connections to mobile user gateways.
Select Quarantine List; then, click OK.Configure a data redistribution agent that redistributes quarantine list information from the service connections to mobile user gateways.- From the Panorama that manages Prisma Access, select PanoramaCloud ServicesStatusNetwork DetailsService Connection.Make a note of the User-ID Agent Address of the service connection from which you want to redistribute quarantine list information.Since all service connections have the same redistributed quarantine list information, choose any service connection. You can also configure more than one service connection.
![]() Make sure that you are in the Mobile_User_Template, then select DeviceData RedistributionAgents.Add a Data Redistribution agent, give it a Name, and select Enabled.Enter the User-ID Agent Address of the service connection as the Host and 5007 as the Port.Make sure that your network does not block access to this port between Panorama and Prisma Access.(Optional) If you have configured this service connection as a Collector (DeviceData RedistributionCollector Settings), enter the Collector Name and Collector Pre-Shared Key.Select Quarantine List; then, click OK.
Make sure that you are in the Mobile_User_Template, then select DeviceData RedistributionAgents.Add a Data Redistribution agent, give it a Name, and select Enabled.Enter the User-ID Agent Address of the service connection as the Host and 5007 as the Port.Make sure that your network does not block access to this port between Panorama and Prisma Access.(Optional) If you have configured this service connection as a Collector (DeviceData RedistributionCollector Settings), enter the Collector Name and Collector Pre-Shared Key.Select Quarantine List; then, click OK.![]() Commit and Push your changes.View your quarantine list information by selecting PanoramaDevice Quarantine.See View Quarantined Device Information in the GlobalProtect Administrator’s Guide for details.
Commit and Push your changes.View your quarantine list information by selecting PanoramaDevice Quarantine.See View Quarantined Device Information in the GlobalProtect Administrator’s Guide for details.