Network Security
Policy Object: Quarantine Device Lists (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Policy Object: Quarantine Device Lists (Strata Cloud Manager)
Configure the quarantine list feature for Strata Cloud Manager Managed NGFWs and
Prisma Access mobile user (GlobalProtect) deployments.
Quarantine devices for cloud managed NGFWs and
Prisma Access using the Quarantine Device List in
Strata Cloud Manager. You can either manually or automatically (based on auto-tags)
add devices to a quarantine list. You can block quarantined devices from accessing
the network or restrict the device traffic based on a security rule.
Prisma Access allows you to identify and quarantine compromised devices with
the GlobalProtect app.
Set Up a Quarantined Device List
The Quarantined Device List screen is where
you identify devices you want to block from accessing your network.
Follow
these steps to add a device to the Quarantined Device List:
- Select ConfigurationNGFW and Prisma AccessObjectsQuarantined Device List.The Global configuration scope is already selected for you.You can modify the scope to your Prisma Access deployments or to your NGFW folders.Select Add Device.Fill in the Host ID and Serial Number fields.Select Save.Repeat steps 1-4 to add additional devices.
Use Quarantine Device List for Security Policy Enforcement
Prevent quarantined devices from sending or receiving traffic on the network by specifying options in a security rule.Follow these steps to configure Security Policy to use your Quarantined Device List to prevent quarantined devices from sending or receiving traffic on the network:- Select ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy from the sidebar.The Global configuration scope is already selected for you.You can modify the scope to your Prisma Access deployments or to your NGFW folders.Scroll down to Security Rules and select Add Rule.The Add Security Policy Rule screen appears.Scroll down to DEVICES under either Source or Destination and select Match Quarantined Devices.This tells your rule to use devices in the quarantine list as the match criteria, whether you specify Quarantine as the Source Device for Source traffic or the Destination Device for Destination traffic.Under Action and Advanced Inspection, specify an action that blocks the quarantined device, such as Deny as required by your rule.Select Save.
Configure Identity Redistribution for Prisma Access
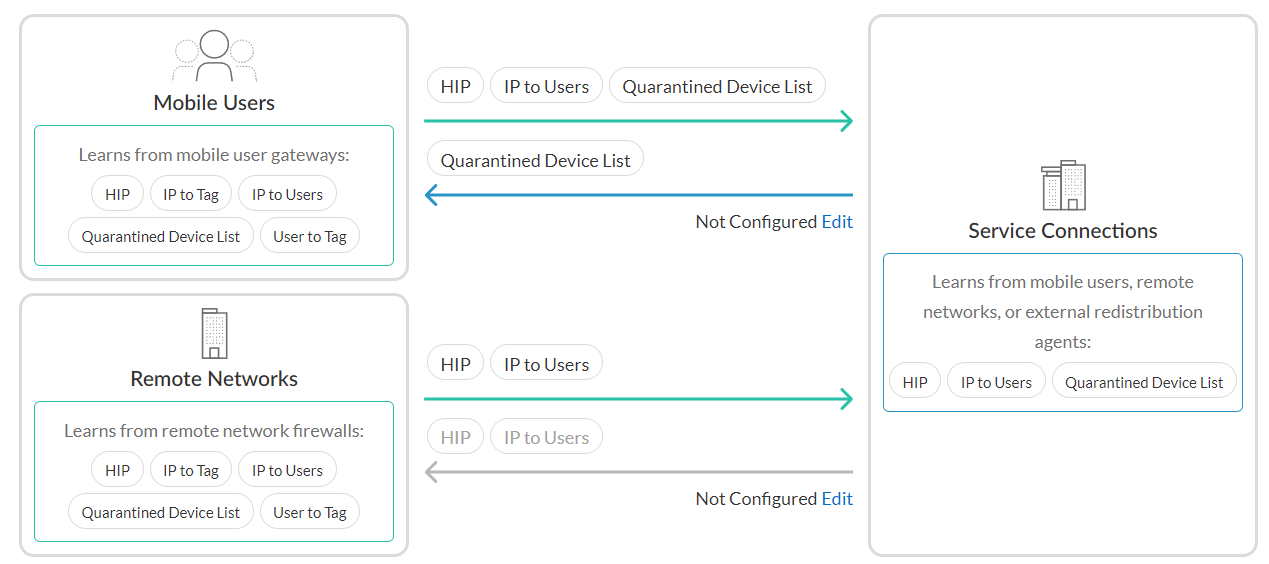
The Identity Redistribution screen is where you configure how identity information is redistributed in the Prisma Access Infrastructure. Configure identity redistribution to use the quarantined device list so that all devices on the network that enforce policy know to block the compromised devices.For more information on setting up Identity Redistribution for NGFWs, click here.Follow these steps to configure identity redistribution to use the Quarantined Device List you created:- Select ConfigurationNGFW and Prisma AccessIdentity ServicesIdentity Redistribution List.Select the appropriate configuration scope, Shared or Mobile Users.You can ignore Service Connections for now because Service connections learn from mobile users, remote networks, or external redistribution agents, as shown in the diagram. If you’re unsure about which to select, see Global and Local Policy. Shared is selected by default.
![]() Select Edit next to Mobile Users.Select the checkbox next to the Quarantined Device List.Select Save.Learn more about Identity Redistribution.
Select Edit next to Mobile Users.Select the checkbox next to the Quarantined Device List.Select Save.Learn more about Identity Redistribution.Block Login for Quarantined Devices for Prisma Access
Block quarantined devices from accessing the network, or block users from logging into the network from devices on the Quarantined Device List.Follow these steps to configure Authentication Settings to prevent users from logging into GlobalProtect from a quarantined device:- Select .Scroll down to User Authentications and select Authentication Settings.The Authentication Settings screen appears.Select the check box for Block Login for Quarantined Devices.Select Save.