Launch the VM-Series Auto Scaling Template for AWS (v2.0)
Table of Contents
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
-
- Activate Credits
- Transfer Credits
- Create a Deployment Profile
- Manage a Deployment Profile
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Renew Your Software NGFW Credits
- Amend and Extend a Credit Pool
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Create and Apply a Subscription-Only Auth Code
- Migrate to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- Use Panorama-Based Software Firewall License Management
- What Happens When Licenses Expire?
- Install a Device Certificate on the VM-Series Firewall
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
-
-
- VM-Series Firewall for NSX-V Deployment Checklist
- Install the VMware NSX Plugin
- Apply Security Policies to the VM-Series Firewall
- Steer Traffic from Guests that are not Running VMware Tools
- Add a New Host to Your NSX-V Deployment
- Dynamically Quarantine Infected Guests
- Migrate Operations-Centric Configuration to Security-Centric Configuration
- Use Case: Shared Compute Infrastructure and Shared Security Policies
- Use Case: Shared Security Policies on Dedicated Compute Infrastructure
- Dynamic Address Groups—Information Relay from NSX-V Manager to Panorama
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
- Use Migration Coordinator to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- VM-Series Firewall Startup and Health Logs on AWS
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
-
- What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
- How Does the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1) Enable Dynamic Scaling?
- Plan the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1)
- Customize the Firewall Template Before Launch (v2.0 and v2.1)
- Launch the VM-Series Auto Scaling Template for AWS (v2.0)
- SQS Messaging Between the Application Template and Firewall Template
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.0)
- Modify Administrative Account and Update Stack (v2.0)
-
- Launch the Firewall Template (v2.1)
- Launch the Application Template (v2.1)
- Create a Custom Amazon Machine Image (v2.1)
- VM-Series Auto Scaling Template Cleanup (v2.1)
- SQS Messaging Between the Application Template and Firewall Template (v2.1)
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.1)
- Modify Administrative Account (v2.1)
- Change Scaling Parameters and CloudWatch Metrics (v2.1)
-
-
- Enable the Use of a SCSI Controller
- Verify PCI-ID for Ordering of Network Interfaces on the VM-Series Firewall
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series Firewall on Azure Stack
- Enable Azure Application Insights on the VM-Series Firewall
- Set up Active/Passive HA on Azure
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on GCP
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Locate VM-Series Firewall Images in the GCP Marketplace
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
End-of-Life (EoL)
Launch the VM-Series Auto Scaling Template for AWS (v2.0)
You can choose to deploy the firewall template
in one VPC and the sample application template in the same VPC as
the one in which you deployed the firewalls, or in a different VPC.
If
the applications that you want to secure belong to a separate AWS
account, the sample application template includes support for cross-account
deployments. The solution supports a hub and spoke architecture
whereby you can deploy the firewall template in one AWS account
and use it as a hub to secure your applications (spokes) that belong
to the same or to different AWS accounts.
- (Required only if you deploy more than one internal load balancer) Enable Traffic to the ELB Service (v2.0 and v2.1)
Launch the VM-Series Firewall Template
This workflow tells you how to deploy the
application load balancer and the VM-Series firewalls using the
firewall template.
This firewall template includes an
AWS NAT gateway that the firewalls use to initiate outbound requests
for retrieving updates, connecting to Panorama, and publishing metrics
to AWS CloudWatch. If you are not using Panorama to manage the firewalls,
you must deploy a jump server (a bastion host with an EIP address) that
attaches to the Untrust subnet within the VPC to enable SSH and/or
HTTPS access to the VM-Series firewalls. This jump server is required
because the management interface on the VM-Series firewalls has
a private IP address only.
- Review the checklist for Plan
the VM-Series Auto Scaling Template for AWS (v2.0).Make sure that you have completed the following tasks:
- (For PAYG only) Reviewed and accepted the EULA for the PAYG bundle you plan to use.
- (For BYOL only) Obtained the auth code. You need to enter this auth code in the /license folder of the bootstrap package.
- Downloaded the files required to launch the VM-Series Auto Scaling template from the GitHub repository.
- (Optional) Modify the init-cfg.txt file.For more details read about the bootstrapping process and the init-cfg.txt file.If you’re using Panorama to manage the firewalls, complete the following tasks:
- Generate the VM Auth Key on Panorama. The firewalls must include a valid key in the connection request to Panorama. Set the lifetime for the key to 8760 hours (1 year).
- Open the init-cfg.txt file with a text editor, such
as Notepad. Make sure that you do not alter the format as this causes
a failure in deploying the VM-Series Auto Scaling template. Add
the following information as name-value pairs:
- IP addresses for the primary Panorama and optionally a secondary Panorama. Enter:panorama-server=panorama-server-2=
- Specify the template stack name and the device group to which you want to assign the firewall. Enter:tplname=dgname=
- VM auth key. Enter:vm-auth-key=
- Verify that you have not deleted the command for swapping
the management interface (mgmt) and the dataplane interface (ethernet
1/1) on the VM-Series firewall on AWS. For example, the file must
include name-value pairs as shown here:op-command-modes=mgmt-interface-swapvm-auth-key=755036225328715panorama-server=10.5.107.20panorama-server-2=10.5.107.21tplname=FINANCE_TG4dgname=finance_dg
- Save and close the file.
- (For
BYOL only) Add the license auth code in the /license folder
of the bootstrap package. For more information see Prepare the Bootstrap Package.
- Create a new .txt file with a text editor, such as Notepad.
- Add the authcode for your BYOL licenses to this file,then
save the file with authcodes (no file extension) and upload it to
the /license folder. The auth code must support the number of firewalls
that may be required for your deployment. You must use an auth code
bundle instead of individual auth codes so that the firewall can
simultaneously fetch all license keys associated with a firewall.
If you use individual auth codes instead of a bundle, the firewall
retrieves only the license key for the first auth code included
in the file.
- Change the default credentials for the VM-Series firewall
administrator account defined in the bootstrap.xml file.Required for using the VM-Series Auto Scaling template in a production environment.The bootstrap.xml file in the GitHub repository is provided for testing and evaluation only. For a production deployment, you must Customize the Bootstrap.xml File (v2.0) prior to launch.
- Prepare
the Amazon Simple Storage (S3) buckets for launching the VM-Series Auto
Scaling template to a production environment.Make sure to create the S3 buckets in the same region in which you plan to deploy the template; the bootstrapping files hosted in the public S3 bucket are provided only to make it easier for you to evaluate the template.
- Create a new S3 bucket for the bootstrap
files.
- Sign in to the AWS Management Console and open the S3 console.
- Click Create Bucket.
- Enter a Bucket Name and a Region, and click Create. The bucket must be at the S3 root level. If you nest the bucket, bootstrapping fails because you cannot specify a path to the location of the bootstrap files.
- Upload the bootstrap files to the S3 bucket. The bootstrap
folders must be in the root folder of the S3 bucket.
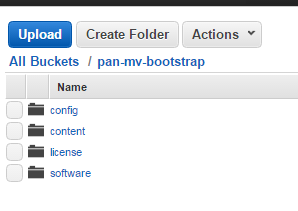
- Click the name of bucket and then click Create folder.
- Create the following folder structure for bootstrapping.
![]()
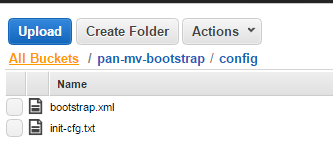
- Click the link to open the config folder.
- Select ActionsUpload and Add Files, browse to select the init-cfg.txt file and bootstrap.xml file, and click Open.
- Click Start Upload to add the files to the config folder. The folder can contain only two files: init-cfg.txt and the bootstrap.xml.
![]()
- (For BYOL only) Click the link to open the license folder and upload the txt file with the auth code required for licensing the VM-Series firewalls.
- Upload the AWS Lambda code (panw-aws.zip file) to
an S3 bucket. In this example, the AWS Lambda code is in the same
S3 bucket as the bootstrap package.
- Click the bucket name.
- Click Add Files to select the panw-aws.zip file, click Open.
- Click Start Upload to add the zip file to the S3 bucket.
![]()
- Create a new S3 bucket for the bootstrap
files.
- Select the firewall template.If you need to Customize the Firewall Template Before Launch (v2.0), do that now and select the modified template.
- In the AWS Management Console, select CloudFormationCreate Stack.
- Select Upload a template to Amazon S3, choose the firewall-v2.0.template and click Open and Next.
- Specify the Stack name. The stack name allows you to uniquely identify all the resources that this template deploys.
- Configure the parameters for the VPC.
- Enter the parameters for the VPC
Configuration as follows:
- Enter a VPCName.
- Select the two Availability Zones that your setup spans in Select two AZs.
- Enter the parameters for the VPC
Configuration as follows:
- Select your preferences for the VM-Series firewalls.
![]()
- Look up the AMI ID for the VM-Series firewall and enter it. Make sure that the AMI ID matches the AWS region, PAN-OS version and the BYOL or PAYG licensing option you opted to use.
- Select the EC2 Key pair (from the drop-down) for launching the firewall. To log in to the firewalls, you must provide the name of this key pair and the private key associated with it.
- Restrict SSH access to the firewall’s management interface. Make sure to supply a CIDR block that corresponds to your dedicated management IP addresses or network. Do not make the allowed source network range larger than necessary and do not ever configure the allowed source as 0.0.0.0/0. Verify your IP address before configuring it on the template to make sure that you do not lock yourself out.
- Select Yes if you want to Enable Debug Log. Enabling the debug log generates more verbose logs that help with troubleshooting issues with the deployment. These logs are generated using the stack name and are saved in AWS CloudWatch.
By default, the template uses CPU utilization as the scaling parameter for the VM-Series firewalls. Custom PAN-OS metrics are automatically published to the CloudWatch namespace that matches the stack name you specified earlier. - Specify the name of the Amazon S3 bucket(s).You can use one S3 bucket for the bootstrap package and the zip file.
![]()
- Enter the name of the S3 bucket that contains
the bootstrap package.If the bootstrap bucket is not set up properly or if you enter the bucket name incorrectly, the bootstrap process fails and you cannot be able to log in to the firewall. Health checks for the load balancers also fail.
- Enter the name of the S3 bucket that contains the panw-aws.zip file.
- Enter the name of the S3 bucket that contains
the bootstrap package.
- Specify the keys for enabling API access to the firewall
and Panorama.
![]()
- Enter the key that the firewall must use to authenticate API calls. The default key is based on the sample bootstrap.xml file and you should only use it for testing and evaluation. For a production deployment, you must create a separate PAN-OS login just for the API call and generate an associated key.
- Enter the API Key to allow AWS Lambda to make API calls to Panorama, if you are using Panorama for centralized management. For a production deployment, you should create a separate login just for the API call and generate an associated key.
- Copy and paste the license deactivation API key for
your account. This key is required to successfully deactivate licenses
on your firewalls when a scale-in event occurs. To get this key:
- Log in to the Customer Support Portal.
- Select AssetsAPI Key Management.
- Copy the API key.
- Enter the name for the application load balancer.
- (Optional) Apply tags to identify the resources
associated with the VM-Series Auto Scaling template.Add a name-value pair to identify and categorize the resources in this stack.
- Review the template settings and launch the template.
- Select I acknowledge that this template might cause AWS CloudFormation to create IAM resources.
- Click Create to launch the template. The CREATE_IN_PROGRESS event displays.
- On successful deployment the status updates to CREATE_COMPLETE.
![]() Unless you customized the template, the VM-Series Auto Scaling template launches an ASG that includes one VM-Series firewall in each AZ, behind the application load balancer.
Unless you customized the template, the VM-Series Auto Scaling template launches an ASG that includes one VM-Series firewall in each AZ, behind the application load balancer.
- Verify that the template has launched all required resources.
- On the AWS Management Console, select the
stack name to view the Output for the list
of resources.
![]()
- On the EC2 Dashboard, select Auto Scaling Groups. Verify that in each AZ, you have one ASG for the VM-Series firewalls with the one firewall in each ASG. The ASG name prefix includes the stack name.
- Log in to the VM-Series firewall. You must deploy
a jump server or use Panorama to access the web interface on the
firewall.
- It can take up to 20 minutes for the firewalls to boot up and be available to handle traffic.
- When you finish testing or a production deployment, the only way to ensure charges stop occurring is to completely delete the stack. Shutting down instances, or changing the ASG maximum to 0 is not sufficient.
- On the AWS Management Console, select the
stack name to view the Output for the list
of resources.
- Save the following information. You need to provide these
values as inputs when deploying the application template.
- IP addresses of the NAT Gateway in each AZ. You need this IP address to restrict HTTP access to the web servers if you deploy the application in a different VPC. Specifying this IP address ensures that the firewall secures access your applications in a different VPC, and that nobody can bypass the firewall to directly access the web server. The sample application template (panw_aws_nlb_vpc-2.0.template) displays a template validation error if you do not enter the NAT Gateway IP addresses; you must enter the IP addresses as a comma-separated list.
- Network Load Balancer SQS URL. An AWS Lambda function in the firewall stack monitors this queue so that it can learn about any network load balancers that you deploy, and create NAT policy rules (one per application) on the VM-Series firewalls that enable the firewalls to send traffic to the network load balancer IP address.
Launch the Application Template
The application template allows you to complete
the sandwich topology and is provided so that you can evaluate the
auto scaling solution. This application template deploys a network
load balancer and a pair of web servers behind the auto scaling
group of VM-Series firewalls, which you deployed using the firewall
template. The web servers in this template have a public IP address
for direct outbound access to retrieve software updates. Use this
template to evaluate the solution, but build your own template to
deploy to production. For a custom template, make sure to enable SQS
Messaging Between the Application Template and Firewall Template.
When
launching the application template, you must select the template
based on whether you want to deploy the application template within
the same VPC (panw_aws_nlb-2.0.template) in which you deployed the
firewall template or in a separate VPC (panw_aws_nlb_vpc-2.0.template).
For a separate VPC, the template provides supports for cross-account
deployments. A cross-account deployment requires you to create an
IAM role and enable permissions and trust relationship between the
trusting AWS account and the trusted AWS account, and the account information
is required as input when launching the template.
- (Required
only for a cross-account deployment) Create the IAM role. Refer
to AWS documentation.This role grants access to a user who belongs to a different AWS account. This user requires permissions to access the Simple Queue Service (SQS) resource in the firewall template. The firewall uses this queue to learn about each network load balancer that you deploy so that it can create NAT policy to send traffic to the web servers that are behind the network load balancer.
- For Account ID, type the AWS account ID of the account into which you are deploying the application template. Specifying that account ID allows you to grant access to the resources in your account that hosts the firewall template resources.
- Select Require external ID and enter a value that is a shared secret. Specifying an external ID allows the user to assume the role only if the request includes the correct value.
- Choose Permissons to allow Amazon SQS Full Access.
- Use the Palo Alto Networks public S3 bucket or prepare
your private (S3) bucket for launching the application template.
- Create a zip file with all the files in the GitHub repository, excluding the three .template files, named nlb.zip in the screenshot below.
- Upload the zip file to the S3 bucket you created earlier
or to a new bucket.
![]()
- Copy the pan_nlb_lambda template into the same bucket to which you copied the nlb.zip file.
- Select the application template to launch.
- In the AWS Management Console, select CloudFormationCreate Stack.
- Select Upload a template to Amazon S3, to choose the panw_aws_nlb-2.0.template to deploy the resources that the template launches within the same VPC as the firewalls, or the panw_aws_nlb_vpc-2.0.template to deploy the resources in to a different VPC. Click Open and Next.
- Specify the Stack name. The stack name allows you to uniquely identify all the resources that are deployed using this template.
- Configure the parameters for the VPC and network load
balancer.
- Select the two Availability Zones that your setup will span in Select list of AZ. If you are deploying within the same VPC make sure to select the same Availability Zones that you selected for the firewall template.
- Enter a CIDR Block for the VPC.
The default CIDR is 192.168.0.0/16.
![]()
- (Only if you are using the panw_aws_nlb-2.0.template
to deploy the applications within the same VPC)
![]() Select the VPC ID and the Subnet IDs associated with the trust subnet on the firewalls in each AZ. The network load balancer is attached to the trust subnet on the firewalls, to complete the load balancer sandwich topology.
Select the VPC ID and the Subnet IDs associated with the trust subnet on the firewalls in each AZ. The network load balancer is attached to the trust subnet on the firewalls, to complete the load balancer sandwich topology. - Enter a name for the network load balancer.
- Configure the parameters for AWS Lambda.
- Enter the S3 bucket name where nlb.zip and the pan_nlb_lambda.template is stored.
- Enter the name of the pan_nlb_lambda.template and the zip file name.
- Paste the SQS URL that you copied earlier.
- Enter a unique TableName. This
table stores a mapping of the port and IP address for the applications
associated with the network load balancer in your deployment.When you delete the application stack this table is deleted. Therefore, if multiple instances of the network load balancer write to the same table and the table is deleted, the NAT rules on the firewalls not function properly and the application traffic maybe be inaccurately forwarded to the wrong port/network load balancer.
- Modify the web server EC2 instance type to meet your deployment needs.
- Select the EC2 Key pair (from the drop-down) for launching the web servers. To log in to the web servers, you must provide the key pair name and the private key associated with it.
- (Only if you are using the panw_aws_nlb_vpc-2.0.template)
Lock down access to the web servers.
- Restrict SSH From access to the web servers. Only the IP addresses you list here can log in to the web servers.
- Restrict HTTP access to the web servers. Enter the public IP addresses of the NAT gateway from the firewall template output, and make sure to separate IP addresses with commas. Entering the NAT gateway IP address allows you to ensure that all web traffic to the application servers are secured by the VM-Series firewalls.
- (Only if you are using the panw_aws_nlb_vpc-2.0.template)
Configure the other parameters requires to launch the application
template stack in a different VPC.
![]()
- Select SameAccount true if
you are deploying this application template within the same AWS
account as the firewall template, and leave the cross account role
and external ID blank; select false for a
cross-account deployment.For a cross-account deployment, enter the Amazon Resource Number (ARN) for the CrossAccountRole and ExternalId that you defined in (Required only for a cross-account deployment) Create the IAM role. Refer to AWS documentation.You can get the ARN from SupportSupport Center on the AWS Management Console.
- Enter the VPC Namein which you want to deploy the application template resources.
- Optional Change the NLBSubnetIPBlocks for the Management subnet for the network load balancer.
- Select SameAccount true if
you are deploying this application template within the same AWS
account as the firewall template, and leave the cross account role
and external ID blank; select false for a
cross-account deployment.
- Review the template settings and launch the template.
- Verify that the network load balancer is deployed and
in a ready state.
![]()
- Get the DNS name for the application
load balancer, and enter it into a web browser.For example: http://MVpublic-elb-123456789.us-east-2.elb.amazonaws.com/When the web page displays, you have successfully launched the auto scaling template.
- Verify that each firewall has a NAT policy rule to the
IP address of each network load balancer.When you deploy the application template to launch another instance of a network load balancer and pair of web servers, the firewall learns about the port allocated for the next network load balancer instance and creates another NAT policy rule. So, if you deploy the application template three times, the firewall has three NAT policy rules for ports 81, 82, and 83.
![]()
- If you have launched the application template more than once, you need to Enable Traffic to the ELB Service.
Enable Traffic to the ELB Service (v2.0 and v2.1)
If you add a second or additional internal
load balancers (ILBs) in your deployment, you must complete additional
configuration so that the internal load balancer, the VM-Series
firewalls auto scaling groups, and the web servers can report as
healthy and traffic is load balanced across all your AWS resources.
In
v2.0, the ILB can only be a network load balancer. In v2.1 the ILB
can be an application load balancer or a network load balancer.
- On the AWS management console, verify the ports
allocated for each network balancer on the DynamoDB table.When you launch a new internal load balancer, the application template must send an SQS message to the SQS URL you provided as input when you launched the template. The AWS Lambda function in the firewall template monitors the SQS and adds the port mapping to the DynamoDB table for the firewall template. Starting at port 81, the port allocated for every additional internal load balancer you deploy increments by 1. So, the second internal load balancer uses port 82, and the third port uses port 83.
- Select the DynamoDB service on the AWS management console.
- Select Tables and click the
table that matches the stack name for your firewall template. For
example, MV-CFT20-firewall-us-east-2.In the Items list, view the ports used by the internal load balancers that are publishing to the SQS associated with the firewall template.
![]()
- Create a target group. The internal load
balancer sends requests to registered targets using the port and
protocol that you specify for the servers in the target group.When you add a new target group, use the port information that you verified on the DynamoDB table.
![]()
- Edit the listener rules on the internal
load balancer to route requests to the target web servers.
- On the AWS management console, select Load Balancers in the Load Balancing section, and select the internal load balancer that matches your stack name.
- Select View/edit rules to modify the rules for the listener.
- Select Insert rule and add
a path-based route to forward traffic to the target group you defined
above as follows:
![]()
- Attach the target group to both VM-Series firewalls auto
scaling groups.
- Select Auto Scaling Groups in the Auto Scaling section and select an auto scaling group that matches the stack name.
- Select DetailsEditand select the new target
group from the Target Groups drop-down.
- Log in to each web server that was deployed by the application
template, create a new directory with the target group name and
copy the index.html file into the directory. Until you set up the
path to the index.html file, the health check for this web server
reports as unhealthy.sudo sucd/var/www/htmlmkdir <target-groupname>cp index.html <target-groupname>
- Verify the health status of the web servers.Select Auto Scaling Groups, and use the application stack name to find the webserver auto scaling group to verify that the web servers are reporting healthy.
![]()