Prisma AIRS
Strata Cloud Manager
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Strata Cloud Manager
Create an AI security profile to enable AI application protection, AI data
protection, and AI model protection, and add it to your security policy rules.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
This page helps you create and associate an AI security profile with a security
policy rule. The AI security profile inspects and secures the AI traffic between AI
applications and the LLM models passing through Prisma AIRS AI Runtime: Network intercept managed by Strata Cloud Manager.
- Log in to Strata Cloud Manager.Navigate to Configuration NGFW and Prisma Access Security Services AI Security.Select the Configuration Scope as Global or limit it to your AI security profile.Select AI Security → Add Profile.
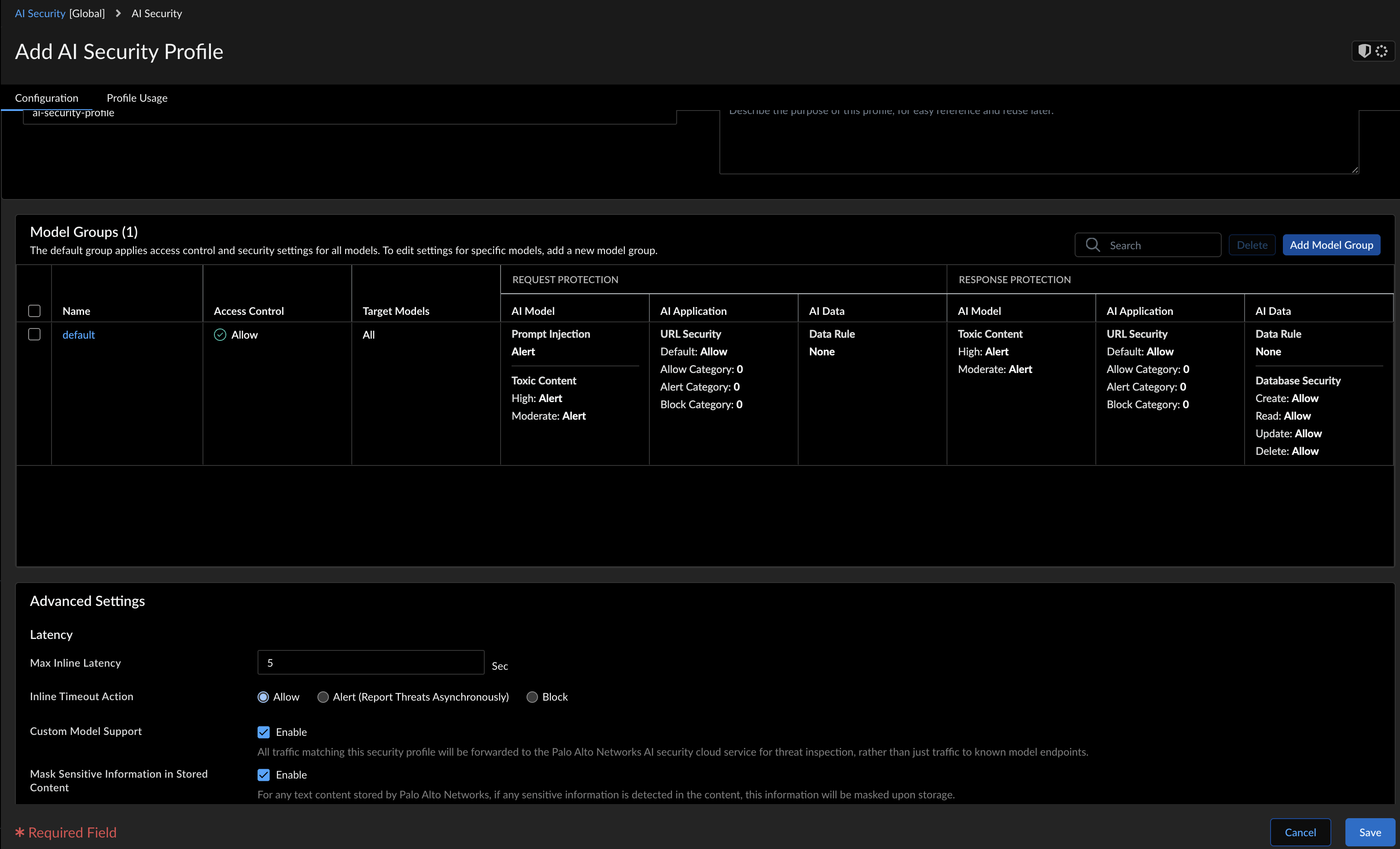
![]() Enter a Name and a Description.Add Model Group for customized protections. See Create Model Groups in Strata Cloud Manager.For example, a model group with URL categorization and prompt injection alert settings is attached to the following security profile for a target AI model. You can attach a security policy as a zone or a Dynamic Address Group:
Enter a Name and a Description.Add Model Group for customized protections. See Create Model Groups in Strata Cloud Manager.For example, a model group with URL categorization and prompt injection alert settings is attached to the following security profile for a target AI model. You can attach a security policy as a zone or a Dynamic Address Group:- For zone-based security, follow the use case on how to Create Traffic Objects for Zone-Based Security using specific clusters to monitor the ingress and east-west traffic. Attach this zone to a security policy rule to enforce security policy rules on the AI traffic sourced from this zone and the traffic objects within this zone.
- For protecting the source AI applications, use Dynamic Address Groups in Policy and reference these DAGs in the security policy rule.
In the Advanced Settings, configure the following:- Max Inline Latency: Set the maximum allowed latency for inline threat detection. The latency range is between 1 and 300 seconds.
- Inline Timeout Action: Specify the action to be taken when the
inline threat detection exceeds the max inline latency.
- Allow
- Alert (Report threats asynchronously)
- Block
- Custom Model Support: When enabled, all traffic matching this security profile will be forwarded to the Palo Alto Networks AI security cloud service for threat inspection, rather than just traffic to known model endpoints.
Click Create.To push the security policy rules to the firewall, navigate to Manage Configuration Operations.Select Push Config.When a query is detected with the action alert or block, an AI security log is generated with the respective AI Incident Type and AI Incident Subtype.As the user interacts with the application and the application makes requests to an AI model, the AI security logs are generated for each security policy rule. Check the specific logs in the AI Security Report under AI Security Log Viewer.