Advanced DNS Security Powered by Precision AI®
View DNS Security Logs (Strata Cloud Manager)
Table of Contents
View DNS Security Logs (Strata Cloud Manager)
View logs using Strata Cloud Manager to get a detailed view into the DNS queries made by
users in your network environment.
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.Search for DNS queries that have been processed using DNS Security.
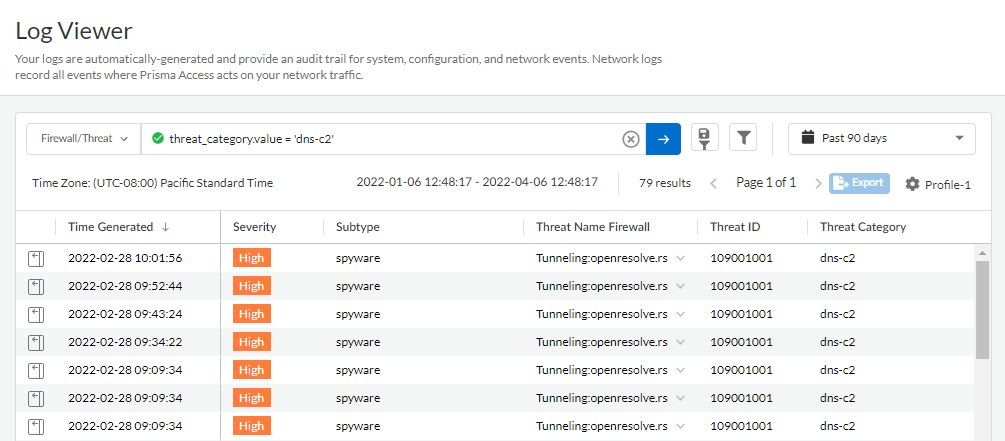
- Select Log Viewer.Constrain your search using the threat filter and submit a log query based on the DNS category, for example, threat_category.value = 'dns-c2' to view logs that have been determined to be a C2 domain. To search for other DNS types, replace c2 with another supported DNS category (ddns, parked, malware, etc). Adjust the search criteria as necessary for your search, including additional query parameters (such as the severity level and subtype) along with a date range.
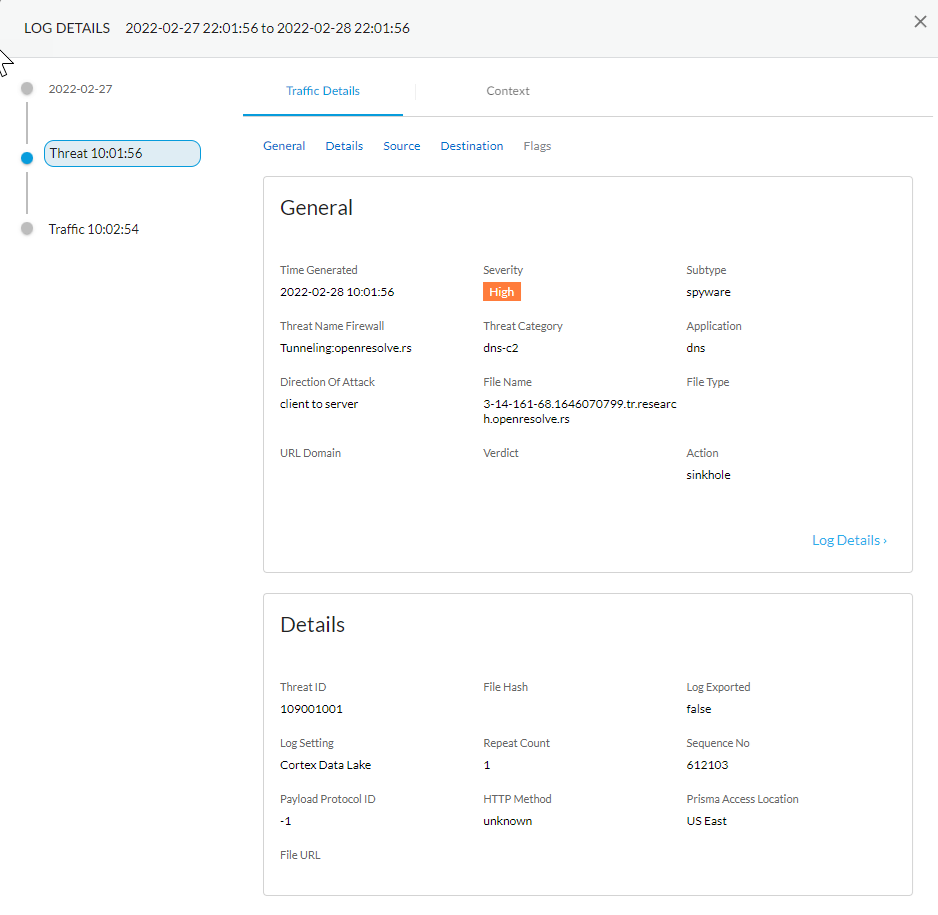
![]() Select a log entry to view the details of a detected DNS threat.The threat Category is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.
Select a log entry to view the details of a detected DNS threat.The threat Category is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.![]() For stockpiled domains and DNS tunneling domains, including tunneling-based APTs (advanced persistent threats), you can view the various tools used in the attack, as well as the attack campaigns associated with the domain. This is reflected in the Threat ID/Name field for the log entry for a given domain. The Threat ID/Name for DNS domains with attributions use the following format; in this example, for DNS tunnel domains: Tunneling:<tool_name>,<tool_name>,<tool_name>,...:<domain_name>, whereby the tool_name refers to the DNS tunneling tools used to embed data into the DNS queries and responses, but also the cyber threat campaign name, in a comma-separated list. These campaigns can be industry accepted incidents and use the same naming conventions or might be one identified and named by Palo Alto Networks and described in the Unit 42 Threat Research blogs. A blog of such a campaign, in this case, one leveraging DNS tunneling techniques, can be found here: Leveraging DNS Tunneling for Tracking and Scanning.The associated tool and campaign attributions might take some time after the initial detection has completed to become viewable in the logs as well as the Palo Alto Networks ThreatVault and Test-A-Site. When the attribution component finishes and has been verified, the complete DNS tunneling tools and campaign details display as expected in the Threat ID/Name and campaign fields.(Advanced DNS Security Resolver) Search for DNS queries that have been processed by the Advanced DNS Security Resolver.Logs generated by the Advanced DNS Security Resolver provide expanded transaction details. As a result of this change, the logs generated by the resolver are listed under the log type: DNS Security (Resolver and 12.1 or later).
For stockpiled domains and DNS tunneling domains, including tunneling-based APTs (advanced persistent threats), you can view the various tools used in the attack, as well as the attack campaigns associated with the domain. This is reflected in the Threat ID/Name field for the log entry for a given domain. The Threat ID/Name for DNS domains with attributions use the following format; in this example, for DNS tunnel domains: Tunneling:<tool_name>,<tool_name>,<tool_name>,...:<domain_name>, whereby the tool_name refers to the DNS tunneling tools used to embed data into the DNS queries and responses, but also the cyber threat campaign name, in a comma-separated list. These campaigns can be industry accepted incidents and use the same naming conventions or might be one identified and named by Palo Alto Networks and described in the Unit 42 Threat Research blogs. A blog of such a campaign, in this case, one leveraging DNS tunneling techniques, can be found here: Leveraging DNS Tunneling for Tracking and Scanning.The associated tool and campaign attributions might take some time after the initial detection has completed to become viewable in the logs as well as the Palo Alto Networks ThreatVault and Test-A-Site. When the attribution component finishes and has been verified, the complete DNS tunneling tools and campaign details display as expected in the Threat ID/Name and campaign fields.(Advanced DNS Security Resolver) Search for DNS queries that have been processed by the Advanced DNS Security Resolver.Logs generated by the Advanced DNS Security Resolver provide expanded transaction details. As a result of this change, the logs generated by the resolver are listed under the log type: DNS Security (Resolver and 12.1 or later).![]()
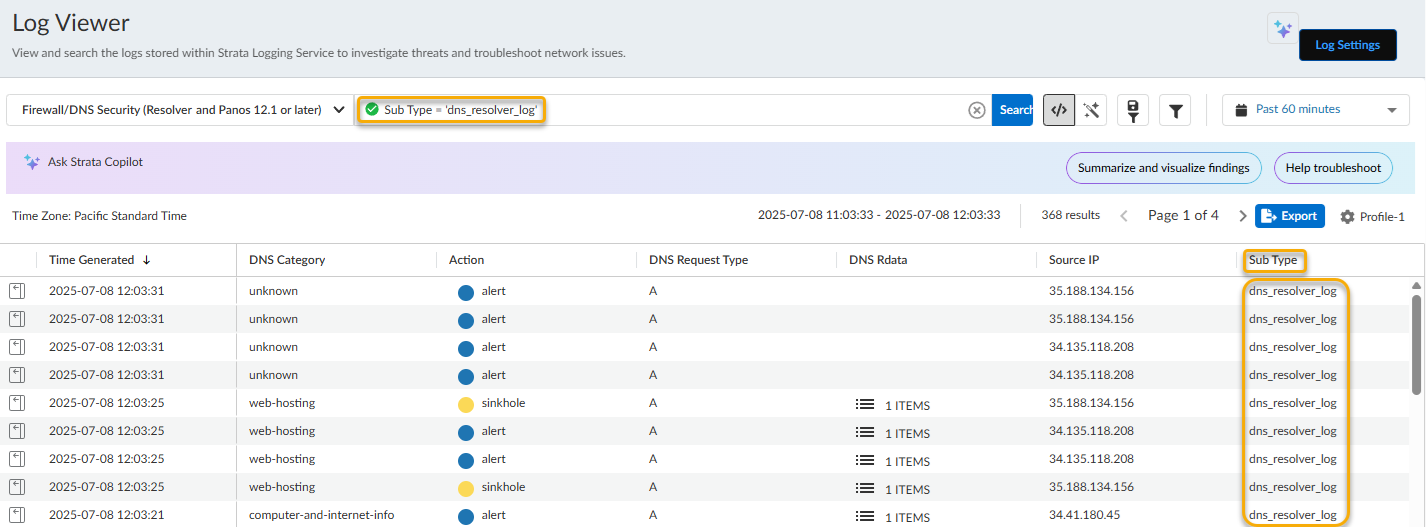
- Select Incidents and AlertsLog Viewer.Constrain your search using the threat filter and submit a log query based on the DNS category, for example, DNS Category = 'grayware' to view logs that have been determined to be a grayware domain. To search for other DNS types, replace grayware with another supported DNS category (ddns, parked, malware, etc). Adjust the search criteria as necessary for your search, including additional query parameters (such as the severity level and subtype) along with a date range.As in the above example, you can also constrain your search using the threat filter and submit a log query based on the DNS category, for example, threat_category.value = 'dns-c2' to view logs that have been determined to be a C2 domain.To constrain the search to logs generated by DNS queries that have passed through the Advanced DNS Security Resolver, use the following query parameter: Sub Type = 'dns_resolver_log'
![]() Select a log entry to view the details of a detected DNS threat.The threat Category is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.(Advanced DNS Security Resolver - using Prisma Access Agent) Search for DNS queries submitted from Prisma Access Agent and processed by the Advanced DNS Security Resolver.Logs generated by the Advanced DNS Security Resolver provide expanded transaction details. As a result of this change, the logs generated by the resolver are listed under the log type: DNS Security (Resolver and 12.1 or later).
Select a log entry to view the details of a detected DNS threat.The threat Category is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.(Advanced DNS Security Resolver - using Prisma Access Agent) Search for DNS queries submitted from Prisma Access Agent and processed by the Advanced DNS Security Resolver.Logs generated by the Advanced DNS Security Resolver provide expanded transaction details. As a result of this change, the logs generated by the resolver are listed under the log type: DNS Security (Resolver and 12.1 or later).![]()
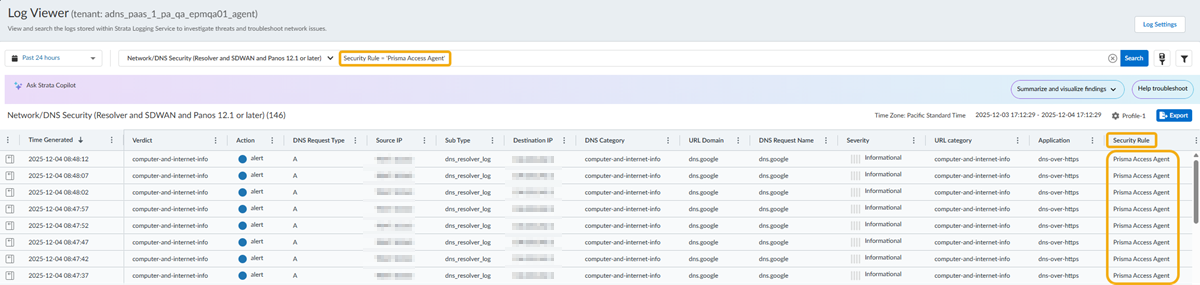
- Select Incidents and AlertsLog Viewer.Constrain your search using the threat filter and submit a log query based on the DNS category, for example, DNS Category = 'grayware' to view logs that have been determined to be a grayware domain. To search for other DNS types, replace grayware with another supported DNS category (ddns, parked, malware, etc). Adjust the search criteria as necessary for your search, including additional query parameters (such as the severity level and subtype) along with a date range.As in the above example, you can also constrain your search using the threat filter and submit a log query based on the DNS category, for example, threat_category.value = 'dns-c2' to view logs that have been determined to be a C2 domain.To constrain the search to logs generated by DNS queries that have passed through the Advanced DNS Security Resolver from the Prisma Access Agent connection source, use the following query parameter: Security Rule = 'Prisma Access Agent'.
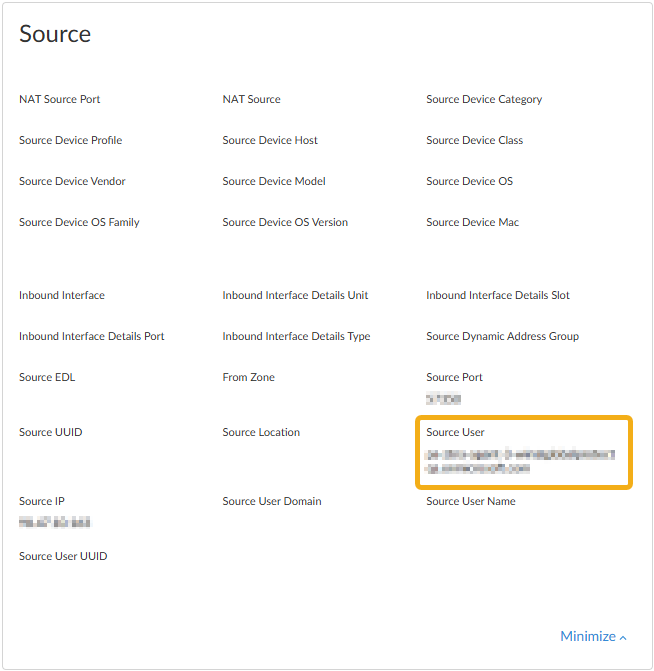
![]() Select a log entry to view the details of a DNS query.The threat Category is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.Log entries generated by Prisma Access Agent submitted DNS queries also provide the following field entries, which can be used to create more targeted searches:
Select a log entry to view the details of a DNS query.The threat Category is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.Log entries generated by Prisma Access Agent submitted DNS queries also provide the following field entries, which can be used to create more targeted searches:- Source User = '<prisma_access_agent_user>'—Prisma Access Agent user identification; typically the email address or user principal name.
![]()
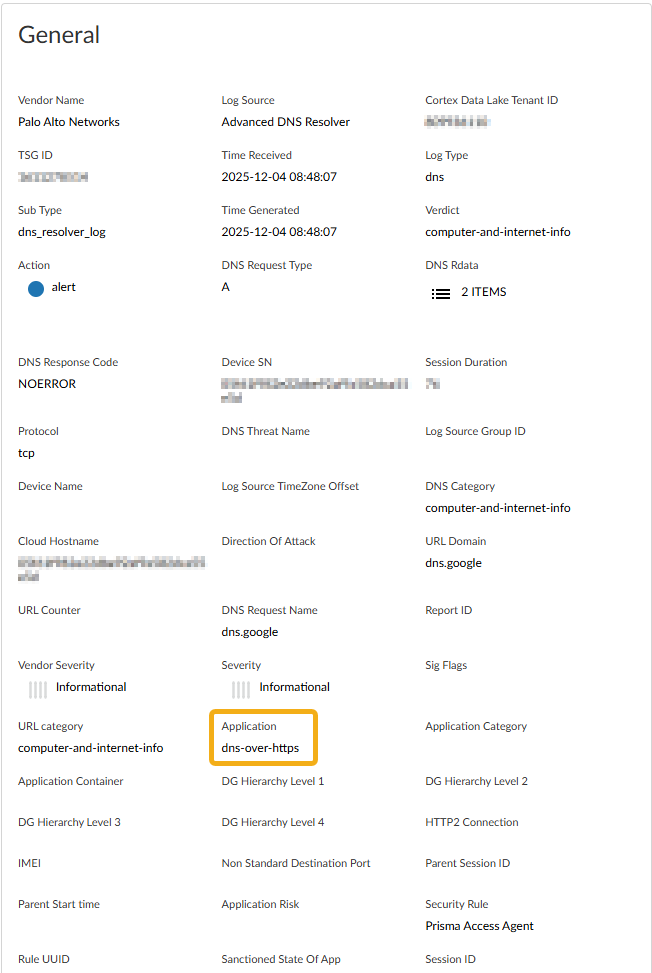
- Application = 'dns-over-https'—DNS queries from Prisma Access Agent users are transmitted exclusively via DoH.
![]()