Prisma Access
New Features in Prisma Access 6.1
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
New Features in Prisma Access 6.1
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
This section provides you with a list of new features in Prisma Access 6.1
Preferred and Innovation, along with the recommended and required software versions you
need to use.
- Recommended Software Versions for Prisma Access 6.1 Preferred and Innovation
- Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 6.1 Preferred and Innovation Features
- Prisma Access 6.1 Features
Recommended Software Versions for Prisma Access 6.1 Preferred and Innovation
There are two Prisma Access 6.1 versions:
- 6.1 Preferred runs a PAN-OS 11.2.7-h5 dataplane.
- 6.1 Innovation runs on a PAN-OS 12.1.1 dataplane.
For Prisma Access 6.1 features, Palo Alto Networks recommends
that you upgrade your Prisma Access to the following versions
before installing the plugin.
| Prisma Access Version | Cloud Services Plugin Version | Required Dataplane Version for 6.1 | Recommended GlobalProtect Version | Recommended Panorama Version |
|---|---|---|---|---|
| 6.1 | 6.1 | 6.1 Preferred: Dependent on feature (PAN-OS 11.2.7-h5 is the
baseline version for 6.1 Preferred) 6.1 Innovation: PAN-OS 12.1.1
|
6.1.7+
6.1.3+
6.2.1+
Minimum required versions for IPv6 Support for Public Apps for
IP Optimization:
|
12.1.2
11.2.0
11.1.0
11.0.1+
10.2.10+
|
Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 6.1 Preferred and Innovation Features
Prisma Access6.1 features require one of more of the following components to
function:
- Infrastructure Upgrade—The infrastructure includes the underlying
service back-end, orchestration, and monitoring infrastructure. Prisma Access upgrades the infrastructure before the general
availability (GA) date of a Prisma Access release. Features that require only an infrastructure upgrade to be unlocked take effect for all Prisma Access deployments, regardless of version, at the time of the infrastructure upgrade.
- Plugin Upgrade (Prisma Access Panorama Managed Deployments
Only)—Installing the plugin activates the features that are
available with that release. You download and install the plugin on the
Panorama that manages Prisma Access.Prisma Access (Managed by Panorama) release 6.1 uses the Cloud Services Plugin 6.1.
- Dataplane Upgrade—The dataplane enables traffic inspection and
security policy enforcement on your network and user traffic.
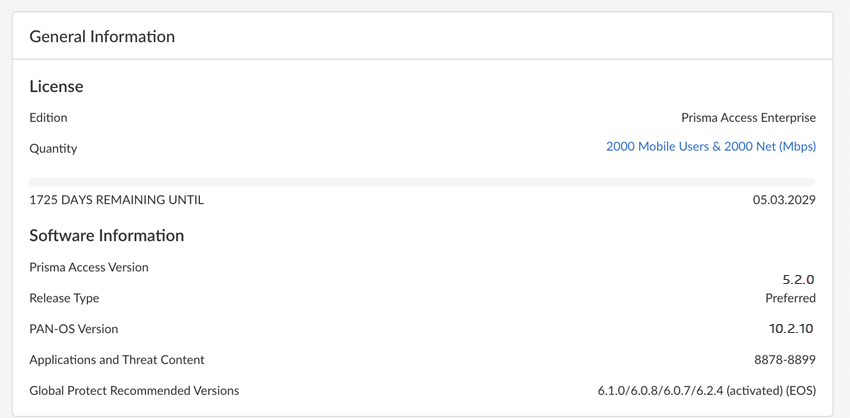
- For Prisma Access (Managed by Strata Cloud Manager), view your Prisma Access version
and release type by going to ManageConfigurationNGFW and Prisma AccessOverviewPrisma Access Version.'
![]()
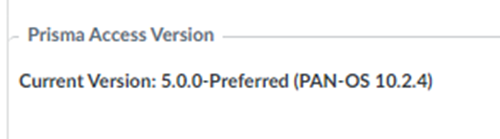
- For Prisma Access (Managed by Panorama) deployments, view your dataplane version by going to PanoramaCloud ServicesConfigurationService Setup and viewing the Prisma Access Version. Prisma Access 6.1 Preferred runs PAN-OS 11.2.7-h5 and Prisma Access 6.1 Innovation runs PAN-OS 12.1.1.
![]()
- For Prisma Access (Managed by Strata Cloud Manager), view your Prisma Access version
and release type by going to ManageConfigurationNGFW and Prisma AccessOverviewPrisma Access Version.'
A dataplane upgrade to 6.1 Innovation is optional, and is
only required if you want to take advantage of the features that require a dataplane
upgrade.
These features are activated with the infrastructure upgrade only for Prisma Access 6.1:
- None
These features require an infrastructure upgrade, a minimum Cloud Services
plugin version of 6.0, and a minimum dataplane of PAN-OS 11.2:
- Additional Prisma Access Locations
- Cloud-Delivered Security Services Support for Prisma Access
These features require an infrastructure and plugin upgrade and require a
minimum dataplane version of PAN-OS 11.2.7-h5, making them Prisma Access
6.1 Preferred features:
- Response Page Customization and Context Passing
- SaaS Policy Rule Recommendations for NGFW and Prisma Access
- Server-Initiated Traffic Flow for Prisma Access ZTNA Connector
These features require an infrastructure, plugin, and dataplane upgrade to
PAN-OS 12.1.1, making them Prisma Access 6.1 Innovation features:
- CloudHSM Support for Prisma Access
- SASE Private Location
Prisma Access 6.1 Features
The following table describes the new features that will be generally available with
Prisma Access 6.1.
Additional Prisma Access Locations
|
Supported in:
Prisma Access 6.1 Preferred and Innovation
For new Prisma Access deployments, these locations
are activated by default; for existing deployments, reach
out to your Palo Alto Networks account representative, who
will contact the Site Reliability Engineering (SRE) team and
submit a request.
|
Prisma Access adds the following locations.
Note that
these locations support a limited functionality set; if you
require additional functionality, we recommend that you onboard alternate locations.
- Colombia Central (Chia)
- France South East (Marseille)
- India South Central (Hyderabad)
- Israel Central (Jerusalem)
- Mexico Northeast (Monterrey)
- Saudi Arabia West (Jeddah)
- US Midwest (Chicago)
- US West Central (Phoenix)
Audio Passthrough for Privileged Remote Access RDP Sessions
When users accessing remote desktops through a web browser cannot hear audio from
applications running on the remote server, they are prevented from using
applications that require audio output such as training videos, notification alerts,
or communication tools. You can enable audio passthrough in a Privileged
Remote Access (PRA) profile to allow audio from the remote RDP server to be heard on
the user's device. Audio passthrough is disabled by default in the default PRA
profile. You configure this setting per PRA profile, which allows you to enable
audio for specific user groups or application types based on your security
requirements. This configuration is only available for RDP applications.
Cloud-Delivered Security Services Support for Prisma Access
|
Supported in:
Prisma Access 6.1 Preferred and Innovation
(minimum PAN-OS dataplane version of 11.2
required)
|
To maintain a robust defense against emerging threats, Prisma Access now includes
support for the following Cloud-Delivered Security Services (CDSS)
capabilities:
These features require a minimum Cloud Services plugin of 6.0 (for Prisma Access
(Managed by Panorama deployments only) and a minimum dataplane version of
PAN-OS® 11.2.
- Advanced DNS Security Powered by Precision
AI®—The Advanced DNS Security service defends against sophisticated
DNS-related threats to maintain network integrity and data security.
- DNS hijacking and misconfiguration prevention—Meticulously detects and immediately blocks DNS hijacking (where attackers alter DNS records to redirect traffic) and accidental or malicious DNS misconfigurations. This ensures the integrity of DNS resolution by preventing unauthorized redirection through advanced monitoring and analysis.
- Malicious traffic distribution system (TDS)—Combats threats hidden within malicious TDS—sophisticated attack frameworks that use complex DNS schemes to distribute malware and exploit kits. The service analyzes DNS traffic patterns to identify indicators of compromise (IOCs), effectively blocking access to these malicious distribution channels.
- Domain masquerading protection—Safeguards against domain masquerading by identifying and blocking malicious domains that closely resemble legitimate ones (typosquatting). It uses cutting-edge AI and machine learning algorithms to analyze vast amounts of DNS data, detecting subtle patterns and characteristic behaviors associated with spoofed or malicious domains.
- Advanced URL Filtering—Use
Prisma Access to add support for the following categories:
- Compromised website—This category specifically identifies legitimate websites that have been hacked or infected with malicious content. This allows you to use granular policy control to distinguish between inherently malicious sites and otherwise trustworthy sites that have been temporarily compromised.
- File converter—This categorizes sites that allow users to convert, compress, or modify files. This new category helps organizations manage access to these tools, mitigating data leakage and compliance risks associated with unauthorized file sharing and modification.
- ML-powered quishing (QR code) protection—Blocks quishing attacks by introducing an ML-powered QR code detector. This feature specifically addresses the growing threat of malicious QR codes embedded on legitimate websites, which attackers use to bypass the perimeter defenses of enterprise-protected networks and target unmanaged personal devices.
- Deepfake content detection—Protects against hyper-realistic social engineering. A new deep learning model is active to identify and block malicious content featuring deepfake videos. This provides essential protection from attackers who use highly convincing deepfake impersonations of trusted individuals in phishing attacks.
- Advanced WildFire® Powered by Precision
AI—Enhanced defenses against evasive threats including a new
deep learning model for PDF phishing, multi-CPU sandboxing for advanced malware,
and ML-powered API Vector Categorization for fileless attacks.
- PDF analysis for phishing—A new Convolutional Neural Network (CNN)-based deep learning model is available. This model analyzes the visual appearance (in addition to the text) of embedded URLs in PDF files to detect highly evasive, embedded phishing attacks that exploit the PDF format.
- API vector categorization—Leverages Machine Learning (ML) to perform in-memory analysis of the patterns and sequences of API calls made by malware during runtime. This advanced approach creates a unique behavioral "fingerprint" (API Vector) to accurately identify and classify highly evasive, fileless, and memory-resident attacks that bypass conventional analysis.
- Multi-CPU advanced dynamic analysis—Enhances Advanced Dynamic Analysis (sandboxing) by including multiple virtual CPUs (vCPUs) in the Windows guest sandbox environment. This capability is specifically designed to defeat sophisticated malware that evades detection by checking for and refusing to execute in single-CPU virtual environments.
- Advanced Threat Prevention Powered
by Precision AI—The following new features enhance threat detection,
custom threat coverage, and protection against advanced data exfiltration
attempts.
- Exfiltration shield for advanced threat prevention—Introduces a sophisticated machine learning (ML) model to combat advanced data exfiltration. This feature focuses on detecting stealthy data egress over common protocols like DNS relay and HTTP headers, which are frequently used to bypass traditional security. Integration is seamless with existing Advanced DNS Security and ATP subscriptions.
CloudHSM Support on Prisma Access
|
Supported in:
Prisma Access 6.1 Innovation
|
Do your security and compliance requirements prevent you from storing Transport Layer
Security (TLS) private keys directly on your Prisma® Access service infrastructure
for SSL decryption? This feature allows you to integrate with AWS CloudHSM or an on-premises hardware
security module (HSM) solution to store and manage the issuing Certificate Authority
(CA) private keys externally, enhancing the security of your cryptographic
operations. The SSL decryption functionality on Prisma Access mandates that you
bring your own public key infrastructure (PKI) to the platform or create a new
self-signed PKI within Prisma Access. This feature requires an issuing CA or forward
trust certificate (consisting of public and private keys) to generate new
certificates for visited sites and domains. Prisma Access requires that all
cryptographic secrets, including the TLS certificate private keys needed for SSL
decryption, are stored inside the configuration file that resides on the Prisma
Access service infrastructure and on each SPN that is part of the tenant. Some
Prisma Access customers prefer not to provide the TLS private keys on PA
infrastructure or reside on PA SPNs for SSL decryption operations (security and
compliance requirements).
Customizable Authentication Timers for Dynamic Privilege Access
Organizations with stringent security requirements need the ability to enforce
periodic validation to ensure continuous trust verification of user identities.
Dynamic Privilege Access-enabled Prisma® Access Agents already deliver continuous
trust verification today by seamlessly validating the user in the background without
disrupting the end-user experience. Augmenting this capability, Prisma Access Agent
now enables you to configure how frequently users are
prompted to re-authenticate, with customizable intervals ranging from 10 hours to 30
days. You can set customizable warning timers to notify users before
re-authentication is required, preventing unexpected disconnections and workflow
disruption. The feature introduces a re-authentication frequency setting that
controls user refresh token lifetime globally across your deployment. For stricter
security enforcement, you can enable aggressive authentication to force immediate
re-authentication when users connect or extend gateway sessions. The gateway session
timeout setting has been renamed for clarity and notification preferences are now
managed at the global level.
FedRAMP Moderate Support
The Federal Risk and Authorization Management Program (FedRAMP) is a United States
government-wide program that provides a standardized approach to security
assessment, authorization, and continuous monitoring for cloud products and services
for government users. Prisma Access demonstrates FedRAMP Moderate compliance.
This release adds FedRAMP Moderate support for the following
feature:
- Encrypted DNS. This feature is provided as a preview and is only available upon request. It enables Prisma Access to act as a DNS proxy, allowing Federal customers to meet CISA mandates by securely forwarding all external DNS traffic to CISA’s DNS service using DNS over HTTPs (DoH) or DNS over TLS (DoT) protocols, while maintaining split DNS for internal domains and providing the compliance logging required by OMB mandates.
Granular Data Profiles
|
Prisma Access support added in the Prisma Access 6.1.0
release.
|
Granular data profiles enhance your Enterprise Data Loss Prevention (E-DLP) detection capabilities by allowing you to apply
differentiated inline content inspection requirements and response actions within
the same Security policy rule. For example, you can use a single granular data
profile to block high-risk data patterns while alerting on lower-risk ones, set
varying log severities for different data profiles, and set specific file types for
each data profile included in the granular data profile.
Granular data profiles simplify policy rulebase management by consolidating multiple
rules into a single, more flexible Security policy rule. Furthermore, they reduce
false positive detections and allow your data security admins to achieve a more
nuanced approach to data protection that aligns closely with your organization's
risk management strategy while maintaining a lean and efficient Security policy
rulebase.
Regional Cloud Mapping Updates for Advanced WildFire
|
For the Prisma Access 6.1 release, Prisma Access Compute
locations for Spain, Saudi Arabia, and Qatar, point to their
respective regional WildFire cloud locations for sample
processing.
|
Many organizations face strict data residency requirements that mandate the local
processing and storage of security data. For certain Advanced WildFire customers
using Prisma Access in select regions, using the local Advanced WildFire cloud for
file analysis, can lead to potential non-compliance issues with regional regulatory
policies, preventing these customers from adopting the service.
To help you meet these regulatory obligations and ensure optimal performance, Prisma Access now automatically selects the
nearest and most compliant WildFire® region based on the Prisma Access Compute
location. This critical enhancement ensures all customer data processing
and storage automatically adheres to regional requirements.
The selection process is fully automated in the back end, using a static mapping
between your deployment region and the closest WildFire service instance. This
capability removes the operational burden of manual regional configuration and
guarantees that you receive the best possible security analysis experience from a
regionally compliant service instance. The focus is placed entirely on the value
gained: seamless compliance and better performance through automatic
configuration.
For the Prisma Access 6.1 release, Prisma Access Compute locations for Spain, Saudi
Arabia, and Qatar, point to their respective regional WildFire cloud locations for
sample processing.
Response Page Customization and Context Passing
|
Supported in:
Prisma Access 6.1 Preferred and Innovation with Strata Cloud Manager
|
The current response pages provided restricted
customization options, small buffer sizes, and complex workflows. For Prisma Access Mobile users, the customizable response pages
feature addresses the technical restrictions by expanding the response page size and
providing an intuitive upload interface for custom HTML templates. You can create
detailed response pages that include variables, stylesheets, images, and JavaScript,
which allows you to maintain brand consistency while clearly communicating
information to your users.
Using Internet Security policies, you can configure flexible match criteria based on
source (IP addresses, hostname, users/groups) and destination (IP addresses, URL
hostnames, URL category), and apply specific response pages for each scenario.
When users encounter blocked content or need to acknowledge policies, the response
pages now pass specific context, such as user identity, URL category, and rule
details. These enhancements deliver an improved administrative experience and create
a more consistent and informative experience for end users. The solution scaled to
support large deployments while maintaining performance across your security
infrastructure.
SASE Private Location
|
Supported in:
Prisma Access 6.1 Innovation
|
When regulatory compliance, data sovereignty, and geograpic location
prevent you from using external cloud infrastructure, SASE Private Location enables you to
deploy Prisma® Access services within your own infrastructure. This hybrid
deployment model addresses compliance, data sovereignty, and geographic location
requirements by keeping your network traffic and security processing within your
premises, eliminating the need to route data through external cloud infrastructure.
Using SASE private location, you can deploy agent-based Mobile Users in your data
center. You continue to manage configurations, policy rules, and monitoring through
the familiar Prisma Access UI.
Organizations in regulated industries, such as healthcare, financial
services, and government sectors, benefit from SASE Private Location. These
organizations often must comply with HIPAA regulations, data residency requirements,
or FedRAMP standards that prohibit sending traffic to external cloud services. You
can maintain the same Prisma Access security capabilities while ensuring that your
data never leaves your controlled environment. This approach is valuable when you
need low-latency access to critical applications or when your security policy rules
mandate that network security functions operate within your physical premises. Use
SASE Private Location when configuring your Prisma Access deployment to meet
stringent compliance requirements
The GlobalProtect® portal continues to operate from the cloud for global
accessibility, while the gateways run locally behind load balancers in your
environment, providing the optimal balance of centralized management and localized
performance.
SASE Private Location eliminates the traditional choice between cloud
managed security services and on-premises compliance requirements. You can achieve
regulatory compliance without sacrificing the operational benefits of cloud
management, automated updates, and centralized policy enforcement that characterize
modern SASE architectures. This capability becomes essential when your organization
requires air-gapped environments, operates in countries with strict data sovereignty
laws, or maintains corporate policies that restrict the use of external cloud
services for security functions.
Server-Initiated Traffic Flow for Prisma Access ZTNA Connector
Prisma® Access ZTNA Connector server-initiated traffic flow allows
applications running in your data center to initiate connections to remote
endpoints, solving a critical limitation where connections previously could only
flow from clients to servers. This feature enables your data center servers to
establish TCP, UDP, and ICMP connections to GlobalProtect® users, Remote Network hosts, and IP subnet hosts
in other ZTNA Connector data centers.
When you enable server-initiated traffic on a ZTNA Connector group, you
gain bidirectional communication capability without deploying separate Service
Connections, significantly reducing operational overhead. Your data center
applications can now proactively reach out to endpoints, which is essential for
remote troubleshooting, device management, patch distribution, and Voice Over
IP (VoIP) applications. For example, your IT helpdesk can use applications
like TeamViewer or LogMeIn to remotely access and troubleshoot user devices,
inventory management systems can scan and update remote endpoints, and VoIP servers
can initiate calls to users on managed devices.
The server-initiated feature integrates with your existing network
architecture through either static or dynamic routing. With dynamic BGP routing,
your data center routers automatically learn routes to permitted destinations,
simplifying network management. For security, you control which destinations your
servers can initiate connections to by selecting specific mobile user pools, remote
network prefixes, and ZTNA Connector IP subnet targets.
When server-initiated traffic is enabled, all outbound flows are
source-NATed with the ZTNA Connector’s IPsec tunnel interface IP, ensuring
consistent routing regardless of overlapping data center IP spaces. This approach
maintains compatibility with existing security policies while allowing you to
enforce more granular security through your data center firewall or at the
destination endpoints. The server-initiated traffic feature works seamlessly with
Dynamic DNS Updates, allowing data center applications to resolve connected
GlobalProtect users.
Tenant Control for Google Workspace Applications
Organizations face a critical data protection challenge in needing to permit access
to sanctioned corporate SaaS apps while blocking personal or unsanctioned instances
of the same app. To address this, we introduced a CASB/DLP enhancement, Tenant
Control for Google Workspace Applications. This session-tracking capability allows
the system to identify the specific Google tenant (such as corporate
your.company.com vs. personal gmail.com) a user is accessing. This enables
administrators to create granular policies that permit sanctioned Google Workspace
access while blocking or controlling personal accounts, directly preventing data
exfiltration. This feature requires an active SaaS Inline license. See SaaS policy rule recommendationsto help
you understand which Google Workspace applications are included in this feature and
how to enable this capability.
Service Provider Interconnect with Non-IPsec
The Service Provider Interconnect (SPI)
feature, formerly known as Service Provider Backbone (Cleanpipe), has been
transformed to support native IP ingress and high-bandwidth connectivity, enabling
service providers to deliver Prisma Access services more efficiently. With support
for up to 20 Gbps per tenant and 400 Gbps per interconnect, SPI eliminates IPsec
tunnel overhead and enhances throughput and scalability for large enterprise and
MPLS deployments. It also unlocks the complete Prisma Access feature set—including
ZTNA, CASB, and IoT Security—while maintaining strict multi-tenant isolation and
offering flexible egress options through either the service provider’s network or
Prisma Access-managed points.
Guided Configuration Workflow
The new Configuration Center provides a guided workflow that assists
administrators in the end-to-end configuration of interconnects. The workflow covers
all key stages, including ingress configuration involving cloud service provider
setup, interconnect configuration, VLAN and IP pool configuration, and egress path
definition. This guided process simplifies complex setup tasks and ensures accuracy
and consistency across all interconnect deployments.
Visibility and Monitoring Enhancements
Management and monitoring interfaces are enhanced to offer a unified,
centralized experience across all interconnects and associated tenants. You can:
- View interconnect type, operational status, and capacity utilization at a glance.
- Access detailed per-tenant insights on VLAN health, traffic usage, and routing states.
Prisma SASE 5G Advanced Monitoring
The Prisma 5G SASE feature has been enhanced
to deliver deeper monitoring, richer observability, and a more streamlined
configuration experience for both RADIUS and API-based integrations. The
configuration workflow is also enhanced and combined with the Service Provider
Interconnect (SPI) workflow, enabling administrators to configure and monitor 5G and
interconnect environments seamlessly from a unified interface.
Key Enhancements
Unified Configuration Workflow
- Administrators can define the connection type (RADIUS or API) during setup.
- Enables end-to-end configuration and monitoring across both 5G and SPI environments.
Enhanced 5G SASE Monitoring
- Existing monitoring capabilities are extended with dynamic metrics that adjust automatically based on the selected integration type.
- Provides detailed proxy and API usage metrics, including:
- Active, added, and cleared mappings.
- Connection and processing status for each interface.
New UE Mapping Tab
- Introduced within the SASE Monitoring feature to deliver comprehensive device-level visibility.
- Supports search and filter options for IMSI, IMEI, IP address, tenant, and region.
- Features a simplified UE Metrics Trend widget to track 5G registration and unknown IP trends, enabling quick analysis of user activity and connection patterns.
Remote Networks Enhanced with Non-IPsec Support
You can now configure Remote Networks using the
Service Provider Interconnect (SP Interconnect) option to enable Native IP
connectivity for high-bandwidth sites without relying on IPsec tunnels.
This capability streamlines the onboarding of large campus and branch networks while
supporting scalable, high-performance traffic flows.
During configuration, service providers can define key parameters such as
transport type, bandwidth, routing, and VLAN attachments to align with network
design and throughput needs. To ensure seamless bidirectional communication, static
routes must be created based on branch CIDRs and advertised by the Service Provider
colocation router, enabling efficient and reliable traffic exchange between Prisma
Access and customer networks.