Send Cortex XDR Risk Signals to Okta
Table of Contents
Expand all | Collapse all
-
- Cloud Identity Engine Attributes
- Collect Custom Attributes with the Cloud Identity Engine
- View Directory Data
- Cloud Identity Engine User Context
- Create a Cloud Dynamic User Group
- Configure Third-Party Device-ID
- Configure an IP Tag Cloud Connection
- View Mappings and Tags
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Send Cortex XDR Risk Signals to Okta
- Configure SSF Okta Receiver as a Risk Connection
- Configure the Secrets Vault
-
- Set Up Password Authentication
-
- Configure Azure as an IdP in the Cloud Identity Engine
- Configure Okta as an IdP in the Cloud Identity Engine
- Configure PingOne as an IdP in the Cloud Identity Engine
- Configure PingFederate as an IdP in the Cloud Identity Engine
- Configure Google as an IdP in the Cloud Identity Engine
- Configure a SAML 2.0-Compliant IdP in the Cloud Identity Engine
- Set Up a Client Certificate
- Configure an OIDC Authentication Type
- Set Up an Authentication Profile
- Configure Cloud Identity Engine Authentication on the Firewall or Panorama
- Configure the Cloud Identity Engine as a Mapping Source on the Firewall or Panorama
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Get Help
Send Cortex XDR Risk Signals to Okta
Share Cortex XDR user risk intelligence with Okta for coordinated and rapid responses
to security events.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can send user risk signals from Cortex XDR to Okta through the Shared
Signals Framework (SSF) Transmitter in Cloud Identity Engine (CIE). The SSF
Transmitter enables the exchange of the risks signals. The CIE functions as the
signal "transmitter" while Okta is the "receiver." All Cortex XDR risk signals sync
with the CIE and flow through the SSF stream to Okta. These signals indicate whether
a user's risk is low, medium, or high. Okta uses these signals along with its own
insights to enforce risk entity policy rules that you define.
For example, you can create a rule that logs users out of all active sessions and
supported applications when Okta detects high-risk user activity during an active
Okta session. By sharing risk intelligence between platforms, your security
infrastructure can respond to threats in a coordinated, rapid manner.
How The SSF Transmitter Works
- Cortex XDR detects high-risk user activity during an active Okta session. For example, a user risk level is now high.
- Cortex XDR syncs user risk and device risk data with the Cloud Identity Engine.
- The CIE receives this data and sends it to Okta as security events through the SSF Transmitter.
- Okta processes the signals as risk detection events and enforces risk-based policy rules.
- Sign in to the Cloud Identity Engine.Configure Cortex XDR as a risk source.This step enables Cortex XDR to sync user risk and device risk signals with the CIE.The Cortex XDR directory must be associated with the CIE already.
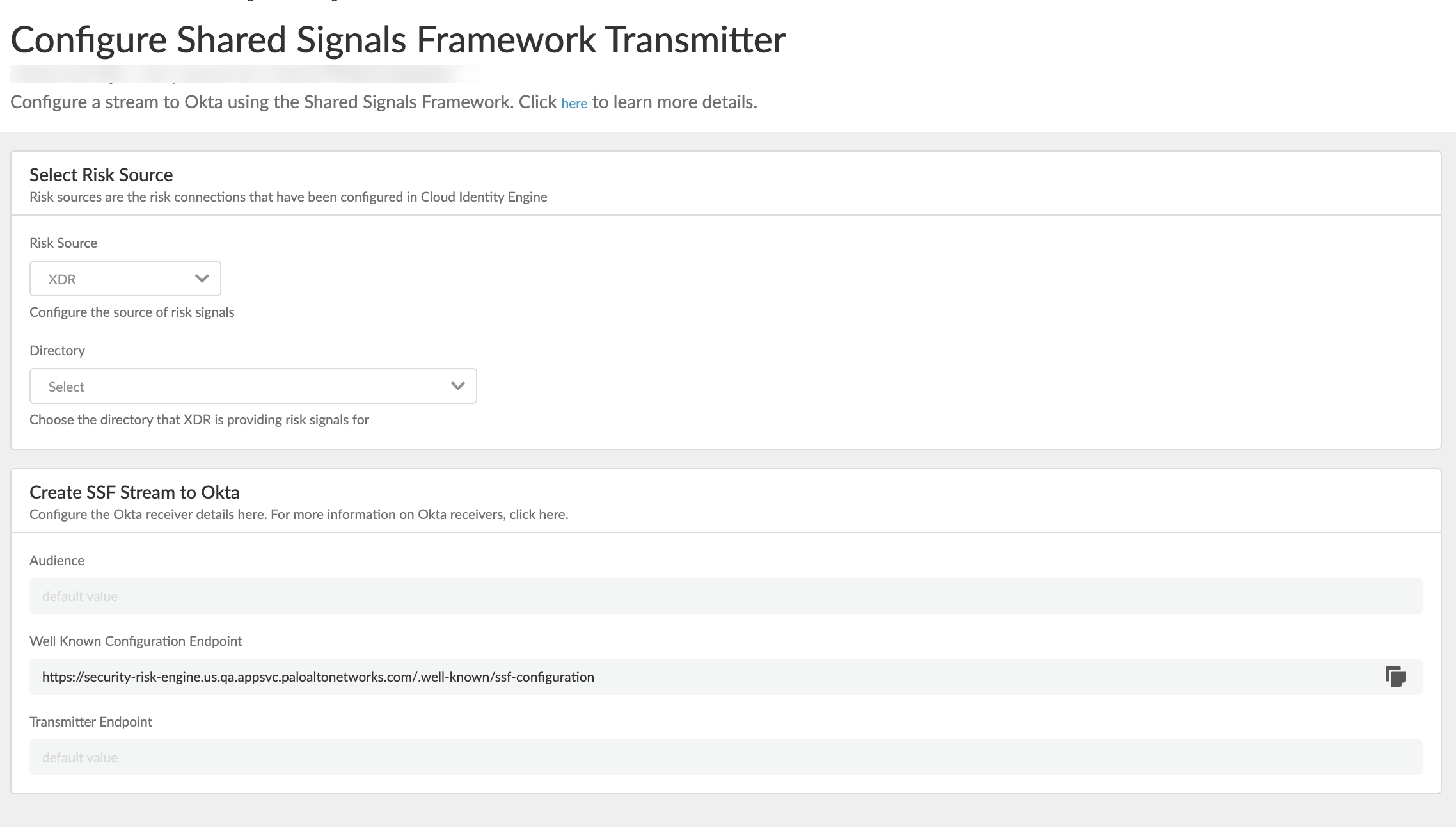
- Select Security RiskRisk Connections.Add a risk source.Connect Cortex, and then select an existing Cortex Directory.Click Continue.The Cortex directory you selected is added to the Risk Collection for Cortex.Configure the Shared Signals Framework Transmitter.
![]()
- Select Security RiskRisk Connections.Under Risk Sharing, Add the Shared Signals Framework Okta.The SSF Transmitter configuration window opens.For Risk Source, select XDR.For Directory, select the target Okta directory for Cortex XDR risk signals.Verify SSF stream details.The Create SSF Stream to Okta fields are pre-filled based on risk source, SSF transmitter, and SSF receiver details.
- Leave the Audience field as is.
- Copy the Well Known Configuration Endpoint value. You'll need this URL to set up Okta as a shared signal receiver.
- Verify that the Transmitter Endpoint value is your organization's Okta tenant address appended with /security/api/v1/security-events: your-org.okta.com/security/api/v1/security-events.
- Submit the configuration.SSF stream details are available for viewing under Risk Sharing. Find the stream of interest, and then click Actions View.
Configure your Okta tenant to receive shared signals.Paste the Well Known Configuration Endpoint value from the SSF transmitter configuration into the Well-known URL field in the Okta configuration.