Download PDF
Cloud NGFW for AWS
View Logs Natively in AWS
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
View Logs Natively in AWS
Configure Cloud NGFW for AWS logging.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
A log is an automatically generated, time-stamped file that provides an audit trail
for system events on the firewall or network traffic events that the firewall
monitors. Log entries contain artifacts, which are properties, activities, or
behaviors associated with the logged event, such as the application type or the IP
address of an attacker. Each log type records information for a separate event type.
For example, the firewall generates a Threat log to record traffic that matches a
spyware, vulnerability, or malware signature or a DoS attack that matches the
thresholds configured for a port scan or host sweep activity on the firewall.
The Cloud NGFW can send traffic, threat, and decryption logs to an S3 Bucket,
CloudWatch Log Group, or Kinesis Data Firehose. The names of these log destinations
must be included in the Cloud NGFW CloudFormation template (CFT) that is launched
when you add your Tenet admin AWS Account to the Cloud NGFW. The CloudWatch Log
Group and Kinesis Data Firehose have a default value of
PaloAltoCloudNGFW in the CFT. The S3 Bucket has no
default. The Cloud NGFW does not create these resources in your AWS environment. The
CFT gives the Cloud NGFW the permissions to write the logs to the destination. A
destination with the name you provided in the CFT must exist in your deployment to
successfully capture NGFW logs.
The CloudWatch log
group, S3 Bucket, CloudWatch namespace and the Kinesis stream should be
precreated in the CloudFormation template (CFT).
Log Types
Cloud NGFW can capture and save three types of logs.
- Traffic—Traffic logs display an entry for the start and end of each session. See Cloud NGFW for AWS Traffic Log Fields for more information.
- Threat—Threat logs display entries when traffic matches one of the Security Profiles attached to a security rule on the firewall. Each entry includes the following information: date and time; type of threat (such as malware or spyware); threat description or URL (Name column); alarm action (such as allow or block); and severity level.See Cloud NGFW for AWS Threat Log Fields for more information.
Severity Description CriticalSerious threats, such as those that affect default installations of widely deployed software, result in root compromise of servers, and the exploited code is widely available to attackers. The attacker usually does not need any special authentication credentials or knowledge about the individual victims and the target does not need to be manipulated into performing any special functions.HighThreats that have the ability to become critical but have mitigating factors; for example, they may be difficult to exploit, don't result in elevated privileges, or don't have a large victim pool.MediumMinor threats in which impact is minimized, such as DoS attacks that don't compromise the target or exploits that require an attacker to reside on the same LAN as the victim, affect only nonstandard configurations or obscure applications, or provide very limited access.LowWarning-level threats that have very little impact on an organization's infrastructure. They usually require local or physical system access and may often result in victim privacy or DoS issues and information leakage.InformationalSuspicious events that don't pose an immediate threat, but that are reported to call attention to deeper problems that could possibly exist. URL Filtering log entries are logged as Informational. Log entries with any verdict and an action set to block are logged as Informational. - Decryption—decryption logs display entries for unsuccessful TLS handshakes by default and can display entries for successful TLS handshakes if you enable them in the decryption policy. If you enable entries for successful handshakes, ensure that you have the system resources (log space) for the logs. See Cloud NGFW for AWS Decryption Log Fields for more information.
Log Destination
You have three choices of destinations for your
Cloud NGFW logs. These destinations all reside outside of the Cloud NGFW service
but within your AWS account—S3 bucket, Cloudwatch log group, or Kinesis data
firehose. Each log file is generated as a JSON file.
When you Subscribe to Cloud NGFW for
AWS, you're asked to set up your AWS CloudFormation template stack.
The stack prepopulates the logging destinations for CloudWatch log group and
Kinesis Data Firehose delivery stream with a destination called
PaloAltoCloudNGFW. The S3 Bucket field isn't
prepopulated. If you want to send the logs to a different destination, you must
create that destination and replace the default value the name before you
complete stack creation.
Each NGFW resource (displayed as the NGFW name in
the log stream name) outputs its logs into multiple streams (distinguished by the
string of random characters in the log stream name). Therefore, logs for a
particular Cloud NGFW resource might be spread across multiple streams.If you
send the logs to a CloudWatch log group, you can view the log entries directly
in the AWS CloudWatch console. In the CloudWatch log group you specify when
configuring logging, you will see a list of log streams. The log stream name is
displayed as:
/<aws-account-id>/<region>/<NGFW-name>/<random-string>/<log-type>.<year>.<month>.<day>.<hour>
For
example
/account123/us-west-1/firewall-1/qadd232312345dea/TRAFFIC.2022.02.10.Twenty-three
The <random string> refers to the individual NGFW resource that generated
the log.
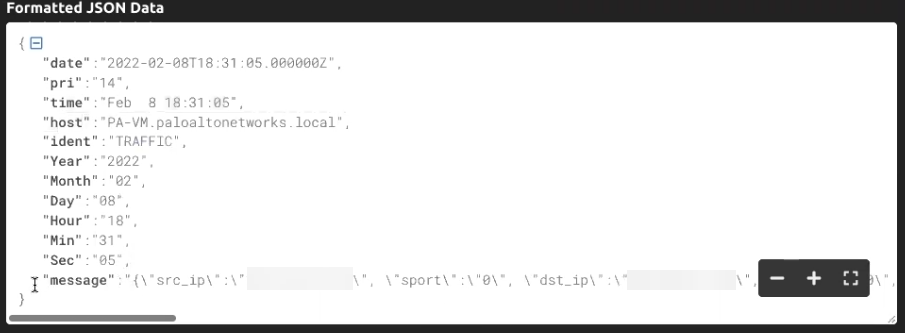
You can click on the stream name to view log entries, which are displayed
as shown in the following example.

If you send the logs to an S3 Bucket, the log files are saved as a JSON
file. The NGFW sends a new log file when one of the following criteria is
met—the firewall has generated 256 MB of logs or 10 minutes have elapsed since
the last log file was generated. To locate the files in the S3 Bucket you
specify, access the S3 console in AWS and find the bucket you specified. Then
select AWS-account-idregionNGFW-namelog-typeyearmonthdayhour. S3 bucket log file names adhere to the following format:
<aws-account-id>-<region>-<NGFW-name>-<log-type>-<year>-<month>-<day>-<hour>-<random-string>
The <random string> refers to the individual NGFW resource that generated
the log.
You can then download the file and use a JSON reader to view the logs in a
more readable format. In addition to the log information, each log entry also
contains a header that records the date, priority, time, firewall hostname, log
type, year, month, day, hour, minute, and second.
If you send log files to a Kinesis Firehose, logs are sent to the stream
name that you specify and then to the final destination; such as an S3 Bucket,
Datadog, or Splunk. The source for your Kinesis firehose must be Direct PUT
or other sources. In addition to the log information, each log entry
also contains a header that records the date, priority, time, firewall hostname,
log type, year, month, day, hour, minute, second, region, firewall name, and AWS
account ID. The NGFW adds the region, firewall name, and AWS account ID to the
logs to help identify where the log was generated because this information isn't
included in the log file name. You can then download the JSON file for viewing.
The times and dates recorded in log entries and log file names are displayed
in UTC time. However, the log dates displayed in the AWS console are
displayed in your local time and date.
Enable Log Settings in the Cloud NGFW console
If you have previously started from an AWS member account or AWS Firewall Manager account, you can
access the Cloud NGFW console to enable AWS log destinations.
If you have previously started from an AWS member account and created
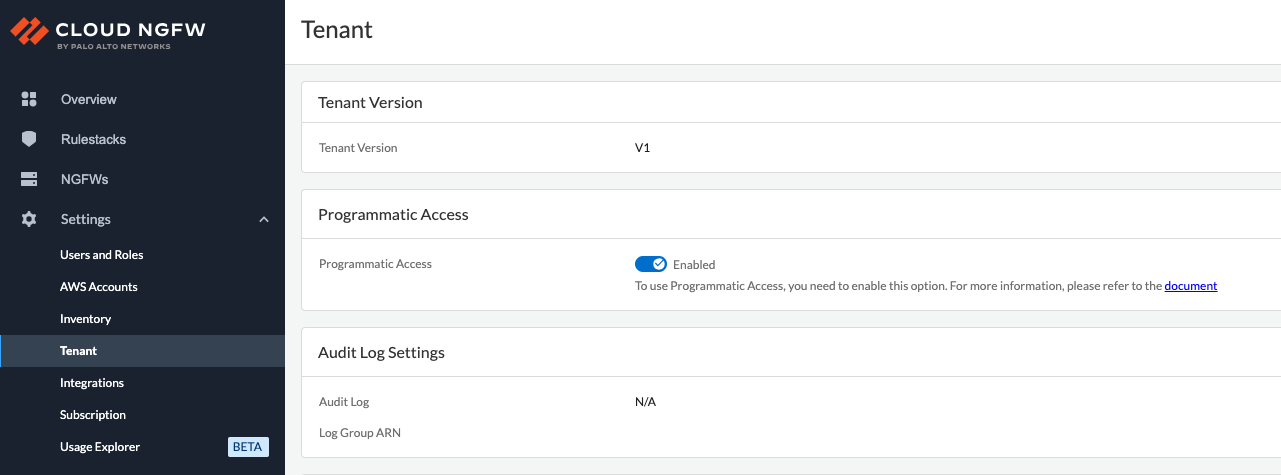
the Cloud NGFW tenant before Jul 30, 2025, the tenant information page will
display the tenant version as V1. However, if you started from an AWS member
account after Jul 30, 2025, the tenant information page will display the tenant
version as V2.
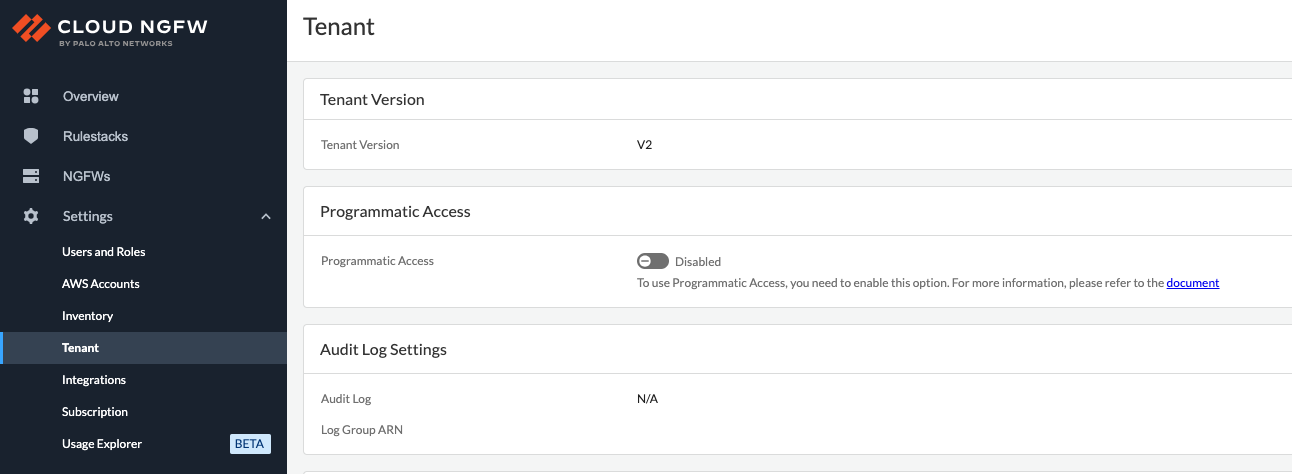
For Cloud NGFW tenants created after July 30, 2025
(V2 tenants), audit logging is currently unavailable for certain UI
and core firewall management APIs. Actions performed through the firewall
list and firewall details pages in the UI (e.g., viewing the list of
firewalls), or via the corresponding APIs, will not generate audit log
entries.
Following are the affected firewall management
APIs:
POST /ngfirewalls (create ngfirewall) GET /ngfirewalls (list ngfirewalls) GET /ngfirewalls/{firewall_id} (read ngfirewall) PATCH /ngfirewalls/{firewall_id} (update ngfirewall) DELETE /ngfirewalls/{firewall_id} (delete ngfirewall) POST /ngfirewalls/{firewall_id}/link (associate fw link) DELETE /ngfirewalls/{firewall_id}/link (disassociate fw link) POST /ngfirewalls/{firewall_id}/rulestack (associate rulestack) DELETE /ngfirewalls/{firewall_id}/rulestack (disassociate rulestack) GET /ngfirewalls/{firewall_id}/logprofile (read logprofile) POST /ngfirewalls/{firewall_id}/logprofile (update logprofile)
V1 Tenants
- Log in to the Cloud NGFW console.
![]() Select NGFWs and select the firewall on which to configure logging.Select Log Settings.Under Log Type, select one or more option log type to be captured.You have the option to send all logs to the same destination or choose a different destination for each log type.Select the Log Destination. If you're selecting more than one log type, you must select the destination individually for each log type.Enter the Log Destination name. The log destination name is a must.Click Save.
Select NGFWs and select the firewall on which to configure logging.Select Log Settings.Under Log Type, select one or more option log type to be captured.You have the option to send all logs to the same destination or choose a different destination for each log type.Select the Log Destination. If you're selecting more than one log type, you must select the destination individually for each log type.Enter the Log Destination name. The log destination name is a must.Click Save.V2 Tenants
- Log in to the Cloud NGFW console.
![]() Select NGFWs and select the firewall on which to configure logging.Select Log Settings.Under Log Destination Type, select one option.If you select S3 as the log destination, you can specify the S3 bucket ARN. This step assumes that you have previously created resource-level (bucket) policies to add permissions on the S3 bucket that provides access to the Cloud NGFW account (Account ID 124755910362)If you select Cloudwatch Log Group or Kinesis Data FireHose as the log destination, you can specify the name of the resource. This step assumes that you have previously onboarded AWS accounts (where these AWS destinations are present) to establish the cross-account IAM permissions to access the Cloudwatch Log Group or Kinesis.Click Save.
Select NGFWs and select the firewall on which to configure logging.Select Log Settings.Under Log Destination Type, select one option.If you select S3 as the log destination, you can specify the S3 bucket ARN. This step assumes that you have previously created resource-level (bucket) policies to add permissions on the S3 bucket that provides access to the Cloud NGFW account (Account ID 124755910362)If you select Cloudwatch Log Group or Kinesis Data FireHose as the log destination, you can specify the name of the resource. This step assumes that you have previously onboarded AWS accounts (where these AWS destinations are present) to establish the cross-account IAM permissions to access the Cloudwatch Log Group or Kinesis.Click Save.Enable Logs in the Strata Cloud Manager console
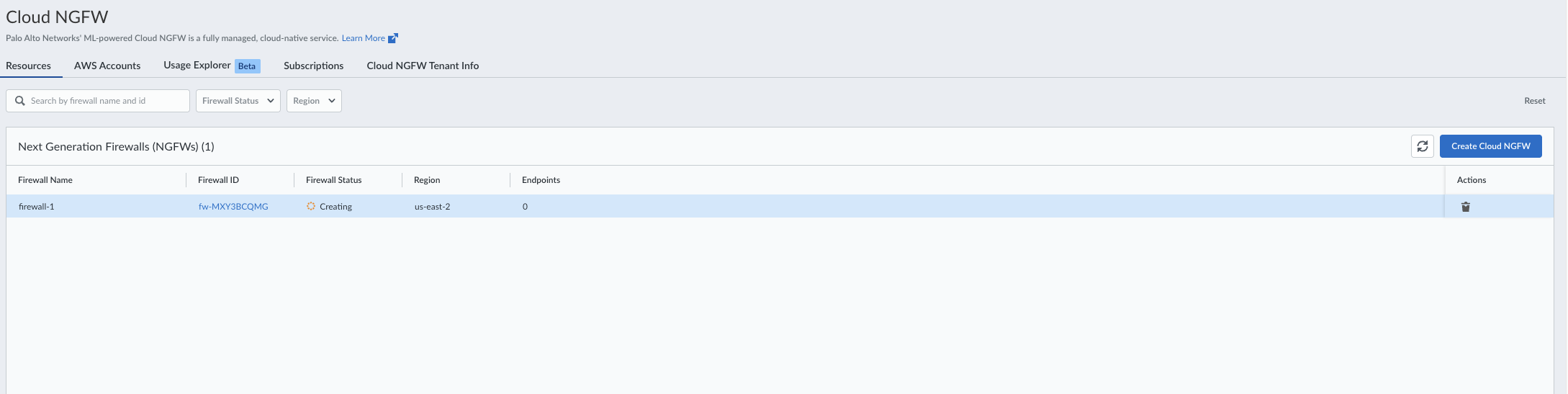
If you have previously started from Strata Cloud Manager, you can access the Cloud NGFW page in the Strata Cloud Manager console to enable logs.Enable Traffic & Threat Logs for AWS Destinations
If you have previously started from Strata Cloud Manager, you can access the Cloud NGFW page in the Strata Cloud Manager console to enable AWS log destinations.- Log in to the SCM Console.Go to Configurations > Cloud NGFWs.Select the CNGFW resource.
![]() If you select S3 as the log destination, you can specify the S3 bucket ARN. This step assumes that you have previously created resource-level (bucket) policies to add permissions on the S3 bucket that provides access to the Cloud NGFW account (124755910362)If you select Cloudwatch Log Group or Kinesis Data FireHose as the log destination, you can specify the name of the resource. This step assumes that you have previously onboarded the AWS account (where these AWS destinations are present) to establish the cross-account IAM permissions to access the Cloudwatch Log Group or Kinesis Data FireHose.Click Save.
If you select S3 as the log destination, you can specify the S3 bucket ARN. This step assumes that you have previously created resource-level (bucket) policies to add permissions on the S3 bucket that provides access to the Cloud NGFW account (124755910362)If you select Cloudwatch Log Group or Kinesis Data FireHose as the log destination, you can specify the name of the resource. This step assumes that you have previously onboarded the AWS account (where these AWS destinations are present) to establish the cross-account IAM permissions to access the Cloudwatch Log Group or Kinesis Data FireHose.Click Save.![]()
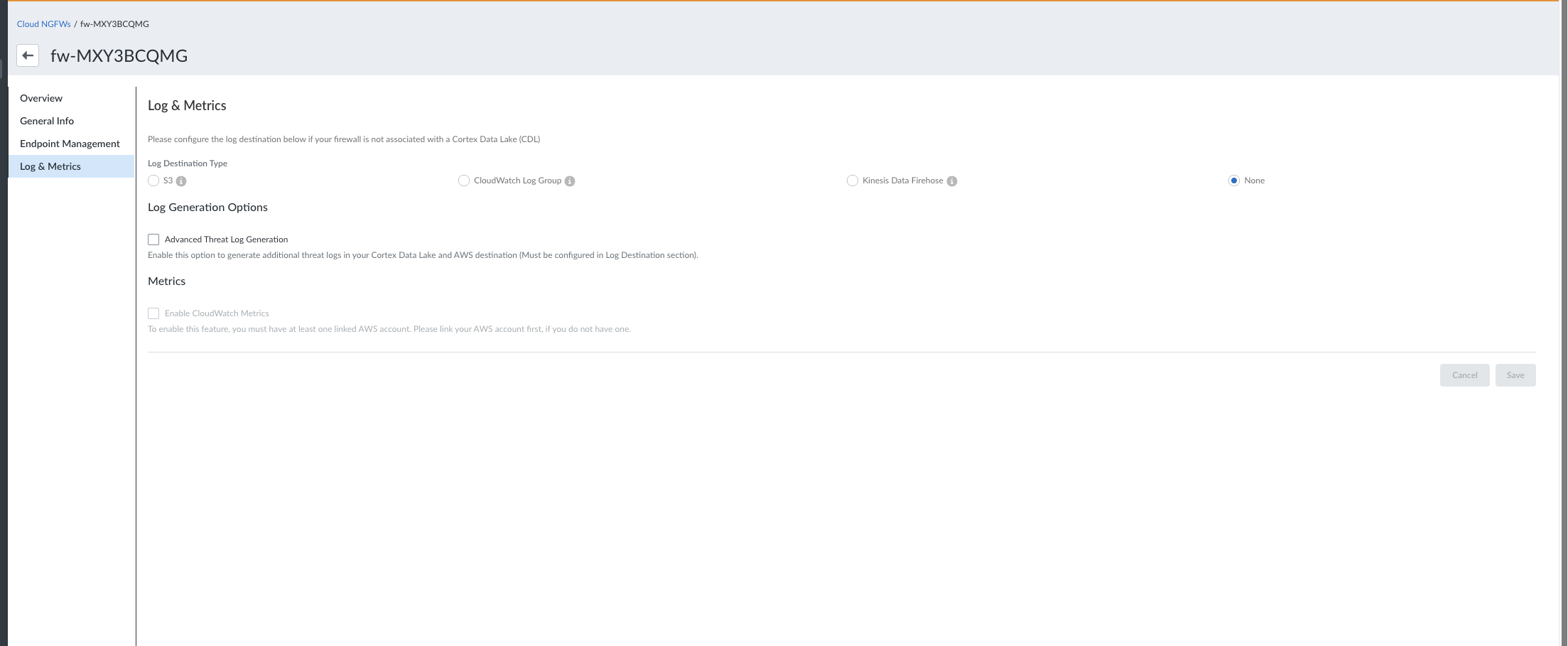
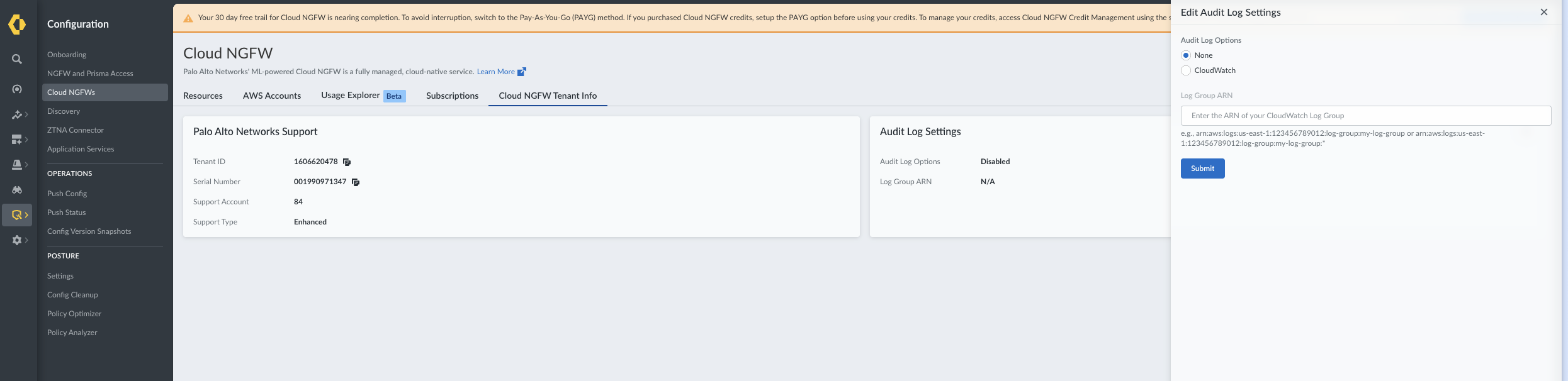
Enable Audit Logs for AWS Destinations
- Log in to the SCM console.Go to Configurations > Cloud NGFWs.Click Cloud NGFW Tenant Info.In Audit Log Settings section, click Settings icon.
![]() Under Log Destination Type, select Cloudwatch option.The Log Group ARN must be the same as the allowed log group ARN in your CNGFW account.Click Submit.
Under Log Destination Type, select Cloudwatch option.The Log Group ARN must be the same as the allowed log group ARN in your CNGFW account.Click Submit.View Cloud NGFW Logs in the Strata Cloud Manager console
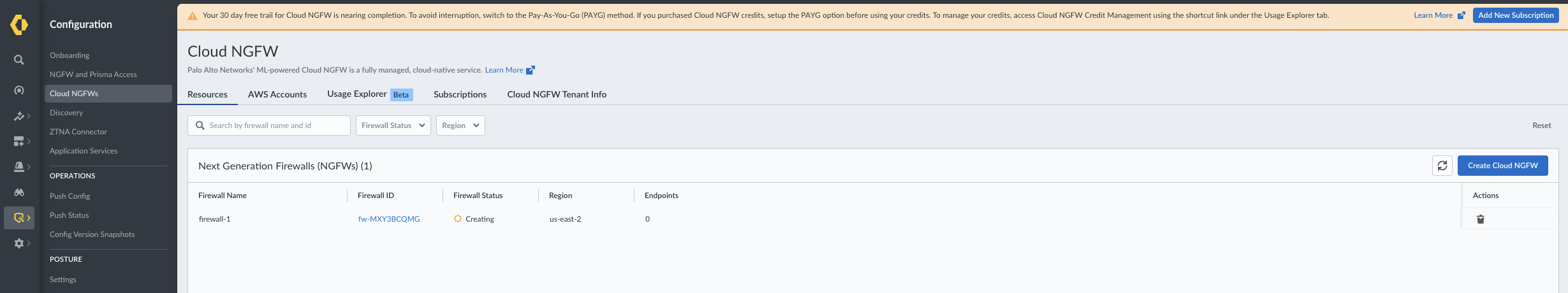
- Log in to the Strata Cloud Manager (SCM) console.Go to Configurations > Cloud NGFWs. This will display the list of your Cloud NGFW resources.
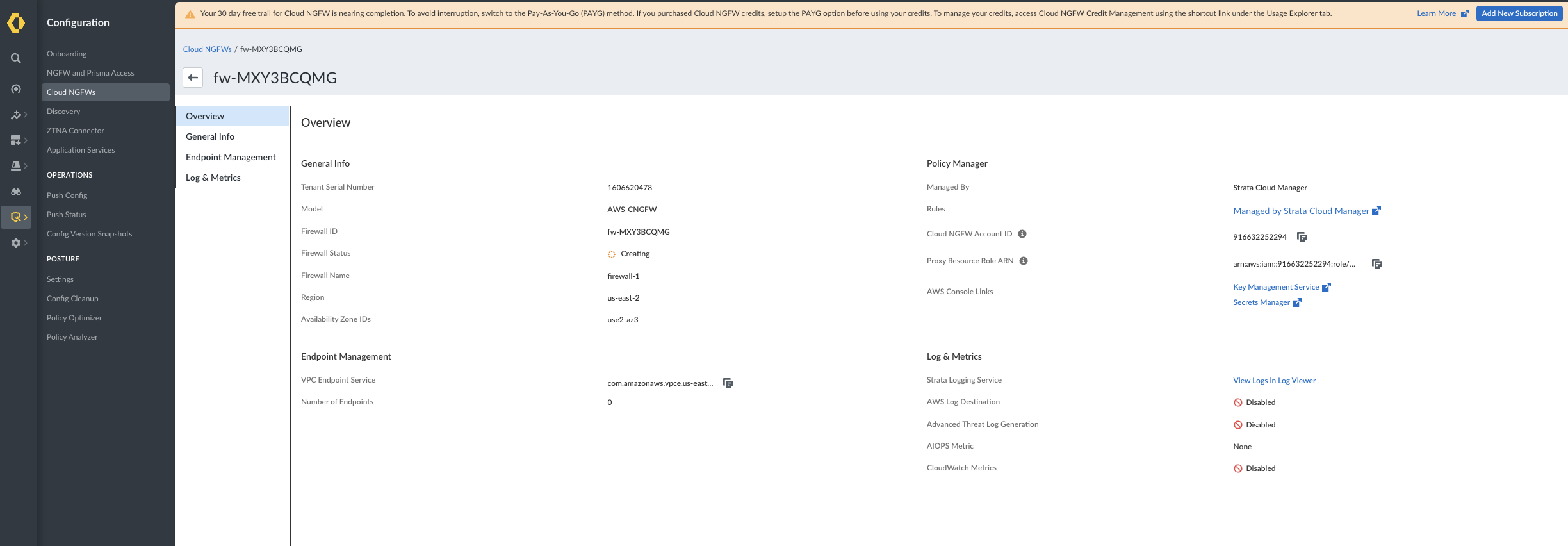
![]() Click Firewall ID of the specific Cloud NGFW resource you want to view. This opens the detailed overview page for that particular firewall.
Click Firewall ID of the specific Cloud NGFW resource you want to view. This opens the detailed overview page for that particular firewall.![]() Click View Logs link on the overview panel.
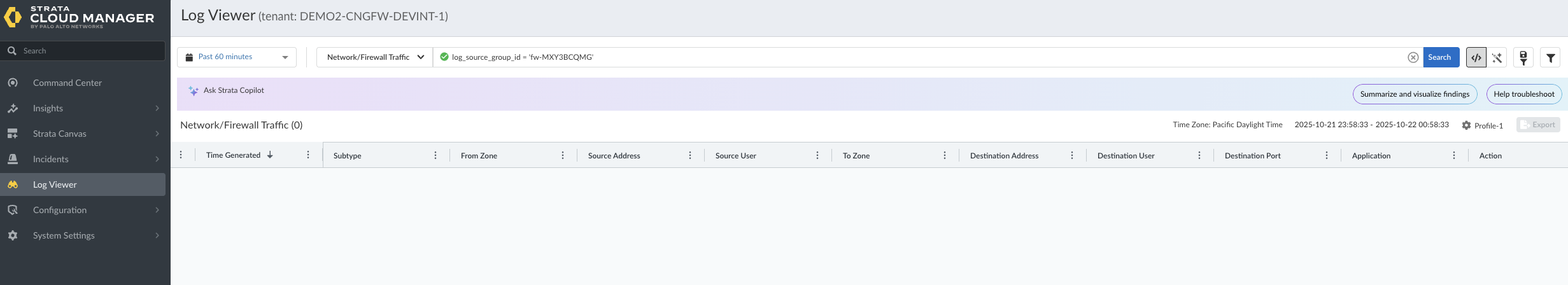
Click View Logs link on the overview panel.![]() This action will open the Log Viewer, typically in a new tab, and it will be automatically filtered to show the logs specifically for the Cloud NGFW resource you selected in step 3.
This action will open the Log Viewer, typically in a new tab, and it will be automatically filtered to show the logs specifically for the Cloud NGFW resource you selected in step 3.