Download PDF
Cloud NGFW for AWS
Add a Certificate to Cloud NGFW for AWS
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Add a Certificate to Cloud NGFW for AWS
Learn how to add a certificate to the Cloud NGFW for AWS.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Cloud NGFW uses certificates to access an intelligent feed and to enable inbound and
outbound decryption. These certificates are stored in the AWS Secrets Manager.
There are three types of certificates used in a typical deployment.
- Intermediate CA Certificate (CA Certificate)—A certificate authority (CA) is a trusted organization that issues SSL certificates. These digital certificates are files used to link an entity to a public key. Web browsers use these certificates to authenticate content sent from web servers. Web browsers normally come with lists of CAs that they implicitly trust to identify hosts. The purpose of CA is to verify the authenticity of the website, domain, or organizations.
- Server Certificate—A certificate associated with a specific domain name.
If a website has a valid certificate, it means that a certificate authority has
taken steps to verify that the web address actually belongs to that
organization. When you type a URL your browser checks the certificate to make
sure that the website address matches the address on the certificate. It also
makes sure the certificate is signed by a trusted certificate authority.You may occasionally connect to a server with an untrusted certificate. Cloud NGFW for AWS will drop the connection as if the server terminated the connection.
- Root CA Certificate—A certificate authority can issue multiple certificates in the form of a tree structure. A root certificate is the top-most certificate of the tree.
When adding a certificate to the AWS Secrets Manager for use with Cloud NGFW, the
following prerequisites must be met.
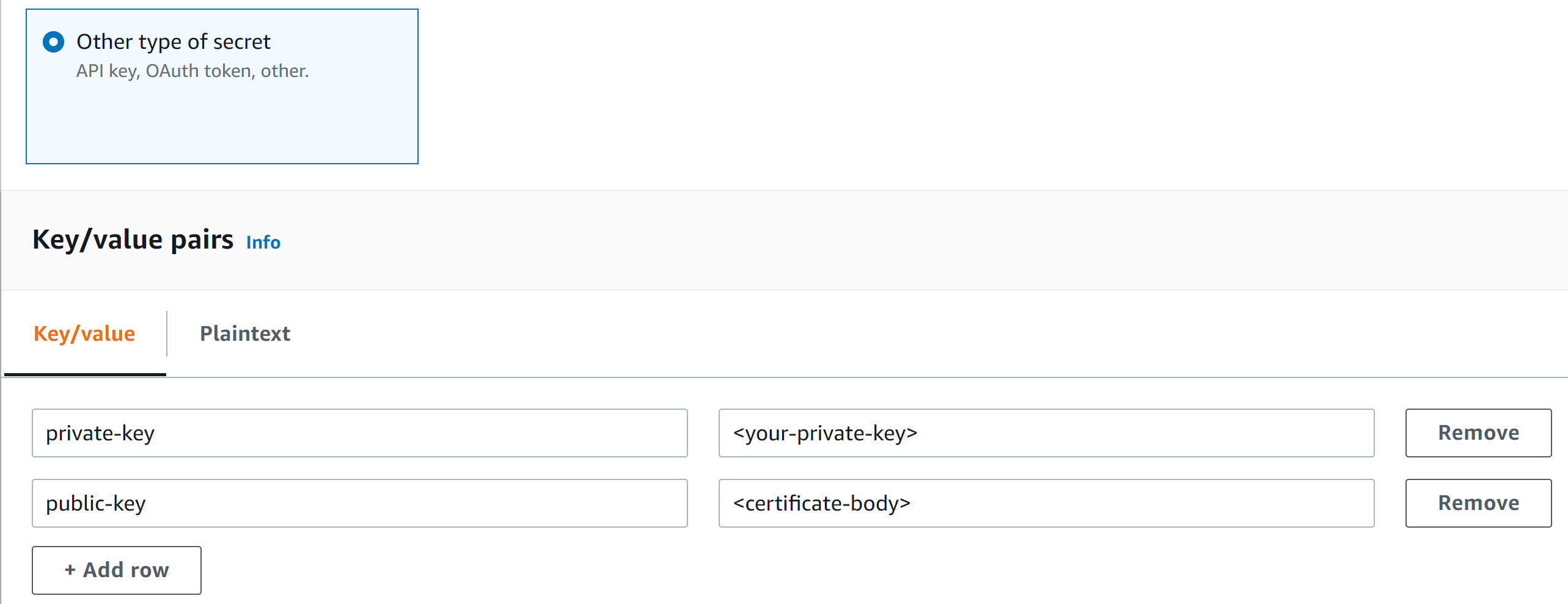
- Certificate added as a key or value pair, with two keys—private-key and public-key. For the private key, the value should be the actual key and, for the public-key, the value should be the actual certificate body.
- A tag with the key PaloAltoCloudNGFW and value of true.
- Import the root CA certificate and Intermediate CA certificates to the trust store of the client.
- If you're using end-entity certificates for decrypting traffic, only the end-entity certificates (both private and public keys) must be stored in the AWS Secrets Manager.
- PKCS8 private key format is supported. PKCS1 private key format isn't supported.
Supported PKCS format:
-----BEGIN PRIVATE KEY----- -----END PRIVATE KEY-----
Unsupported PKCS1 format:
-----BEGIN RSA PRIVATE KEY----- -----END RSA PRIVATE KEY-----
Complete the following procedure to add a certificate for use with Cloud NGFW for
AWS.
- Add your certificate to the AWS Secrets Manager.
- Log in to the AWS console, navigate to the AWS Secrets Manager, and click Store a new secret.Select Other type of secret.Under Key and value pairs, create a key called private-key and another called public-key.Paste your entire private key and entire public key in the corresponding field.
![]() Click Next.Enter a descriptive Secret Name.Add a tag with the Key PaloAltoCloudNGFW and Value true.
Click Next.Enter a descriptive Secret Name.Add a tag with the Key PaloAltoCloudNGFW and Value true.![]() Click Next, Next again, and Store to finishing adding your certificate.Select Rulestacks and select a previously created rulestack on which to configure a certificate.Select ObjectsCertificate ListAdd Certificate.Enter a descriptive Name for your certificate.(Optional) Enter a description for your certificate.Select a certificate.
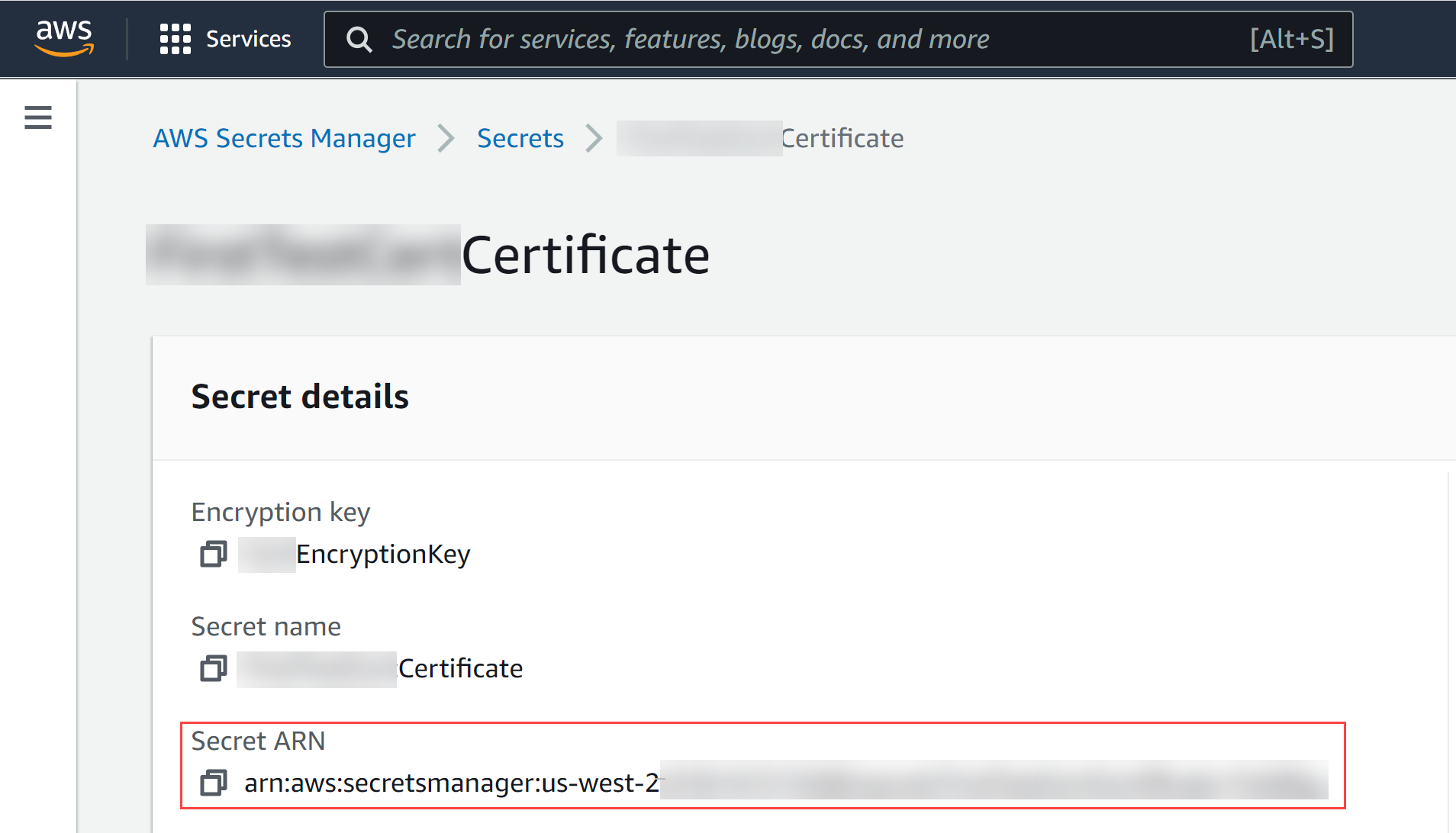
Click Next, Next again, and Store to finishing adding your certificate.Select Rulestacks and select a previously created rulestack on which to configure a certificate.Select ObjectsCertificate ListAdd Certificate.Enter a descriptive Name for your certificate.(Optional) Enter a description for your certificate.Select a certificate.- Enter the Certificate ARN if you want Cloud NGFW
to download the certificate from AWS Secrets Manager.
![]()
- Check Self Signed Certificate if you want Cloud NGFW to create a self-signed certificate.
Click Save.