Device Security
Offboard Device Security Subscriptions
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Offboard Device Security Subscriptions
Deactivate Device Security licenses, transfer Device Security subscriptions, or let
them expire.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
There are three ways to offboard Device Security services from a firewall:
- Deactivate the Device Security license on a firewall and optionally transfer it to another firewall
- Transfer a firewall from one customer support portal (CSP) account to another
- Let the subscription expire
Deactivate Firewalls and Transfer Licenses
If you want to remove an Device Security license
from a firewall—and perhaps then use the license on another firewall—you
can do so on the Customer Support Portal.
- Log in to your Customer Support Portal account.Disassociate Device Security licenses from one or more firewalls.
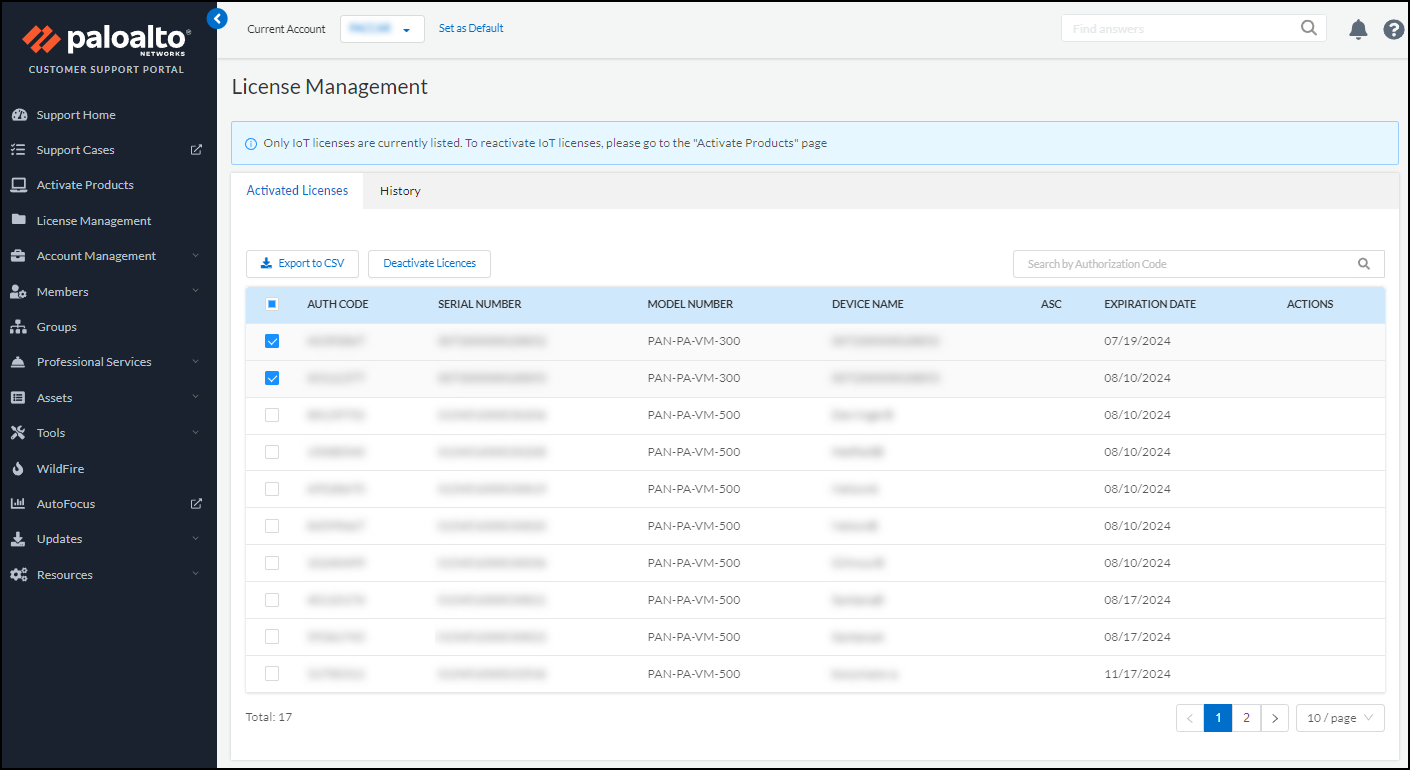
- Select License ManagementActivated Licenses, select the license-to-firewall associations that you want to sever based on firewall serial numbers, and then Deactivate Licenses.
![]()
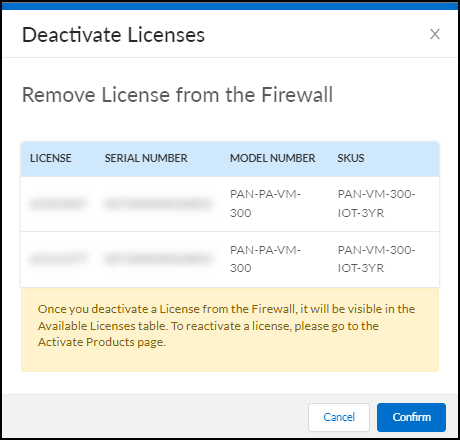
- Confirm the deactivation.If you want to apply the deactivated licenses to other firewalls and you have multiple Device Security license purchase orders, note the number of available licenses in the orders on the Activate Products page before confirming the deactivation. Then when you return to this page after deactivating licenses, you can tell which order they were returned to because the license number will have increased.
![]() This dissociates the selected Device Security licenses from the firewall serial numbers and returns them to the pool of available licenses in the original order on the Activate Products page.
This dissociates the selected Device Security licenses from the firewall serial numbers and returns them to the pool of available licenses in the original order on the Activate Products page.
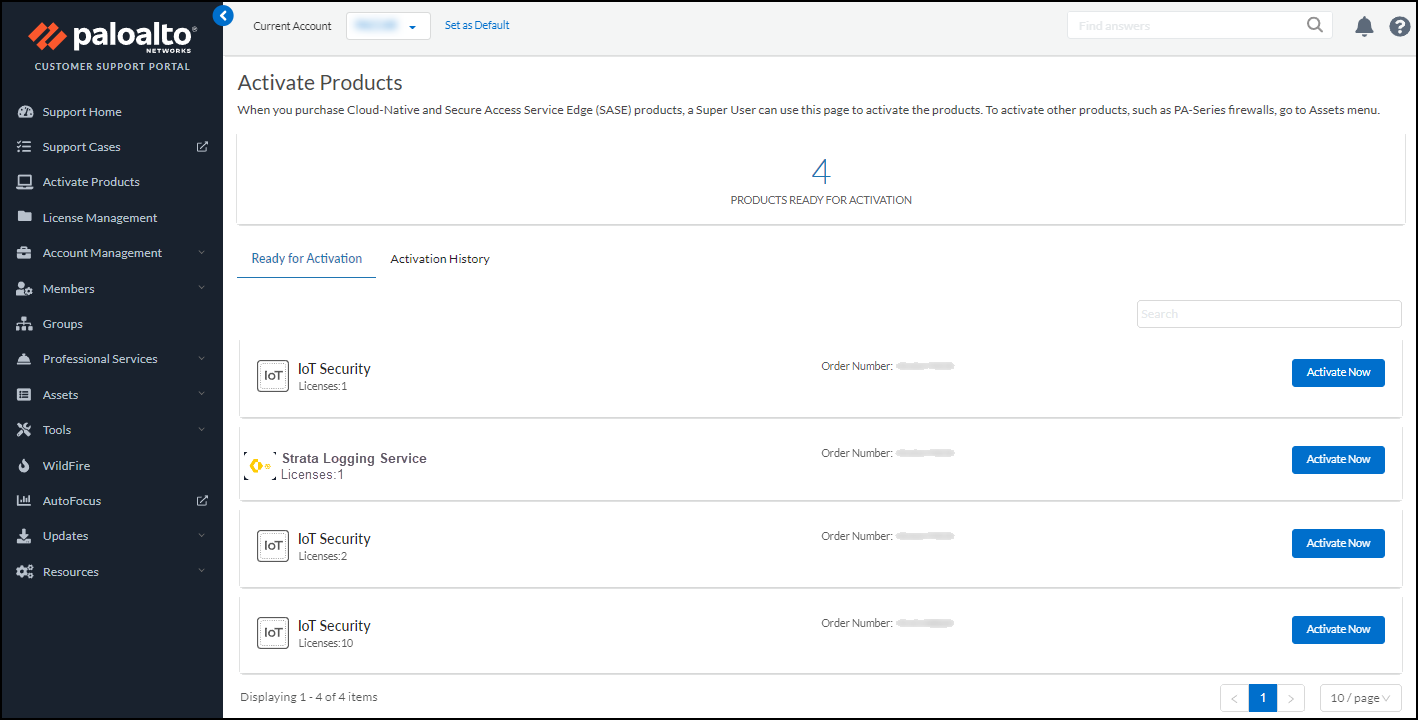
Verify that the Hub also shows that the Device Security licenses disassociated from the firewalls.Both the Device Security license and the firewall need to be disassociated on the Hub. If the Device Security license and the firewalls still show as associated on the Hub, reach out to Palo Alto Networks support.Associate licenses with other firewalls or reassociate them with the same firewalls.- Select Activate ProductsReady for Activation and then click Activate Now for the order with licenses to activate.
![]()
- Follow the workflow described in Onboard Device Security.When you reach the point in the onboarding workflow when you select firewalls to subscribe to Device Security, you can see the length of time remaining for each license in the Purchased Term drop-down list. If you want to apply the same license that you just deactivated to another firewall, you’ll notice that its remaining length of unused time will be shorter than other licenses that haven’t yet been put in service. For example, if the original order contains licenses valid for three years and you used a license for one year before deactivating it, you can easily spot it because its remaining validity period will be the only one listed as just two years.
Transfer Firewalls between CSP Accounts
If you have two CSP accounts or are an MSSP managing multiple accounts, you can transfer a firewall from one account to another, perhaps because you’re moving it to a different location managed by a different team with their own account. When you transfer the firewall, all its licenses are transferred along with it. To do this, log in to the CSP and click Devices. Find the device you want to transfer, click its serial number to open a device details pane for it, and then click Transfer Ownership. In the Device Transfer dialog box that appears, enter the destination email address of the owner of the account to which you’re transferring the firewall.Let the Device Security Subscription Expire
When a firewall no longer has an Device Security subscription because it expired (and there is no pending license renewal), Device Security services for that firewall stop and the connection between IoT Security and the firewall is terminated. Device Security unsubscribes from the firewall log feed. As a result, it stops receiving and processing logs from that firewall. The firewall stops receiving new policy recommendations and IP address-to-device mappings, and it clears its cached mappings after 200 minutes (about three hours). At that point, none of the device-based policy rules using Device-ID will work and should be removed from your policy set. An efficient way to remove them is to check the Source Device and Destination Device columns on the PoliciesSecurity page and remove all rules that have entries in either of these two columns.