Device Security
Networks
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Networks
Device Security organizes subnets and CIDR blocks hierarchically
to improve navigation of your network topology.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
|
Device Security learns about the addressing scheme on your
network through several means. You can add subnets and Classless Inter-Domain
Routing (CIDR) blocks manually, even specifying if a subnet contains
devices that have static IP addresses. Device Security can discover
subnets by observing the exchanges between DHCP clients and servers.
Device Security can learn about subnets through third-party integrations
with network switches, using SNMP for network discovery.
It can also learn about subnets and CIDR blocks through IP Address
Management (IPAM) integrations with BlueCat and Infoblox.
As Device Security gathers network information, it organizes it hierarchically and displays the
subnets and blocks on the Networks page. If you are using
Device Security in Strata Cloud Manager, navigate to NetworksNetworks.
If you are using the Device Security portal, navigate to NetworksNetworks and SitesNetworks. Blocks are logical partitions of IP address space that serve as an
organizational tool for managing addresses. Large “parent” blocks can contain smaller
“child” blocks and subnets, where devices are found. Another conceptual grouping is
“remainders”. These are sets of IP addresses within a block that don’t belong to either
a subnet or child block.
At the top of the Networks page are two panels that provide a high-level view of your
network and how different types of devices are distributed throughout it. The Overview
panel is divided in two sections. On the left is the overall number of “networks”, which
is really a collection of all the network elements (blocks, subnets, and remainders) in
your network, and the total number of subnets in your network. On the right of the
Overview panel is the total number of network elements at a particular level. If you
don’t select an entry in the Prefix column of a block in the Networks table, the current
level shows the total number of blocks and subnets at the root level. For example, the
following Overview panel shows that there are 342 networks (various blocks, subnets, and
remainders) of which 332 are subnets. At the current (root) level, there are 24 networks
(blocks and subnets) consisting of 18 subnets and 6 blocks (24-18).

If you select one of the blocks by clicking the entry for it in the Prefix column in the
Networks table, the overall totals stay the same but the totals in the current level
changes to show the subnets, child blocks, and remainders within the selected block.

To see the elements in a child block, select the entry in the Prefix column. To
return to the root level, click Networks (number) in the
breadcrumbs above the Networks table.
The other panel at the top of the Networks page contains a bar chart showing
the distribution of device types in each subnet.
The number in parentheses after “Subnet Distribution by Device Type” is the
total number of subnets with active devices during the time period set in the filter at
the top of the page. The overall number of subnets in the left panel is for all subnets
regardless of whether Device Security detects device activity in them. Device Security can
learn about subnets without detecting device activity by various means:
- User-configured subnets in the Device Security portal
- User-initiated uploads of subnet configurations in .csv files
- Third-party integration using SNMP for network discovery
- Third-party integrations with IP Address Management (IPAM) solutions from BlueCat or Infoblox
- Detection of IP endpoints but not devices in subnets
- Detection of past device activity in subnets that are inactive during a shorter time period filter set on the Networks page
The total number of subnets in the two panels might be the same if Device Security detects
device activity in every subnet of which it’s aware, but most likely the totals are
different.
Hover your cursor over one of the bars to see an information pop-up listing the
device types in this subnet. For example, the 10.54.0.0/23 subnet shown below has one
office device in a subnet that otherwise consists of only network devices. It
immediately suggests that the office device might be misplaced on the network.

Click the subnet on the left of the bar chart to see the Subnet Detail panel. By default,
device types are shown. To see the device categories and device profiles, click the
Category and Profile tab.

To see details about one type of devices in a subnet, such as the one office device,
click the number in the QTY (Quantity) column. Device Security opens
the AssetsDevices page filtered to show the device or devices selected. Then click the name
of a particular device to see the Device Details page for it.
In the Networks table, Device Security displays all the blocks and subnets it has been configured
with, discovered, and learned through third-party integrations on the Networks page.
When a “parent” block has other blocks and subnets nested below it, the number of its
“children” is shown parenthetically. To see these blocks click the prefix of the block
containing it.

For example, if you click the 192.168.0.0/16 block
in the screen capture above, Device Security displays a list of the
blocks and subnets within it.

Notice how it contains 18 blocks and subnets and that some of
the blocks have parenthetical numbers after them, indicating that
there are other smaller blocks and subnets beneath them. You can
continue to move downward to lower levels in the hierarchy by clicking
the prefix of any block that has a parenthetical number after it.
To move upward, click a higher level in the breadcrumb trail at
the top of the page.
The Networks page mainly consists of a table presenting a hierarchical
view of your network and attributes of the blocks and subnets that
constitute it.

Type: There are several types of network grouping categories:
- Subnet – A network section with a broadcast domain and gateway.
- IP Block – A partition of IP address space that can logically contain other blocks and subnets.Shared IP Block – An IP block whose space is partitioned into at least one subnet that's reused in different shared network segments. This results in devices with overlapping IP addresses on the same network. For example, you might use the same subnet for guest traffic in multiple network segments throughout your network. In this case, you would first make a list of firewalls and where they are on the network, perhaps at the same site or at different sites. Next, you'd plan out how to group the firewalls into different network segments and assign each firewall and site to a particular segment. Finally, you'd define the IP block containing the guest subnet as a shared IP block. Device Security can now automatically detect which network segment an IP address comes from based on its shared IP block and the firewall that sent the log containing the address.Non-shared IP Block – An IP block whose space is partitioned into smaller blocks and subnets that are unique in your network. IP addresses in non-shared IP blocks are used in only one network segment in your network.
- Remainder – All IP addresses that aren't in more specific IP blocks or subnets contained within a larger, superset block.
- Network Segment – A logical grouping of one or more firewalls plus an IP block. When firewalls send traffic logs, Device Security identifies which network segment a device belongs to by the IP block that its IP address is in + the firewall that sent the log. In this way, the logs uniquely identify each device even when it's using the same IP address as another device in a different network segment.
Name, VLAN, and Description:
When manually adding blocks and subnets in the Device Security portal,
you can include a name and description and, for subnets, a VLAN.
Device Security can also learn these attributes through third-party
integrations. BlueCat IPAM integrations can provide a name for a
block or subnet. SNMP and Infoblox IPAM integrations can provide
the VLAN for a subnet. An Infoblox IPAM integration can provide
a description.
You can later modify the VLAN and description but not the
name.
Zone: A zone represents a logical grouping of physical and virtual
interfaces on the firewall to control and log traffic. Device Security learns about
zones from your firewalls through
firewall device telemetry.
Monitored: Yes or No means
a network has devices whose network activity Device Security is monitoring
or not.
Categories and Profiles:
The number of device categories (such as Personal Computer or IP
Phone) and the device profiles (such as PC-Windows and Poly IP Phone)
in a subnet.
Source: There are several ways that a
block or subnet can be added to Device Security. This column shows
where each block or subnet comes from. The following are the possible
sources:
- Discovered – Device Security discovered a subnet by observing network traffic.
- Config – A user manually configured an IP block or subnet.
- Preconfig – An IP block was preconfigured by Device Security and cannot be removed. For example, the 10.0.0.0/8 Class A private block.
- BlueCat IPAM – Device Security learned an IP block or subnet through integration with BlueCat IPAM.
- Infoblox IPAM – Device Security learned an IP block or subnet through integration with Infoblox IPAM.
- Network Discovery SNMP – Device Security learned an IP block or subnet by using SNMP to discover network information from switches.
IP Endpoints: IP Endpoints are devices whose IP addresses Device Security
knows but not their MAC addresses. In addition, their behaviors are not stable enough
for Device Security to confidently deduce that their addresses are statically
defined. Device Security displays the number of IP endpoints in a subnet. Click
the number to download a .zip file containing a report of IP endpoints in
comma-separated-value format.
DHCP and Gateway:
When Device Security integrates with switches using SNMP for network discovery
and learns the IP addresses of the DHCP server and gateway for a
subnet, it displays them in these columns. A BlueCat IPAM integration
also provides the gateway for subnets.
Prefix: The network portion of an IP address for a CIDR block or subnet.
If you click the entry in the Prefix column for a block, Device Security displays the
blocks, subnets and remainders within it.
If you click the entry for a subnet, Device Security opens the Subnet Detail panel over the
right side of the page. The panel includes various details about the subnet such as a
VLAN ID; DHCP server IP address; the number of devices in it per device type, category,
and profile; the name and details of the connected switch for the subnet; and firewall
security rule details (if there are rules for this subnet learned through Cortex XSOAR
integration with Panorama).

Not every Subnet Detail panel includes the Connected Switch and Firewall Security
Rules sections. For example, Device Security only learns about connected switches from
third-party integrations with Cisco Prime, DNA Center, or Meraki or from
integrations using SNMP for network discovery.
Devices: The number of devices that Device Security has discovered
in a subnet and learned about through a third-party integration.
Static: If a subnet is defined as having static IP addresses, Yes appears
in this column. Otherwise, a dash ( - ) appears
here, indicating that Device Security does not have enough data to
determine if a subnet has static IP addresses or not.
Firewall Security Rules:
(Requires a third-party integration through a
Cortex XSOAR server or cloud-hosted instance)
After you configure Device Security to communicate with Panorama through Cortex
XSOAR, it can fetch any firewall security rules that reference a subnet as the source or
destination. The number of rules applied to a subnet appear in the Firewall Security
Rules column. When you click the subnet entry in the Prefix column, you can see the
rules themselves in the Subnet Detail panel that appears.
When 0 appears in the Firewall Security Rules column, it means
that a previous rule referencing the subnet has been removed and now no other rules
apply to it.
Low-confidence Devices: This is the number
of devices whose identity Device Security cannot identify confidently. Click
the number for a subnet to open the Devices page with a filter applied
to show only the low-confidence devices in that subnet; that is, devices
with calculated confidence score of 0-69%.
A confidence score indicates the level of confidence Device Security has in its identification of a device. Device Security has three
confidence levels based on calculated confidence scores: high (90-100%),
medium (70-89%), and low (0-69%).
Site Mapping: Subnets and blocks that
are nested within other blocks inherit the site of the topmost block
of their set. For example, if there’s a 10.1.0.0/16 block at a site
named “NYC” and it contains a 10.1.1.0/24 subnet or block, then
this subnet or block inherits “NYC” as its site too. Yes or No indicates
whether a subnet or block inherited its site in this manner or not.
Site: The site to which a block or subnet
belongs can be defined manually (see Device-to-Site Mapping) or learned
through an integration with Infoblox IPAM.
Devices Discovered via Integration: The
number of devices learned through integration with a third-party system.
Removable: Indicates if you can remove
a subnet or block. Preconfigured blocks, like 10.0.0.0/8, and those currently
being used for site mapping cannot be removed.
Clicking the subnet entry in the Prefix column opens the Subnet Detail panel where you can
see more information about it.
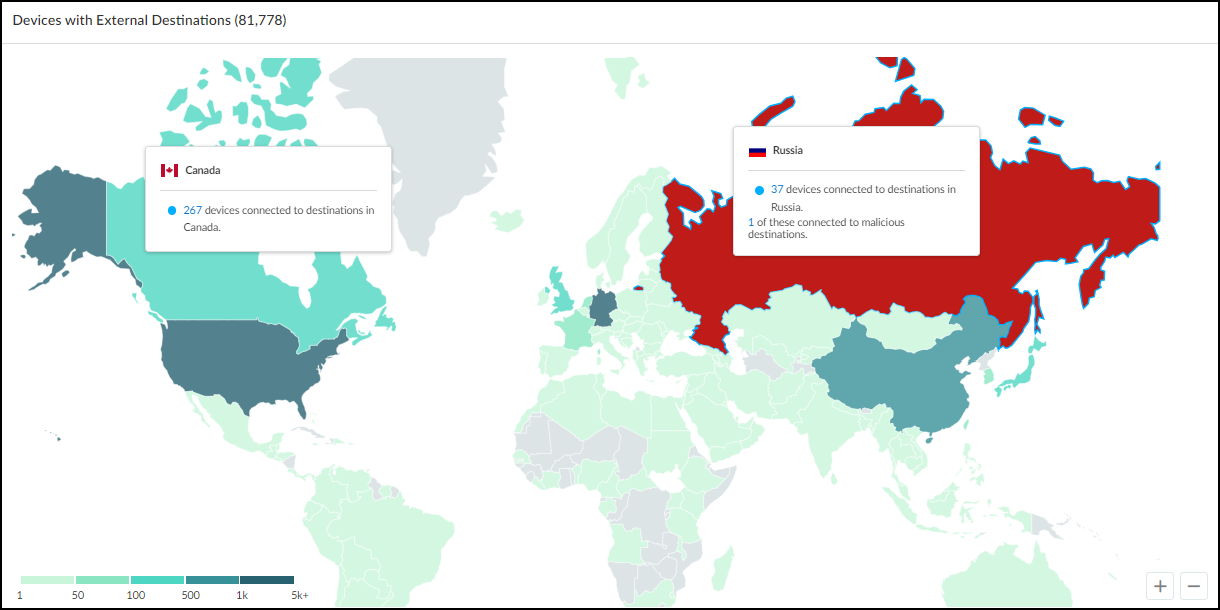
Below the Networks table is a map showing the number of devices that made connections to
external destinations; that is, to destinations outside the local network. The color of
the countries to which devices connected indicate how many devices made connections to
them and if any of the destinations were malicious.
- Gray indicates there were no devices with connections to a country.
- Green indicates devices connected to safe destinations to a country. The darker the green the more devices connected to destinations there. (See the legend for numbers.) Hover your cursor over a country to see an information pop-up with the number of devices that connected to destinations there during the time period filter at the top of the page. If you click a country, the information pop-up remains in view until you click the country again to close it. This allows you to click two or more countries and easily compare the number of connections to each one. Click the number in the pop-up to open the AssetsDevices page with a filter set to show devices that connected to this country.
- Red indicates at least one device connected to a malicious destination there.
![]()
Click-drag your cursor to move the map. Use the scroll wheel on your mouse or the
+/- tools in the lower right corner of
the map to zoom in and out.