Device Security
Use a Virtual Wire Interface for DHCP Visibility
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Use a Virtual Wire Interface for DHCP Visibility
Use a Virtual Wire interface to capture DHCP traffic to send to the data lake for
Device Security to access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
|
To gain complete visibility of DHCP traffic, deploy a Virtual Wire (vWire) in
front of the DHCP server. This
guide assumes familiarity with PAN-OS configuration, including Virtual
Wire configuration. For details on configuring Virtual Wire interfaces,
see the
PAN-OS Networking Administrator’s Guide.
Network Architecture
This solution is for networks where a DHCP server is on the same network segment
as the firewall interface, as shown in the figure below.

For full
visibility of all four DHCP messages, place the DHCP server behind
a Virtual Wire interface. Doing so enables the firewall to generate
Enhanced Application logs (EALs) for all packets in the exchange.
After proper configuration and physical network changes, the network
looks similar to the following illustration:

Configuration
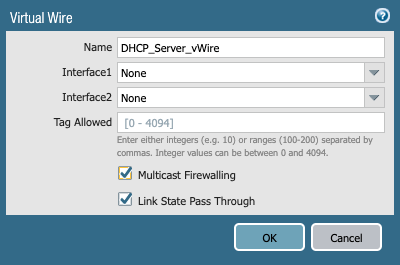
- Configure a Virtual Wire interface, complete with zones.The configuration of the Virtual Wire object must include multicast firewalling:
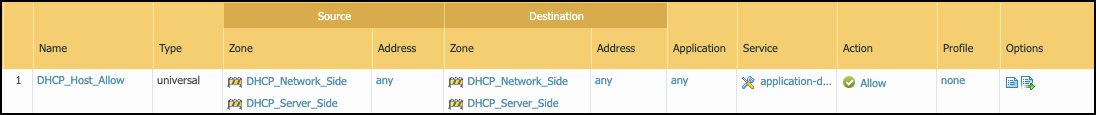
![]() Configure a policy rule to allow traffic between the two Virtual Wire interface zones.Configure this policy rule to allow all the existing traffic that the server currently sees use the same log forwarding object as the rest of the rule base. The Policy Optimization section below covers optimizing this policy rule set and preventing double logging.
Configure a policy rule to allow traffic between the two Virtual Wire interface zones.Configure this policy rule to allow all the existing traffic that the server currently sees use the same log forwarding object as the rest of the rule base. The Policy Optimization section below covers optimizing this policy rule set and preventing double logging.![]() Connect the external DHCP server to one side of the Virtual Wire and connect the network switch to the other side.Instead of connecting the DHCP server host directly to the firewall, you can use an isolated VLAN to minimize cabling in the switching infrastructure.Policy OptimizationThe goal of this solution is to gain visibility into DHCP payloads while minimizing performance impact on the firewall. To that end, configure the following policy rule set for the Virtual Wire zones:
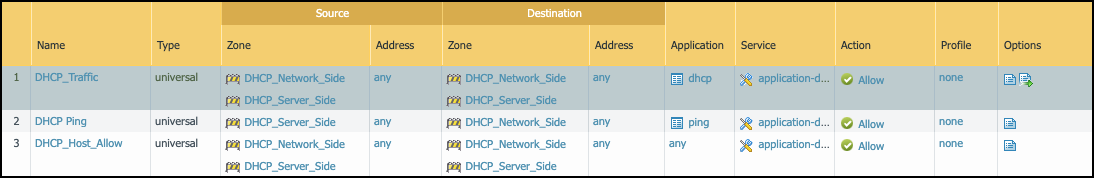
Connect the external DHCP server to one side of the Virtual Wire and connect the network switch to the other side.Instead of connecting the DHCP server host directly to the firewall, you can use an isolated VLAN to minimize cabling in the switching infrastructure.Policy OptimizationThe goal of this solution is to gain visibility into DHCP payloads while minimizing performance impact on the firewall. To that end, configure the following policy rule set for the Virtual Wire zones:![]()
- The “DHCP_Traffic” policy rule allows DHCP to and from the DHCP server. This rule uses the standard log forwarding profile with EALs enabled.
- The “DHCP Ping” policy rule allows pings from the DHCP server to the rest of the subnet. This enables DHCP servers to check if an IP address is active before assigning it as a lease to a new request. This rule does not forward logs.
- The “DHCP_Host_Allow” policy rule allows everything else to and from the DHCP server and does not forward logs for traffic matches.
To minimize the performance impact of the additional sessions that the firewall sees as a result of this Virtual Wire configuration, security profiles are not assigned to the above policy rules. If you want to microsegment the DHCP server, replace the “DHCP_Host_Allow” rule with a more granular policy rule set that allows applications in accordance with best practices. You can use security profiles in that policy rule set.