Cloud NGFW for Azure
Set Up Inbound Decryption on Cloud NGFW for Azure
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for Azure Docs
Set Up Inbound Decryption on Cloud NGFW for Azure
Learn how to set up inbound decryption on Cloud NGFW for Azure.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Cloud NGFW uses SSL Inbound Decryption to inspect and
decrypt inbound SSL/TLS traffic from a client to a targeted network server (any
server you have the certificate for and can import onto the firewall) and block
suspicious sessions. The firewall acts as a proxy between the external client and
the internal server and generates a new session key for each secure session. The
firewall creates a secure session between the client and the firewall and another
secure session between the firewall and the server to decrypt and inspect the
traffic. However, Cloud NGFW keeps your traffic packet headers and payload intact,
providing complete visibility of the source’s identity to your applications in your
VNets.
You must concatenate the web certificate and private key as a single
pem or pfx file and upload it to the Azure key vault to perform SSL Inbound
Inspection. The firewall validates that the certificate sent by the targeted server
during the SSL/TLS handshake matches a certificate in your decryption policy rule.
If there is a match, the firewall forwards the server's certificate to the client
requesting server access and establishes a secure connection.
Don’t upload the certificate and key separately to the Azure key vault.
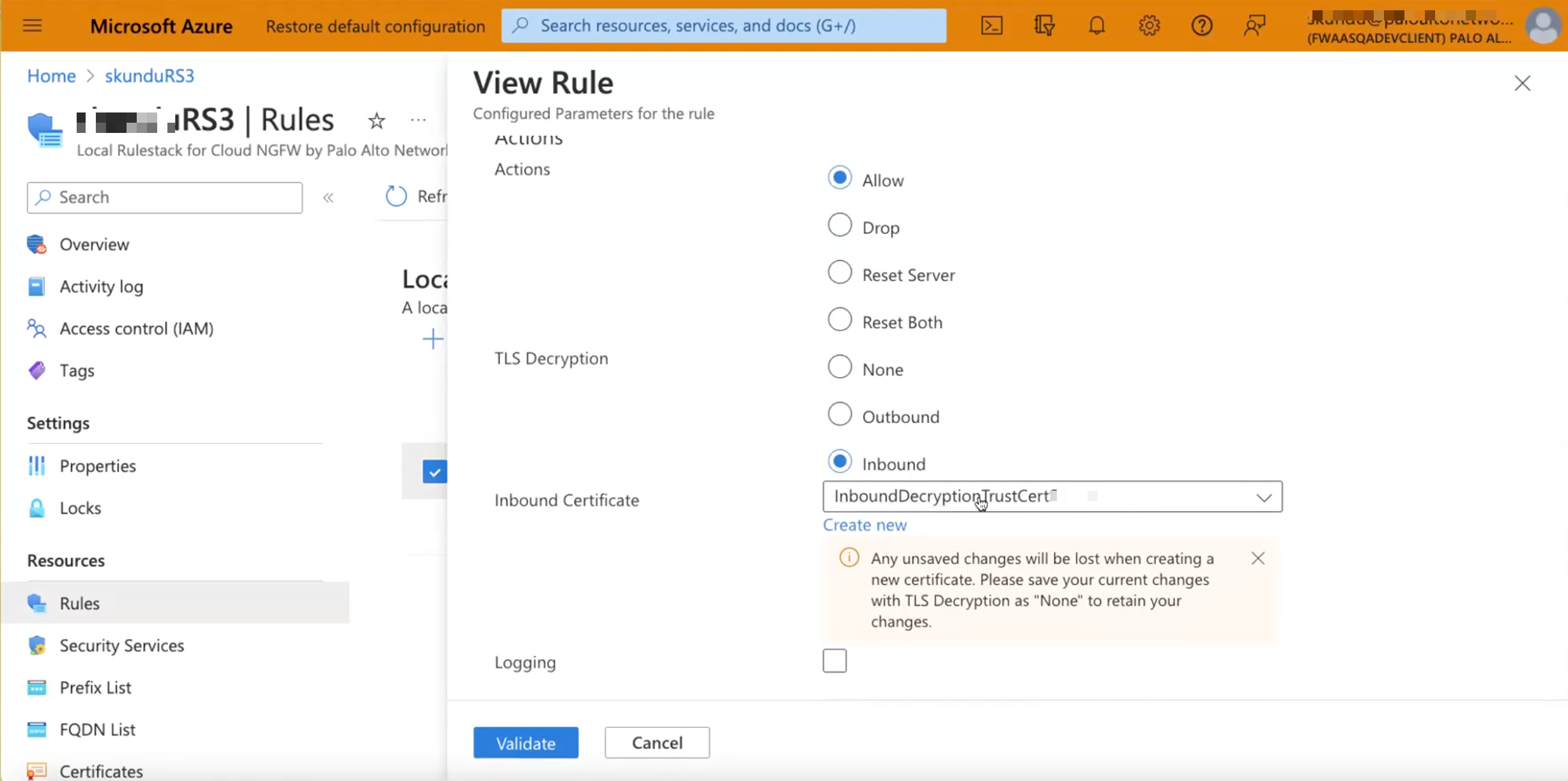
- Select Rulestacks and select a previously created rulestack that to apply the certificate.Select Rules, then Create a new Security Rule for decryption.Provide the following details under General.
- Name—Name of the rule.
- Description—A description for the rule.
- Priority—A unique priority for the rule.
- Enabled—Enable the field to associate the rulestack with the rule. This field is enabled by default.
Define matching criteria for the Source and Destination IP address fields.Configure Granular Controls.- Specify the Application Match Criteria you want the rule to allow
or block.You can create TLS decryption rules with Applications—Any or SSL—Match only.
- Specify a URL category as the match criteria for the rule.
- Specify the Protocol and Ports you want the rule to allow or block.
- Allow—Allow traffic.
- Drop—Block traffic and enforce the default drop action defined for the application being denied.
- Reset Server—Sends the TCP reset to the server-side device.
- Reset Both—Sends a TCP reset to both client and server-side devices.
Under TLS Decryption, select Inbound and select an Inbound Inspection Certificate.![]()
- Create a certificate if you have not done so already. The Azure Resource Name (ARN) of the secret is used in the certificate ARN when creating the certificate object.
- PKCS8 is the supported certificate format.
- Inbound decryption supports self-signed and root CA signed certificates and does not support chained certificates.
- The decryption profile for TLS decryption is set to best practice Security policy. See decrypt traffic for full visibility and threat inspection for more information.
Select Logging to enable logging.Click Validate.Click Config Actions>Deploy Configuration>Commit to save the rule to the running configuration of the firewall.