Cloud NGFW for Azure
Use XFF IP Address Values in Policy
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for Azure Docs
Use XFF IP Address Values in Policy
Learn how to use X-Forwarded-For header values in policy.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
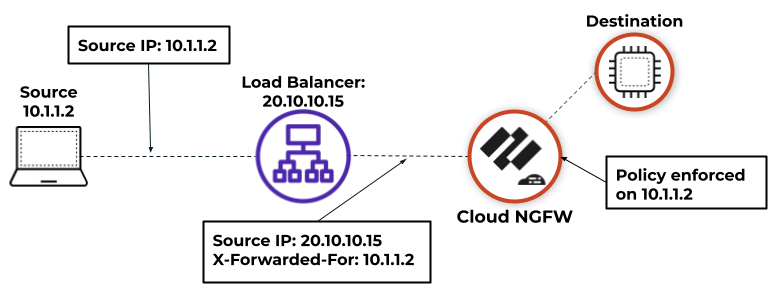
If you have an upstream device, such as a load balancer, deployed between the users
on your network and you Cloud NGFW instance, the Cloud NGFW might see the upstream
device IP address as the source IP address in HTTP/HTTPS traffic that the proxy
forwards rather than the IP address of the client that requested the content. In
many cases, the upstream device adds an X-Forwarded-For (XFF) header to HTTP
requests that include the actual IPv4 or IPv6 address of the client that requested
the content or from whom the request originated.
In Microsoft Azure, by default, an application gateway inserts the original source IP
address and port in the XFF header. To use XFF headers in policy on your firewall,
you must configure the application gateway to omit the port from the XFF header. See
Azure documentation to learn how to
configure your application gateway.
This feature is supported on Panorama-managed Cloud NGFW for
Azure only.
When configuring security policy rules on Panorama, you can enable Cloud NGFW to use
the source IP address in an XFF HTTP header field to enforce security policy. When a
packet passes through a single proxy server before reaching the firewall, the XFF
field contains the IP address of the originating endpoint. However, if the packet
passes through multiple upstream devices, the firewall uses the most recently added
IP address to enforce policy or use other features that rely on IP information.
- Log in to Panorama.Select your Cloud NGFW for Azure template.Select DeviceSetupContent IDX-Forwarded-For Headers.Click the edit icon.Select Enabled for Security Policy from the Use X-Forwarded-For Header drop-down.You cannot enable Use X-Forwarded-For Header for security policy and User-ID at the same time.
![]() Optional Select Strip X-Forwarded-For Header to remove the XFF field from outgoing HTTP requests.Selecting this option does not disable the use of XFF headers in policy. The Cloud NGFW for Azure strips the XFF field from client requests after using it to enforce policy.Click OK.Commit your changes.
Optional Select Strip X-Forwarded-For Header to remove the XFF field from outgoing HTTP requests.Selecting this option does not disable the use of XFF headers in policy. The Cloud NGFW for Azure strips the XFF field from client requests after using it to enforce policy.Click OK.Commit your changes.