Advanced WildFire Powered by Precision AI™
Advanced WildFire Example
Table of Contents
Advanced WildFire Example
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The following example scenario summarizes the
full Advanced WildFire™ lifecycle. In this example, a sales representative
from Palo Alto Networks downloads a new software sales tool that
a sales partner uploaded to Dropbox. The sales partner unknowingly
uploaded an infected version of the sales tool install file and
the sales rep then downloads the infected file.
This example
will demonstrate how a Palo Alto Networks firewall in conjunction
with Advanced WildFire can discover zero-day malware downloaded
by an end user, even if the traffic is SSL encrypted. After Advanced
WildFire identifies the malware a log is sent to the firewall and
the firewall alerts the administrator who then contacts the user
to eradicate the malware. Advanced WildFire then generates a new
signature for the malware, after which firewalls automatically download
the signature to protect against future exposure. Although some
file sharing web sites have an antivirus feature that checks files
as they are uploaded, they can only protect against known malware.
This
example uses a web site that uses SSL encryption. In this case,
the firewall has decryption enabled, including the
option to forward decrypted content for analysis.
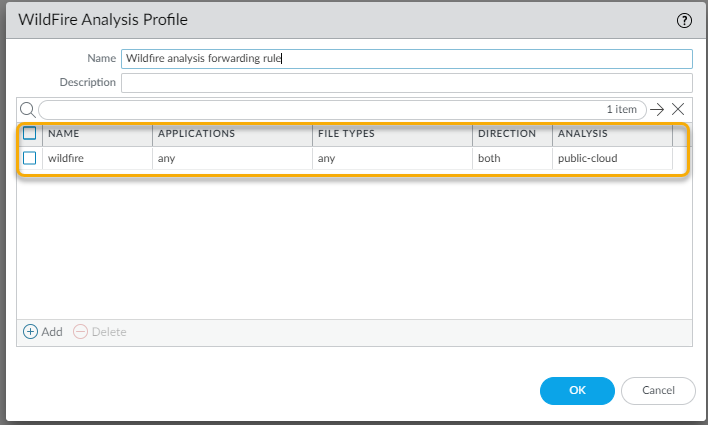
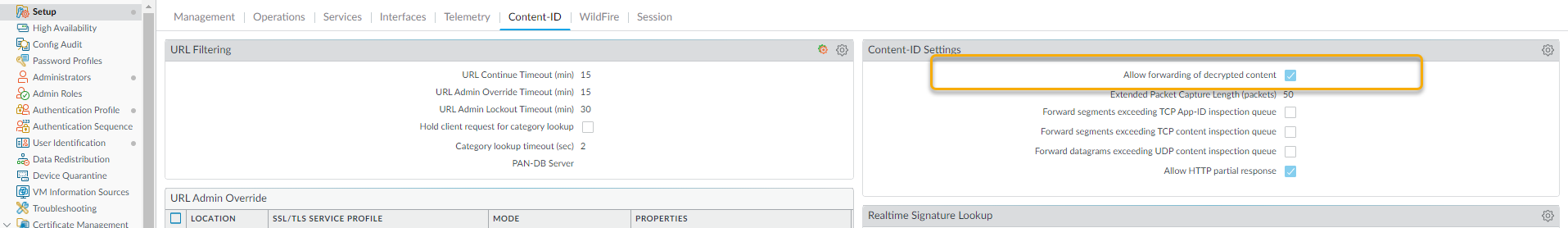
- The sales person from the partner company uploads a sales tool file named sales-tool.exe to his Dropbox account and then sends an email to the Palo Alto Networks sales person with a link to the file.The Palo Alto sales person receives the email from the sales partner and clicks the download link, which takes her to the Dropbox site. She then clicks Download to save the file to her desktop.The firewall that is protecting the Palo Alto sales rep has a WildFire Analysis profile rule attached to a security policy rule that will look for files in any application that is used to download or upload any of the supported file types. The firewall can also be configured to forward the email-link file type, which enables the firewall to extract HTTP/HTTPS links contained in SMTP and POP3 email messages. As soon as the sales rep clicks download, the firewall forwards the sales-toole.exe file to Advanced WildFire, where the file is analyzed for zero-day malware. Even though the sales rep is using Dropbox, which is SSL encrypted, the firewall is configured to decrypt traffic, so all traffic can be inspected. The following screen shots show the WildFire Analysis profile rule, the security policy rule configured with the WildFire analysis profile rule attached, and the option to allow forwarding of decrypted content enabled.
![]()
![]()
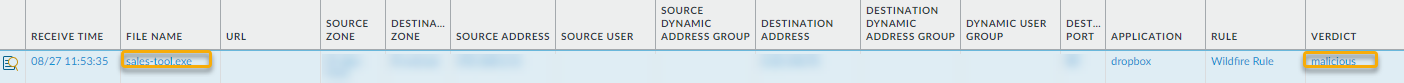
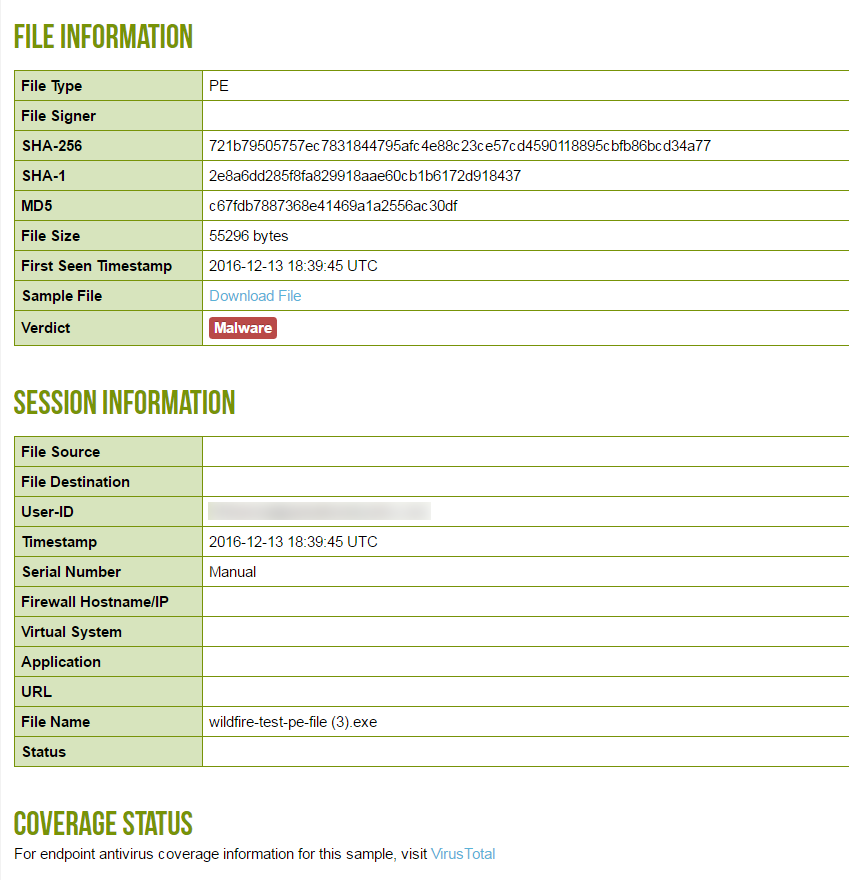
![]() At this point, Advanced WildFire has received the file and is analyzing it for more than 200 different malicious behaviors.After Advanced WildFire has completed the file analysis, it sends an Advanced WildFire log back to the firewall with the analysis results. In this example, the log shows that the file is malicious.
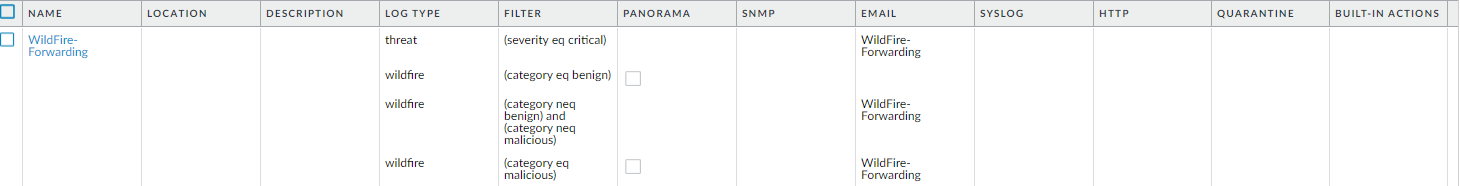
At this point, Advanced WildFire has received the file and is analyzing it for more than 200 different malicious behaviors.After Advanced WildFire has completed the file analysis, it sends an Advanced WildFire log back to the firewall with the analysis results. In this example, the log shows that the file is malicious.![]() The firewall is configured with a log forwarding profile that will send alerts to the security administrator when malware is discovered.
The firewall is configured with a log forwarding profile that will send alerts to the security administrator when malware is discovered.![]() The security administrator identifies the user by name (if User-ID is configured), or by IP address if User-ID is not enabled. At this point, the administrator can shut down the network or VPN connection that the sales representative is using and will then contact the desktop support group to work with the user to check and clean the system.By using the Advanced WildFire detailed analysis report, the desktop support person can determine if the user system is infected with malware by looking at the files, processes, and registry information detailed in the Advanced WildFire analysis report. If the user runs the malware, the support person can attempt to clean the system manually or re-image it.
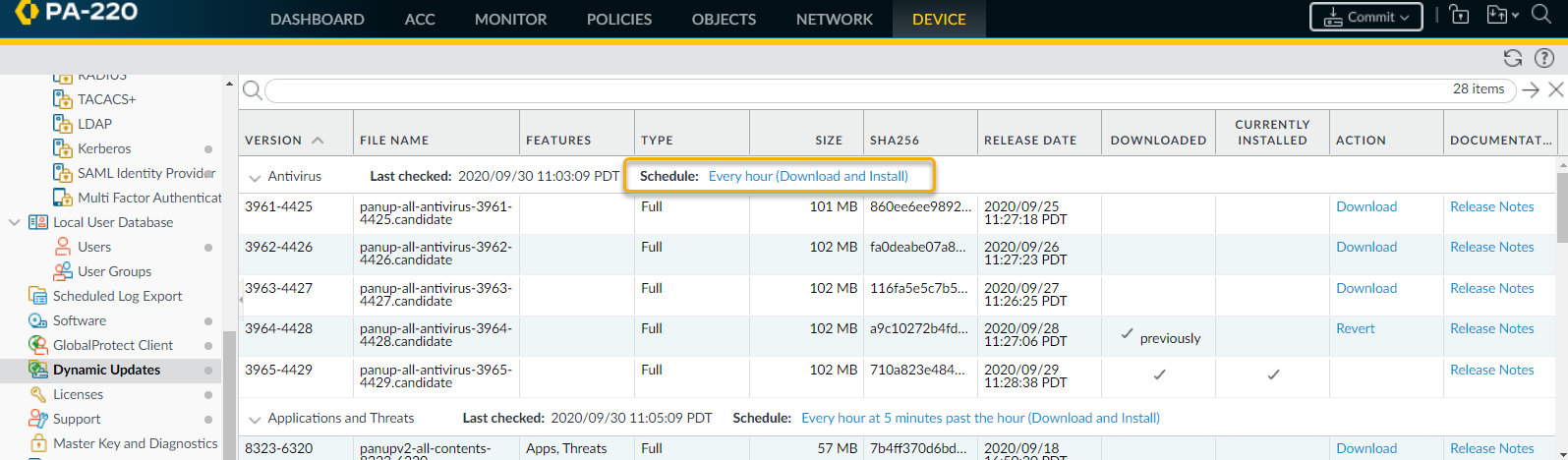
The security administrator identifies the user by name (if User-ID is configured), or by IP address if User-ID is not enabled. At this point, the administrator can shut down the network or VPN connection that the sales representative is using and will then contact the desktop support group to work with the user to check and clean the system.By using the Advanced WildFire detailed analysis report, the desktop support person can determine if the user system is infected with malware by looking at the files, processes, and registry information detailed in the Advanced WildFire analysis report. If the user runs the malware, the support person can attempt to clean the system manually or re-image it.![]() Now that the administrator has identified the malware and the user system is being checked, how do you protect from future exposure? Answer: In this example, the administrator set a schedule on the firewall to download and install Advanced WildFire signatures every 15 minutes and to download and install Antivirus updates once per day. In less than an hour and a half after the sales rep downloaded the infected file, Advanced WildFire identified the zero-day malware, generated a signature, added it to the Advanced WildFire update signature database provided by Palo Alto Networks, and the firewall downloaded and installed the new signature. This firewall and any other Palo Alto Networks firewall configured to download Advanced WildFire and antivirus signatures is now protected against this newly discovered malware. The following screenshot shows the Advanced WildFire update schedule:
Now that the administrator has identified the malware and the user system is being checked, how do you protect from future exposure? Answer: In this example, the administrator set a schedule on the firewall to download and install Advanced WildFire signatures every 15 minutes and to download and install Antivirus updates once per day. In less than an hour and a half after the sales rep downloaded the infected file, Advanced WildFire identified the zero-day malware, generated a signature, added it to the Advanced WildFire update signature database provided by Palo Alto Networks, and the firewall downloaded and installed the new signature. This firewall and any other Palo Alto Networks firewall configured to download Advanced WildFire and antivirus signatures is now protected against this newly discovered malware. The following screenshot shows the Advanced WildFire update schedule:![]() All of this occurs well before most antivirus vendors are even aware of the zero-day malware. In this example, within a very short period of time, the malware is no longer considered zero-day because Palo Alto Networks has already discovered it and has provided protection to customers to prevent future exposure.
All of this occurs well before most antivirus vendors are even aware of the zero-day malware. In this example, within a very short period of time, the malware is no longer considered zero-day because Palo Alto Networks has already discovered it and has provided protection to customers to prevent future exposure.