Strata Cloud Manager
New Features in September 2024
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
New Features in September 2024
Here are the new features available in Strata Cloud Manager in September
2024.
Here are the latest new features introduced on Strata Cloud Manager. Features listed
here include some feature highlights for the products supported with .
For the full list of new features supported for a product you're using with Strata Cloud Manager, see the release notes for that product.
Prisma Access: Remote Browser Isolation in China
|
September 30, 2024
Supported for:
|
Remote Browser Isolation (RBI) is available in China to protect your users' managed
devices from malware and potential zero-day attacks that result from standard web
browsing activity. RBI in China works with Prisma® Access in
China to isolate and transfer all browsing activity to the cloud-delivered platform.
This ensures that potentially malicious code and content are secured and isolated
away from your users' managed devices and the corporate network. This approach
dramatically strengthens your security posture against highly evasive threats,
especially those originating from risky websites.
Furthermore, the core capabilities available in RBI in China are the same as the RBI
capabilities for the rest of the world, ensuring a consistent user experience
globally, and the procedures for configuring RBI in China are identical to existing
RBI configurations.
Panorama CloudConnector Plugin 2.1.0
|
September 25, 2024
Supported for:
|
When managing Panorama, administrators require consistent security
controls, including centralized proxy configuration, for all outgoing
communications. Historically, the Panorama CloudConnector Plugin did not
automatically inherit these settings, creating a security gap where essential
interactions with cloud services bypassed the defined proxy policies. This lack of
integration increased administrative overhead and compromised the overall
consistency of the security posture.
The Panorama CloudConnector plugin 2.1.0 now
addresses this critical challenge by fully integrating with Panorama’s centralized
proxy configuration settings. This enhancement ensures that the plugin automatically
uses proxy configuration defined in Panorama for all future interactions with the
cloud. This integration simplifies administrative workflows, eliminates the risk of
misconfiguration, and ensures unified security enforcement for connectivity to cloud
platforms. See Panorama CloudConnector Plugin Release
Notes.
Prisma Access: Agent Proxy Support for Private IP from Branches
|
September 20, 2024
Supported for:
|
Visibility and enforcement based on an endpoint's private IP address was previously
unavailable for users connecting via
GlobalProtect® agent to the Explicit Proxy. This new feature
solves that challenge by allowing you to now leverage the private IP addresses of
endpoints for logging and to apply IP address-based enforcement. This enhancement
ensures consistent policy application and granular monitoring for users who connect
to Prisma® Access Explicit Proxy through the GlobalProtect agent from the branches.
Prisma Access: Explicit Proxy China Support
|
September 20, 2024
Supported for:
|
Multinational organizations operating in China face unique challenges in securing
internet access for users and headless devices where VPN agents cannot be installed
due to compliance reasons or network restrictions. Prisma
® Access
explicit proxy support in China addresses
this critical need by providing a secure internet gateway that works without
requiring default route changes to the infrastructure, while coexisting with VPN
agents.
This solution also acts as a reliable proxy solution that complies with local
regulations while effectively managing internet access and safeguarding sensitive
information across endpoints. The explicit proxy support in China leverages AWS
infrastructure with a 1:1 architecture where each Envoy proxy is paired with a proxy
firewall virtual machine (VM). This architecture enables secure traffic handling
while accommodating the unique networking constraints.
When you implement this solution, users connecting from branch locations can
access the internet securely through the explicit proxy without having GlobalProtect
® clients installed. Additionally, headless devices such as IoT systems
or servers can route traffic through the proxy for security inspection. The
service integrates with your existing authentication methods, including SAML and
Kerberos, and supports the same Security policy rules you configure for your global
deployment. Palo Alto Networks NGFW capabilities securely inspect traffic,
with logs and telemetry available through the same management interface you use for
your global deployment. The architecture also supports routing specific domains to
Service Connection when needed, providing flexibility for accessing both internet
and private resources.
Prisma Access: Static IP Enhancements for Mobile Users
|
September 20, 2024
Supported for:
|
Managing mobile user access on networks that rely on IP address-based
authorization is challenging because dynamic IP assignment from Prisma® Access can
break access policies. The Static IP Allocation feature allows you to assign a fixed IP address to Prisma Access mobile
users to address this challenge. This feature is useful if your network deployments
restrict user access to resources using IP addresses as part of their network and
application design. This functionality simplifies deployment and provides critical
benefits:
You can assign static IP addresses for mobile
users based on the Prisma Access theater or User-ID™
You can now use location groups and user groups to improve your IP address assignment
for mobile users, in addition to theater and User-ID.
The supported number of IP address pool profiles is significantly increased,
simplifying the management and scaling of large mobile user deployments.
Prisma Access: View Prisma Access, Dataplane, and Application and Threats Content Releases in Strata Cloud Manager and Panorama
|
September 20, 2024
Supported for:
|
Managing component versions and tracking End-of-Support (EoS) dates across Prisma®
Access, Dataplane, and content releases typically requires checking multiple
locations. Prisma Access now lets you view the status of these components in a
single page for Prisma Access deployments managed by Strata Cloud
Manager and Panorama® and includes notifications that show you when your
current running Panorama version and plugin versions will be EoS.
Prisma® Access consists of components you manage such as Panorama and
the Cloud Services plugin, components that Prisma Access manages such as the
dataplane version, and components that Prisma Access manages but whose version you
can control (such as the GlobalProtect® version hosted on the Prisma Access portal).
Prisma Access lets you view the status of these components in a single page and
provides you with this information:
- Prisma Access version
- PAN-OS dataplane version
- Release Type (Preferred or Innovation)
- Applications and Threats content version


Prisma Access: New Prisma Access Cloud Management Location
|
September 20, 2024
Supported on Strata Cloud Manager for:
|
Prisma Access Cloud Management can now be deployed in the Qatar region.
Prisma Browser Visibility
|
September 6, 2024
Supported for:
|
Depending on your license for Prisma Access Browser Standalone or Prisma Access Browser with Prisma Access
Enterprise Bundle, the following new items are available in Strata Cloud
Manager for visibility:
- MonitorSubscription UsageNow shows Prisma Access Browser, either fully activated or number allocated vs. available (if it’s a partial allocation).
![]()
- Activity InsightsUsersNew Connect Method = PA Browser
![]() To see user and device details
To see user and device details![]()
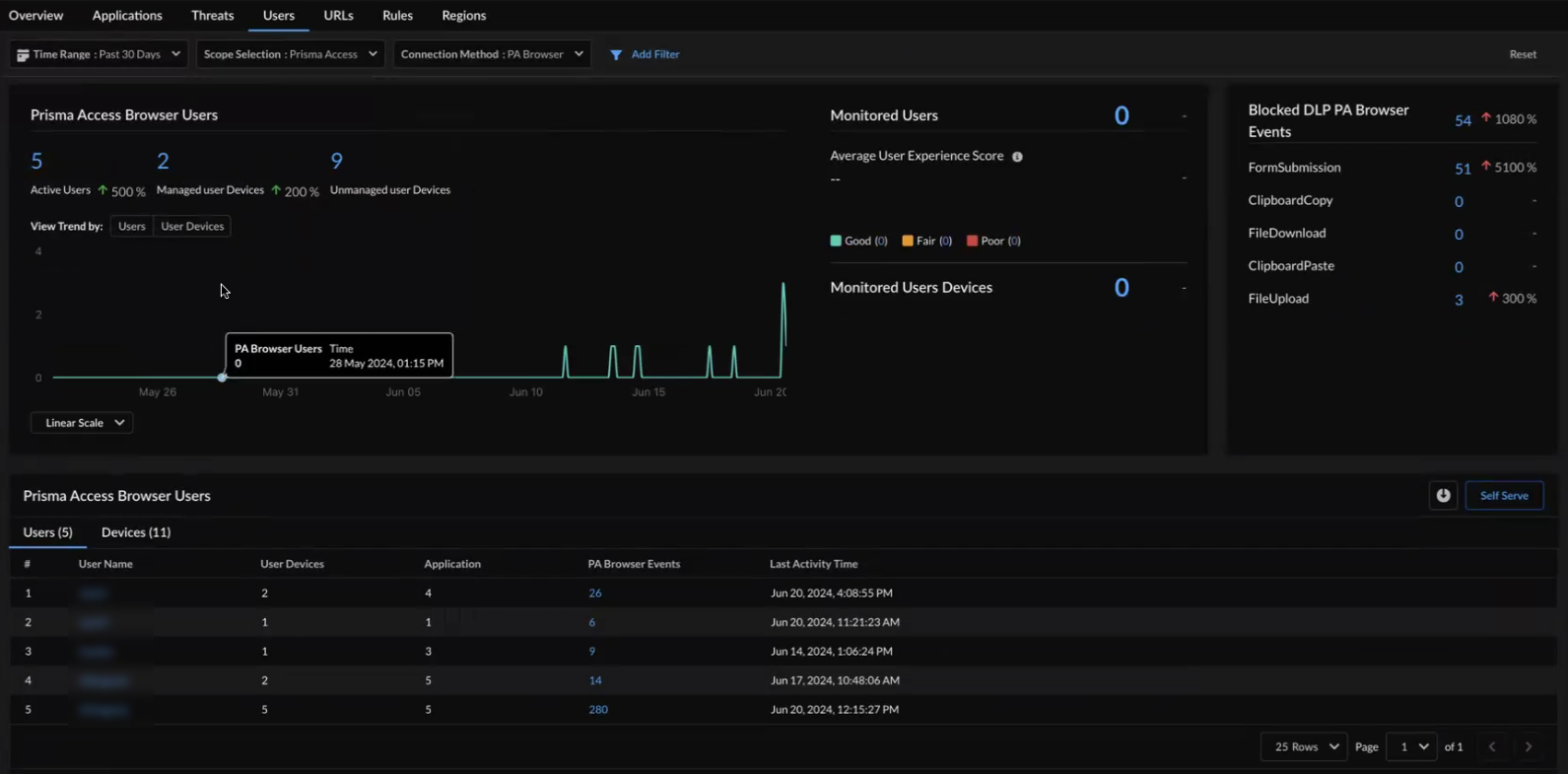
- Activity InsightsUsersdetailsSelect a user to drill down into details to see the new widgets such as the Prisma Access Browser Event Summary.
![]()
- Activity InsightsApplicationsNew column for count of PA Browser Events.
![]() Select the number of events and it will redirect you to the Prisma Access Browser management pages.
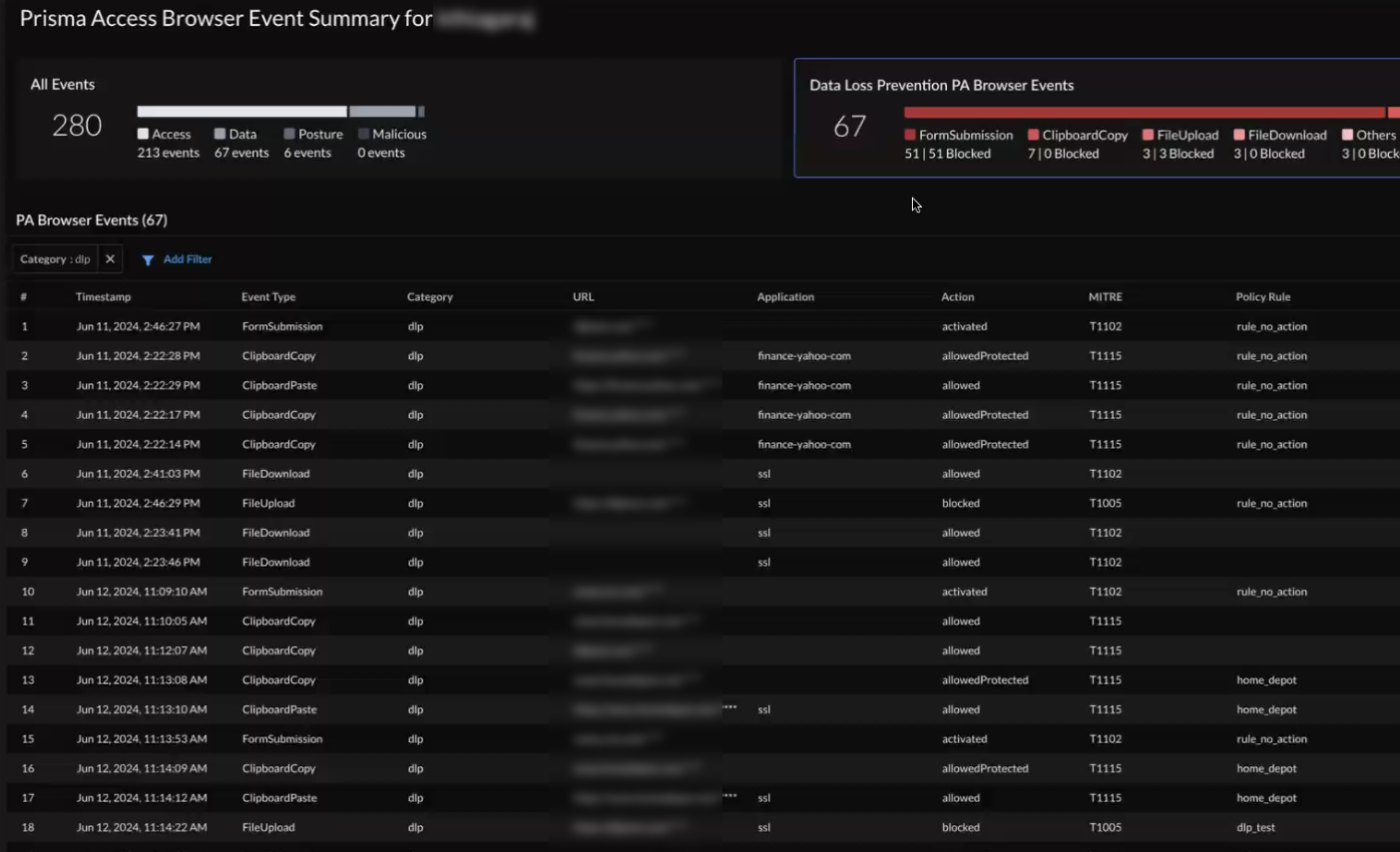
Select the number of events and it will redirect you to the Prisma Access Browser management pages. - Activity InsightsApplicationsdetailsSelect an application to drill down into details to see the new widgets for PA Browser Access Events (the web apps or websites that users accessed) and PA Browser Data Events (the data control events that are performed) in the aggregate view or the breakdown view for allowed and blocked events.
Strata Cloud Manager: Enhanced Auto VPN Configuration for Large Enterprises
|
September 20, 2024
Supported for:
|
It is a complex and often difficult process
to add new sites and secure connectivity across all sites in distributed enterprises
that have firewalls at the edge of their network. Additionally, securing these
networks requires manual configuration that is time-consuming and prone to
misconfiguration.
With these Auto VPN configuration enhancements, you can
configure a link bundle that enables you to combine multiple physical links into one
virtual SD-WAN interface. These bundles provide multiple and more robust options for
path selection and failover protection that you can specify when you onboard a
next-generation firewall (NGFW) as a branch device in the VPN cluster using Prisma® Access as a hub.
With bundles that include more than one physical link, you maximize application quality
when a physical link deteriorates. Create a link bundle by assigning the same link
tag (using an SD-WAN Interface profile) to multiple links that have similar access
and SD-WAN policy rules. For example, you can create a link tag named Low Cost
Broadband and then use it to tag your cable modem and fiber optic broadband
services.
In addition to improving the Auto VPN configuration settings, we
extended Auto VPN connectivity to 500 sites per tenant.
Strata Cloud Manager: Advanced DNS Security
|
September 20, 2024
Supported for:
|
The Advanced DNS Security service is a new
subscription offering by Palo Alto Networks that operates new domain detectors in
the Advanced DNS Security cloud that inspect changes in DNS responses to detect
various types of DNS hijacking in real-time. With access to Advanced DNS Security,
you can detect and block DNS responses from hijacked domains and misconfigured
domains. Hijacked and misconfigured domains can be introduced into your network by
either directly manipulating DNS responses or by exploiting the DNS infrastructure
configuration settings in order to redirect users to a malicious domain from which
they initiate additional attacks. The primary difference between these two
techniques is where the exploit occurs. In the case of DNS hijacking, the attackers
gain the ability to resolve DNS queries to attacker-operated domains by compromising
some aspect of an organization's DNS infrastructure, be it through unauthorized
administrative access to a DNS provider or the DNS server itself, or an MiTM attack
during the DNS resolution process. Misconfigured domains present a similar problem -
the attacker seeks to incorporate their own malicious domain into an organization’s
DNS by taking advantage of domain configuration issues, such as outdated DNS
records, which can enable attackers to take ownership of the customer’s subdomain.
Advanced DNS Security can detect and categorize hijacked and misconfigured domains in
real-time by operating cloud based detection engines, which provide DNS health
support by analyzing DNS responses using ML-based analytics to detect malicious
activity. Because these detectors are located in the cloud, you can access a wide
array of detection mechanisms that are updated and deployed automatically without
requiring the user to download update packages when changes to detectors are made.
Upon initial release, Advanced DNS Security supports two analysis engines: DNS
Misconfiguration Domains and Hijacking Domains. Additionally, DNS responses for all
DNS queries are sent to the Advanced DNS Security cloud for enhanced response
analysis to more accurately categorize and return a result in a real-time exchange.
Analysis models are delivered through content updates, however, enhancements to
existing models are performed as a cloud-side update, requiring no updates by the
user. Advanced DNS Security is enabled and
configured through the Anti-Spyware (or DNS Security) profile and require
active Advanced DNS Security and Advanced Threat Prevention (or Threat Prevention)
licenses.
Strata Cloud Manager: Local Deep Learning for Advanced Threat Prevention
|
September 20, 2024
Supported on Strata Cloud Manager for:
Prisma Access (Managed by Strata Cloud Manager)
|
When handling high volumes of evasive threats or operating under challenging network
conditions, relying solely on cloud-based threat analysis can introduce unwanted
latency. Local Deep Learning for Advanced Threat
Prevention solves this challenge by providing fast, local deep
learning-based analysis for zero-day threats, complementing the cloud-based Inline Cloud Analysis
component of Advanced Threat Prevention.
With an active Advanced Threat Prevention license, the system quickly analyzes known
malicious traffic matching published signatures and applies the configured action,
such as dropping the session. For suspicious content, the Deep Learning Analysis
detection module reroutes the traffic locally for immediate analysis. Because this
module is based on the proven detection engines operating in the Advanced Threat
Prevention cloud, you gain the same zero-day and advanced threat detection
capabilities, but with the added benefit of processing a much higher traffic volume
locally. This allows you to inspect more traffic and receive rapid verdicts without
the lag associated with cloud queries. Content updates deliver the latest Local Deep
Learning models, ensuring your detection remains current.
Strata Cloud Manager: New Check Box for Overriding Security Checks
|
September 20, 2024
Supported for:
|
In security environments, strict validation checks are critical for maintaining a
robust security posture, but this rigidity can sometimes be an obstacle. When
pushing a configuration, a failed security check with a "block" action can halt the
entire deployment process. This creates unnecessary friction in time-sensitive
situations, forcing you to delay or manually reconfigure to bypass the strict
rule.
Strata Cloud Manager now addresses this pain point by introducing a feature in the
Push Config that allows you to override specific security check failures that
would normally block a push operation. This enhancement gives you the power and
flexibility to continue the deployment when you have a valid reason to proceed,
ensuring you are not stalled by strict checks. This capability allows you to balance
security enforcement with operational efficiency while still ensuring that all
validation errors are visible for your review and necessary investigation.
GlobalProtect: Support for PAN-OS-11.2-DHCP-Based IP Address Assignments
|
September 20, 2024
Supported on NGFW:
|
Starting from PAN-OS 11.2.1, the DHCP Based IP Address Assignment
feature is supported for both VM-Series virtual firewall and hardware
next-generation firewall platforms.
DHCP Based IP Address Assignment feature in PAN OS 11.2.0 release is
supported for VM-Series Virtual Firewalls only. The feature is not supported
for hardware next-generation firewall platforms.
You can now configure a DHCP server profile on the
GlobalProtect gateway to use DHCP server for managing and assigning IP addresses
for the endpoints connected remotely through the GlobalProtect app.
Users who are using enterprise DHCP servers can enable this feature for centralized
IP management and IP address assignments. When you configure a DHCP server profile
on the GlobalProtect gateway and upon successful communication between the gateway
and the DHCP server, the gateway obtains DHCP IP addresses from a DHCP member
server. The GlobalProtect gateway then assigns the IP addresses as the tunnel IP for
the endpoints that are remotely connected through the GlobalProtect app. If the DHCP
server fails to respond to the gateway within the set communication timeout and
retry times period, the gateway falls back to the private Static IP pool for the
allocation of IP addresses for the endpoints.
When the GlobalProtect gateway assigns the DHCP IP addresses to the
endpoints, you can configure their DHCP server to create Dynamic DNS ( Address and
Pointer Record) records for the GlobalProtect connected users. DDNS are useful for
endpoint admins to do troubleshooting on the GlobalProtect connected remote user
endpoints. The IP addresses get registered to the DDNS server only when you
configure IP Address Management (IPAM) on Windows server, DDNS server, or on the
Infoblox server.
GlobalProtect: Use Default Browser for SAML/CAS Authentication
|
September 20, 2024
Supported on NGFW
|
This feature enables you to configure the GlobalProtect app to use the default browser to authenticate to
the GlobalProtect portal through the Client Authentication
setting of the portal configuration. You can now select the Use Default
Browser option on the Client Authentication
screen for the app to use the default browser for SAML/CAS authentication to
authenticate to the portal for the first time. The Use Default
Browser option is displayed on the Client
Authentication screen only when you choose SAML/CAS as the
authentication profile.
Starting from PAN-OS 11.1, you do not need to set the pre-deployment keys/plist
entries to configure the app to choose whether the app should use the default
browser or embedded browser instead you can configure it through the Client
Authentication setting of the portal configuration.
End users can benefit from using the default system browser for SAML
authentication because they can leverage the same login for GlobalProtect
with their saved user credentials on the default system browser such as Chrome,
Firefox, or Safari.
This feature is available starting from the PAN-OS 11.1
version. For the earlier PAN-OS versions, you must use the predeployment registry
key/plist setting.
Advanced URL Filtering: URL Categorization Check
|
September 20, 2024
Supported for:
|
To configure URL Access Management profiles (also known as URL Filtering profiles)
and Security policy rules that block and allow the intended web traffic, you need to
know the current URL categorization of a website. You also use this information to
create a custom URL category or
troubleshoot why a website isn't blocked or allowed as expected. While you can look
up any URL on Palo Alto Networks Test A Site website, doing so requires navigating away from the
management interface.
To make URL lookups more convenient and efficient, PAN-OS® 11.1 adds a URL category checker where you configure
URL Access Management profiles. The category checker provides in-product access to
Test A Site, which queries PAN-DB, Palo Alto Networks cloud-based URL database.
Enter a domain or URL, and the results panel shows two distinct sections: one for
the primary URL category and one for the risk category. Each section includes a
description of the category and corresponding example sites. If you disagree with
the primary URL category, you can initiate a change request from the results
panel. This action redirects you to a prepopulated form on the external Test A Site
website.
Enhanced Report Management
|
September 27, 2024
Supported for:
|
Managing network visibility often requires switching across multiple
dashboards to analyze data. Centralized Report Management in Strata Cloud Manager eliminates this need by offering a unified system to enhance
visibility of network activity within your organization and help analyze historical
and track real-time data based on your needs. You can download reports using data
from the dashboards and Activity Insights Summary for Prisma® Access and your Palo
Alto Networks Next-Generation Firewalls (NGFWs). Strata Cloud Manager enables you
to share and schedule reports at your preferred intervals.
Strata Cloud Manager generates reports using either the last 24 hours of
data or the data from the past 30 days depending on the default time period settings
on the dashboard. However, you can customize the time period for gathering data in a
report when you schedule it. You can also manage scheduled and downloaded reports
from the past 30 days to help you monitor and troubleshoot network activity
effectively when needed.