Next-Generation Firewall
Create a GRE Tunnel
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Create a GRE Tunnel
Create a Generic Routing Encapsulation (GRE) tunnel to connect two endpoints in a
point-to-point, logical link.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Create a Generic Routing Encapsulation (GRE) tunnel to connect two endpoints in a
point-to-point, logical link.
As an alternative, you can
Create a GRE Tunnel over a Cellular Interface.
- Create a tunnel interface.
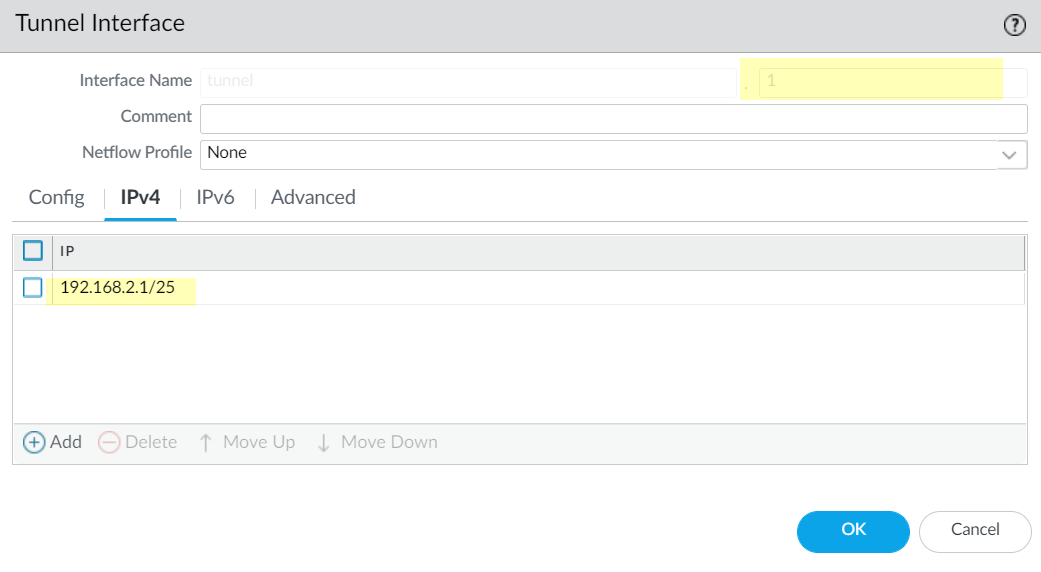
- Select NetworkInterfacesTunnel.Add a tunnel and enter the tunnel Interface Name followed by a period and a number (range is 1 to 9,999). For example, tunnel.1.On the Config tab, assign the tunnel interface to a Virtual Router.Assign the tunnel interface to a Virtual System if the firewall supports multiple virtual systems.Assign the tunnel interface to a Security Zone.
![]() Assign an IP address to the tunnel interface. (You must assign an IP address if you want to route to this tunnel or monitor the tunnel endpoint.) Select IPv4 or IPv6 or configure both.This address and the corresponding address of the tunnel interface of the peer should be on the same subnet because it is a point-to-point, logical link.
Assign an IP address to the tunnel interface. (You must assign an IP address if you want to route to this tunnel or monitor the tunnel endpoint.) Select IPv4 or IPv6 or configure both.This address and the corresponding address of the tunnel interface of the peer should be on the same subnet because it is a point-to-point, logical link.- (IPv4 only) On the IPv4 tab, Add an IPv4 address, select an address object, or click New Address and specify the Type of address and enter it. For example, enter 192.168.2.1.
- (IPv6 only) On the IPv6 tab,
Enable IPv6 on the interface.
- For Interface ID, select EUI-64 (default 64-bit Extended Unique Identifier).
- Add a new Address, select an IPv6 address object, or click New Address and specify an address Name. Enable address on interface and click OK.
- Select Type of address and enter the IPv6 address or FQDN and click OK to save the new address.
- Select Enable address on interface and click OK.
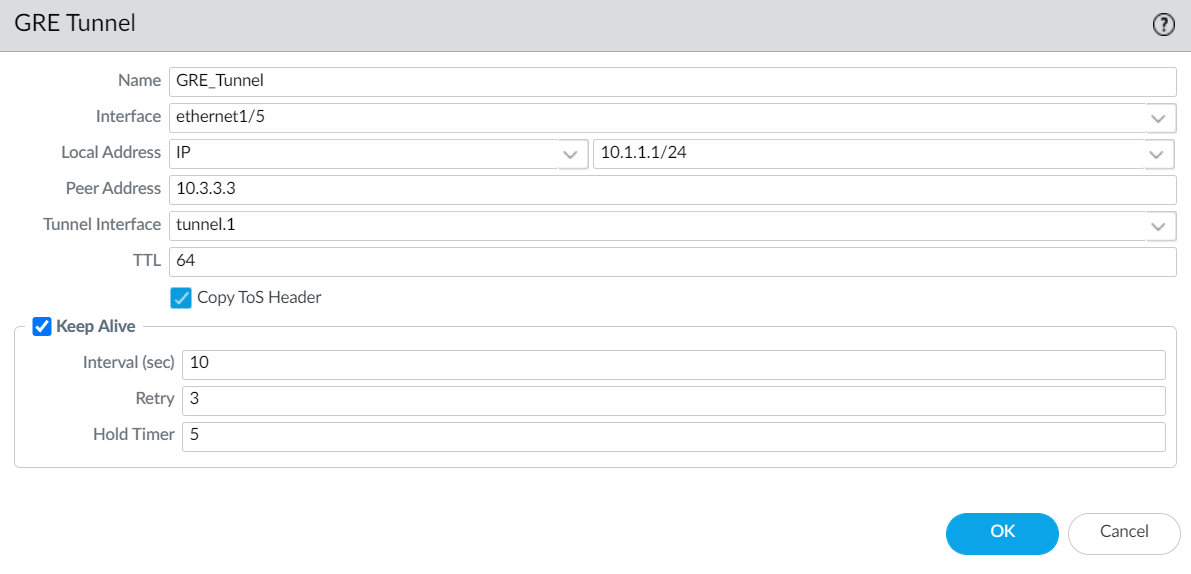
Click OK.Create a GRE tunnel to force packets to traverse a specific point-to-point path.- Select NetworkGRE Tunnels and Add a tunnel by Name.Select the Interface to use as the local GRE tunnel endpoint (source interface), which is an Ethernet interface or subinterface, an Aggregate Ethernet (AE) interface, a loopback interface, or a VLAN interface.Select the Local Address to be IP and select the IP address of the interface you just selected.Enter the Peer Address, which is the IP address of the opposite endpoint of the GRE tunnel.Select the Tunnel Interface that you created in Step 1. (This identifies the tunnel when it is the egress Interface for routing.)Enter the TTL for the IP packet encapsulated in the GRE packet (range is 1 to 255; default is 64).Select Copy ToS Header to copy the Type of Service (ToS) field from the inner IP header to the outer IP header of the encapsulated packets to preserve the original ToS information. Select this option if your network uses QoS and depends on the ToS bits for enforcing QoS policies.
![]() (Best Practice) Enable the Keep Alive function for the GRE tunnel.If Keep Alive is enabled, by default it takes three unreturned keepalive packets (Retries) at 10-second intervals for the GRE tunnel to go down and it takes five Hold Timer intervals at 10-second intervals for the GRE tunnel to come back up.
(Best Practice) Enable the Keep Alive function for the GRE tunnel.If Keep Alive is enabled, by default it takes three unreturned keepalive packets (Retries) at 10-second intervals for the GRE tunnel to go down and it takes five Hold Timer intervals at 10-second intervals for the GRE tunnel to come back up.- Select Keep Alive to enable the keepalive function for the GRE tunnel (default is disabled).(Optional) Set the Interval (sec) (in seconds) between keepalive packets that the local end of the GRE tunnel sends to the tunnel peer. This is also the interval that, when multiplied by the Hold Timer, is the length of time that the firewall must see successful keepalive packets before the GRE tunnel comes back up (range is 1 to 50; default is 10). Setting an interval too small will cause many keepalive packets that might be unnecessary in your environment and will require extra bandwidth and processing. Setting an interval too large can delay failover because error conditions might not be identified immediately.(Optional) Enter the Retry setting, which is the number of intervals that keepalive packets are not returned before the firewall considers the tunnel peer down (range is 1 to 255; default is 3). When the tunnel is down, the firewall removes routes associated with the tunnel from the forwarding table. Configuring a retry setting helps avoid taking measures on a tunnel that is not really down.(Optional) Set the Hold Timer, which is the number of Intervals that keepalive packets are successful, after which the firewall re-establishes communication with the tunnel peer (range is 1 to 64; default is 5).Click OK.Configure a routing protocol or static route to route traffic to the destination by way of the GRE tunnel. For example, Configure a Static Route to the network of the destination server and specify the egress Interface to be the local tunnel endpoint (tunnel.1). Configure the Next Hop to be the IP address of the tunnel at the opposite end. For example, 192.168.2.3.Commit your changes.Configure the opposite end of the tunnel with its public IP address, its local and peer IP addresses (that correspond to the peer and local IP addresses, respectively, of the GRE tunnel on the firewall), and its routing protocol or static route.Verify that the firewall can communicate with the tunnel peer over the GRE tunnel.
- Access the CLI.> ping source 192.168.2.1 host 192.168.2.3