Advanced WildFire Powered by Precision AI™
Forward Files For WildFire Appliance Analysis
Table of Contents
Forward Files For WildFire Appliance Analysis
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Configure Palo Alto Networks firewalls to forward
unknown files or email links and blocked files that match existing
antivirus signatures for analysis. Use the WildFire Analysis profile
to define files to forward to the WildFire private cloud (or additionally,
the public cloud for hybrid could deployments), and then attach
the profile to a security rule to trigger inspection for zero-day
malware.
Specify traffic to be forwarded for analysis based
on the application in use, the file type detected, links contained
in email messages, or the transmission direction of the sample (upload, download,
or both). For example, you can set up the firewall to forward Portable
Executables (PEs) or any files that users attempt to download during
a web-browsing session. In addition to unknown samples, the firewall
forwards blocked files that match existing antivirus signatures.
This provides Palo Alto Networks a valuable source of threat intelligence
based on malware variants that signatures successfully prevented
but neither WildFire nor the firewall has seen before.
You
can extend WildFire analysis resources to a WildFire Hybrid Cloud, by configuring
the firewall to continue to forward sensitive files to your WildFire
private cloud for local analysis, and forward less sensitive or
unsupported file types to the WildFire public cloud.
Additionally,
you can dedicate WildFire appliance resources to analyze specific
file types: either documents (Microsoft Office files and PDFs) or
PEs. For example, if you deploy a WildFire Hybrid Cloud to analyze
documents locally and PEs in one of the WildFire public clouds,
you can dedicate all analysis environments to documents. This allows
you to offload analysis of PEs to the public cloud, allowing you
to allocate additional WildFire appliance resources to process sensitive
documents.
Before you begin:
- If another firewall resides between the firewall you are configuring to forward files and the WildFire cloud or WildFire appliance, make sure that the firewall in the middle allows the following ports:
Port Usage 443 - Registration
- PCAP Downloads
- Sample Downloads
- Report Retrieval
- File Submission
- PDF Report Downloads
10443 Dynamic Updates
- (PA-7000 Series Firewalls Only) To enable a PA-7000 Series firewall to forward samples for WildFire analysis, you must first configure a data port on an NPC as a Log Card interface. If you have a PA-7000 series appliance equipped with an LFC (log forwarding card), you must configure a port used by the LFC. When configured, the log card port or the LFC interface takes precedence over the management port when forwarding WildFire samples.Specify the WildFire private or hybrid cloud to which you want to forward samples.Select DeviceSetupWildFire and edit the General Settings based on your WildFire cloud deployment (private or hybrid).WildFire Private Cloud:
- Enter the IP address or FQDN of the WildFire appliance in the WildFire Private Cloud field.WildFire Hybrid Cloud:
- Enter the WildFire Public Cloud URL:
- United States: wildfire.paloaltonetworks.com
- Europe: eu.wildfire.paloaltonetworks.com
- Japan: jp.wildfire.paloaltonetworks.com
- Singapore: sg.wildfire.paloaltonetworks.com
- United Kingdom: uk.wildfire.paloaltonetworks.com
- Canada: ca.wildfire.paloaltonetworks.com
- Australia: au.wildfire.paloaltonetworks.com
- Germany: de.wildfire.paloaltonetworks.com
- India: in.wildfire.paloaltonetworks.com
- Switzerland: ch.wildfire.paloaltonetworks.com
- Poland: pl.wildfire.paloaltonetworks.com
- Indonesia: id.wildfire.paloaltonetworks.com
- Taiwan: tw.wildfire.paloaltonetworks.com
- France: fr.wildfire.paloaltonetworks.com
- Qatar: qatar.wildfire.paloaltonetworks.com
- South Korea: kr.wildfire.paloaltonetworks.com
- South Africa: za.wildfire.paloaltonetworks.com
- Israel: il.wildfire.paloaltonetworks.com
- Saudi Arabia: sa.wildfire.paloaltonetworks.com
- Italy: it.wildfire.paloaltonetworks.com
- Spain: es.wildfire.paloaltonetworks.com
Enter the IP address or FQDN of the WildFire appliance in the WildFire Private Cloud field.Define the size limits for files the firewall forwards and configure WildFire logging and reporting settings.Continue editing WildFire General Settings (DeviceSetupWildFire).- Review the File Size Limits for files
forwarded from the firewall.It is a recommended WildFire best practice to set the File Size for PEs to the maximum size limit of 10 MB, and to leave the File Size for all other file types set to the default value.
- Select Report Benign Files to allow logging for files that receive a WildFire verdict of benign.
- Select Report Grayware Files to allow logging for files that receive a WildFire verdict of grayware.
- Define what session information is recorded in WildFire analysis reports by editing the Session Information Settings. By default, all session information is displayed in WildFire analysis reports. Clear the check boxes to remove the corresponding fields from WildFire analysis reports and click OK to save the settings.
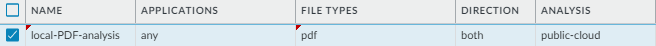
Define traffic to forward for WildFire analysis.If you have a WildFire appliance set up, you can use both the private cloud and the public cloud in a hybrid cloud deployment. Analyze sensitive files locally on your network, while sending all other unknown files to the WildFire public cloud for comprehensive analysis and prompt verdict returns.- Select ObjectsSecurity ProfilesWildFire Analysis, Add a new WildFire analysis profile, and give the profile a descriptive Name.Add a profile rule to define traffic to be forwarded for analysis and give the rule a descriptive Name, such as local-PDF-analysis.Define for the profile rule to match to unknown traffic and to forward samples for analysis based on:
- Applications—Forward files for analysis based on the application in use.
- File Types—Forward files for analysis based on file types, including links contained in email messages. For example, select PDF to forward unknown PDFs detected by the firewall for analysis.
- Direction—Forward files for analysis based the transmission direction of the file (upload, download, or both). For example, select both to forward all unknown PDFs for analysis, regardless of the transmission direction.
Set the Analysis location to which the firewall forwards files matched to the rule.- Select public-cloud to forward matching samples to the WildFire public cloud for analysis.
- Select private-cloud to forward matching samples to a WildFire private cloud for analysis.For example, to analyze PDFs that could contain sensitive or proprietary information without sending these documents out of your network, set the Analysis location for the rule local-PDF-analysis to private-cloud.
![]() Different rules can forward matched samples to different analysis locations, depending on your needs. The example above shows a rule that forwards sensitive file types for local analysis in a WildFire private cloud. You could create another rule to forward less sensitive file types, such as PEs, to the WildFire public cloud. This flexibility is supported with a WildFire hybrid cloud deployment.In a hybrid cloud deployment, files that match to both private-cloud and public-cloud rules are forwarded only to the private cloud as a cautionary measure.(Optional) Continue to add rules to the WildFire analysis profile as needed. For example, you could add a second rule to the profile to forward Android application package (APK), Portable Executable (PE), and Flash files to the WildFire public cloud for analysis.Click OK to save the WildFire analysis profile.(Optional) Continue to add rules to the WildFire analysis profile as needed. For example, you could add a second rule to the profile to forward Android application package (APK), Portable Executable (PE), and Flash files to the WildFire public cloud for analysis.Click OK to save the WildFire analysis profile.(Optional) Allocate WildFire appliance resources to analyze either documents or executables.If you are deploying a hybrid cloud to analyze specific file types locally and in the WildFire public cloud, you can dedicate analysis environments to process a file type. This allows you to better allocate resources according to your analysis environment configuration. If you do not dedicate resources for an analysis environment, resources are allocated using default settings.Use the following CLI command:
Different rules can forward matched samples to different analysis locations, depending on your needs. The example above shows a rule that forwards sensitive file types for local analysis in a WildFire private cloud. You could create another rule to forward less sensitive file types, such as PEs, to the WildFire public cloud. This flexibility is supported with a WildFire hybrid cloud deployment.In a hybrid cloud deployment, files that match to both private-cloud and public-cloud rules are forwarded only to the private cloud as a cautionary measure.(Optional) Continue to add rules to the WildFire analysis profile as needed. For example, you could add a second rule to the profile to forward Android application package (APK), Portable Executable (PE), and Flash files to the WildFire public cloud for analysis.Click OK to save the WildFire analysis profile.(Optional) Continue to add rules to the WildFire analysis profile as needed. For example, you could add a second rule to the profile to forward Android application package (APK), Portable Executable (PE), and Flash files to the WildFire public cloud for analysis.Click OK to save the WildFire analysis profile.(Optional) Allocate WildFire appliance resources to analyze either documents or executables.If you are deploying a hybrid cloud to analyze specific file types locally and in the WildFire public cloud, you can dedicate analysis environments to process a file type. This allows you to better allocate resources according to your analysis environment configuration. If you do not dedicate resources for an analysis environment, resources are allocated using default settings.Use the following CLI command:admin@WF-500# set deviceconfig setting wildfire preferred-analysis-environment documents | executables | defaultand choose from one of the following options:- documents—Dedicate analysis resources to concurrently analyze 25 documents, 1 PE, and 2 email links.
- executables—Dedicate analysis resources to concurrently analyze 25 PEs, 1 documents, and 2 email links.
- default—The appliance concurrently analyzes 16 documents, 10 portable executables (PE), and 2 email links.
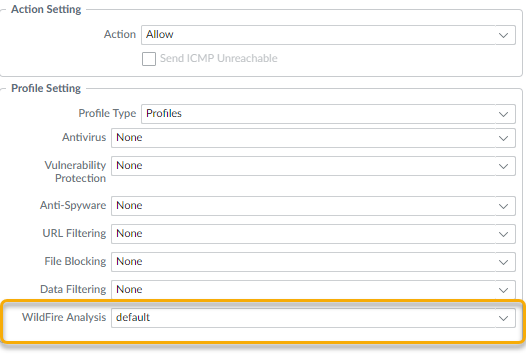
Confirm that all WildFire appliances processes are running by running the following command:admin@WF-500> show system software statusAttach the WildFire Analysis profile to a security policy rule.Traffic allowed by the security policy rule is evaluated against the attached WildFire analysis profile; the firewalls forwards traffic matched to the profile for WildFire analysis.- Select PoliciesSecurity and Add or modify a policy rule.Click the Actions tab within the policy rule.In the Profile Settings section, select Profiles as the Profile Type and select a WildFire Analysis profile to attach to the policy rule
![]() Make sure to enable the firewall to also Forward Decrypted SSL Traffic for WildFire Analysis.This is a recommended WildFire best practice.Review and implement WildFire Best Practices.Click Commit to apply the WildFire settings.(Optional) Verify WildFire Submissions.Choose what to do next...
Make sure to enable the firewall to also Forward Decrypted SSL Traffic for WildFire Analysis.This is a recommended WildFire best practice.Review and implement WildFire Best Practices.Click Commit to apply the WildFire settings.(Optional) Verify WildFire Submissions.Choose what to do next...- Verify WildFire Submissions to confirm that the firewall is successfully forwarding files for WildFire analysis.
- Submit Malware or Reports from the WildFire Appliance. Enable this feature to automatically forward malware identified in your WildFire private cloud to the WildFire public cloud. The WildFire public cloud re-analyzes the sample and generates a signature if the sample is malware. The signature is distributed to global users through Wildfire signature updates.
- Monitor WildFire Appliance Activity to assess alerts and details reported for malware.