Advanced WildFire Powered by Precision AI™
Session Information Sharing
Table of Contents
Session Information Sharing
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
In addition to forwarding unknown and blocked samples for analysis,
the firewall also forwards information about the network session
for a sample. Palo Alto Networks uses session information to learn
more about the context of the suspicious network event, indicators
of compromise related to the malware, affected hosts and clients,
and applications used to deliver the malware.
Forward of session information is enabled by default; however,
you can adjust the default settings and choose what type of session
information is forwarded to one of the WildFire cloud options.
Session Information Sharing (Cloud Management)
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS tab
and follow the guidance there.
If you’re using Prisma Access Cloud Management, continue here.
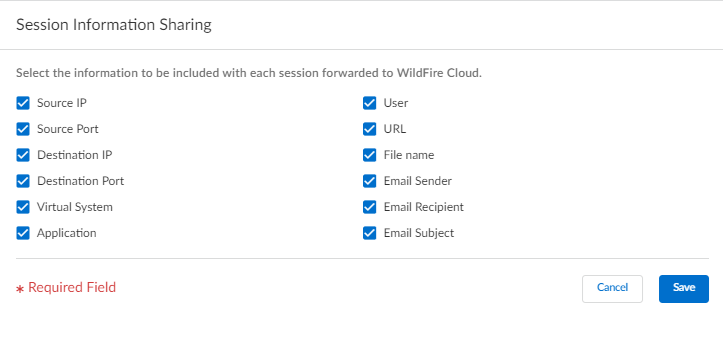
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager application on the hub.Select ConfigurationNGFW and Prisma AccessSecurity ServicesWildFire and Antivirus and configure your Session Information Settings options.
![]()
- Source IP—Forward the source IP address that sent the unknown file.
- Source Port—Forward the source port that sent the unknown file.
- Destination IP—Forward the destination IP address for the unknown file.
- Destination Port—Forward the destination port for the unknown file.
- Virtual System—Forward the virtual system that detected the unknown file.
- Application—Forward the user application that transmitted the unknown file.
- User—Forward the targeted user.
- URL—Forward the URL associated with the unknown file.
- Filename—Forward the name of the unknown file.
- Email sender—Forward the sender of an unknown email link (the name of the email sender also appears in WildFire logs and reports).
- Email recipient—Forward the recipient of an unknown email link (the name of the email recipient also appears in WildFire logs and reports).
- Email subject—Forward the subject of an unknown email link (the email subject also appears in WildFire logs and reports).
Save your changes.
Session Information Sharing (PAN-OS & Panorama)
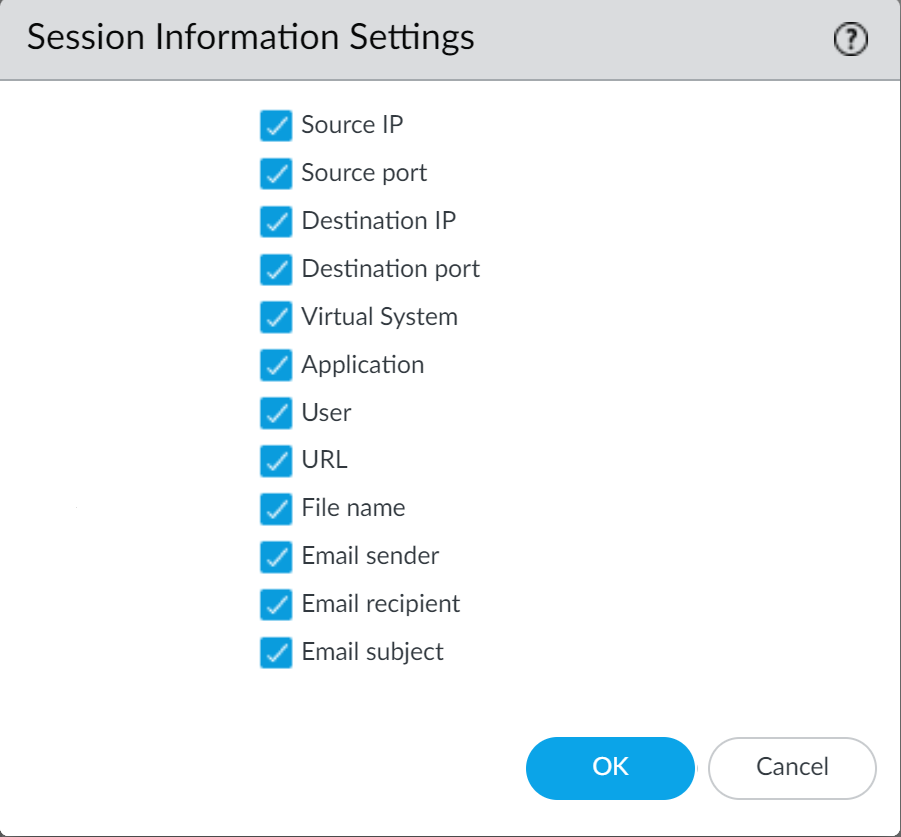
- Log in to the PAN-OS web interface.Select DeviceSetupWildFire and select or clear the following Session Information Settings options.
![]()
- Source IP—Forward the source IP address that sent the unknown file.
- Source Port—Forward the source port that sent the unknown file.
- Destination IP—Forward the destination IP address for the unknown file.
- Destination Port—Forward the destination port for the unknown file.
- Virtual System—Forward the virtual system that detected the unknown file.
- Application—Forward the user application that transmitted the unknown file.
- User—Forward the targeted user.
- URL—Forward the URL associated with the unknown file.
- Filename—Forward the name of the unknown file.
- Email sender—Forward the sender of an unknown email link (the name of the email sender also appears in WildFire logs and reports).
- Email recipient—Forward the recipient of an unknown email link (the name of the email recipient also appears in WildFire logs and reports).
- Email subject—Forward the subject of an unknown email link (the email subject also appears in WildFire logs and reports).
Click OK to save your changes.