Advanced WildFire Powered by Precision AI™
Enable Advanced WildFire Inline ML
Table of Contents
Enable Advanced WildFire Inline ML
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can prevent malicious variants of portable
executables and PowerShell scripts from entering your network in
real-time using machine learning (ML) based analytics on the firewall
dataplane. By utilizing WildFire® Cloud analysis technology on your
security platform, Advanced WildFire Inline ML dynamically detects
malicious files of a specific type by evaluating various file details,
including decoder fields and patterns, to formulate a high probability
classification of a file. This protection extends to currently unknown
as well as future variants of threats that match characteristics that
Palo Alto Networks identified as malicious. Advanced WildFire inline
ML complements your existing Antivirus profile protection configuration. Additionally,
you can specify file hash exceptions to exclude any false-positives
that you encounter, which enables you to create more granular rules in
your profiles to support your specific security needs.
To enable Advanced WildFire Inline ML, you must have an active Advanced WildFire or WildFire
subscription, create (or modify) an Antivirus (or WildFire and Antivirus for Prisma Access) security profile to configure and enable the service, and then attach
the Antivirus profile to a security policy rule.
Advanced WildFire Inline ML is not currently supported
on the VM-50 or VM50L virtual appliance.
Enable Advanced WildFire Inline ML (Cloud Management)
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS tab
and follow the guidance there.
If you’re using Prisma Access Cloud Management, continue here.
- To take advantage of WildFire Inline ML, you must have an active WildFire subscription as part of your Prisma Access subscription.Create a new or update your existing WildFire and Antivirus security profile to use the real-time WildFire inline ML models.
- Select an existing WildFire and Antivirus security profile or create a new one (select ConfigurationNGFW and Prisma AccessSecurity ServicesWildFire and Antivirus and Add Profile.
- Configure your WildFire and Antivirus profile to forward samples for analysis.
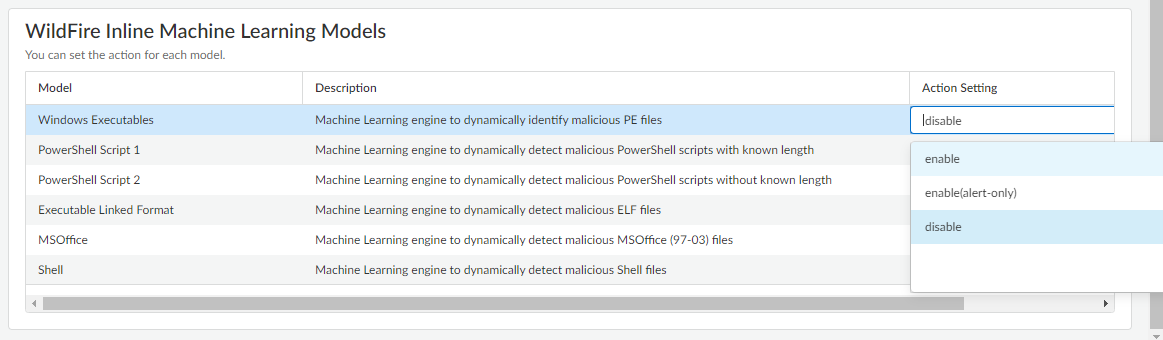
- Select WildFire Inline Machine Learning Models and apply an Action Setting for each WildFire Inline ML model. This enforces the WildFire Inline ML Actions settings configured for each protocol on a per model basis.
![]() The following classification engines available:
The following classification engines available:- Windows Executables
- PowerShell Scripts 1
- PowerShell Scripts 2
- Executable Linked Format
- MSOffice
- Shell Scripts
- enable—WildFire inspects traffic according to your selections in the WildFire Inline ML Action column in the decoders section of the Action tab.
- enable(alert-only)—WildFire inspects traffic according to your selections in the WildFire Inline ML Action column in the decoders section of the Action tab and overrides any action with a severity level higher than alert (drop, reset-client, reset-server, reset-both) alert, which allows traffic to pass while still generating and saving an alert in the threat logs.
- disable—WildFire allows traffic to pass without any policy action.
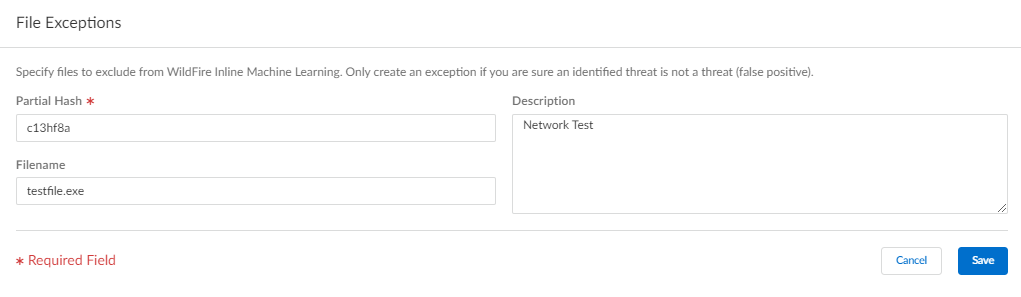
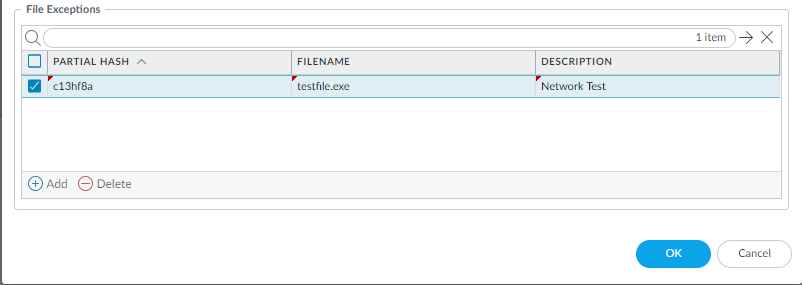
(Optional) Add file exceptions to your WildFire and Antivirus security profile if you encounter false-positives. This is typically done for users who are not forwarding files to WildFire for analysis. You can add the file exception details directly to the exception list or by specifying a file from the threat logs.If your WildFire Analysis security profile is configured to forward the filetypes analyzed using WildFire inline ML, false-positives are automatically corrected as they are received. If you continue to see ml-virus alerts for files that have been classified as benign by WildFire Analysis, please contact Palo Alto Networks Support.- Add file exceptions directly to the exception list.
- Select Advanced Settings and Add Exception in the File Exceptions pane.
- Add the hash, filename, and description of the file that you want to exclude from enforcement.
![]()
- When finished, Save your file exceptions.
Save your WildFire and Antivirus profile configuration and push configuration changes.Enable Advanced WildFire Inline ML (PAN-OS & Panorama)
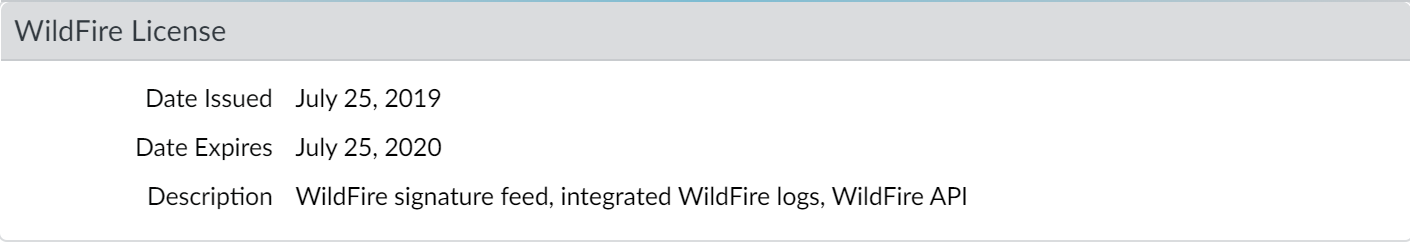
To enable your WildFire inline ML configuration, attach the Antivirus profile configured with the inline ML settings to a security policy rule.To bypass Advanced WildFire Inline ML, you must set the Action Setting to disable (for all protocols) on a per-model basis or create a WildFire Inline ML file exception using the partial hash. Do not configure your antivirus profile with signature exceptions based off of WildFire Inline ML Threat IDs. This will cause the firewall to block all traffic from your network to the IP address.WildFire inline ML is not currently supported on the VM-50 or VM50L virtual appliance.- To take advantage of WildFire inline ML, you must have an active WildFire subscription to analyze Windows executables.Verify that you have a WildFire subscription. To verify which subscriptions that you currently have licenses for, select DeviceLicenses and verify that the appropriate licenses display and have not expired.
![]() Create a new or update your existing Antivirus security profile(s) to use the real-time WildFire inline ML models.
Create a new or update your existing Antivirus security profile(s) to use the real-time WildFire inline ML models.- Select an existing Antivirus Profile or create a new one (select Objects > Security Profiles > Antivirus and Add a new profile.
- Configure your Antivirus profile.
- Select the WildFire Inline ML tab and apply an Action Setting for each WildFire Inline ML model. This enforces the WildFire Inline ML Actions settings configured for each protocol on a per model basis. The following classification engines available:
- Windows Executables
- PowerShell Scripts 1
- PowerShell Scripts 2
- Executable Linked Format (available with installation of PAN-OS content release 8367 and later)
- MSOffice (available with installation of PAN-OS content release 8434 and later)
- Shell Scripts (available with installation of PAN-OS content release 8543 and later)
- OOXML (available with installation of PAN-OS 11.1.3 and later and PAN-OS content release 8825 and later)
- Mach-O (available with installation of PAN-OS 11.1.3 and later and PAN-OS content release 8885-8930 and later)
![]() The following action settings are available:
The following action settings are available:- enable (inherit per-protocol actions)—WildFire inspects traffic according to your selections in the WildFire Inline ML Action column in the decoders section of the Action tab.
- alert-only (override more strict actions to alert)—WildFire inspects traffic according to your selections in the WildFire Inline ML Action column in the decoders section of the Action tab and overrides any action with a severity level higher than alert (drop, reset-client, reset-server, reset-both) alert, which allows traffic to pass while still generating and saving an alert in the threat logs.
- disable (for all protocols)—WildFire allows traffic to pass without any policy action.
- Click OK to exit the Antivirus Profile configuration window and Commit your new settings.
(Optional) Add file exceptions to your Antivirus security profile if you encounter false-positives. This is typically done for users who are not forwarding files to WildFire for analysis. You can add the file exception details directly to the exception list or by specifying a file from the threat logs.If your WildFire Analysis security profile is configured to forward the filetypes analyzed using WildFire inline ML, false-positives are automatically corrected as they are received. If you continue to see ml-virus alerts for files that have been classified as benign by WildFire Analysis, please contact Palo Alto Networks Support.- Add file exceptions directly to the exception list.
- Select Objects > Security Profiles > Antivirus.
- Select an Antivirus profile for which you want to exclude specific files and then select WildFire Inline ML.
- Add the hash, filename, and description of the file that you want to exclude from enforcement.
![]()
- Click OK to save the Antivirus profile and then Commit your updates.
- Add file exceptions from threat logs entries.
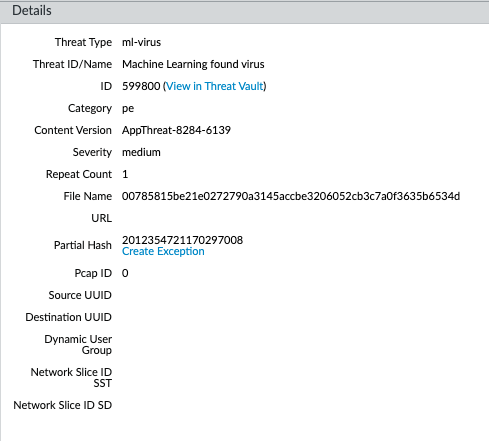
- Select Monitor > Logs > Threat and filter the logs for the ml-virus threat type. Select a threat log for a file that you wish to create a file exception for.
- Go to the Detailed Log View and scroll down to the Details pane then select Create Exception.
![]()
- Add a Description and click OK to add the file exception.
- The new file exception can be found File Exceptions list under Objects > Security Profiles > Antivirus > WildFire Inline ML.
(Optional) Verify the status of your firewall’s connectivity to the Inline ML cloud service.Use the following CLI command on the firewall to view the connection status.show mlav cloud-statusFor example:show mlav cloud-status MLAV cloud Current cloud server: ml.service.paloaltonetworks.com Cloud connection: connected
If you are unable to connect to the Inline ML cloud service, verify that the following domain is not being blocked: ml.service.paloaltonetworks.com.(Optional) Configure the Content Cloud FQDN Settings.To view information about files that have been detected using WildFire Inline ML, examine the threat logs (Monitor > Logs > Threat, then select the log type from the list). Files that have been analyzed using WildFire inline ML are labeled with the threat type ml-virus: ![]()