Next-Generation Firewall
Enable SCP Uploads for an Administrator
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Enable SCP Uploads for an Administrator
Enable Secure Protocol Copy (SCP) uploads for a firewall Superuser
administrator.
| Where Can I Use This? | What Do I Need? |
|---|---|
| NGFW (Managed by PAN-OS or Panorama) |
|
Enable the use of Secure Copy Protocol (SCP) for Superuser administrators on Palo
Alto Networks Next-Generation Firewalls to upload supported files, such as PAN-OS
software updates, dynamic content updates, and configuration files, from a local
device to a Palo Alto Networks firewall. This allows you to automate supported file
uploads using the CLI rather than uploading using the firewall web interface.
A system log generates when you successfully use SCP to upload files to your firewall
or if an SCP upload fails for any reason.
Palo Alto Networks supports SCP uploads of PAN-OS software versions, PAN-OS software
changes, dynamic content updates, PAN-OS plugin versions, configuration files, and
license key files.
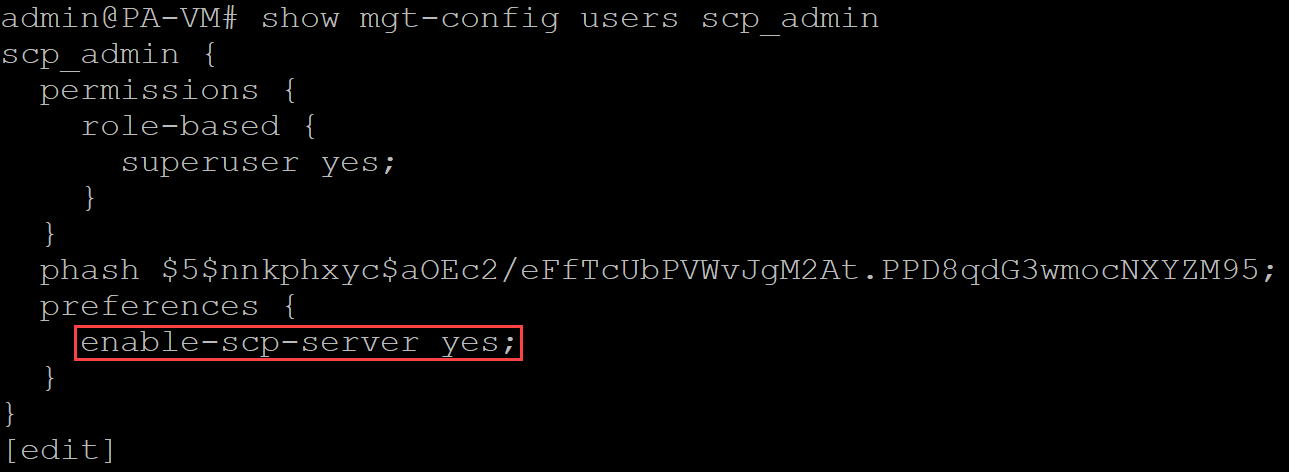
- (Optional) Configure a firewall administrator with Superuser privileges for SCP functionality.In this example, a Superuser firewall administrator named scp_admin was created.Log in to the firewall CLI.Enable SCP functionality for a Superuser admin.The admin initiating SCP must have Superuser privileges.In this example, SCP functionality is enabled for the dedicated Superuser scp_admin created in the previous step.
- Enter configuration mode.admin>configureEnable SCP functionality for a Superuser admin.admin#set mgt-config users <admin_name> preferences enable-scp-server yesVerify that SCP functionality was successfully enabled for the Superuser admin.admin#show mgt-config users <admin_name>In the permissions, verify that enable-scp-server displays yes.
![]() Commit.admin# commitPerform an SCP upload to your firewall.This step assumes you already have the file you want to upload to your firewall available on your local device.This example demonstrates how to upload an Application & Threats content update to your firewall. The predefined target directories for SCP uploads are:
Commit.admin# commitPerform an SCP upload to your firewall.This step assumes you already have the file you want to upload to your firewall available on your local device.This example demonstrates how to upload an Application & Threats content update to your firewall. The predefined target directories for SCP uploads are:- PAN-OS Software Versions—/scp/software/
- PAN-OS Software Patches—/scp/patch/
- Application & Threats Content Updates—/scp/content/
- WildFire Content Updates—/scp/wildfire/
- Antivirus Content Updates—/scp/anti-virus/
- PAN-OS Plugin Versions—/scp/plugin/
- XML Configuration Files—/scp/config/All PAN-OS configuration files must have the .xml extension appended to the file name for SCP uploads to succeed.
- License Key Files—/scp/license/
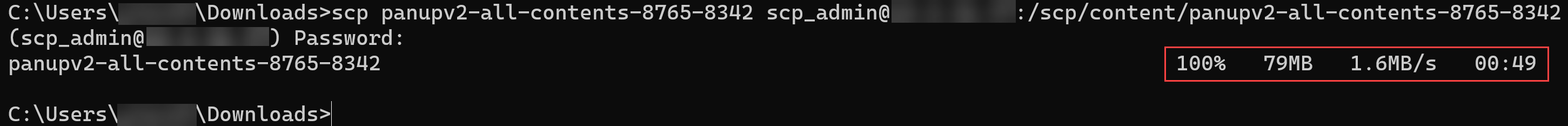
- Open a CLI terminal and use the cd command to navigate to the folder or directory where the file you want to SCP is located.After navigating to the correct folder or directory, enter ls to view the folder or directory contents.In this example, you can see the panupv2-all-contents-8765-8342 file we will upload to the firewall.Upload a file to the firewall using the SCP-enabled Superuser admin.SCP applications like WinSCP and FileZilla are not supported. You must run the SCP command from the device command line.
- Operating System running OpenSSH 8 or earlierscp <file_name> <scp_superuser>@<firewall_IP>:/scp/<file_type>/<file_name>Example of the SCP command to upload the Application & Threats content update using the scp_admin.scp panupv2-all-contents-8765-8342 scp_admin@<firewall_IP>:/scp/content/panupv2-all-contents-8765-8342Operating System running OpenSSH 9 or laterStarting from OpenSSH 9.0, the scp program defaults to the SFTP protocol for file transfers. This default behavior is incompatible with PAN-OS SCP support, resulting in the following error message in system logs: Invalid number of arguments for SCP command.Add the -O option to the SCP command to force the system to use the legacy SCP protocol instead of the default SFTP protocol.scp -O <file_name> <scp_superuser>@<firewall_IP>:/scp/<file_type>/<file_name>Example of the SCP command to upload the Application & Threats content update using the scp_admin.scp -O panupv2-all-contents-8765-8342 scp_admin@<firewall_IP>:/scp/content/panupv2-all-contents-8765-8342Enter yes when prompted to verify the authenticity of the firewall.You're not prompted to verify authenticity if you have already connected to the firewall using SSH from this device and can skip this step.Enter the SCP admin Password when prompted and click Enter to continue.The SCP upload progress displays.The SCP upload is complete when the progress status displays 100% and the CLI command prompt is becomes available.
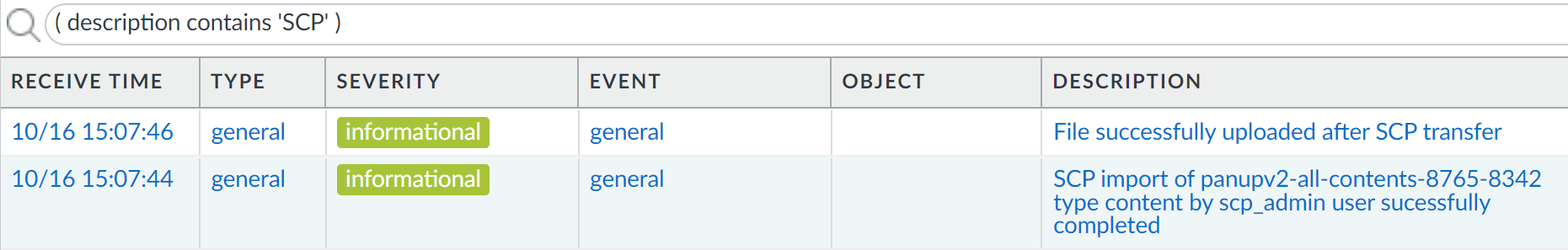
![]() Review the system logs to verify the SCP upload was successful.You can verify that the SCP upload was successful by reviewing the generated system log and confirm that the uploaded file is available. In this example, we review the system log for the SCP upload of Application & Threats content update version 8765-8342.
Review the system logs to verify the SCP upload was successful.You can verify that the SCP upload was successful by reviewing the generated system log and confirm that the uploaded file is available. In this example, we review the system log for the SCP upload of Application & Threats content update version 8765-8342.- Log in to the firewall web interface.Select MonitorLogsSystem and filter for SCP uploads.Filter for SCP uploads using the following query:( description contains 'SCP' )
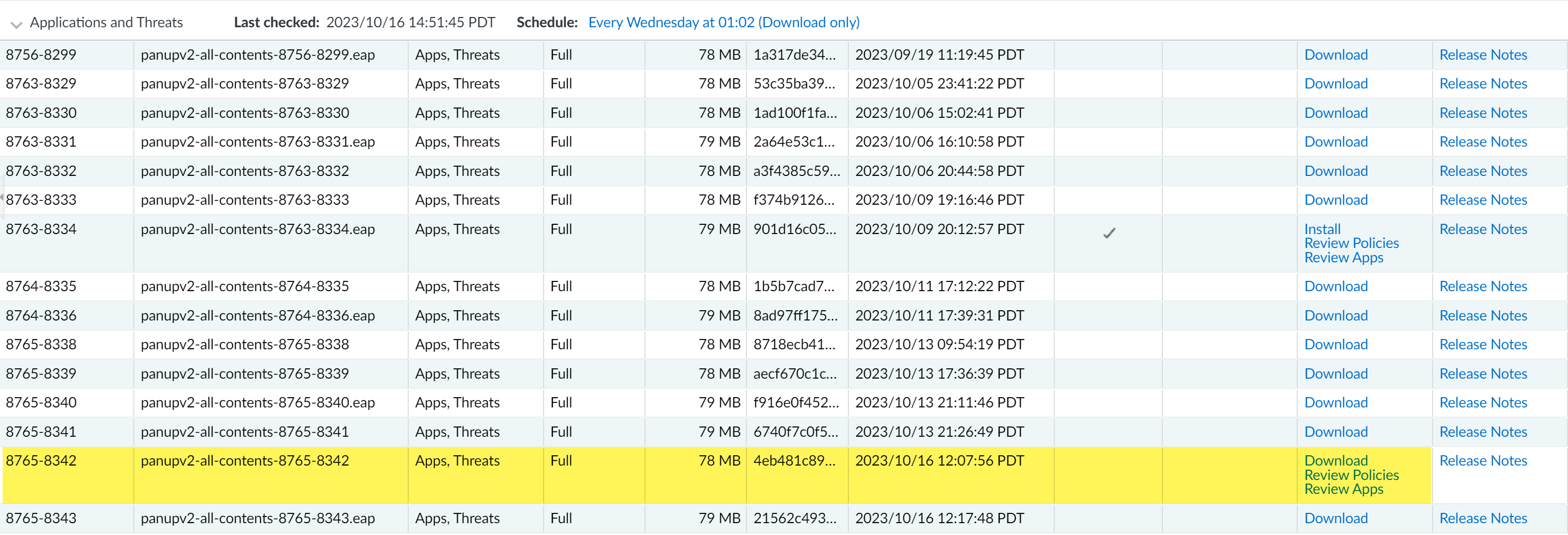
![]() Select DeviceDynamic Updates and confirm the uploaded content update is available to Download.
Select DeviceDynamic Updates and confirm the uploaded content update is available to Download.![]()