Cloud NGFW for Azure
View Cloud NGFW Logs and Activity in Panorama
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for Azure Docs
View Cloud NGFW Logs and Activity in Panorama
Learn how to view logs and activity in Panorama.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
When integrating Cloud NGFW resources with Panorama, logs and activity are
captured and displayed in Panorama on the Monitoring and Application Command Center
(ACC) tabs. Panorama collects logs generated by the Cloud NGFW and displays them on
the Monitor tab. You can select from the Traffic, Threat, URL Filtering, and
Decryption logs and filter those by ID or name.
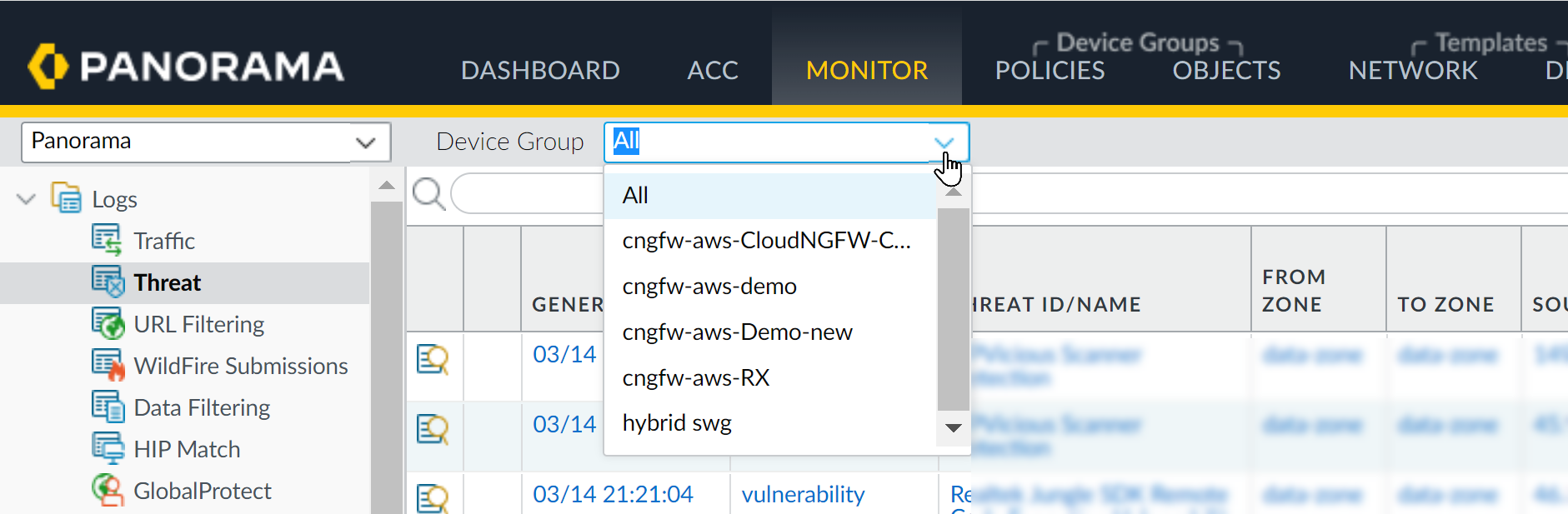
- Log in to Panorama.Select Monitor.From the Device Group drop-down, select the Cloud Device Group to view activity.You can use a Panorama filter to view the log of an individual Cloud Device Group. Locate the Device Name. Click the + icon in the upper right portion of the Panorama interface to add a new filter. Enter the name for the filter, then click Save. Click the Load Filter icon. Select the newly created filter to display the logs for the individual Cloud Device Group.From the Logs menu on the left side on the Panorama console, you can choose a specific type of log to view.
![]()
View Cloud NGFW Activity in the ACC
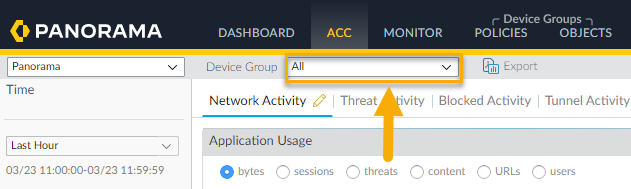
The ACC is an analytical tool that provides actionable intelligence about the activity within your network. The ACC uses the Cloud NGFW logs to graphically depict traffic trends on your network. The graphical representation allows you to interact with the data and visualize the relationships between events on the network including network usage patterns, traffic patterns, and suspicious activity and anomalies.In Panorama, you can filter ACC content based on Cloud Device Group. To learn how to filter and view specific information about activity on your Cloud NGFW resources, see the ACC documentation for PAN-OS.- Log in to Panorama.Select ACC.From the Device Group drop-down, select the Cloud Device Group to view activity.
![]() You can use a Panorama filter to view the log of an individual Cloud Device Group. Locate the Device Name. Click the + icon in the upper right portion of the Panorama interface to add a new filter. Enter the name for the filter, then click Save. Click the Load Filter icon. Select the newly created filter to display the logs for the individual Cloud Device Group.
You can use a Panorama filter to view the log of an individual Cloud Device Group. Locate the Device Name. Click the + icon in the upper right portion of the Panorama interface to add a new filter. Enter the name for the filter, then click Save. Click the Load Filter icon. Select the newly created filter to display the logs for the individual Cloud Device Group.Prerequisites for Configuring Cloud NGFW Log Collection Using Panorama
This section describes the prerequisites for configuring Panorama to collect logs for your Cloud NGFW for Azure resources.- If you intend to store logs in Panorama, you must configure your Panorama virtual appliance to run in Panorama Mode with an extra attached disk for log storage. Click here for more information.If you deployed your Panorama virtual appliance behind another firewall, the policy configuration on that firewall must allow TCP connections from the hub vNET/vWAN on the following ports: 3978, 28443, 28270.If you configured the Cloud Device Group for your Azure plugin to use a public IP address to communicate with Panorama, a public IP address must be configured on the Panorama management interface.
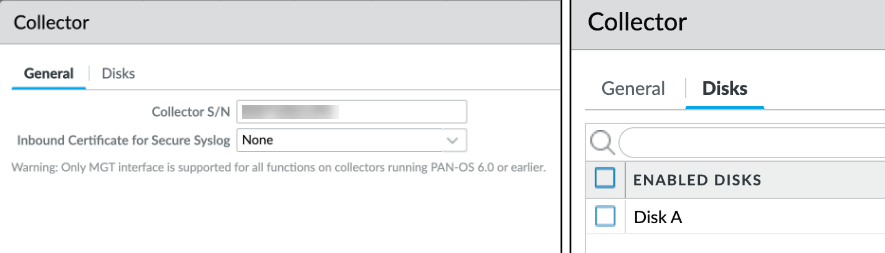
![]() Configure a managed collector with an S/N and a disk.
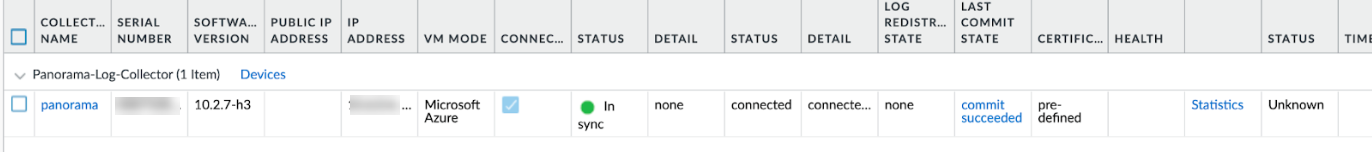
Configure a managed collector with an S/N and a disk.![]() The status must be GREEN, and in sync:
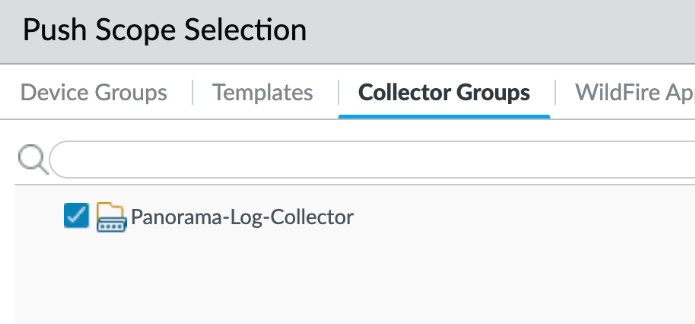
The status must be GREEN, and in sync:![]() Push to the log collector Group; explicitly push to the Collector Group to resolve synchronization issues noted in the previous step. This step is necessary. In Panorama, select Push to devices > Edit Selections > Collector Group.
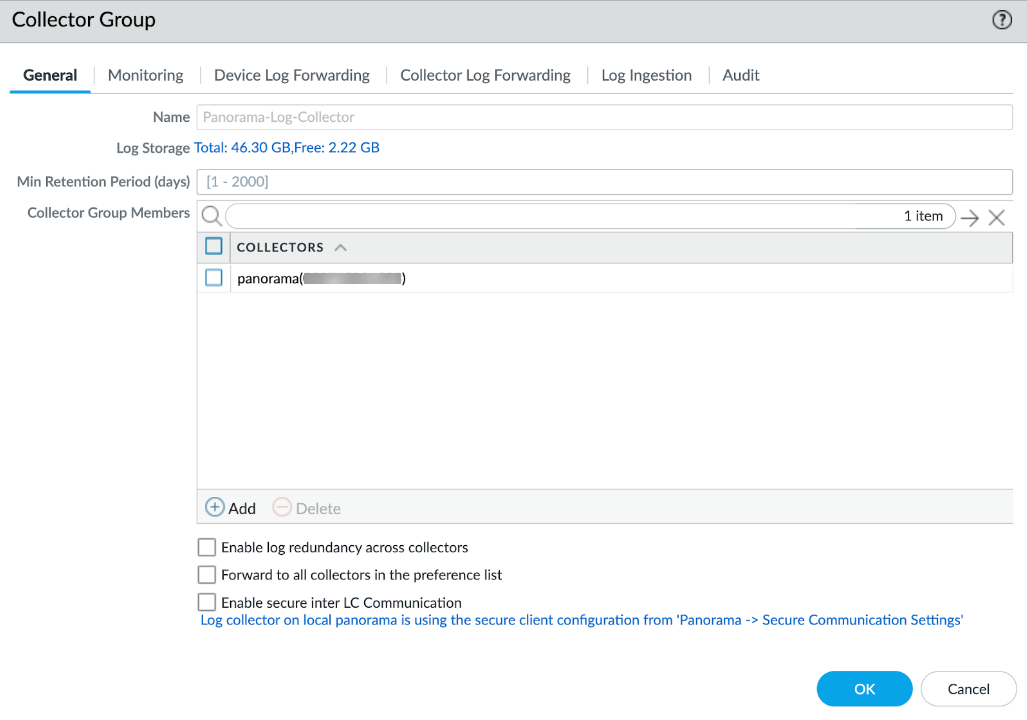
Push to the log collector Group; explicitly push to the Collector Group to resolve synchronization issues noted in the previous step. This step is necessary. In Panorama, select Push to devices > Edit Selections > Collector Group.![]() Configure the collector group with the managed collector.
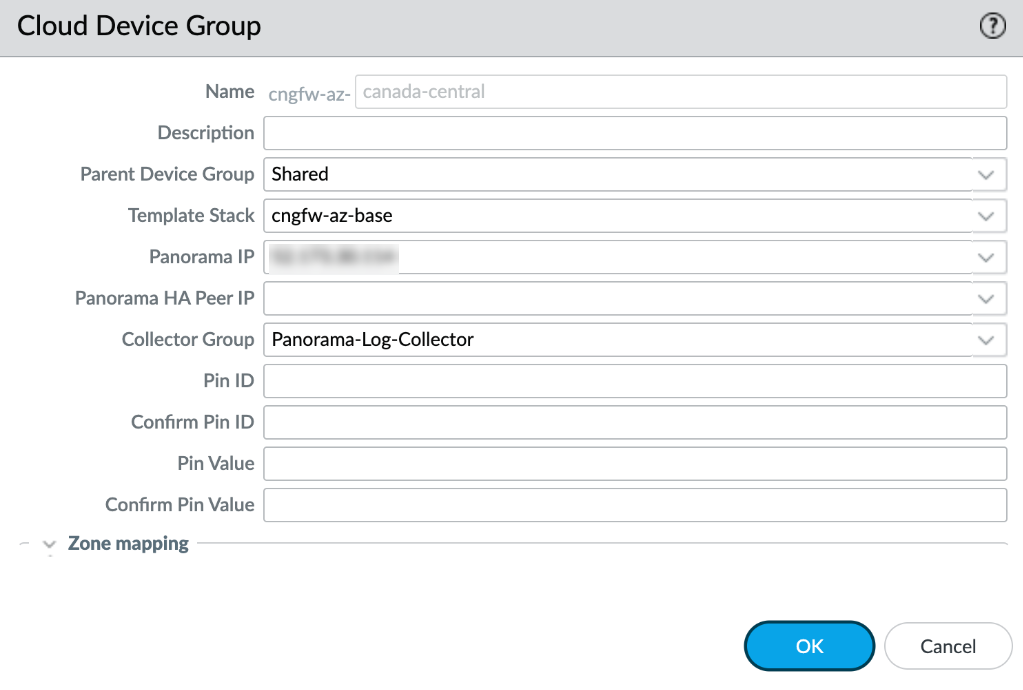
Configure the collector group with the managed collector.![]() The Cloud Device Group must have the log collector Group selected before deploying the Cloud NGFW; you can't perform this task after deploying your Cloud NGFW.
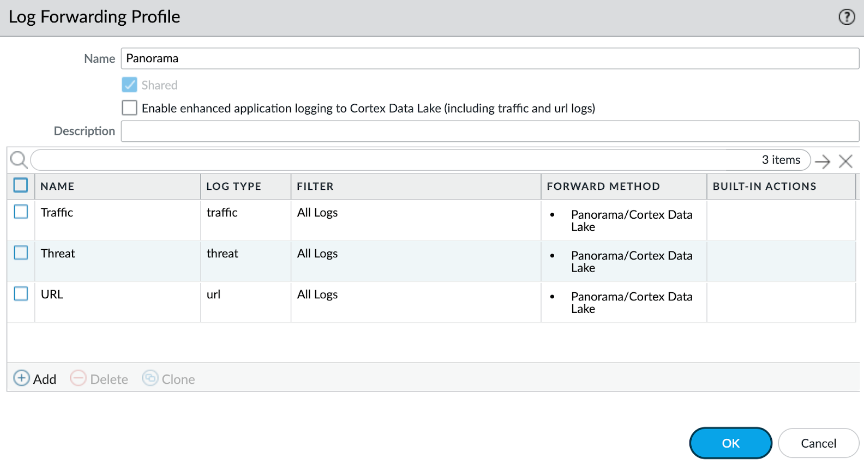
The Cloud Device Group must have the log collector Group selected before deploying the Cloud NGFW; you can't perform this task after deploying your Cloud NGFW.![]() Configure the log forwarding profile. Create this profile under the Cloud Device Group and configure it to forward the required log types to Panorama.
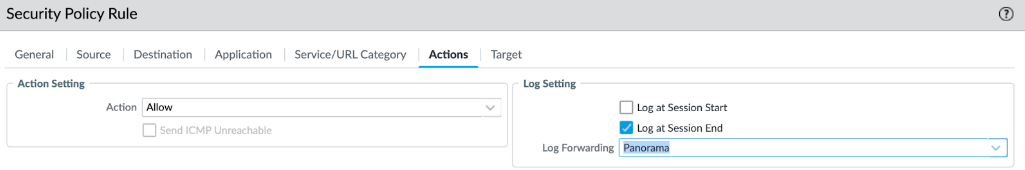
Configure the log forwarding profile. Create this profile under the Cloud Device Group and configure it to forward the required log types to Panorama.![]() Configure log forwarding in the Security policy rules.
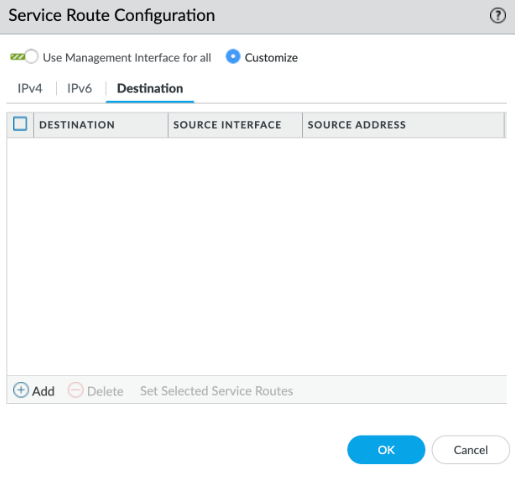
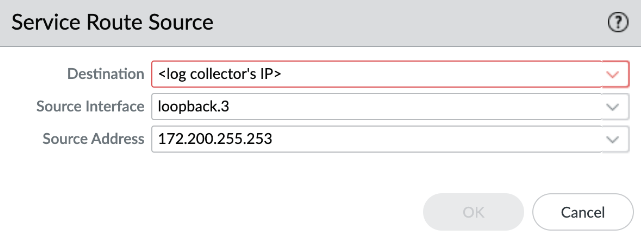
Configure log forwarding in the Security policy rules.![]() If you're using a Dedicated Log Collector, you must configure a destination-based service route for the log collector’s IP address.
If you're using a Dedicated Log Collector, you must configure a destination-based service route for the log collector’s IP address.![]() Also configure an explicit policy rule to allow traffic to the log collector IP address.
Also configure an explicit policy rule to allow traffic to the log collector IP address.![]() When using Panorama for policy management and log collection, consider that the Cloud NGFW connects to Panorama using a private IP address. If you have configured a public IP address on the management node the log collector uses the public IP address. For more information about this behavior, refer to this knowledge base article in the Customer Support Portal.If you intend to use Panorama to collect system-level logs, configure the Log Settings under the device template:
When using Panorama for policy management and log collection, consider that the Cloud NGFW connects to Panorama using a private IP address. If you have configured a public IP address on the management node the log collector uses the public IP address. For more information about this behavior, refer to this knowledge base article in the Customer Support Portal.If you intend to use Panorama to collect system-level logs, configure the Log Settings under the device template:![]()