Cloud NGFW Credit Usage Visibility
Table of Contents
Expand all | Collapse all
-
- Cloud NGFW for Azure
- Cloud NGFW Components
- Cloud NGFW for Azure Supported Regions
- Cloud NGFW for Azure Limits and Quotas
- Cloud NGFW for Azure Pricing
- Cloud NGFW for Azure Free Trial
- Cloud NGFW Credit Distribution and Management
- Cloud NGFW Credit Usage Visibility
- Start with Cloud NGFW for Azure
- Manage Cloud NGFW Roles for Azure Users
- Integrate Single Sign-on
- Monitor Cloud NGFW Health
- Create a Support Case
- Register Your Cloud NGFW Tenant with a Palo Alto Networks Support Account
- Cloud NGFW for Azure Certifications
- Cloud NGFW For Azure Privacy and Data Protection
-
- About Rulestacks and Rules on Cloud NGFW for Azure
- Create a Rulestack on Cloud NGFW for Azure
- Cloud NGFW for Azure Security Rule Objects
- Create a Prefix List on Cloud NGFW for Azure
- Create an FQDN List for Cloud NGFW on Azure
- Add a Certificate to Cloud NGFW for Azure
- Create Security Rules on Cloud NGFW for Azure
- Cloud NGFW for Azure Security Services
- Enable DNS Security on Cloud NGFW for Azure
- Set Up Outbound Decryption on Cloud NGFW for Azure
- Set Up Inbound Decryption on Cloud NGFW for Azure
-
- Panorama Integration
- Panorama Integration Prerequisites
- Link the Cloud NGFW to Palo Alto Networks Management
- Use Panorama for Cloud NGFW Policy Management
- Update Your Panorama Registration
- Update Your Panorama Registration
- Enable User-ID on the Cloud NGFW for Azure
- Configure Service Routes for On-Prem Services
- Use XFF IP Address Values in Policy
- View Cloud NGFW Logs and Activity in Panorama
- View Traffic and Threat Logs in Strata Logging Service
- Strata Cloud Manager Policy Management
-
- Configure Logging for Cloud NGFW on Azure
- Cloud NGFW for Azure Traffic Log Fields
- Cloud NGFW for Azure Threat Log Fields
- Cloud NGFW for Azure Decryption Log Fields
- Enable Log Settings
- Disable Log Settings
- Enable Activity Logging on Cloud NGFW for Azure
- Multiple Logging Destinations on Cloud NGFW for Azure
- View the Logs
- View Audit Logs on a Firewall Resource
- View Audit Logs on Resource Groups
- What's New
- Cloud NGFW for Azure Known Issues
- Cloud NGFW for Azure Addressed Issues
Cloud NGFW Credit Usage Visibility
Gain greater visibility about your Cloud NGFW credits.
Use the credit usage and visibility functionality to gain more insights into how your
Cloud NGFW credits are consumed. With this information you can:
- Determine how your Cloud-Delivered Security Services (CDSS) are being consumed.
- View firewall and tenant level credit usage daily, monthly, or yearly.See Credit Distribution and Management for more information.
To use the credit visibility functionality for your Cloud NGFW:
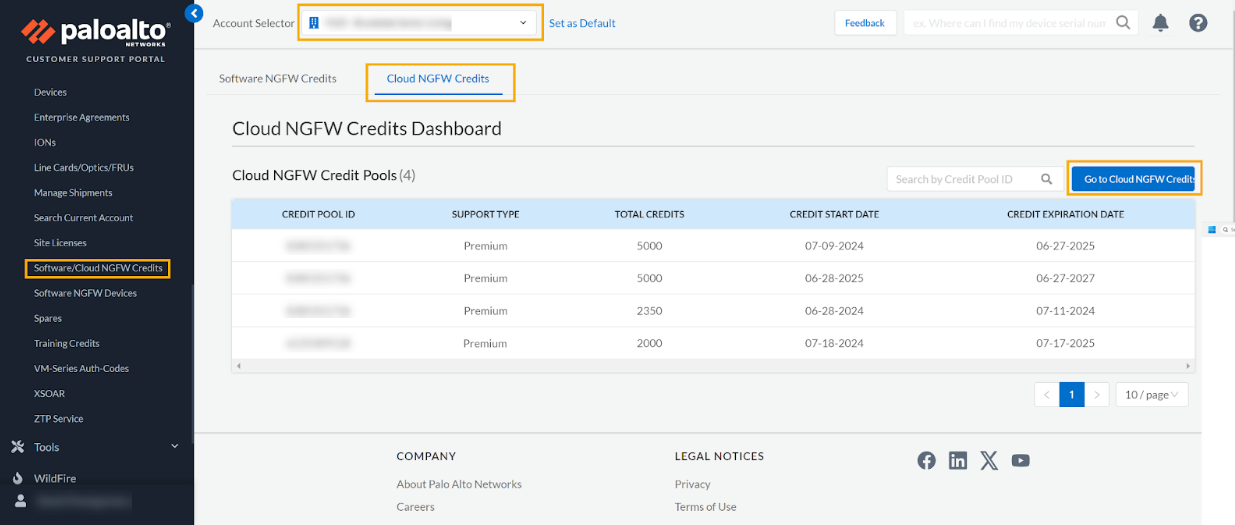
- Log in to the Palo Alto Networks Customer Support Portal.In the portal, select Product.Select Software and Cloud NGFW credits.Use the Account Selector to ensure that you’re viewing the correct account, then click the Cloud NGFW credits tab to display the credit pools associated with the account.Click Go to Cloud NGFW Credits to access the Cloud NGFW Credit Management application in the Palo Alto Networks hub.
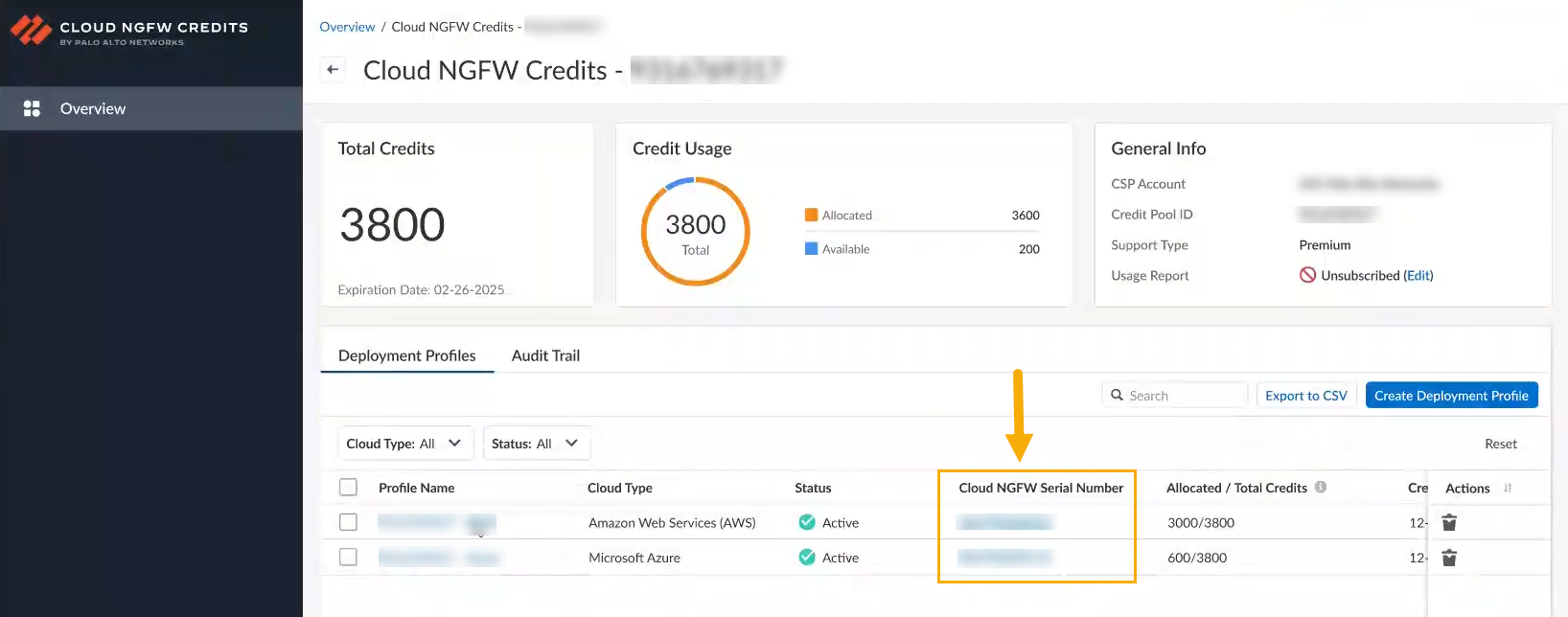
![]() The Cloud NGFW Credits page provides access to credit visibility functionality. To access it, select the Cloud NGFW serial number associated with the deployment profile you want to view.The Cloud NGFW Credits page provides access to the credit visibility functionality. To access it, select the Cloud NGFW serial number associated with the deployment profile you want to view.
The Cloud NGFW Credits page provides access to credit visibility functionality. To access it, select the Cloud NGFW serial number associated with the deployment profile you want to view.The Cloud NGFW Credits page provides access to the credit visibility functionality. To access it, select the Cloud NGFW serial number associated with the deployment profile you want to view.![]()
Use the Tenant Usage Details Page
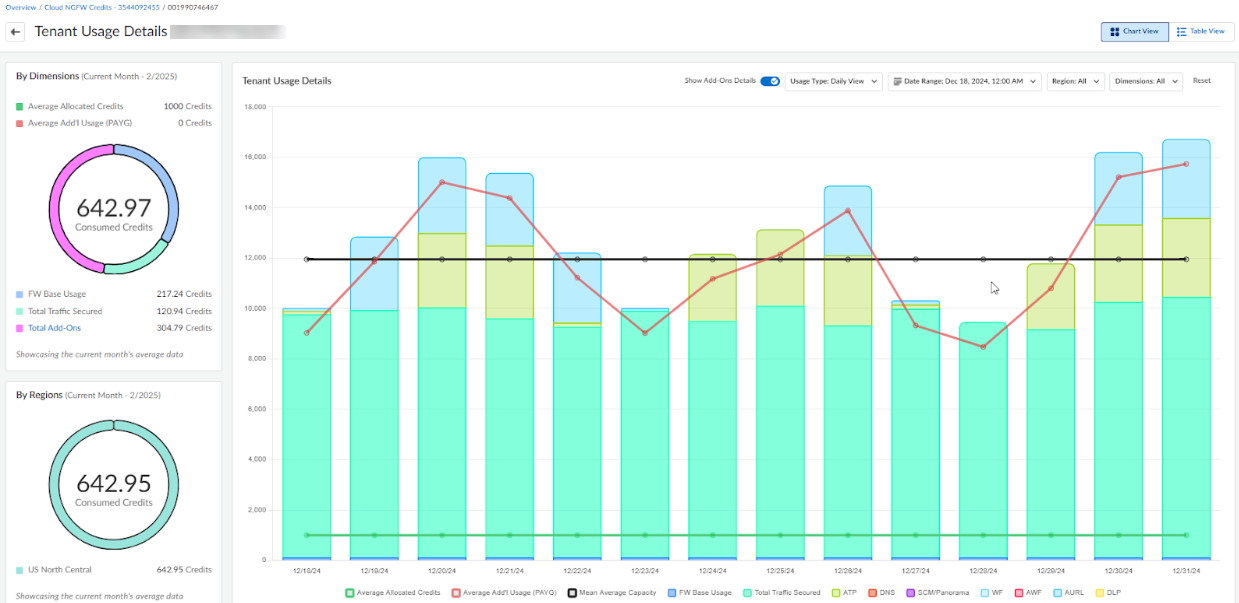
The Tenant Usage Details page displays information about how Cloud NGFW credits are consumed. When you first access this page a chart view provides a graphical representation of your credit consumption. You can change this view to a table view using the option in the upper right of the web interface.Tenant Usage Details Chart ViewThe chart view provides a color-coded graphical representation of usage details and is organized by base FW usage, traffic secured, and dimensions. When using the chart view, consider:- By default, the chart view displays usage for the last 15 days.
- You can toggle Show Add-ons Details to view credits consumed by each and every add-on service. This also provides average allocated credits and average additional credit usage for the selected time range; this is represented by the green and red line, respectively.
- By default, data is limited to five years for monthly or yearly views. When looking at the daily view, you can only select dates for 2 years from the current date.
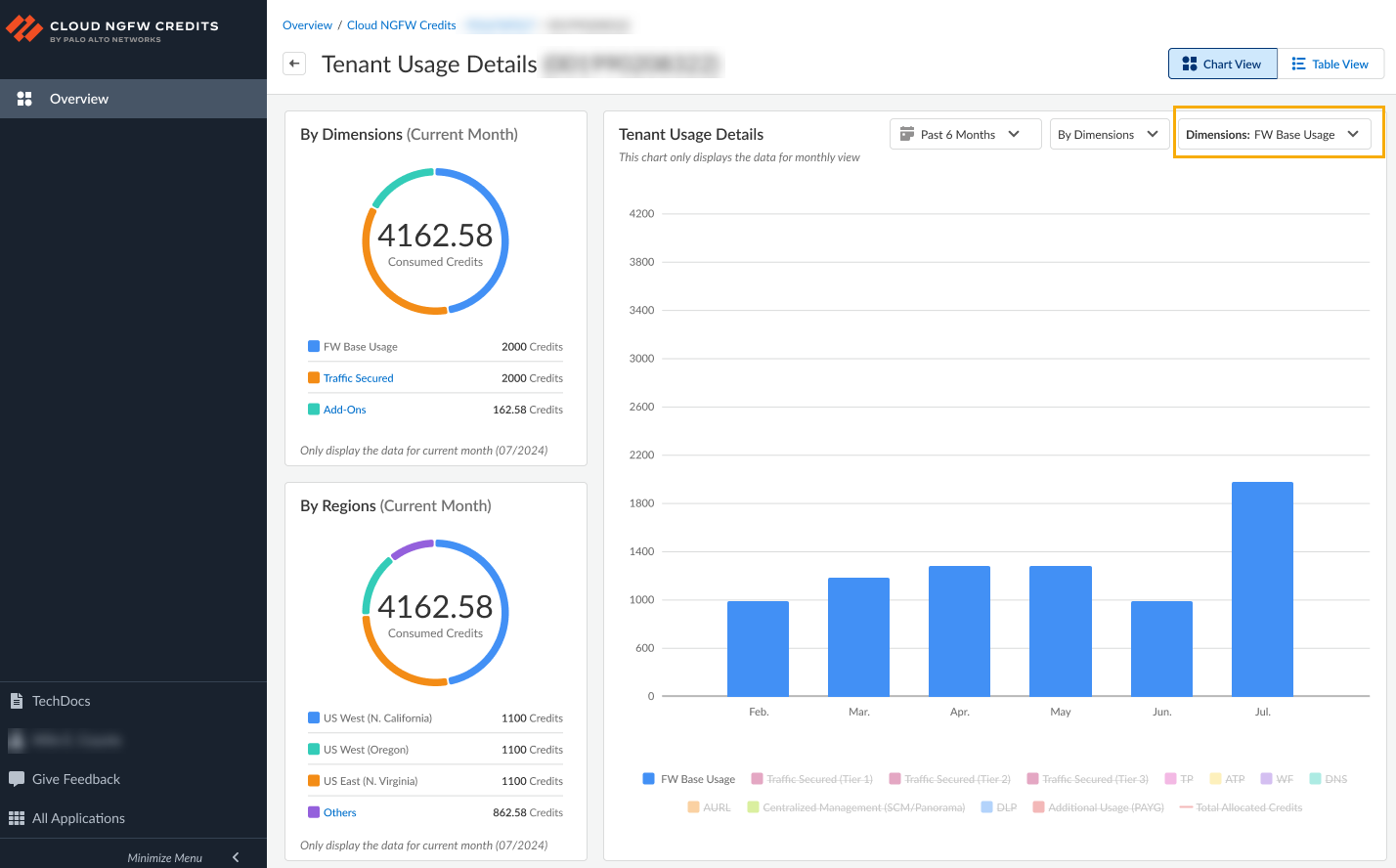
![]() To display credit consumption based on FW Base Usage, select that dimension:
To display credit consumption based on FW Base Usage, select that dimension:![]() DimensionsThe table below describes what dimensions you can view.
DimensionsThe table below describes what dimensions you can view.Dimension Description FW base usage Firewall base usage. Traffic secured Indicates the amount of traffic secured by Cloud NGFW. You pay an hourly rate for each Cloud NGFW resource. You also pay for the amount of traffic, billed by the gigabyte, processed by the NGFW resource. TP Threat prevention (TP) ATP Advanced Threat Prevention (ATP) is an intrusion prevention system (IPS) solution that can detect and block malware, vulnerability exploits, and command and control (C2) across all ports and protocols, using a multilayered prevention system with components operating on Cloud NGFW for AWS and in the cloud. The Threat Prevention cloud operates a multitude of detection services using the combined threat data from Palo Alto Networks services to create signatures, each possessing specific identifiable patterns, and are used by the Cloud NGFW for AWS to enforce Security policy rules when matching threats and malicious behaviors are detected. These signatures are categorized based on the threat type and are assigned unique identifier numbers. To detect threats that correspond with these signatures, Cloud NGFW for AWS operates analysis engines that inspect and classify network traffic exhibiting anomalous traits. WF Cloud NGFW can detect and forward files, executables, and malicious scripts (such as JScript and PowerShell) in your VPC traffic to WildFire™ cloud service for analysis. WildFire then applies threat intelligence, analytics, and correlations on these forwarded files (executables or scripts) and delivers verdicts based on the analysis. If a threat is detected on them, WildFire creates protections to block malware, and globally distribute these protections for that threat in a few minutes. DNS Domain Name Service (DNS) is a critical and foundational protocol of the internet, as described in the core RFCs for the protocol. Malicious actors have utilized command and control (C2) communication channels over the DNS and, in some cases, have even used the protocol to exfiltrate data. DNS exfiltration can happen when a bad actor compromises an application instance in your VPC and then uses DNS lookup to send data out of the VPC to a domain that they control. Malicious actors can also infiltrate malicious data and payloads to the VPC workloads over DNS. Palo Alto Networks Unit 42 research has described different types of DNS abuse discovered. AURL Palo Alto Networks provides a set of predefined URL filtering categories. You can also specify your own URL filtering categories using a customer URL category object. For example, create a custom list of URLs that you want to use as match criteria in a Security policy rule. This is a good way to specify exceptions to URL categories, where you’d like to enforce specific URLs differently than the URL category to which they belong. DLP Data loss prevention (DLP). Tenant Usage Details table ViewThe table view displays how credits are consumed in a tabular format that you can download as a CSV file. Use this view to search for a specific deployment profile or to change how consumed credits are displayed over a period of time. This view includes the following areas:- Credit Info. This area displays the total number of credits allocated to the deployment profile. You can expand this view to display all deployment profiles associated with the tenant.
- Tenant Info. This area displays the cloud type (either Amazon Web Services or Microsoft Azure), the number of firewalls, and a link to the Cloud NGFW console. Use the Check Firewall Usage Details link to view details about how credits are used by the firewall.
- Tenant Usage Details. Use this area of the interface to display detailed
information about how credits are used over a period of time; you can
optionally customize this display by specifying the time frame for your
credit consumption. It includes:
- Search. Locate how credits are consumed for a given deployment profile.
- Total Allocated Credits. The total number of credits allocated to the deployment profile.
- Total Consumed Credits (FW Usage). The total number of credits consumed by the deployment profile; also referred to as the total number of credits consumed by the firewall.
- Yearly Average Additional Usage. This represents the number of
credits consumed beyond the credits allocated to the deployment
profile over the course of the year.The Cloud NGFW does not incur additional daily usage charges. Additional usage fees are applicable only if the monthly average exceeds the total allocated credits through the deployment profile. Any additional usage credits will be charged as Pay-As-You-Go (PAYG).
- Download as CSV. Use this option to download credit consumption data to a
.CSV file.Click Reset to clear credit data.
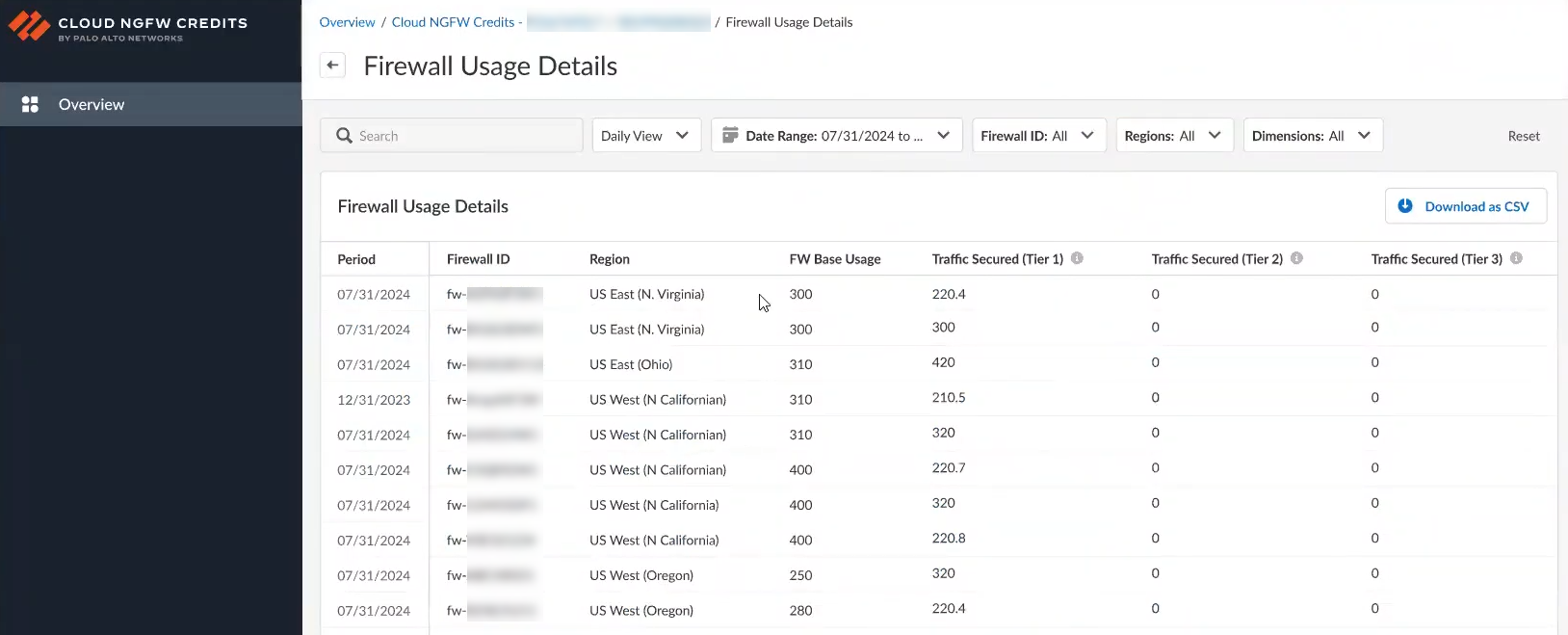
![]() You can also display details for each firewall by selecting the link in the Total Consumed Credits (FW Usage). By default Firewall Usage Details are displayed in a daily view; you can use additional options to display these details in a specific date range, or, you can display them based on an individual firewall ID, by region, or by dimensions. Options include:
You can also display details for each firewall by selecting the link in the Total Consumed Credits (FW Usage). By default Firewall Usage Details are displayed in a daily view; you can use additional options to display these details in a specific date range, or, you can display them based on an individual firewall ID, by region, or by dimensions. Options include:- Period. The time frame for credit consumption.
- Firewall ID. The ID associated with the firewall.
- Region. The region where the firewall resides.
- FW Base Usage. Indicates the credits allocated to the base firewall.
- Traffic Secured (based on Tier). The credits are allocated to secured traffic.
![]()