Enterprise DLP
Report a False Positive Detection
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
-
- About Enterprise DLP
- What’s Supported with Enterprise DLP?
- Data Patterns, Document Types, and Data Profiles
- Enable Role Based Access
- Edit the Cloud Content Settings
- Edit the Enterprise DLP Data Filtering Settings
- Edit the Enterprise DLP Snippet Settings
- Configure Syslog Forwarding for Enterprise DLP Incidents
- Request a New Feature
-
-
- Enable Existing Data Patterns and Filtering Profiles
- Modify a DLP Rule on Strata Cloud Manager
- Create a SaaS Security Policy Recommendation to Leverage Enterprise DLP
- Reduce False Positive Detections
- Data Dictionaries
- Recommendations for Security Policy Rules
- Enterprise DLP Migrator
-
-
-
- Driver License - Australia
- Driver License - Austria
- Driver License - Belgium
- Driver License - Brazil
- Driver License - Bulgaria
- Driver License - Canada
- Driver License - China
- Driver License - Croatia
- Driver License - Cyprus
- Driver License - Czech Republic
- Driver License - Denmark
- Driver License - Estonia
- Driver License - Finland
- Driver License - France
- Driver License - Germany
- Driver License - Greece
- Driver License - Hungary
- Driver License - Iceland
- Driver License - Ireland
- Driver License - Italy
- Driver License - Japan
- Driver License - Latvia
- Driver License - Liechtenstein
- Driver License - Lithuania
- Driver License - Luxembourg
- Driver License - Malta
- Driver License - Netherlands
- Driver License - New Zealand
- Driver License - Norway
- Driver License - Poland
- Driver License - Portugal
- Driver License - Romania
- Driver License - Slovakia
- Driver License - Slovenia
- Driver License - South Africa
- Driver License - South Korea
- Driver License - Spain
- Driver License - Sweden
- Driver License - Switzerland
- Driver License - Taiwan
- Driver License - Turkey
- Driver License - UK
- Driver License - US
- Driver License - US - AK
- Driver License - US - AL
- Driver License - US - AR
- Driver License - US - AZ
- Driver License - US - CA
- Driver License - US - CO
- Driver License - US - CT
- Driver License - US - DC
- Driver License - US - DE
- Driver License - US - FL
- Driver License - US - GA
- Driver License - US - HI
- Driver License - US - IA
- Driver License - US - ID
- Driver License - US - IL
- Driver License - US - IN
- Driver License - US - KS
- Driver License - US - KY
- Driver License - US - LA
- Driver License - US - MA
- Driver License - US - ME
- Driver License - US - MI
- Driver License - US - MN
- Driver License - US - MO
- Driver License - US - MS
- Driver License - US - MT
- Driver License - US - NC
- Driver License - US - ND
- Driver License - US - NE
- Driver License - US - NH
- Driver License - US - NM
- Driver License - US - NV
- Driver License - US - NY
- Driver License - US - OH
- Driver License - US - OK
- Driver License - US - OR
- Driver License - US - PA
- Driver License - US - RI
- Driver License - US - SC
- Driver License - US - SD
- Driver License - US - TN
- Driver License - US - TX
- Driver License - US - UT
- Driver License - US - VA
- Driver License - US - VT
- Driver License - US - WA
- Driver License - US - WI
- Driver License - US - WV
- Driver License - US - WY
- National ID - Albania
- National Id - Argentina ID
- National ID - Australia
- National Id - Austria - Central Register of Residents
- National Id - Austria Social Security Card - e-card
- National ID - Bahrain
- National Id - Belgium - Citizen Service Number - BSN
- National Id - Belgium - National Registration Number
- National ID - Bosnia and Herzegovina
- National ID - Brazil
- National Id - Brazil - CNPJ
- National Id - Brazil - CPF
- National Id - Bulgaria - Uniform Civil Number
- National Id - Canada - Social Insurance Number - SIN
- National ID - Chile
- National Id - China ID
- National Id - Colombia National ID
- National ID - Costa Rica
- National Id - Croatia - Personal Identification Number
- National ID - Cuba
- National Id - Cyprus - Identity Card
- National Id - Czech - Birth Number
- National Id - Czech - National eID Card
- National Id - Denmark - CPR Number
- National ID - Dominican Republic
- National ID - Ecuador
- National ID - Egypt
- National Id - Estonia - Personal Identification Code
- National Id - Finland - Personal Identity Code - HETU
- National Id - France - INSEE
- National Id - France - Social Security Number - NIR
- National Id - Germany
- National Id - Greece
- National Id - Hong Kong ID
- National Id - Hungary - Personal Identification Number
- National Id - Iceland
- National ID - India
- National ID - Indonesia
- National ID - Iran
- National Id - Ireland - Personal Public Service Number - PPSN
- National ID - Israel
- National Id - Italy - Fiscal Code Card - Codice Fiscale
- National Id - Japan Corporate Number
- National Id - Japan My Number
- National ID - Kazakhstan
- National ID - Kuwait
- National Id - Latvia - Personal Public Service Number - PPSN
- National Id - Liechtenstein
- National Id - Lithuania
- National Id - Luxembourg
- National Id - Malaysia National ID
- National Id - Malta
- National ID - Mexico
- National ID - Moldova
- National ID - Montenegro
- National Id - Netherlands - Citizen Service Number - BSN
- National ID - North Macedonia
- National Id - Norway - Identification Number - Fødselsnummer
- National ID - Pakistan
- National ID - Paraguay
- National ID - Peru
- National ID - Philippines
- National Id - Poland
- National Id - Portugal
- National Id - Romania - Identity Card - CNP
- National ID - Russia
- National ID - Serbia
- National Id - Singapore NRIC
- National Id - Slovakia
- National Id - Slovenia
- National ID - South Africa
- National ID - South Korea
- National Id - Spain - National Identity Document - Documento Nacional de Identidad
- National ID - Sri Lanka
- National Id - Sweden - Personal Identity Number
- National ID - Switzerland
- National Id - Taiwan ID
- National Id - Thailand ID
- National Id - Turkey Identification Number
- National Id - UAE Emirates ID
- National Id - UK National Insurance Number - NINO
- National ID - Uruguay
- National Id - US Social Security Number - SSN
- National ID - Venezuela
- Passport - Australia
- Passport - Austria
- Passport - Belgium
- Passport - Brazil
- Passport - Bulgaria
- Passport - Canada
- Passport - Croatia
- Passport - Cyprus
- Passport - Czech Republic
- Passport - Denmark
- Passport - Estonia
- Passport - Finland
- Passport - France
- Passport - Germany
- Passport - Greece
- Passport - Hungary
- Passport - Iceland
- Passport - Ireland
- Passport - Italy
- Passport - Latvia
- Passport - Liechtenstein
- Passport - Lithuania
- Passport - Luxembourg
- Passport - Malta
- Passport - Netherlands
- Passport - New Zealand
- Passport - Norway
- Passport Number - China
- Passport Number - Singapore
- Passport Number - South Africa
- Passport number - South Korea
- Passport number - Taiwan
- Passport - Poland
- Passport - Portugal
- Passport - Romania
- Passport - Slovakia
- Passport - Slovenia
- Passport - Spain
- Passport - Sweden
- Passport - Switzerland
- Passport - Turkey
- Passport - UK
- Passport - US
- Tax Id - Australia
- Tax Id - Austria
- Tax Id - Belgium
- Tax Id - Brazil
- Tax Id - Bulgaria
- Tax ID - Canada
- Tax ID - China
- Tax ID - Costa Rica
- Tax Id - Cyprus
- Tax Id - Czech Republic
- Tax Id - Denmark
- Tax ID - Dominican Republic
- Tax Id - Estonia
- Tax Id - Finland
- Tax Id - France
- Tax Id - Germany
- Tax Id - Greece
- Tax Id - Hungary
- Tax Id - Iceland
- Tax Id - India - PAN
- Tax Id - Ireland
- Tax Id - Italy
- Tax ID - Japan
- Tax Id - Latvia
- Tax Id - Liechtenstein
- Tax Id - Lithuania
- Tax Id - Luxembourg
- Tax Id - Malta
- Tax Id - Netherlands
- Tax Id - New Zealand
- Tax Id - Norway
- Tax Id - Poland
- Tax Id - Portugal
- Tax Id - Romania
- Tax Id - Slovakia
- Tax Id - Slovenia
- Tax ID - South Africa
- Tax ID - South Korea
- Tax Id - Spain
- Tax Id - Sweden
- Tax Id - Switzerland
- Tax ID - Taiwan
- Tax Id - Turkey
- Tax Id - UK - UTR
- Tax Id - US - TIN
-
-
-
-
- March 2025
- February 2025
- January 2025
- December 2024
- November 2024
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- April 2024
- March 2024
- January 2024
- December 2023
- November 2023
- October 2023
- August 2023
- July 2023
- June 2023
- May 2023
- March 2023
- February 2023
- January 2023
- November 2022
- October 2022
- August 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- July 2021
- New Features in Enterprise DLP Plugin 5.0
- New Features in Enterprise DLP Plugin 4.0
- New Features in Enterprise DLP Plugin 3.0
- New Features in Enterprise DLP Plugin 1.0
-
- Known Issues in the Enterprise DLP Cloud Service
- Known Issues in Endpoint DLP
-
- Known Issues in Enterprise DLP Plugin 5.0.6
- Known Issues in Enterprise DLP Plugin 5.0.5
- Known Issues in Enterprise DLP Plugin 5.0.4
- Known Issues in Enterprise DLP Plugin 5.0.3
- Known Issues in Enterprise DLP Plugin 5.0.2
- Known Issues in Enterprise DLP Plugin 5.0.1
- Known Issues in Enterprise DLP Plugin 5.0.0
-
- Known Issues in Enterprise DLP Plugin 3.0.10
- Known Issues in Enterprise DLP Plugin 3.0.9
- Known Issues in Enterprise DLP Plugin 3.0.8
- Known Issues in Enterprise DLP Plugin 3.0.7
- Known Issues in Enterprise DLP Plugin 3.0.6
- Known Issues in Enterprise DLP Plugin 3.0.5
- Known Issues in Enterprise DLP Plugin 3.0.4
- Known Issues in Enterprise DLP Plugin 3.0.3
- Known Issues in Enterprise DLP Plugin 3.0.2
- Known Issues in Enterprise DLP Plugin 3.0.1
- Known Issues in Enterprise DLP Plugin 3.0.0
-
- Known Issues in Enterprise DLP Plugin 1.0.8
- Known Issues in Enterprise DLP Plugin 1.0.7
- Known Issues in Enterprise DLP Plugin 1.0.6
- Known Issues in Enterprise DLP Plugin 1.0.5
- Known Issues in Enterprise DLP Plugin 1.0.4
- Known Issues in Enterprise DLP Plugin 1.0.3
- Known Issues in Enterprise DLP Plugin 1.0.2
- Known Issues in Enterprise DLP Plugin 1.0.1
- Enterprise DLP Limitations
- Changes to Default Behavior
-
Report a False Positive Detection
Report false positive detections by Enterprise Data Loss Prevention (E-DLP) to Palo Alto Networks
to improve the DLP cloud service detection accuracy.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Enterprise DLP license
|
In some instances, Enterprise Data Loss Prevention (E-DLP) might incorrectly detect and take action
on the file or network traffic that it should not have. This is called a
false positive detection and they can cause
productivity impacts to individual employees and Enterprise DLP administrators
alike. False positive detections are commonly caused by traffic match criteria in
predefined regular expression (regex).
Report false positive detections to Palo Alto Networks to improve Enterprise DLP detection accuracy for yourself and other Enterprise DLP users. You report a
false positive detection against the DLP Incident where the false positive detection
occurred.
The DLP Incident must meet the following conditions to report a false positive
detection:
- Traffic matched against a predefined regular expression (regex) data patterns
- The traffic is match is high confidence
- There is a snippet available of the false positive detection to share with Palo Alto Networks
For predefined data patterns marked with
Augmented with ML, Enterprise DLP uses AI and advanced machine
learning (ML) techniques to improve its detection engine when you report a false
positive detection. This enables Enterprise DLP to continuously learn from
your feedback to reduce false positive detections and increase detection
accuracy for yourself and other Enterprise DLP users. For Enterprise DLP to use AI and ML to learn from your false positive detections
and improve its detection engine:
- Files in inspected traffic must be 19 MB and smaller
- The number of traffic matches per data pattern in the data profile is 100 matches or less
All selected DLP incident snippets are shared with Palo Alto Networks when you
submit a false positive report. The selected snippets are stored and accessible
by Palo Alto Networks for up to 90 days to enable Palo Alto Networks to
investigate and improve Enterprise DLP detection accuracy.
Enterprise DLP does not support reporting false positive detections for
incidents generated from Email DLP or SaaS Security.
- Log in to Strata Cloud Manager.
- Reviewed your data patterns, profiles, and Security policy rules to reduce false positive detections.
- Select ManageConfigurationData Loss PreventionDLP Incidents.
- In the Incidents, click the File name of the false positive DLP incident you want to report to Palo Alto Networks.
- In the Matches within Data Profile window, click Report False Positive.
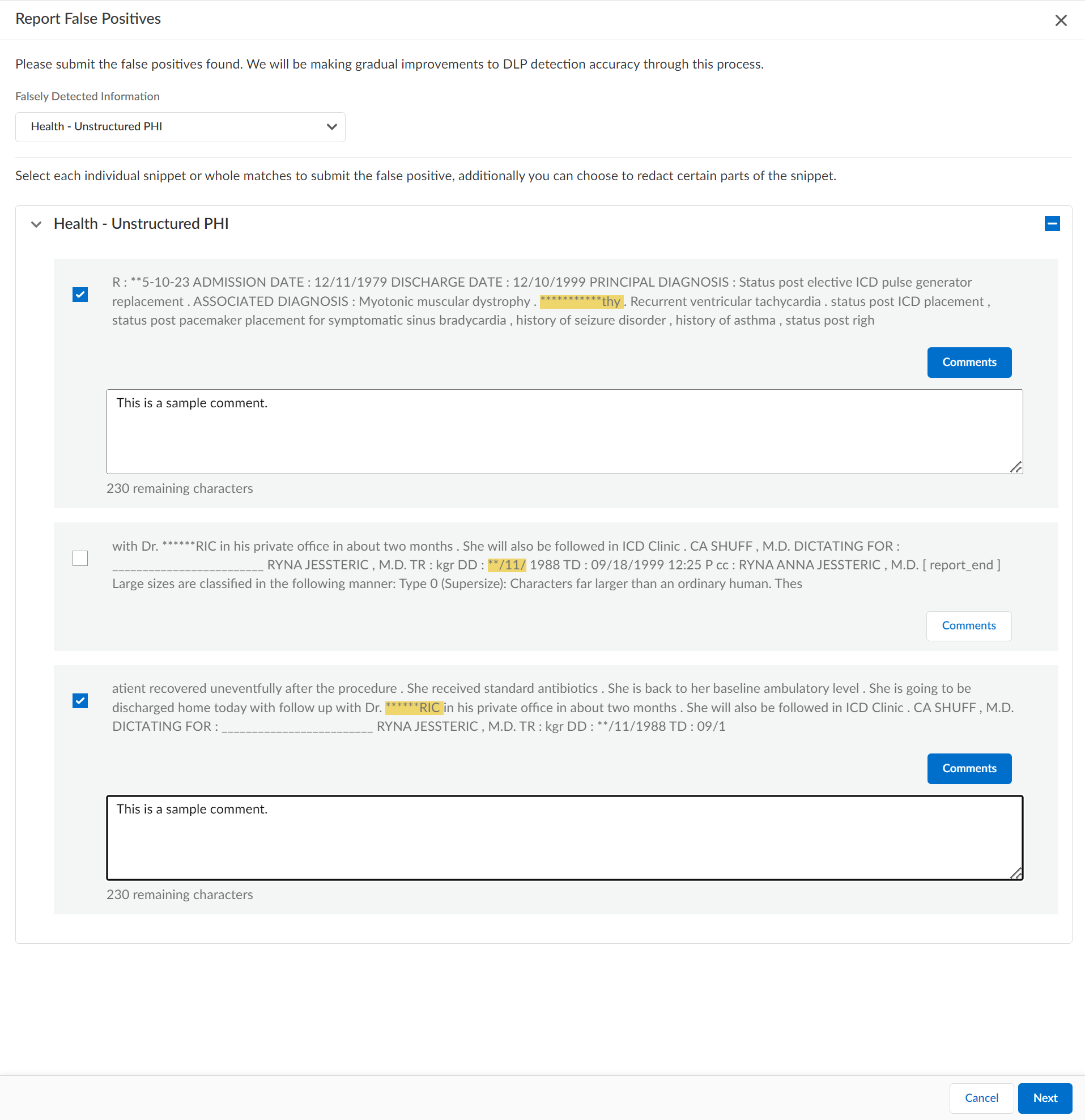
- In the Falsely Detection Information, select one or more data patterns.Enterprise DLP displays the list of available data patterns based on the data profile that generated a false positive detection. Enterprise DLP only displays data patterns associated with the data profile.
- Select one or more snippets of false positive detections.You can select snippets from multiple data patterns associated with the data profile if selected.
- (Optional) Add a Comment to provide additional details to Palo Alto Networks.This helps Palo Alto Networks understand how to improve the predefined data pattern match criteria or how to train the ML models to improve detection accuracy.Click Next.

- A notification displays to confirm submission of the false positive report and that the snippet will be shared with Palo Alto Networks for investigative purposes.Click Submit to report the false positive detection.