Enterprise DLP
Set Up a Proofpoint Server for Email Encryption
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Set Up a Proofpoint Server for Email Encryption
Set up a route to your Proofpoint server to encrypt emails inspected by Enterprise Data Loss Prevention (E-DLP) when using Email DLP.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Set up routing to your Proofpoint server to encrypt emails inspected by Enterprise Data Loss Prevention (E-DLP) that match your encryption Email DLP policy rule.
- Prepare your Proofpoint server to encrypt emails inspected by Enterprise DLP.
- Enable DKIM signing for your Proofpoint server.When enabling DKIM signing, you must also select Enabled for the domain.Additionally, keep a record of your DKIM public key. This is required when updating your domain host records.Contact your email domain provider to update your SPF record.
- Add your Proofpoint IP address to your SPF record.This is required to forward emails to Proofpoint for encryption. Skip this step if you have already updated your SPF record with your Proofpoint IP address.
- Add the DKIM public key to your domain host records.
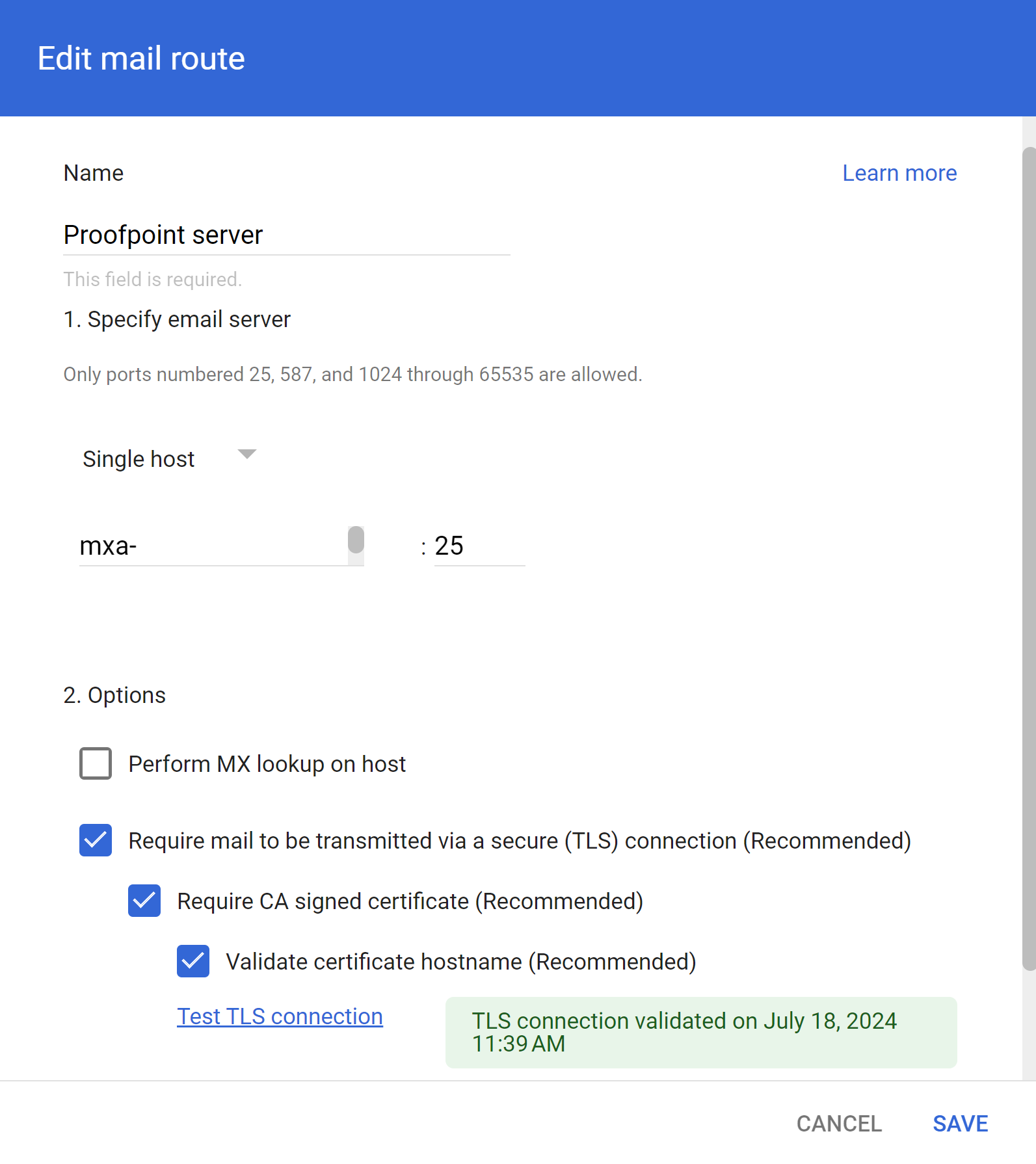
Log in to the Google Admin Console.In the Dashboard, select AppsGoogle WorkspaceGmailHosts and Add Route.Configure your Proofpoint server.- Enter a descriptive Name for the Proofpoint server route.In Specify email server, verify Single host is selected.Only a single host Proofpoint server is supported.Enter the hostname and port for the Proofpoint server.For the Options, verify the following settings are enabled.
- Require mail to be transmitted via a secure (TLS) connection
- Require CA signed certificate
- Validate certificate hostname
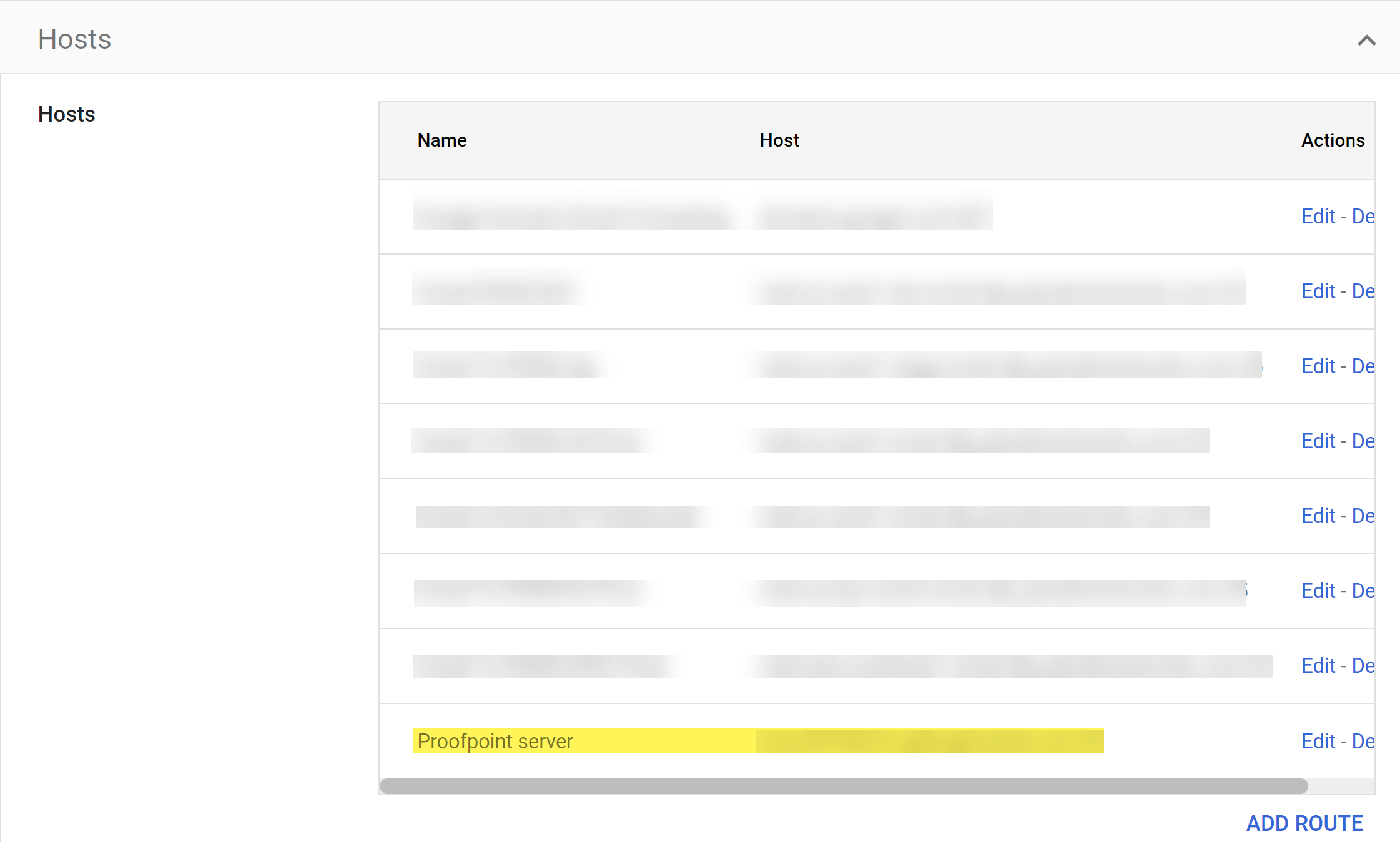
Test TLS connection to verify that your Proofpoint server can successfully connect to Enterprise DLP.Save.![]() Back in the Hosts page, verify that the Proofpoint server route is displayed.
Back in the Hosts page, verify that the Proofpoint server route is displayed.![]() Set Up the Email DLP Host.This is required to forward emails to Enterprise DLP for inspection and verdict rendering to prevent exfiltration of sensitive data. Skip this step if you already configured routing to Enterprise DLP.Create Gmail Transport Rules.After you successfully set up the Email DLP host on Gmail, you must create the Gmail transports rule to instruct Gmail to forward emails to Enterprise DLP and establish the actions Gmail takes based on verdicts rendered by Enterprise DLP.This is required to forward emails to Enterprise DLP for inspection and verdict rendering to prevent exfiltration of sensitive data. Skip this step if you already configured routing to Enterprise DLP.A transport rule isn't required for emails that match your Email DLP policy where the action is set to Monitor. In this case, Enterprise DLP adds x-panw-action - monitor to the email header, a DLP incident is created, and the email continues to its intended recipient.
Set Up the Email DLP Host.This is required to forward emails to Enterprise DLP for inspection and verdict rendering to prevent exfiltration of sensitive data. Skip this step if you already configured routing to Enterprise DLP.Create Gmail Transport Rules.After you successfully set up the Email DLP host on Gmail, you must create the Gmail transports rule to instruct Gmail to forward emails to Enterprise DLP and establish the actions Gmail takes based on verdicts rendered by Enterprise DLP.This is required to forward emails to Enterprise DLP for inspection and verdict rendering to prevent exfiltration of sensitive data. Skip this step if you already configured routing to Enterprise DLP.A transport rule isn't required for emails that match your Email DLP policy where the action is set to Monitor. In this case, Enterprise DLP adds x-panw-action - monitor to the email header, a DLP incident is created, and the email continues to its intended recipient.