Device Security
Lock Devices Through Jamf Pro
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Lock Devices Through Jamf Pro
Learn how to send commands to lock Jamf Pro managed or supervised devices
from the Device Security portal.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
When you integrate Device Security with Jamf Pro, you can send
commands to lock Jamf Pro managed or supervised devices through
Device Security in Strata Cloud Manager or through the
Device Security portal. You can choose to lock devices due to a security
alert raised on a device or due to a vulnerability detected on a device.
Locking devices requires having an
Owner or Administrator role
for Device Security.
You can lock a device from the following pages:
- Alerts Inventory
- Alert Details page
- Vulnerability Details page
- Device Details page, under the Alerts or Vulnerabilities sections
Because locking a device requires a MAC address to identify the device, you can
only lock one device at a time.
Strata Cloud Manager
Learn how to send commands to lock Jamf Pro managed or supervised devices
from Device Security in Strata Cloud Manager.
- Log in to Device Security in Strata Cloud Manager and select the device to lock.
- From the Device Details page:Navigate to AssetsInventory and select the device that you want to lock. On the Device Details page, click on either the Alerts or Vulnerabilities tab, select the alert or vulnerability of concern, and select ActionsSend to…Lock the device via Jamf Pro.
- From the Alert Details page:Navigate to AlertsSecurity Alerts and select the alert of concern. On the Alert Details page, select ActionsSend to…Lock the device via Jamf Pro.
- From the alerts inventory:Navigate to AlertsSecurity Alerts and select the check box for the alert of concern. After you have chosen the alert, select MoreSend to…Lock the device via Jamf Pro.
- From the Vulnerability Details page:Navigate to RisksVulnerabilities and select the vulnerability of concern. On the Vulnerability Details page, under Impact ViewActive Instances, select the check box for the vulnerability instance of concern. After you have chosen the instance, select MoreSend to…Lock the device via Jamf Pro.
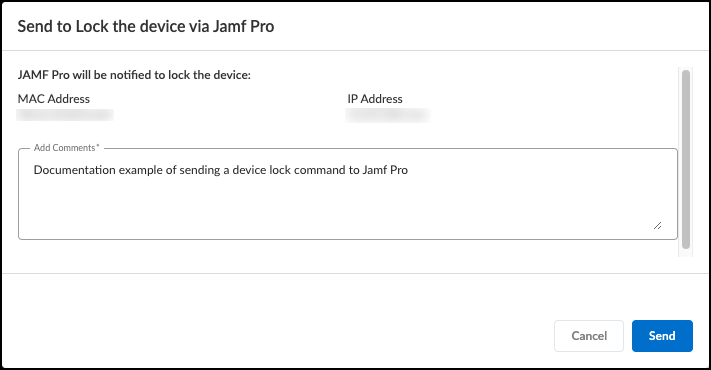
In the Lock the device via Jamf Pro pop-up that appears, verify that the MAC address and IP address are for the device that you want to lock, and then add a comment.![]() Click OK to send the lock command to Jamf Pro.After you click OK, a link to the Cortex XSOAR work plan appears at the bottom of the pop-up. The link opens a new tab or window to see the Cortex XSOAR work plan for this action.
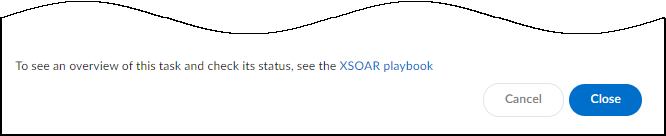
Click OK to send the lock command to Jamf Pro.After you click OK, a link to the Cortex XSOAR work plan appears at the bottom of the pop-up. The link opens a new tab or window to see the Cortex XSOAR work plan for this action.![]() To confirm that the lock command successfully reached Jamf Pro, click the link to the Cortex XSOAR work plan for this action.For the link in Device Security to open the corresponding work plan in Cortex XSOAR, you must already be logged in to your cloud Cortex XSOAR instance before clicking on the link.If you have an on-premises Cortex XSOAR, you need to search the incidents on your Cortex XSOAR to find the work plan.Follow the path through the work plan to see if the action completed successfully, or to triage where the action could have failed.
To confirm that the lock command successfully reached Jamf Pro, click the link to the Cortex XSOAR work plan for this action.For the link in Device Security to open the corresponding work plan in Cortex XSOAR, you must already be logged in to your cloud Cortex XSOAR instance before clicking on the link.If you have an on-premises Cortex XSOAR, you need to search the incidents on your Cortex XSOAR to find the work plan.Follow the path through the work plan to see if the action completed successfully, or to triage where the action could have failed.Legacy IoT Security
Learn how to send commands to lock Jamf Pro managed or supervised devices from the Device Security portal.- Log in to the Device Security portal and select the device to lock.
- From the Device Details page:Navigate to AssetsDevices and select the device that you want to lock. On the Device Details page, click on either the Alerts or Vulnerabilities tab, select the alert or vulnerability of concern, and select ActionsSend to…Lock the device via Jamf Pro.
- From the Alert Details page:Navigate to AlertsSecurity AlertsAll Alerts and select the alert of concern. On the Alert Details page, select ActionsSend to…Lock the device via Jamf Pro.
- From the alerts inventory:Navigate to AlertsSecurity AlertsAll Alerts and select the check box for the alert of concern. After you have chosen the alert, select MoreSend to…Lock the device via Jamf Pro.
- From the Vulnerability Details page:Navigate to VulnerabilitiesVulnerability OverviewAll Vulnerabilities and select the vulnerability of concern. On the Vulnerability Details page, under Impact ViewActive Instances, select the check box for the vulnerability instance of concern. After you have chosen the instance, select MoreSend to…Lock the device via Jamf Pro.
In the Lock the device via Jamf Pro pop-up that appears, verify that the MAC address and IP address are for the device that you want to lock, and then add a comment.![]() Click OK to send the lock command to Jamf Pro.After you click OK, a link to the Cortex XSOAR work plan appears at the bottom of the pop-up. The link opens a new tab or window to see the Cortex XSOAR work plan for this action.
Click OK to send the lock command to Jamf Pro.After you click OK, a link to the Cortex XSOAR work plan appears at the bottom of the pop-up. The link opens a new tab or window to see the Cortex XSOAR work plan for this action.![]() To confirm that the lock command successfully reached Jamf Pro, click the link to the Cortex XSOAR work plan for this action.For the link in Device Security to open the corresponding work plan in Cortex XSOAR, you must already be logged in to your cloud Cortex XSOAR instance before clicking on the link.If you have an on-premises Cortex XSOAR, you need to search the incidents on your Cortex XSOAR to find the work plan.Follow the path through the work plan to see if the action completed successfully, or to triage where the action could have failed.
To confirm that the lock command successfully reached Jamf Pro, click the link to the Cortex XSOAR work plan for this action.For the link in Device Security to open the corresponding work plan in Cortex XSOAR, you must already be logged in to your cloud Cortex XSOAR instance before clicking on the link.If you have an on-premises Cortex XSOAR, you need to search the incidents on your Cortex XSOAR to find the work plan.Follow the path through the work plan to see if the action completed successfully, or to triage where the action could have failed.