Use Case: PBF for Outbound Access with Dual ISPs
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
PAN-OS 10.2
- PAN-OS 11.1 & Later
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- Cloud Management of NGFWs
-
- Management Interfaces
-
- Launch the Web Interface
- Configure Banners, Message of the Day, and Logos
- Use the Administrator Login Activity Indicators to Detect Account Misuse
- Manage and Monitor Administrative Tasks
- Commit, Validate, and Preview Firewall Configuration Changes
- Commit Selective Configuration Changes
- Export Configuration Table Data
- Use Global Find to Search the Firewall or Panorama Management Server
- Manage Locks for Restricting Configuration Changes
-
-
- Define Access to the Web Interface Tabs
- Provide Granular Access to the Monitor Tab
- Provide Granular Access to the Policy Tab
- Provide Granular Access to the Objects Tab
- Provide Granular Access to the Network Tab
- Provide Granular Access to the Device Tab
- Define User Privacy Settings in the Admin Role Profile
- Restrict Administrator Access to Commit and Validate Functions
- Provide Granular Access to Global Settings
- Provide Granular Access to the Panorama Tab
- Provide Granular Access to Operations Settings
- Panorama Web Interface Access Privileges
-
- Reset the Firewall to Factory Default Settings
-
- Plan Your Authentication Deployment
- Pre-Logon for SAML Authentication
- Configure SAML Authentication
- Configure Kerberos Single Sign-On
- Configure Kerberos Server Authentication
- Configure TACACS+ Authentication
- Configure RADIUS Authentication
- Configure LDAP Authentication
- Configure Local Database Authentication
- Configure an Authentication Profile and Sequence
- Test Authentication Server Connectivity
- Troubleshoot Authentication Issues
-
- Keys and Certificates
- Default Trusted Certificate Authorities (CAs)
- Certificate Deployment
- Configure the Master Key
- Export a Certificate and Private Key
- Configure a Certificate Profile
- Configure an SSL/TLS Service Profile
- Configure an SSH Service Profile
- Replace the Certificate for Inbound Management Traffic
- Configure the Key Size for SSL Forward Proxy Server Certificates
-
- HA Overview
-
- Prerequisites for Active/Active HA
- Configure Active/Active HA
-
- Use Case: Configure Active/Active HA with Route-Based Redundancy
- Use Case: Configure Active/Active HA with Floating IP Addresses
- Use Case: Configure Active/Active HA with ARP Load-Sharing
- Use Case: Configure Active/Active HA with Floating IP Address Bound to Active-Primary Firewall
- Use Case: Configure Active/Active HA with Source DIPP NAT Using Floating IP Addresses
- Use Case: Configure Separate Source NAT IP Address Pools for Active/Active HA Firewalls
- Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT
- Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT in Layer 3
- HA Clustering Overview
- HA Clustering Best Practices and Provisioning
- Configure HA Clustering
- Refresh HA1 SSH Keys and Configure Key Options
- HA Firewall States
- Reference: HA Synchronization
-
- Use the Dashboard
- Monitor Applications and Threats
- Monitor Block List
-
- Report Types
- View Reports
- Configure the Expiration Period and Run Time for Reports
- Disable Predefined Reports
- Custom Reports
- Generate Custom Reports
- Generate the SaaS Application Usage Report
- Manage PDF Summary Reports
- Generate User/Group Activity Reports
- Manage Report Groups
- Schedule Reports for Email Delivery
- Manage Report Storage Capacity
- View Policy Rule Usage
- Use External Services for Monitoring
- Configure Log Forwarding
- Configure Email Alerts
-
- Configure Syslog Monitoring
-
- Traffic Log Fields
- Threat Log Fields
- URL Filtering Log Fields
- Data Filtering Log Fields
- HIP Match Log Fields
- GlobalProtect Log Fields
- IP-Tag Log Fields
- User-ID Log Fields
- Decryption Log Fields
- Tunnel Inspection Log Fields
- SCTP Log Fields
- Authentication Log Fields
- Config Log Fields
- System Log Fields
- Correlated Events Log Fields
- GTP Log Fields
- Audit Log Fields
- Syslog Severity
- Custom Log/Event Format
- Escape Sequences
- Forward Logs to an HTTP/S Destination
- Firewall Interface Identifiers in SNMP Managers and NetFlow Collectors
- Monitor Transceivers
-
- User-ID Overview
- Enable User-ID
- Map Users to Groups
- Enable User- and Group-Based Policy
- Enable Policy for Users with Multiple Accounts
- Verify the User-ID Configuration
-
- App-ID Overview
- App-ID and HTTP/2 Inspection
- Manage Custom or Unknown Applications
- Safely Enable Applications on Default Ports
- Applications with Implicit Support
-
- Prepare to Deploy App-ID Cloud Engine
- Enable or Disable the App-ID Cloud Engine
- App-ID Cloud Engine Processing and Policy Usage
- New App Viewer (Policy Optimizer)
- Add Apps to an Application Filter with Policy Optimizer
- Add Apps to an Application Group with Policy Optimizer
- Add Apps Directly to a Rule with Policy Optimizer
- Replace an RMA Firewall (ACE)
- Impact of License Expiration or Disabling ACE
- Commit Failure Due to Cloud Content Rollback
- Troubleshoot App-ID Cloud Engine
- Application Level Gateways
- Disable the SIP Application-level Gateway (ALG)
- Maintain Custom Timeouts for Data Center Applications
-
- Policy Types
- Policy Objects
- Track Rules Within a Rulebase
- Enforce Policy Rule Description, Tag, and Audit Comment
- Move or Clone a Policy Rule or Object to a Different Virtual System
-
- External Dynamic List
- Built-in External Dynamic Lists
- Configure the Firewall to Access an External Dynamic List
- Retrieve an External Dynamic List from the Web Server
- View External Dynamic List Entries
- Exclude Entries from an External Dynamic List
- Enforce Policy on an External Dynamic List
- Find External Dynamic Lists That Failed Authentication
- Disable Authentication for an External Dynamic List
- Register IP Addresses and Tags Dynamically
- Use Dynamic User Groups in Policy
- Use Auto-Tagging to Automate Security Actions
- CLI Commands for Dynamic IP Addresses and Tags
- Application Override Policy
- Test Policy Rules
-
- Network Segmentation Using Zones
- How Do Zones Protect the Network?
-
PAN-OS 11.1 & Later
- PAN-OS 11.1 & Later
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
-
- Tap Interfaces
-
- Layer 2 and Layer 3 Packets over a Virtual Wire
- Port Speeds of Virtual Wire Interfaces
- LLDP over a Virtual Wire
- Aggregated Interfaces for a Virtual Wire
- Virtual Wire Support of High Availability
- Zone Protection for a Virtual Wire Interface
- VLAN-Tagged Traffic
- Virtual Wire Subinterfaces
- Configure Virtual Wires
- Configure a PPPoE Client on a Subinterface
- Configure an IPv6 PPPoE Client
- Configure an Aggregate Interface Group
- Configure Bonjour Reflector for Network Segmentation
- Use Interface Management Profiles to Restrict Access
-
- DHCP Overview
- Firewall as a DHCP Server and Client
- Firewall as a DHCPv6 Client
- DHCP Messages
- Dynamic IPv6 Addressing on the Management Interface
- Configure an Interface as a DHCP Server
- Configure an Interface as a DHCPv4 Client
- Configure an Interface as a DHCPv6 Client with Prefix Delegation
- Configure the Management Interface as a DHCP Client
- Configure the Management Interface for Dynamic IPv6 Address Assignment
- Configure an Interface as a DHCP Relay Agent
-
- DNS Overview
- DNS Proxy Object
- DNS Server Profile
- Multi-Tenant DNS Deployments
- Configure a DNS Proxy Object
- Configure a DNS Server Profile
- Use Case 1: Firewall Requires DNS Resolution
- Use Case 2: ISP Tenant Uses DNS Proxy to Handle DNS Resolution for Security Policies, Reporting, and Services within its Virtual System
- Use Case 3: Firewall Acts as DNS Proxy Between Client and Server
- DNS Proxy Rule and FQDN Matching
-
- NAT Rule Capacities
- Dynamic IP and Port NAT Oversubscription
- Dataplane NAT Memory Statistics
-
- Translate Internal Client IP Addresses to Your Public IP Address (Source DIPP NAT)
- Create a Source NAT Rule with Persistent DIPP
- PAN-OS
- Strata Cloud Manager
- Enable Clients on the Internal Network to Access your Public Servers (Destination U-Turn NAT)
- Enable Bi-Directional Address Translation for Your Public-Facing Servers (Static Source NAT)
- Configure Destination NAT with DNS Rewrite
- Configure Destination NAT Using Dynamic IP Addresses
- Modify the Oversubscription Rate for DIPP NAT
- Reserve Dynamic IP NAT Addresses
- Disable NAT for a Specific Host or Interface
-
- Network Packet Broker Overview
- How Network Packet Broker Works
- Prepare to Deploy Network Packet Broker
- Configure Transparent Bridge Security Chains
- Configure Routed Layer 3 Security Chains
- Network Packet Broker HA Support
- User Interface Changes for Network Packet Broker
- Limitations of Network Packet Broker
- Troubleshoot Network Packet Broker
-
- Enable Advanced Routing
- Logical Router Overview
- Configure a Logical Router
- Create a Static Route
- Configure BGP on an Advanced Routing Engine
- Create BGP Routing Profiles
- Create Filters for the Advanced Routing Engine
- Configure OSPFv2 on an Advanced Routing Engine
- Create OSPF Routing Profiles
- Configure OSPFv3 on an Advanced Routing Engine
- Create OSPFv3 Routing Profiles
- Configure RIPv2 on an Advanced Routing Engine
- Create RIPv2 Routing Profiles
- Create BFD Profiles
- Configure IPv4 Multicast
- Configure MSDP
- Create Multicast Routing Profiles
- Create an IPv4 MRoute
-
-
PAN-OS 11.2
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
- Cloud Management and AIOps for NGFW
Use Case: PBF for Outbound Access with Dual ISPs
In this use case, the branch office has a
dual ISP configuration and implements PBF for redundant internet
access. The backup ISP is the default route for traffic from the
client to the web servers. In order to enable redundant internet
access without using an internetwork protocol such as BGP, we use
PBF with destination interface-based source NAT and static routes,
and configure the firewall as follows:
- Enable a PBF rule that routes traffic through the primary ISP, and attach a monitoring profile to the rule. The monitoring profile triggers the firewall to use the default route through the backup ISP when the primary ISP is unavailable.
- Define Source NAT rules for both the primary and backup ISP that instruct the firewall to use the source IP address associated with the egress interface for the corresponding ISP. This ensures that the outbound traffic has the correct source IP address.
- Add a static route to the backup ISP, so that when the primary ISP is unavailable, the default route comes into effect and the traffic is directed through the backup ISP.
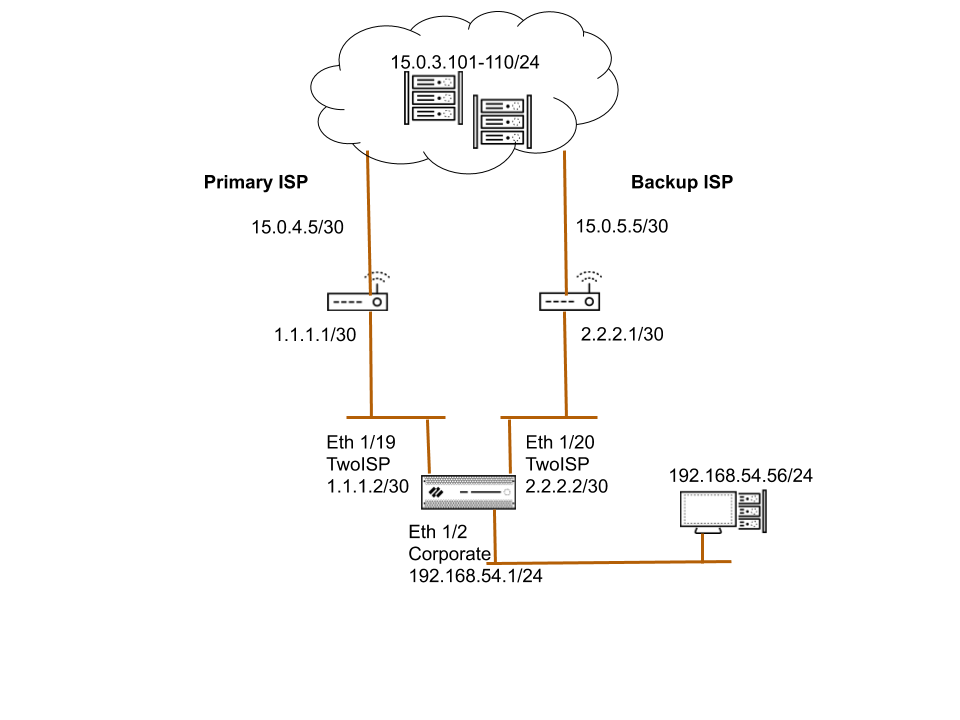
- Configure the ingress and the egress interfaces on the firewall.Egress interfaces can be in the same zone.
- Select NetworkInterfaces and select the interface you want to configure.The interface configuration on the firewall used in this example is as follows:
- Ethernet 1/19 connected to the primary ISP:
- Zone: TwoISP
- IP Address: 1.1.1.2/30
- Virtual Router: Default
- Ethernet 1/20 connected to the backup ISP:
- Zone: TwoISP
- IP Address: 2.2.2.2/30
- Virtual Router: Default
- Ethernet 1/2 is the ingress interface, used by the network clients to connect to the internet:
- Zone: Corporate
- IP Address: 192.168. 54.1/24
- Virtual Router: Default
- To save the interface configuration, click OK.
- On the virtual router, add a static route to the backup ISP.
- Select NetworkVirtual Router and select the default link to open the Virtual Router dialog.
- Select Static Routes and click Add. Enter a Name for the route and specify the Destination IP address for which you are defining the static route. In this example, we use 0.0.0.0/0 for all traffic.
- Select the IP Address radio button and set the Next Hop IP address for your router that connects to the backup internet gateway (you cannot use a domain name for the next hop). In this example, 2.2.2.1.
- Specify a cost metric for the route.

- Click OK twice to save the virtual router configuration.
- Create a PBF rule that directs traffic to the interface that is connected to the primary ISP.Make sure to exclude traffic destined to internal servers/IP addresses from PBF. Define a negate rule so that traffic destined to internal IP addresses is not routed through the egress interface defined in the PBF rule.
- Select PoliciesPolicy Based Forwarding and click Add.
- Give the rule a descriptive Name in the General tab.
- In the Source tab, set the Source Zone; in this example, the zone is Corporate.
- In the Destination/Application/Service tab, set the following:
- In the Destination Address section, Add the IP addresses or address range for servers on the internal network or create an address object for your internal servers. Select Negate to exclude the IP addresses or address object listed above from using this rule.
- In the Service section, Add the service-http and service-https services to allow HTTP and HTTPS traffic to use the default ports. For all other traffic that is allowed by security policy, the default route will be used.To forward all traffic using PBF, set the Service to Any.
- Specify where to forward traffic.
- In the Forwarding tab, specify the interface to which you want to forward traffic and enable path monitoring.
- To forward traffic, set the Action to Forward, and select the Egress Interface and specify the Next Hop. In this example, the egress interface is ethernet1/19, and the next hop IP address is 1.1.1.1 (you cannot use a FQDN for the next hop).
- Enable Monitor, attach the default monitoring profile and select Disable this rule if nexthop/monitor ip is unreachable to trigger a failover to the backup ISP. In this example, we do not specify a target IP address to monitor. The firewall will monitor the next hop IP address; if this IP address is unreachable, the firewall will direct traffic to the default route specified on the virtual router.
- (Required if you have asymmetric routes) Select Enforce Symmetric Return to ensure that return traffic from the Corporate zone to the internet is forwarded out on the same interface through which traffic ingressed from the internet.
- NAT ensures that the traffic from the internet is returned to the correct interface/IP address on the firewall.
- Click OK to save the changes.

- Create NAT rules based on the egress interface and ISP. These rules ensure that the correct source IP address is used for outbound connections.
- Select PoliciesNAT and click Add.
- In this example, the NAT rule we create for each ISP is as follows:NAT for Primary ISPIn the Original Packet tab,Source Zone: CorporateDestination Zone: TwoISPDestination Interface: ethernet1/19In the Translated Packet tab, under Source Address TranslationTranslation Type: Dynamic IP and PortAddress Type: Interface AddressInterface: ethernet1/19IP Address: 1.1.1.2/30NAT for Backup ISPIn the Original Packet tab,Source Zone: CorporateDestination Zone: TwoISPDestination Interface: ethernet1/20In the Translated Packet tab, under Source Address TranslationTranslation Type: Dynamic IP and PortAddress Type: Interface AddressInterface: ethernet1/20IP Address: 2.2.2.2/30

- Create security policy to allow outbound access to the internet.To safely enable applications, create a simple rule that allows access to the internet and attach the security profiles available on the firewall.
- Select PoliciesSecurity and click Add.
- Give the rule a descriptive Name in the General tab.
- In the Source tab, set the Source Zone to Corporate.
- In the Destination tab, Set the Destination Zone to TwoISP.
- In the Service/ URL Category tab, leave the default application-default.
- In the Actions tab, complete these tasks:
- Set the Action Setting to Allow.
- Attach the default profiles for Antivirus, Anti-Spyware, Vulnerability Protection and URL Filtering, under Profile Setting.
- Under Options, verify that logging is enabled at the end of a session. Only traffic that matches a security rule is logged.
- Save the policies to the running configuration on the firewall.Click Commit.
- Verify that the PBF rule is active and that the primary ISP is used for internet access.
- Launch a web browser and access a web server. On the firewall, check the traffic log for web-browsing activity.
- From a client on the network, use the ping utility to verify connectivity to a web server on the internet, and check the traffic log on the firewall.
C:\Users\pm-user1>ping 198.51.100.6 Pinging 198.51.100.6 with 32 bytes of data: Reply from 198.51.100.6: bytes=32 time=34ms TTL=117 Reply from 198.51.100.6: bytes=32 time=13ms TTL=117 Reply from 198.51.100.6: bytes=32 time=25ms TTL=117 Reply from 198.51.100.6: bytes=32 time=3ms TTL=117 Ping statistics for 198.51.100.6: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milliseconds: Minimum = 3ms, Maximum = 34ms, Average = 18ms - To confirm that the PBF rule is active, use the following CLI command:
admin@PA-NGFW> show pbf rule all Rule ID Rule State Action Egress IF/VSYS NextHop NextHop Status ========== === ========== ====== =================== ============== ================= PBF - Prim 1 Active Forward ethernet1/19 1.1.1.1 UP - Verify that the failover to the backup ISP occurs and that the Source NAT is correctly applied.
- Unplug the connection to the primary ISP.
- Confirm that the PBF rule is inactive with the following CLI command:
admin@PA-NGFW> show pbf rule all Rule ID Rule State Action Egress IF/VSYS NextHop NextHop Status ========== === ========== ====== ============== ============== =============== PBF - Prim 1 Disabled Forward ethernet1/19 1.1.1.1 DOWN - Access a web server, and check the traffic log to verify that traffic is being forwarded through the backup ISP.
- View the session details to confirm that the NAT rule is working properly.
admin@PA-NGFW> show session all --------------------------------------------------------- ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port]) Vsys Dst[Dport]/Zone (translated IP[Port]) --------------------------------------------------------- 87212 ssl ACTIVE FLOW NS 192.168.54.56[53236]/Corporate/6 (2.2.2.2[12896]) vsys1 204.79.197.200[443]/TwoISP (204.79.197.200[443]) - Obtain the session identification number from the output and view the session details.The PBF rule is not used and hence is not listed in the output.
admin@PA-NGFW> show session id 87212 Session 87212 c2s flow: source: 192.168.54.56 [Corporate] dst: 204.79.197.200 proto: 6 sport: 53236 dport: 443 state: ACTIVE type: FLOW src user: unknown dst user: unknown s2c flow: source: 204.79.197.200 [TwoISP] dst: 2.2.2.2 proto: 6 sport: 443 dport: 12896 state: ACTIVE type: FLOW src user: unknown dst user: unknown start time : Wed Nov5 11:16:10 2014 timeout : 1800 sec time to live : 1757 sec total byte count(c2s) : 1918 total byte count(s2c) : 4333 layer7 packet count(c2s) : 10 layer7 packet count(s2c) : 7 vsys : vsys1 application : ssl rule : Corp2ISP session to be logged at end : True session in session ager : True session synced from HA peer : False address/port translation : source nat-rule : NAT-Backup ISP(vsys1) layer7 processing : enabled URL filtering enabled : True URL category : search-engines session via syn-cookies : False session terminated on host : False session traverses tunnel : False authentication portal session : False ingress interface : ethernet1/2 egress interface : ethernet1/20 session QoS rule : N/A (class 4)



