Enterprise DLP
Create a Nested Data Profile
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Create a Nested Data Profile
Create a single Enterprise Data Loss Prevention (E-DLP) data profile containing multiple data
profiles to simplify management of sensitive data leaving your network.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Enterprise DLP license
|
Enterprise Data Loss Prevention (E-DLP) supports creating a single data profile that contains
multiple nested data profiles. Creating a
single data profile that contains multiple nested data profiles enables you to
consolidate the match criteria to prevent exfiltration of sensitive data to a single
data profile that you can associate with a single Security policy rule. This enables
your data security administrators to simplify the management of sensitive data
leaving your network and reduces the need to manage multiple Security policy rules
and data profiles. Enterprise DLP synchronizes nested data profiles between Panorama and Strata Cloud Manager
When you create a data profile that contains predefined data profiles and patterns,
be sure to consider the detection types used by the predefined
data patterns because the detection type determines how Enterprise DLP arrives
at a verdict for scanned files.
(Prisma Browser) On Strata Cloud Manager, you can
configure a data profile for Local Detection if you have an
Prisma Browser license. A data profile configured for Local
Detection means that inspection of sensitive data against the
traffic match criteria occurs locally on Prisma Browser rather than being sent
to the Enterprise DLP cloud detection engine.
- Enterprise DLP does not support adding a nested data profile to another nested data profile.
- Enterprise DLP supports adding a data profiles that have only a Primary Rule configured. Enterprise DLP does not support adding data profiles that include both Primary and Secondary Rules to a nested data profile.
- Enterprise DLP supports adding a data profile that includes an advanced detection method to an existing nested data profile if you did not include one when you originally created the data profile.
- (SaaS Security) Enterprise DLP supports adding a nested data profile to SaaS Security Inline policy recommendations and Internet Access policy rules only.Enterprise DLP does not support adding a nested data profile to data asset policy rules in Data Security.
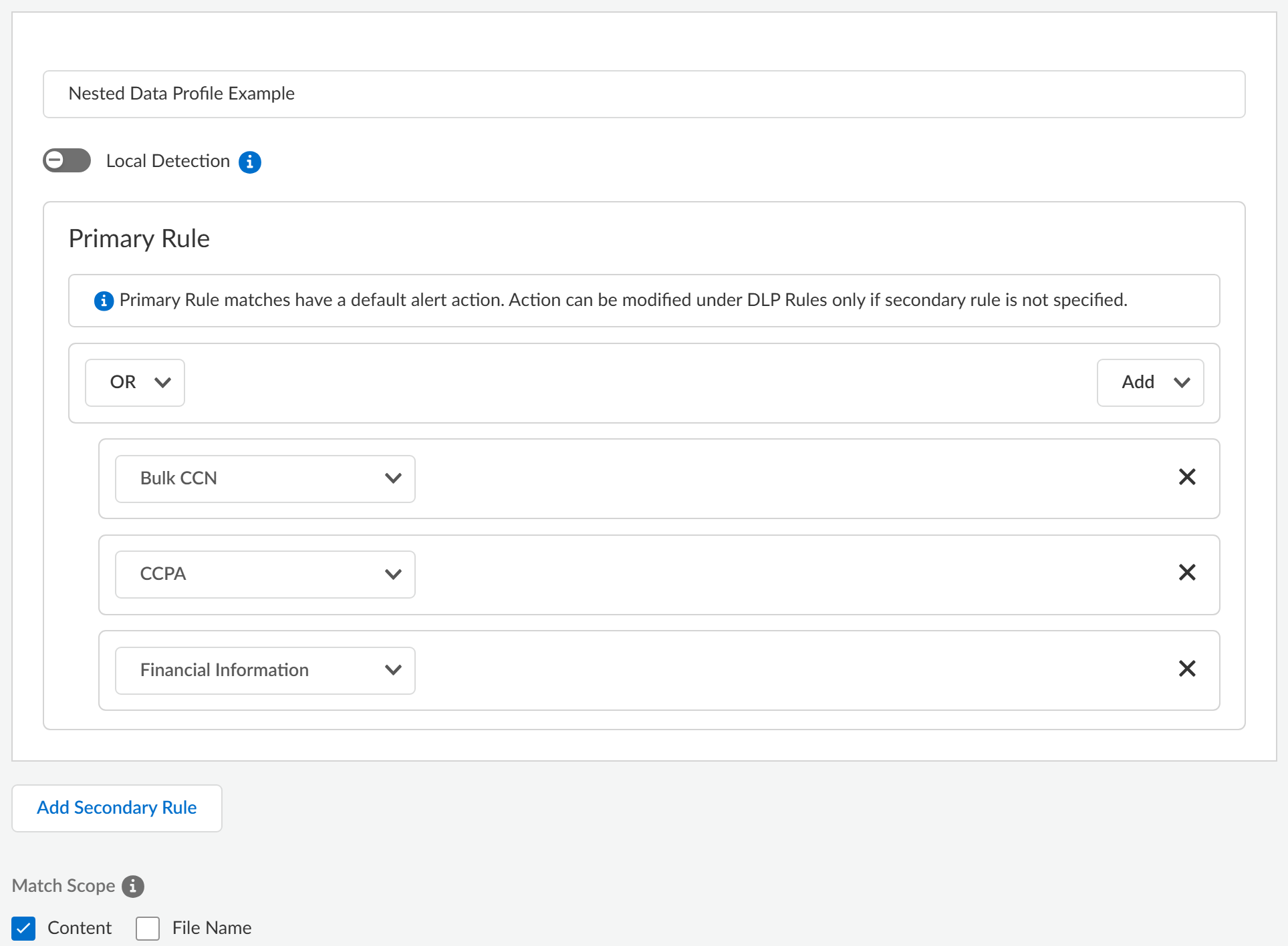
- Log in to Strata Cloud Manager.Select ConfigurationData Loss PreventionData Profiles and Add Data ProfilesCustom Data Profile.You can also create a new data profile by copying an existing data profile that already contains multiple data profiles. This allows you to quickly modify an existing data profile with additional data profile match criteria while preserving the original data profile from which the new data profile was copied.Enterprise DLP appends the name of copied a data profile with Copy - <name_of_original_data_profile>.Enter the Data Profile Name.Configure the Primary Rule for the data profile.Select AddAdd Data Profile to add predefined or custom data profiles. Repeat this step to include additional data profiles.Add the data profile match criteria for allowed traffic to the Primary Rule. Add data profiles for blocked traffic to either Primary Rule or Secondary Rule. Nested data profiles support AND or OR operators.(Optional) Configure a Secondary Rule.Add Data Profile to add predefined or custom data profiles. Repeat this step to include additional data profiles.Data profile match criteria added to the Secondary Rule block all traffic that meets the match criteria for the data profile by default and can’t be modified. If you want to allow traffic that matches a data profile match criteria, add it to the Primary Rule.A data profile containing multiple data profiles support any combination of data profiles with data patterns only, data patterns and EDM data sets, and EDM data sets only.(Prisma Browser) Prisma Browser doesn't support Secondary Rules for both cloud-assisted and local detection data profiles. Prisma Browser ignores all Secondary Rules.Nested data profiles support only the OR operator.Click Test Run to test and verify the data profile accurately detects the sensitive data you configured it to detect.Review the nested data profile configuration.
![]() Additionally, you can use the Preview to see a detailed list view of your Primary and Secondary Rule configuration, the Detection Coverage indicating whether the data profile supports Cloud Only or Local Detection.
Additionally, you can use the Preview to see a detailed list view of your Primary and Secondary Rule configuration, the Detection Coverage indicating whether the data profile supports Cloud Only or Local Detection.- Example of Local Detection Support
- Example of No Local Detection SupportClick Convert to Local Detection Compatible Profile to remove any cloud-assisted data profiles and make the data profile compatible with local detection for Prisma Browser.
Verify that the data profile you created.- Strata Cloud Manager—Log in to Strata Cloud Manager and select ConfigurationData Loss PreventionData Profiles and search for the data profile you created.
- PanoramaSee Update a Data Profile for more information on which data profile settings are editable on Panorama for a data profile created on Strata Cloud Manager.If the data profile has both Primary and Secondary Patterns, changing the data profile Action on Panorama deletes all Secondary Pattern match criteria.
- Select the data profile created on Strata Cloud Manager.
- Set the data profile Action to Block traffic that matches the data profile match criteria.
- Select CommitCommit to Panorama and Commit.
- Click OK.
- Select CommitPush to Devices and Edit Selections.
- Select Device Groups and Include Device and Network Templates.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.
Save the data profile.Modify the DLP rule or add the data profile to a Data Control Rule- NGFW and Prisma Access Tenants—Modify a DLP rule to define the type of traffic to inspect, the impacted file types and apps, the action Enterprise DLP takes when sensitive data is detected, log severity, and more for the data profile match criteria. Enterprise DLP automatically creates a DLP rule with an identical name as the data profile from which it was created.
- Prisma Browser—Create or edit a Data Control rule to prevent exfiltration of sensitive data for specific apps, website classifications, or URLs.