Enterprise DLP
Edit the Enterprise DLP Data Filtering Settings
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
-
- About Enterprise DLP
- What’s Supported with Enterprise DLP?
- Data Patterns, Document Types, and Data Profiles
- Enable Role Based Access
- Edit the Cloud Content Settings
- Edit the Enterprise DLP Data Filtering Settings
- Edit the Enterprise DLP Snippet Settings
- Configure Syslog Forwarding for Enterprise DLP Incidents
- Request a New Feature
-
-
- Enable Existing Data Patterns and Filtering Profiles
- Modify a DLP Rule on Strata Cloud Manager
- Create a SaaS Security Policy Recommendation to Leverage Enterprise DLP
- Reduce False Positive Detections
- Data Dictionaries
- Recommendations for Security Policy Rules
- Enterprise DLP Migrator
-
-
-
- Driver License - Australia
- Driver License - Austria
- Driver License - Belgium
- Driver License - Brazil
- Driver License - Bulgaria
- Driver License - Canada
- Driver License - China
- Driver License - Croatia
- Driver License - Cyprus
- Driver License - Czech Republic
- Driver License - Denmark
- Driver License - Estonia
- Driver License - Finland
- Driver License - France
- Driver License - Germany
- Driver License - Greece
- Driver License - Hungary
- Driver License - Iceland
- Driver License - Ireland
- Driver License - Italy
- Driver License - Japan
- Driver License - Latvia
- Driver License - Liechtenstein
- Driver License - Lithuania
- Driver License - Luxembourg
- Driver License - Malta
- Driver License - Netherlands
- Driver License - New Zealand
- Driver License - Norway
- Driver License - Poland
- Driver License - Portugal
- Driver License - Romania
- Driver License - Slovakia
- Driver License - Slovenia
- Driver License - South Africa
- Driver License - South Korea
- Driver License - Spain
- Driver License - Sweden
- Driver License - Switzerland
- Driver License - Taiwan
- Driver License - Turkey
- Driver License - UK
- Driver License - US
- Driver License - US - AK
- Driver License - US - AL
- Driver License - US - AR
- Driver License - US - AZ
- Driver License - US - CA
- Driver License - US - CO
- Driver License - US - CT
- Driver License - US - DC
- Driver License - US - DE
- Driver License - US - FL
- Driver License - US - GA
- Driver License - US - HI
- Driver License - US - IA
- Driver License - US - ID
- Driver License - US - IL
- Driver License - US - IN
- Driver License - US - KS
- Driver License - US - KY
- Driver License - US - LA
- Driver License - US - MA
- Driver License - US - ME
- Driver License - US - MI
- Driver License - US - MN
- Driver License - US - MO
- Driver License - US - MS
- Driver License - US - MT
- Driver License - US - NC
- Driver License - US - ND
- Driver License - US - NE
- Driver License - US - NH
- Driver License - US - NM
- Driver License - US - NV
- Driver License - US - NY
- Driver License - US - OH
- Driver License - US - OK
- Driver License - US - OR
- Driver License - US - PA
- Driver License - US - RI
- Driver License - US - SC
- Driver License - US - SD
- Driver License - US - TN
- Driver License - US - TX
- Driver License - US - UT
- Driver License - US - VA
- Driver License - US - VT
- Driver License - US - WA
- Driver License - US - WI
- Driver License - US - WV
- Driver License - US - WY
- National ID - Albania
- National Id - Argentina ID
- National ID - Australia
- National Id - Austria - Central Register of Residents
- National Id - Austria Social Security Card - e-card
- National ID - Bahrain
- National Id - Belgium - Citizen Service Number - BSN
- National Id - Belgium - National Registration Number
- National ID - Bosnia and Herzegovina
- National ID - Brazil
- National Id - Brazil - CNPJ
- National Id - Brazil - CPF
- National Id - Bulgaria - Uniform Civil Number
- National Id - Canada - Social Insurance Number - SIN
- National ID - Chile
- National Id - China ID
- National Id - Colombia National ID
- National ID - Costa Rica
- National Id - Croatia - Personal Identification Number
- National ID - Cuba
- National Id - Cyprus - Identity Card
- National Id - Czech - Birth Number
- National Id - Czech - National eID Card
- National Id - Denmark - CPR Number
- National ID - Dominican Republic
- National ID - Ecuador
- National ID - Egypt
- National Id - Estonia - Personal Identification Code
- National Id - Finland - Personal Identity Code - HETU
- National Id - France - INSEE
- National Id - France - Social Security Number - NIR
- National Id - Germany
- National Id - Greece
- National Id - Hong Kong ID
- National Id - Hungary - Personal Identification Number
- National Id - Iceland
- National ID - India
- National ID - Indonesia
- National ID - Iran
- National Id - Ireland - Personal Public Service Number - PPSN
- National ID - Israel
- National Id - Italy - Fiscal Code Card - Codice Fiscale
- National Id - Japan Corporate Number
- National Id - Japan My Number
- National ID - Kazakhstan
- National ID - Kuwait
- National Id - Latvia - Personal Public Service Number - PPSN
- National Id - Liechtenstein
- National Id - Lithuania
- National Id - Luxembourg
- National Id - Malaysia National ID
- National Id - Malta
- National ID - Mexico
- National ID - Moldova
- National ID - Montenegro
- National Id - Netherlands - Citizen Service Number - BSN
- National ID - North Macedonia
- National Id - Norway - Identification Number - Fødselsnummer
- National ID - Pakistan
- National ID - Paraguay
- National ID - Peru
- National ID - Philippines
- National Id - Poland
- National Id - Portugal
- National Id - Romania - Identity Card - CNP
- National ID - Russia
- National ID - Serbia
- National Id - Singapore NRIC
- National Id - Slovakia
- National Id - Slovenia
- National ID - South Africa
- National ID - South Korea
- National Id - Spain - National Identity Document - Documento Nacional de Identidad
- National ID - Sri Lanka
- National Id - Sweden - Personal Identity Number
- National ID - Switzerland
- National Id - Taiwan ID
- National Id - Thailand ID
- National Id - Turkey Identification Number
- National Id - UAE Emirates ID
- National Id - UK National Insurance Number - NINO
- National ID - Uruguay
- National Id - US Social Security Number - SSN
- National ID - Venezuela
- Passport - Australia
- Passport - Austria
- Passport - Belgium
- Passport - Brazil
- Passport - Bulgaria
- Passport - Canada
- Passport - Croatia
- Passport - Cyprus
- Passport - Czech Republic
- Passport - Denmark
- Passport - Estonia
- Passport - Finland
- Passport - France
- Passport - Germany
- Passport - Greece
- Passport - Hungary
- Passport - Iceland
- Passport - Ireland
- Passport - Italy
- Passport - Latvia
- Passport - Liechtenstein
- Passport - Lithuania
- Passport - Luxembourg
- Passport - Malta
- Passport - Netherlands
- Passport - New Zealand
- Passport - Norway
- Passport Number - China
- Passport Number - Singapore
- Passport Number - South Africa
- Passport number - South Korea
- Passport number - Taiwan
- Passport - Poland
- Passport - Portugal
- Passport - Romania
- Passport - Slovakia
- Passport - Slovenia
- Passport - Spain
- Passport - Sweden
- Passport - Switzerland
- Passport - Turkey
- Passport - UK
- Passport - US
- Tax Id - Australia
- Tax Id - Austria
- Tax Id - Belgium
- Tax Id - Brazil
- Tax Id - Bulgaria
- Tax ID - Canada
- Tax ID - China
- Tax ID - Costa Rica
- Tax Id - Cyprus
- Tax Id - Czech Republic
- Tax Id - Denmark
- Tax ID - Dominican Republic
- Tax Id - Estonia
- Tax Id - Finland
- Tax Id - France
- Tax Id - Germany
- Tax Id - Greece
- Tax Id - Hungary
- Tax Id - Iceland
- Tax Id - India - PAN
- Tax Id - Ireland
- Tax Id - Italy
- Tax ID - Japan
- Tax Id - Latvia
- Tax Id - Liechtenstein
- Tax Id - Lithuania
- Tax Id - Luxembourg
- Tax Id - Malta
- Tax Id - Netherlands
- Tax Id - New Zealand
- Tax Id - Norway
- Tax Id - Poland
- Tax Id - Portugal
- Tax Id - Romania
- Tax Id - Slovakia
- Tax Id - Slovenia
- Tax ID - South Africa
- Tax ID - South Korea
- Tax Id - Spain
- Tax Id - Sweden
- Tax Id - Switzerland
- Tax ID - Taiwan
- Tax Id - Turkey
- Tax Id - UK - UTR
- Tax Id - US - TIN
-
-
-
-
- March 2025
- February 2025
- January 2025
- December 2024
- November 2024
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- April 2024
- March 2024
- January 2024
- December 2023
- November 2023
- October 2023
- August 2023
- July 2023
- June 2023
- May 2023
- March 2023
- February 2023
- January 2023
- November 2022
- October 2022
- August 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- July 2021
- New Features in Enterprise DLP Plugin 5.0
- New Features in Enterprise DLP Plugin 4.0
- New Features in Enterprise DLP Plugin 3.0
- New Features in Enterprise DLP Plugin 1.0
-
- Known Issues in the Enterprise DLP Cloud Service
- Known Issues in Endpoint DLP
-
- Known Issues in Enterprise DLP Plugin 5.0.6
- Known Issues in Enterprise DLP Plugin 5.0.5
- Known Issues in Enterprise DLP Plugin 5.0.4
- Known Issues in Enterprise DLP Plugin 5.0.3
- Known Issues in Enterprise DLP Plugin 5.0.2
- Known Issues in Enterprise DLP Plugin 5.0.1
- Known Issues in Enterprise DLP Plugin 5.0.0
-
- Known Issues in Enterprise DLP Plugin 3.0.10
- Known Issues in Enterprise DLP Plugin 3.0.9
- Known Issues in Enterprise DLP Plugin 3.0.8
- Known Issues in Enterprise DLP Plugin 3.0.7
- Known Issues in Enterprise DLP Plugin 3.0.6
- Known Issues in Enterprise DLP Plugin 3.0.5
- Known Issues in Enterprise DLP Plugin 3.0.4
- Known Issues in Enterprise DLP Plugin 3.0.3
- Known Issues in Enterprise DLP Plugin 3.0.2
- Known Issues in Enterprise DLP Plugin 3.0.1
- Known Issues in Enterprise DLP Plugin 3.0.0
-
- Known Issues in Enterprise DLP Plugin 1.0.8
- Known Issues in Enterprise DLP Plugin 1.0.7
- Known Issues in Enterprise DLP Plugin 1.0.6
- Known Issues in Enterprise DLP Plugin 1.0.5
- Known Issues in Enterprise DLP Plugin 1.0.4
- Known Issues in Enterprise DLP Plugin 1.0.3
- Known Issues in Enterprise DLP Plugin 1.0.2
- Known Issues in Enterprise DLP Plugin 1.0.1
- Enterprise DLP Limitations
- Changes to Default Behavior
-
Edit the Enterprise DLP Data Filtering Settings
Edit the Enterprise Data Loss Prevention (E-DLP) data filtering settings to specify the actions the
firewall using Enterprise DLP takes if the data filtering settings are
exceeded.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Enterprise DLP license
|
Edit and apply Enterprise Data Loss Prevention (E-DLP) data filtering settings. These network
settings are determine the networking and file size parameters for files scanned by
the DLP cloud service and specify the actions Enterprise DLP takes when these
parameters are exceeded.
(NGFW and Prisma Access managed by Panorama)
If you want to enable non-file inspection for your NGFW and Prisma Access tenants you must enable the setting from Panorama.
For NGFW and Prisma Access managed by Panorama,
enabling non-file inspection from Strata Cloud Manager is not supported and
causes Panorama commits to fail.
Edit the Enterprise DLP Data Filtering Settings on Strata Cloud Manager
Edit the Enterprise Data Loss Prevention (E-DLP) data filtering settings for Prisma Access (Managed by Strata Cloud Manager) and NGFW (Managed by Strata Cloud Manager).
- Log in to Strata Cloud Manager.
- Select ManageConfigurationData Loss PreventionSettingsData Transfer and edit the Data Transfer settings.
- Edit the File Based Settings.
- Specify the File Movement Max Latency (sec) for a file forward before an action is taken by Enterprise DLP.For inspection of files greater than 20 MB, Palo Alto Networks recommends setting the max latency to greater than 60 seconds.
- Specify the Action When Max Latency is Reached (Allow or Block) Enterprise DLP takes if no verdict was received for a file forward due to the file forward time exceeding the configured Max Latency.Selecting Block applies only to DLP rules configured to block files. This setting does not impact Enterprise DLP data profiles configured to alert when traffic containing sensitive data is scanned.
- Specify the Scan Limit Max File Size for Alert (MB) to enforce the maximum file size for file forwarded to Enterprise DLP when a DLP rules is configured to Alert.
- Specify the Scan Limit Max File Size for Block (MB) to enforce the maximum file size for files forwarded to Enterprise DLP for inspection.
- Specify the Action on Max File Size (Allow or Block) Enterprise DLP takes if no verdict was received for a file forward due to the file size being larger than the configured Max File Size.Selecting Block applies only to DLP rules configured to block files. This setting does not impact Enterprise DLP data filtering profiles configured to alert when traffic containing sensitive data is scanned.
- Check (enable) Log Files Not Scanned to generate an alert in the DLP incident when Enterprise DLP can't scan a forwarded file.
- Specify the Action When Scanning Error Occurred (Alert or Block) the NGFW or Prisma Access tenant takes when any kind of error occurs that prevents Enterprise DLP from inspecting a forwarded file and rendering a verdict.
- Save.
- Edit the Non-File Based Settings.
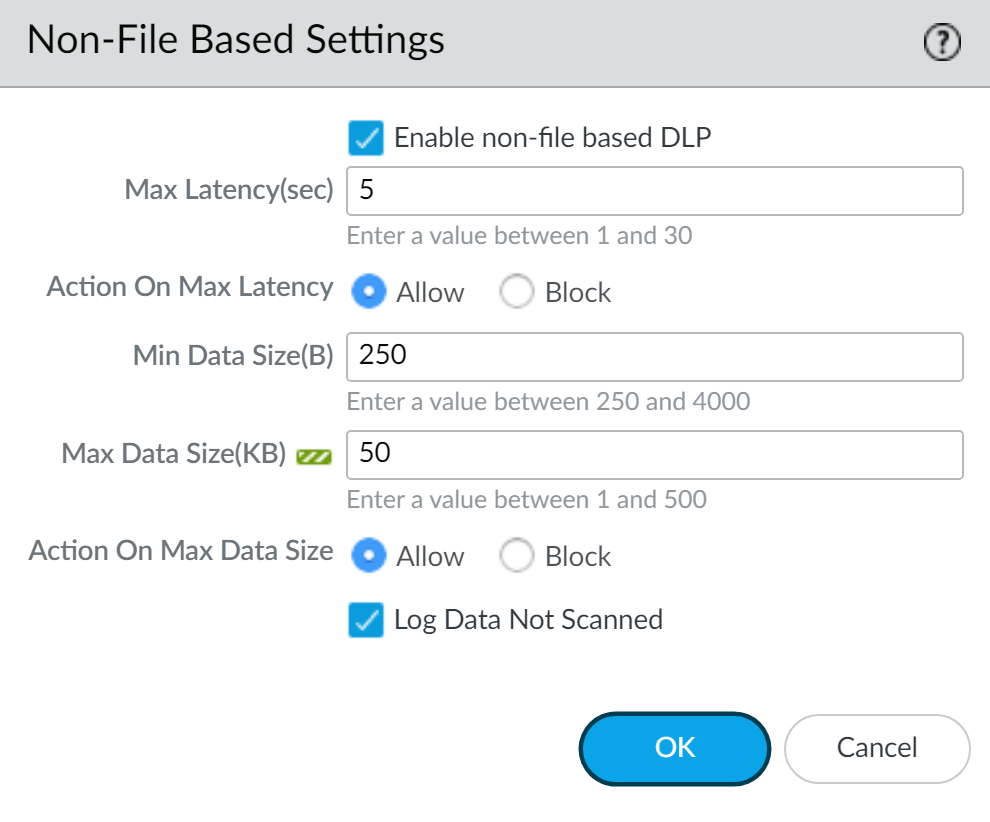
- Enable non-file based DLP.Enable this setting to prevent exfiltration of sensitive data in non-file format traffic for collaboration apps, web forms, cloud and SaaS apps, and social media on your network.
- Specify the Max Latency (sec) to configure the allowable time for a non-file data forwards to determine the allowable time before the NGFW or Prisma Access tenant take the configured Action on Max Latency.
- Specify the Action on Max Latency (Allow or Block) NGFW or Prisma Access tenant takes if it did not receive a verdict from Enterprise DLP due to the forward time exceeding the configured Max Latency.Selecting Block applies only to DLP rules configured to block non-file data. This setting does not impact Enterprise DLP data profiles configured to alert when traffic containing sensitive data is scanned.
- Specify the Min Data Size (B) to enforce a minimum size for non-file data to be scanned by Enterprise DLP. By default, Enterprise DLP supports a minimum non-file traffic data size of 250 bytes.
- Specify the Max Data Size (KB) to enforce a maximum size for non-file data to be scanned by Enterprise DLP.
- Specify the Action on Data Size (Allow or Block) NGFW or Prisma Access tenant takes if it did not receive a verdict from Enterprise DLP for a non-file traffic due to the traffic data size being larger than the Max Data Size.Selecting Block applies only to DLP rules configured to block non-file data. This setting does not impact Enterprise DLP data profiles configured to alert when traffic containing sensitive data is scanned.
- Check (enable) Log Data Not Scanned to generate an alert in the DLP incident when Enterprise DLP can't scan non-file traffic.
- Save.
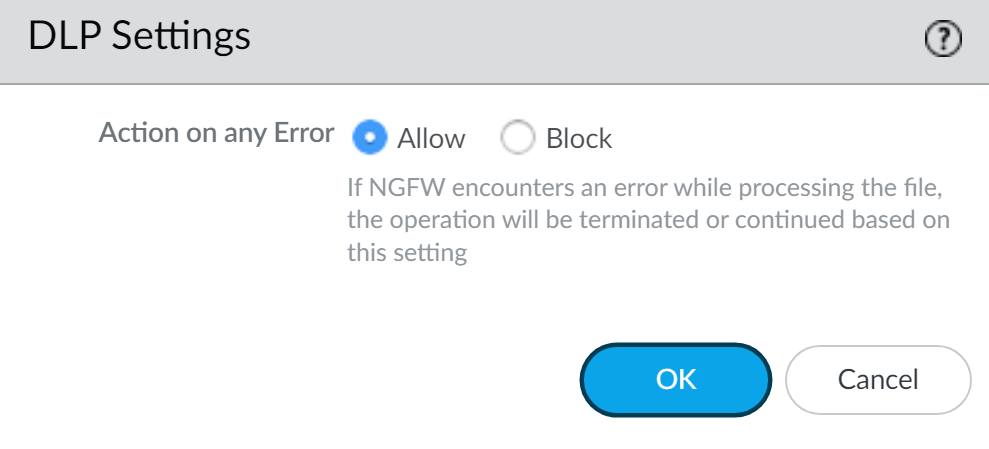
- In the DLP Settings, configure the Action on any Error to specify the action the NGFW or Prisma Access tenant takes when any kind of error occurs that prevents Enterprise DLP from inspecting forwarded file or non-file traffic and rendering a verdict.Select Allow to allow the file or non-file traffic to continue to the intended destination when Enterprise DLP encounters an error or select Block to block the file or non-file traffic. This includes when the NGFW or Prisma Access tenant encounter file or non-file traffic smaller than the configured Min Data Size (B) (non-file), and the Action on Max File Size (file) and Max Data Size (KB) (non-file).Save.
- Push your DLP rule.
- Push Config and Push.
- Select (enable) Remote Networks and Mobile Users.
- Push.
Edit the Enterprise DLP Data Filtering Settings on Panorama
Edit the data filtering settings to specify the actions the NGFW or Prisma Access tenant takes on traffic scanned to the DLP cloud service.
- Log in to the Panorama web interface.
- Select DeviceSetupDLP and select the Template associated with the NGFW or Prisma Access tenant using Enterprise DLP.
- Edit the Data Filtering Settings.
- Specify the Max Latency (sec) for a file upload before an action is taken by the NGFW or Prisma Access tenant.For inspection of files greater than 20 MB, Palo Alto Networks recommends setting the max latency to greater than 60 seconds.
- Specify the Action on Max Latency (Block or Allow) the NGFW or Prisma Access tenant takes if no verdict was received for a file upload due to the upload time exceeding the Max Latency.Selecting Block applies only to data profiles configured to block files. This setting doesn’t impact Enterprise DLP data filtering profiles configured to alert when traffic containing sensitive data is scanned.
- Specify the Max File Size (MB) to enforce a maximum file size for files uploaded to the DLP cloud service for inspection.
- Specify the Action on Max File Size (Block or Allow) the NGFW or Prisma Access tenant takes if no verdict was received for a file upload due to the file size being larger than the configured Max File Size.Selecting Block applies only to data profiles configured to block files. This setting doesn’t impact Enterprise DLP data filtering profiles configured to alert when traffic containing sensitive data is scanned.(DLP 3.0.3 only) Increasing the max file size for the Enterprise DLP data filtering settings to 21 MB or greater when Panorama has the Enterprise DLP 3.0.3 plugin installed is supported only from the Panorama CLI.admin>configureCode copied to clipboardUnable to copy due to lack of browser support.admin#set template <template_name> config shared dlp-settings max-file-size <1 - 100>Code copied to clipboardUnable to copy due to lack of browser support.
- Check (enable) Log Files Not Scanned to generate an alert in the data filtering log when a file can’t be scanned to the DLP cloud service.
- Click OK to save your configuration changes.

- Edit the Non-File Data Filtering Settings.
- Verify that Enable Non File DLP is checked (enabled).Non-File DLP is enabled by default when you install Panorama plugin for Enterprise DLP 3.0.1.
- Specify the Max Latency (sec) to configure the allowable time for non-file data uploads to determine the allowable time before an action is taken by the NGFW or Prisma Access tenant.
- Specify the Action on Max Latency (Allow or Block) the NGFW or Prisma Access tenant takes if no verdict was received for a non-file traffic data upload due to the upload time exceeding the configured Max Latency.Selecting Block applies only to data profiles configured to block non-file data. This setting doesn’t impact Enterprise DLP filtering profiles configured to alert when traffic containing sensitive data is scanned.
- Specify the Min Data Size (B) to enforce a minimum size for non-file data to be scanned by Enterprise DLP.
- Specify the Max Data Size (KB) to enforce a maximum size for non-file data to be scanned by Enterprise DLP.
- Specify the Action on Data File Size (Allow or Block) the NGFW or Prisma Access tenant takes if no verdict was received for a non-file traffic data upload due to the traffic data size being larger than the configured Max Data Size.Selecting Block applies only to data profiles configured to block non-file data. This setting doesn’t impact Enterprise DLP data filtering profiles configured to alert when traffic containing sensitive data is scanned.
- Check (enable) Log Data Not Scanned to generate an alert in the data filtering log when non-file data can’t be scanned by the DLP cloud service.
- Click OK to save your configuration changes.

- Specify the Action on any Error the NGFW or Prisma Access tenant takes when any kind of error occurs that prevents Enterprise DLP from inspecting forwarded file or non-file traffic and rendering a verdict.This includes when the NGFW or Prisma Access tenant encounter file or non-file traffic smaller than the configured Min Data Size (B) (non-file), and the Action on Max File Size (file) and Max Data Size (KB) (non-file).
- Select Allow (default) to continue if the NGFW or Prisma Access tenant experiences any type of error.
- Select Block to stop uploading if the NGFW or Prisma Access tenant experiences any type of error.
Click OK to continue.
- Commit and push the new configuration to your NGFW or Prisma Access tenant.The Commit and Push command isn’t recommended for Enterprise DLP configuration changes. Using the Commit and Push command requires the additional and unnecessary overheard of manually selecting the impacted templates and NGFW or Prisma Access tenant in the Push Scope Selection.
- Full configuration push from Panorama
- Select CommitCommit to Panorama and Commit.
- Select CommitPush to Devices and Edit Selections.
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your NGFW or Prisma Access tenant that are using Enterprise DLP.
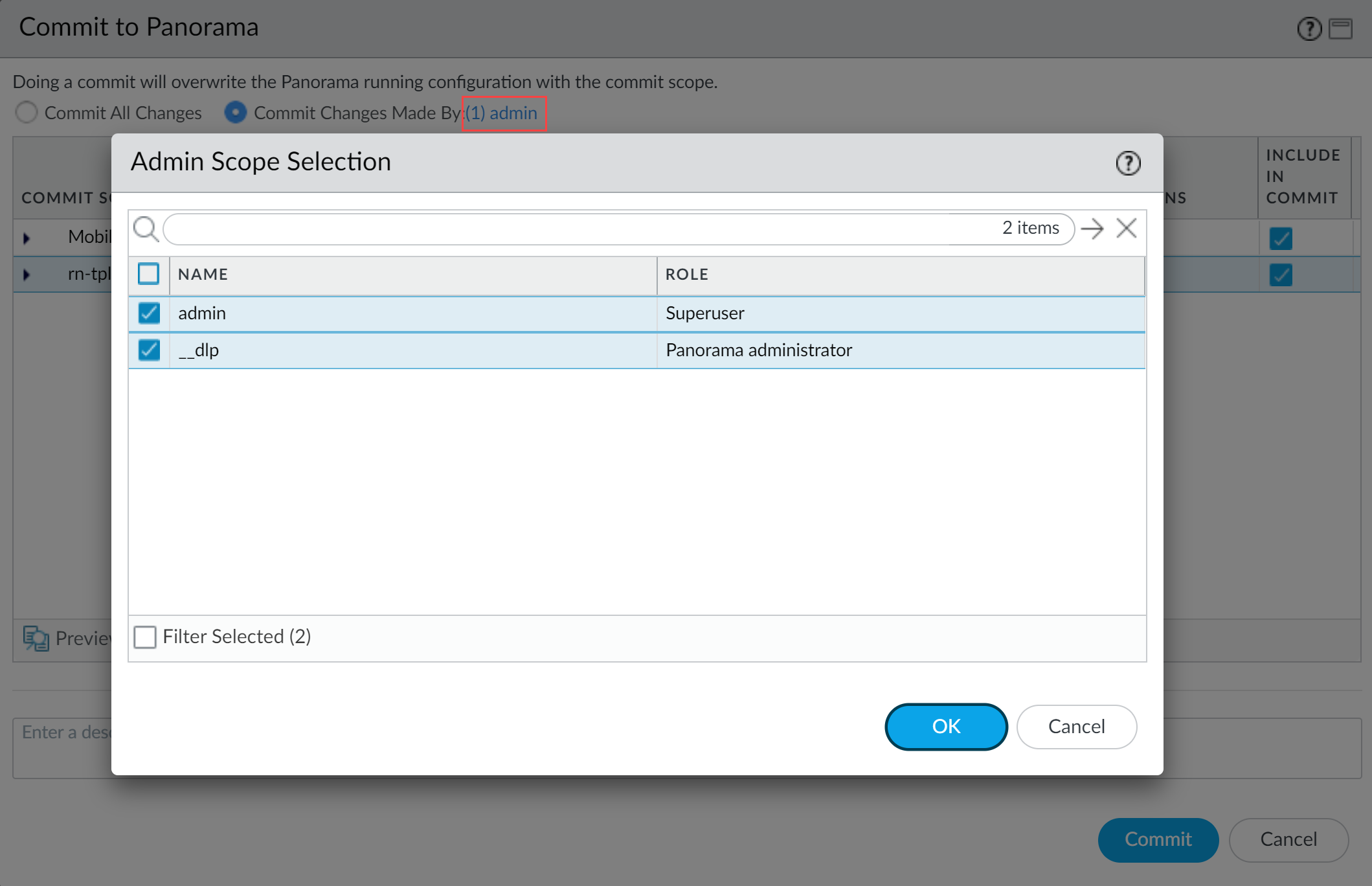
- Partial configuration push from PanoramaYou must always include the temporary __dlp administrator when performing a partial configuration push. This is required to keep Panorama and the DLP cloud service in sync.For example, you have an admin Panorama admin user who is allowed to commit and push configuration changes. The admin user made changes to the Enterprise DLP configuration and only wants to commit and push these changes to NGFW or Prisma Access tenant. In this case, the admin user is required to also select the __dlp user in the partial commit and push operations.
- Select CommitCommit to Panorama.
- Select Commit Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial commit.In this example, the admin user is currently logged in and performing the commit operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.

- Commit.
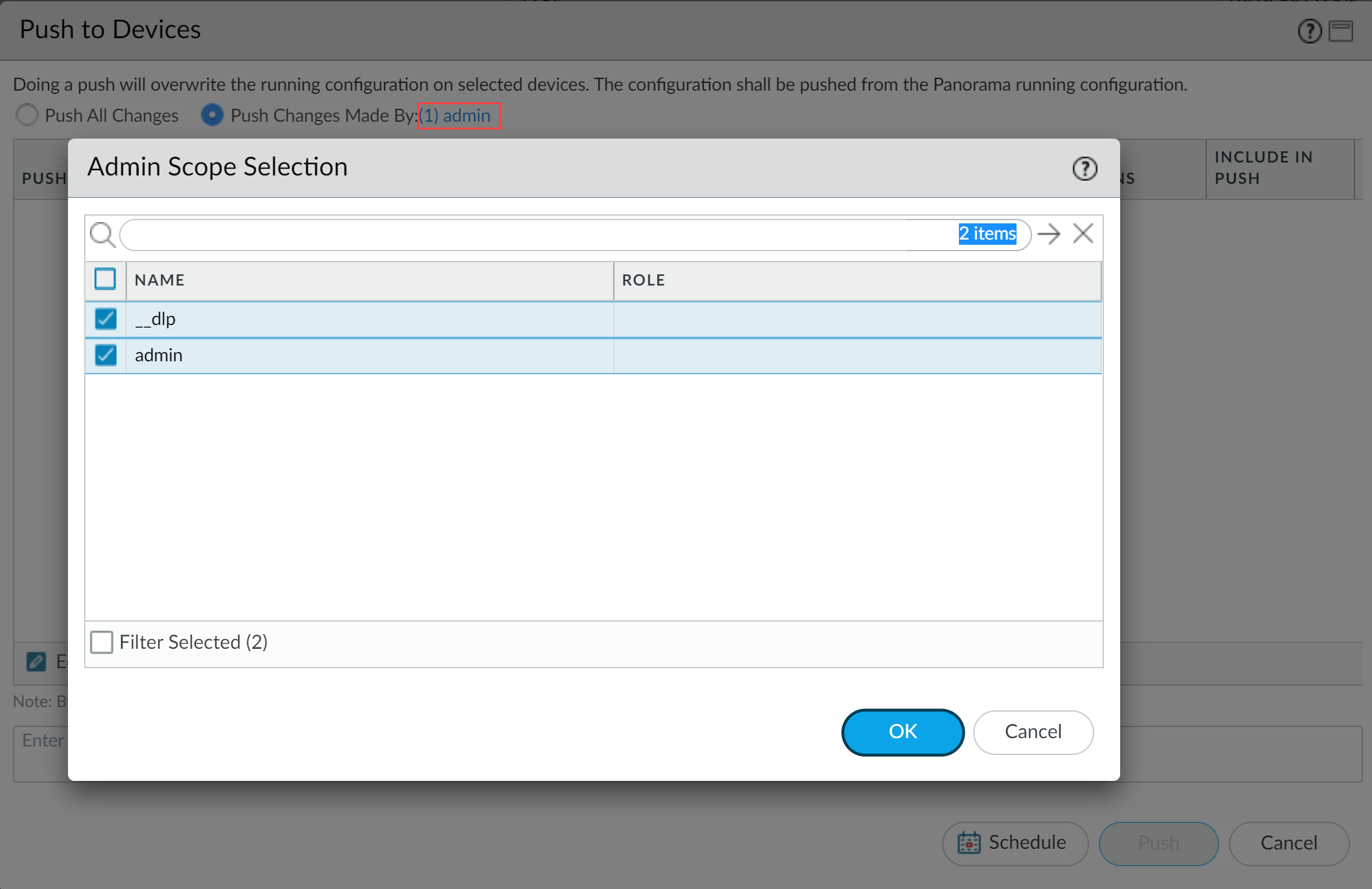
- Select CommitPush to Devices.
- Select Push Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial push.In this example, the admin user is currently logged in and performing the push operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.

- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your NGFW or Prisma Access tenant that using Enterprise DLP.
Expand allCollapse all
Edit the Enterprise DLP Data Filtering Settings for Email DLP
Edit the Enterprise Data Loss Prevention (E-DLP) data filtering settings for Email DLP on Strata Cloud Manager.
- Log in to Strata Cloud Manager.
- Select ManageConfigurationSaaS SecuritySettingsEmail DLP Settings.
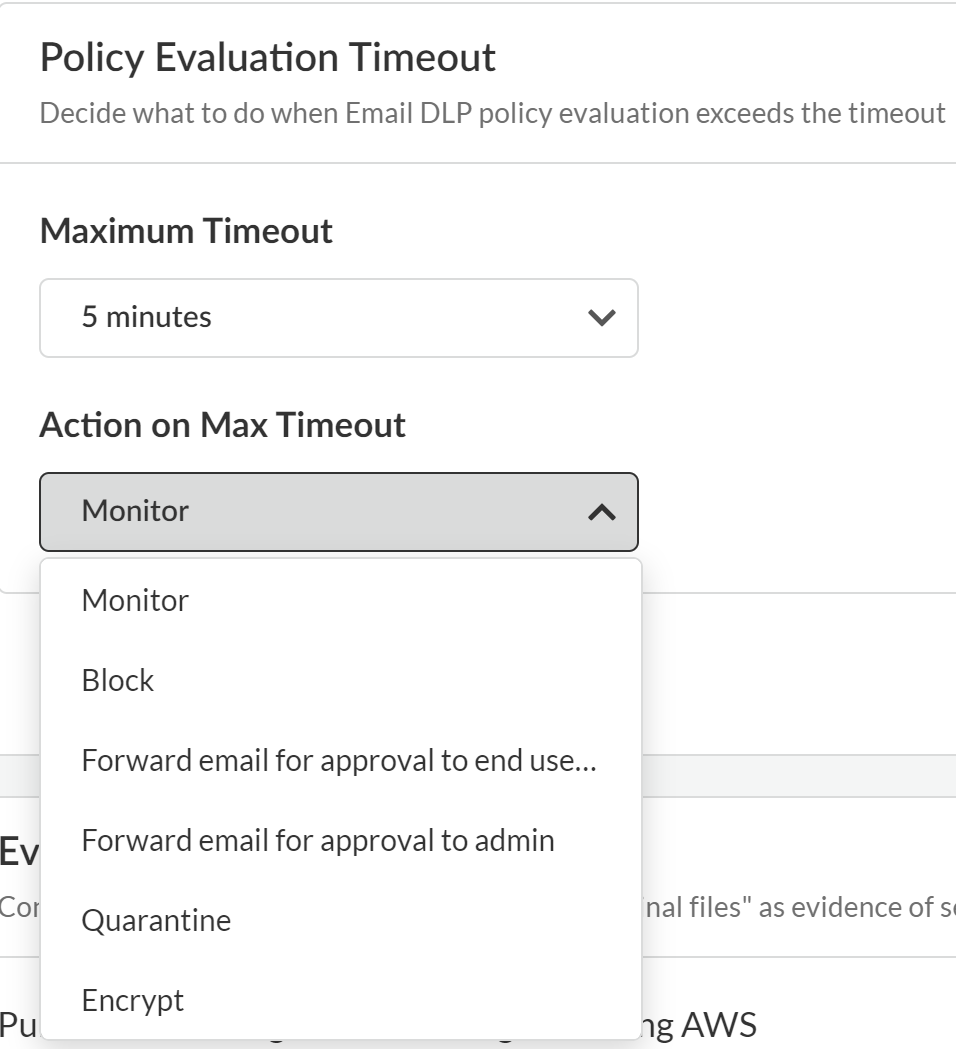
- Edit the Policy Evaluation Timeout to configure what Enterprise DLP does when Email DLP policy evaluation exceeds the configured timeout.
- Maximum Timeout—Maximum time allowed for Enterprise DLP to inspect an outbound email. Minimum timeout is 1 minute. Maximum timeout is 5 minutes.
- Action on Max Timeout—The action Enterprise DLP takes if the maximum timeout is exceeded. The possible actions are the same as those you configure in the Email DLP policy rule Response. Default is Monitor.

- Save Settings.
Edit the Enterprise DLP Data Filtering Settings for Endpoint DLP
Edit the Enterprise Data Loss Prevention (E-DLP) data filtering settings for Endpoint DLP on Strata Cloud Manager.
You can customize the data filtering settings for your USB, printer, and Network
Share peripheral devices independently of one another.
- Log in to Strata Cloud Manager.
- Select ManageConfigurationData Loss PreventionSettingsData Transfer to edit the data filtering settings.
- Edit the File Based Settings for Endpoint DLP.You can configure the data filtering settings for each type of peripheral device (USB Devices, Printers, and Network Shares) independently of one another.
- Verify that the correct Endpoint DLP Data Scan Region is selected.By default, the Nearest Data Scan Region is selected and automatically resolves to the region closest to your Enterprise DLP tenant. You can select a specific region to ensure you meet any data residency requirements if required.For example, your Endpoint DLP administrator sets the Data Scan Region to America instead of Nearest Data Scan Region. Your US based worker travels to Europe with their protected endpoint and generates a DLP Incident. In this case, the traffic is forwarded to an Enterprise DLP cloud service tenant in the US for inspection and verdict rendering even though the endpoint was in Europe when the incident was generated. Additionally the DLP Incident displays under the US Region when filtering your incidents.The data filtering settings are shared across all data scan regions. You cannot configure unique data filtering settings for each data scan region. Changing the data filtering settings for one data scan region changes it for all other supported data scan regions.
- Specify the File Movement Max Latency (Sec) for a file upload to a peripheral device before an action is taken by Enterprise DLP.For inspection of files greater than 20 MB, Palo Alto Networks recommends setting the max latency to greater than 60 seconds.
- Specify the Action When Max Latency is Reached (Alert or Block) Enterprise DLP takes if no verdict was received for a file upload to a peripheral device due to the upload time exceeding the configured Max Latency.Selecting Alert allows the file upload to the peripheral device but generates a DLP Incident.Selecting Block blocks the file upload to the peripheral device and generates a DLP incident.
- Specify the Scan Limit Max File Size for Block (MB) to enforce the maximum file size for file uploads to a peripheral device for a Data in Motion Endpoint DLP policy rule configured to Block.
- Specify the Scan Limit Max File Size for Alert (MB) to enforce the maximum file size for file uploads to a peripheral device for a Data in Motion Endpoint DLP policy rule configured to Alert.
- Specify the Scan Limit Action on Max File Size (Alert or Block) Enterprise DLP takes if no verdict was received for a file upload due to the file size being larger than the configured Max File Size.Selecting Block applies only to DLP rules configured to block files. This setting doesn’t impact Enterprise DLP data filtering profiles configured to alert when traffic containing sensitive data is scanned.
- Specify the Action When File Size Exceeds Max Limit (Alert or Block) Enterprise DLP takes if an inspected file exceeds the maximum alert or block file size limit configured in the previous steps.
- Check (enable) Log Files Not Scanned to generate an alert in the DLP incident when a file can’t be scanned to the DLP cloud service.
- Specify the Action When Scanning Error Occurred (Alert or Block) when any kind of error occurs that prevents Enterprise DLP from inspecting a file upload to a peripheral device and rendering a verdict.
- Specify the Action When Endpoint is Offline (Alert or Block) Enterprise DLP takes if the peripheral device is offline and cannot forward traffic for inspection.
- Save.
- Push your new Endpoint DLP data filtering settings to the Prisma Access Agent.
- Select Endpoint DLP PolicyPush Policies and Push Policies.
- (Optional) Enter a Description for the Endpoint DLP policy push.
- Review the Push Policies scope to understand the changes included the Endpoint DLP configuration push.
- Push.