Use XFF IP Address Values in Security Policy and Logging
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
PAN-OS 10.2
- PAN-OS 11.1 & Later
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- Cloud Management of NGFWs
-
- Management Interfaces
-
- Launch the Web Interface
- Configure Banners, Message of the Day, and Logos
- Use the Administrator Login Activity Indicators to Detect Account Misuse
- Manage and Monitor Administrative Tasks
- Commit, Validate, and Preview Firewall Configuration Changes
- Commit Selective Configuration Changes
- Export Configuration Table Data
- Use Global Find to Search the Firewall or Panorama Management Server
- Manage Locks for Restricting Configuration Changes
-
-
- Define Access to the Web Interface Tabs
- Provide Granular Access to the Monitor Tab
- Provide Granular Access to the Policy Tab
- Provide Granular Access to the Objects Tab
- Provide Granular Access to the Network Tab
- Provide Granular Access to the Device Tab
- Define User Privacy Settings in the Admin Role Profile
- Restrict Administrator Access to Commit and Validate Functions
- Provide Granular Access to Global Settings
- Provide Granular Access to the Panorama Tab
- Provide Granular Access to Operations Settings
- Panorama Web Interface Access Privileges
-
- Reset the Firewall to Factory Default Settings
-
- Plan Your Authentication Deployment
- Pre-Logon for SAML Authentication
- Configure SAML Authentication
- Configure Kerberos Single Sign-On
- Configure Kerberos Server Authentication
- Configure TACACS+ Authentication
- Configure RADIUS Authentication
- Configure LDAP Authentication
- Configure Local Database Authentication
- Configure an Authentication Profile and Sequence
- Test Authentication Server Connectivity
- Troubleshoot Authentication Issues
-
- Keys and Certificates
- Default Trusted Certificate Authorities (CAs)
- Certificate Deployment
- Configure the Master Key
- Export a Certificate and Private Key
- Configure a Certificate Profile
- Configure an SSL/TLS Service Profile
- Configure an SSH Service Profile
- Replace the Certificate for Inbound Management Traffic
- Configure the Key Size for SSL Forward Proxy Server Certificates
-
- HA Overview
-
- Prerequisites for Active/Active HA
- Configure Active/Active HA
-
- Use Case: Configure Active/Active HA with Route-Based Redundancy
- Use Case: Configure Active/Active HA with Floating IP Addresses
- Use Case: Configure Active/Active HA with ARP Load-Sharing
- Use Case: Configure Active/Active HA with Floating IP Address Bound to Active-Primary Firewall
- Use Case: Configure Active/Active HA with Source DIPP NAT Using Floating IP Addresses
- Use Case: Configure Separate Source NAT IP Address Pools for Active/Active HA Firewalls
- Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT
- Use Case: Configure Active/Active HA for ARP Load-Sharing with Destination NAT in Layer 3
- HA Clustering Overview
- HA Clustering Best Practices and Provisioning
- Configure HA Clustering
- Refresh HA1 SSH Keys and Configure Key Options
- HA Firewall States
- Reference: HA Synchronization
-
- Use the Dashboard
- Monitor Applications and Threats
- Monitor Block List
-
- Report Types
- View Reports
- Configure the Expiration Period and Run Time for Reports
- Disable Predefined Reports
- Custom Reports
- Generate Custom Reports
- Generate the SaaS Application Usage Report
- Manage PDF Summary Reports
- Generate User/Group Activity Reports
- Manage Report Groups
- Schedule Reports for Email Delivery
- Manage Report Storage Capacity
- View Policy Rule Usage
- Use External Services for Monitoring
- Configure Log Forwarding
- Configure Email Alerts
-
- Configure Syslog Monitoring
-
- Traffic Log Fields
- Threat Log Fields
- URL Filtering Log Fields
- Data Filtering Log Fields
- HIP Match Log Fields
- GlobalProtect Log Fields
- IP-Tag Log Fields
- User-ID Log Fields
- Decryption Log Fields
- Tunnel Inspection Log Fields
- SCTP Log Fields
- Authentication Log Fields
- Config Log Fields
- System Log Fields
- Correlated Events Log Fields
- GTP Log Fields
- Audit Log Fields
- Syslog Severity
- Custom Log/Event Format
- Escape Sequences
- Forward Logs to an HTTP/S Destination
- Firewall Interface Identifiers in SNMP Managers and NetFlow Collectors
- Monitor Transceivers
-
- User-ID Overview
- Enable User-ID
- Map Users to Groups
- Enable User- and Group-Based Policy
- Enable Policy for Users with Multiple Accounts
- Verify the User-ID Configuration
-
- App-ID Overview
- App-ID and HTTP/2 Inspection
- Manage Custom or Unknown Applications
- Safely Enable Applications on Default Ports
- Applications with Implicit Support
-
- Prepare to Deploy App-ID Cloud Engine
- Enable or Disable the App-ID Cloud Engine
- App-ID Cloud Engine Processing and Policy Usage
- New App Viewer (Policy Optimizer)
- Add Apps to an Application Filter with Policy Optimizer
- Add Apps to an Application Group with Policy Optimizer
- Add Apps Directly to a Rule with Policy Optimizer
- Replace an RMA Firewall (ACE)
- Impact of License Expiration or Disabling ACE
- Commit Failure Due to Cloud Content Rollback
- Troubleshoot App-ID Cloud Engine
- Application Level Gateways
- Disable the SIP Application-level Gateway (ALG)
- Maintain Custom Timeouts for Data Center Applications
-
- Policy Types
- Policy Objects
- Track Rules Within a Rulebase
- Enforce Policy Rule Description, Tag, and Audit Comment
- Move or Clone a Policy Rule or Object to a Different Virtual System
-
- External Dynamic List
- Built-in External Dynamic Lists
- Configure the Firewall to Access an External Dynamic List
- Retrieve an External Dynamic List from the Web Server
- View External Dynamic List Entries
- Exclude Entries from an External Dynamic List
- Enforce Policy on an External Dynamic List
- Find External Dynamic Lists That Failed Authentication
- Disable Authentication for an External Dynamic List
- Register IP Addresses and Tags Dynamically
- Use Dynamic User Groups in Policy
- Use Auto-Tagging to Automate Security Actions
- CLI Commands for Dynamic IP Addresses and Tags
- Application Override Policy
- Test Policy Rules
-
- Network Segmentation Using Zones
- How Do Zones Protect the Network?
-
PAN-OS 11.1 & Later
- PAN-OS 11.1 & Later
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
-
- Tap Interfaces
-
- Layer 2 and Layer 3 Packets over a Virtual Wire
- Port Speeds of Virtual Wire Interfaces
- LLDP over a Virtual Wire
- Aggregated Interfaces for a Virtual Wire
- Virtual Wire Support of High Availability
- Zone Protection for a Virtual Wire Interface
- VLAN-Tagged Traffic
- Virtual Wire Subinterfaces
- Configure Virtual Wires
- Configure a PPPoE Client on a Subinterface
- Configure an IPv6 PPPoE Client
- Configure an Aggregate Interface Group
- Configure Bonjour Reflector for Network Segmentation
- Use Interface Management Profiles to Restrict Access
-
- DHCP Overview
- Firewall as a DHCP Server and Client
- Firewall as a DHCPv6 Client
- DHCP Messages
- Dynamic IPv6 Addressing on the Management Interface
- Configure an Interface as a DHCP Server
- Configure an Interface as a DHCPv4 Client
- Configure an Interface as a DHCPv6 Client with Prefix Delegation
- Configure the Management Interface as a DHCP Client
- Configure the Management Interface for Dynamic IPv6 Address Assignment
- Configure an Interface as a DHCP Relay Agent
-
- DNS Overview
- DNS Proxy Object
- DNS Server Profile
- Multi-Tenant DNS Deployments
- Configure a DNS Proxy Object
- Configure a DNS Server Profile
- Use Case 1: Firewall Requires DNS Resolution
- Use Case 2: ISP Tenant Uses DNS Proxy to Handle DNS Resolution for Security Policies, Reporting, and Services within its Virtual System
- Use Case 3: Firewall Acts as DNS Proxy Between Client and Server
- DNS Proxy Rule and FQDN Matching
-
- NAT Rule Capacities
- Dynamic IP and Port NAT Oversubscription
- Dataplane NAT Memory Statistics
-
- Translate Internal Client IP Addresses to Your Public IP Address (Source DIPP NAT)
- Create a Source NAT Rule with Persistent DIPP
- PAN-OS
- Strata Cloud Manager
- Enable Clients on the Internal Network to Access your Public Servers (Destination U-Turn NAT)
- Enable Bi-Directional Address Translation for Your Public-Facing Servers (Static Source NAT)
- Configure Destination NAT with DNS Rewrite
- Configure Destination NAT Using Dynamic IP Addresses
- Modify the Oversubscription Rate for DIPP NAT
- Reserve Dynamic IP NAT Addresses
- Disable NAT for a Specific Host or Interface
-
- Network Packet Broker Overview
- How Network Packet Broker Works
- Prepare to Deploy Network Packet Broker
- Configure Transparent Bridge Security Chains
- Configure Routed Layer 3 Security Chains
- Network Packet Broker HA Support
- User Interface Changes for Network Packet Broker
- Limitations of Network Packet Broker
- Troubleshoot Network Packet Broker
-
- Enable Advanced Routing
- Logical Router Overview
- Configure a Logical Router
- Create a Static Route
- Configure BGP on an Advanced Routing Engine
- Create BGP Routing Profiles
- Create Filters for the Advanced Routing Engine
- Configure OSPFv2 on an Advanced Routing Engine
- Create OSPF Routing Profiles
- Configure OSPFv3 on an Advanced Routing Engine
- Create OSPFv3 Routing Profiles
- Configure RIPv2 on an Advanced Routing Engine
- Create RIPv2 Routing Profiles
- Create BFD Profiles
- Configure IPv4 Multicast
- Configure MSDP
- Create Multicast Routing Profiles
- Create an IPv4 MRoute
-
-
PAN-OS 11.2
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
- Cloud Management and AIOps for NGFW
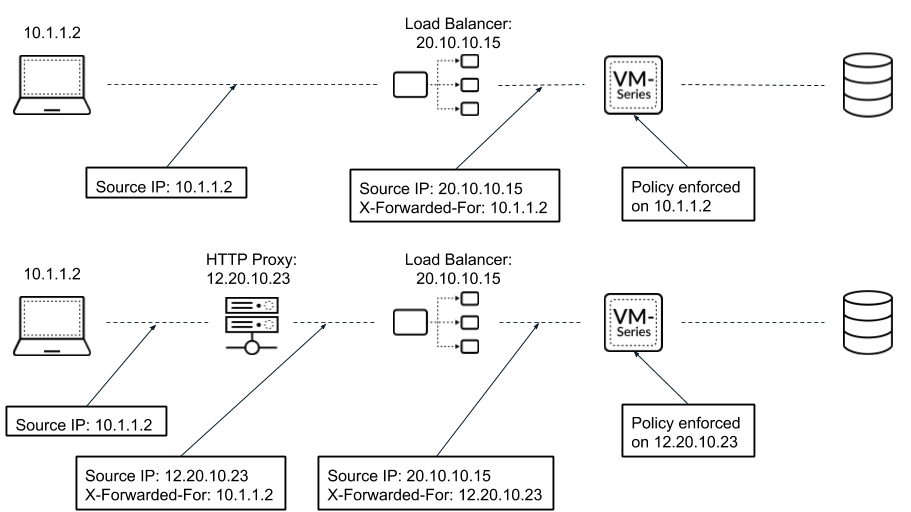
Use XFF IP Address Values in Security Policy and Logging
Configure your firewall to use X-Forwarded For IP address
values in Security Policy and logging.
You can configure the firewall to use the
source IP address in an X-Forwarded-For (XFF) HTTP header
field to enforce security policy. When a packet passes through
a single proxy server before reaching the firewall, the XFF field
contains the IP address of the originating endpoint. However, if the
packet passes through multiple upstream devices, the firewall uses
the most recently added IP address to enforce policy or use other
features that rely on IP information.
- Use XFF Values in Policy
- Display XFF Values in Logs
- Display XFF Values in Reports
Use XFF Values in Policy
Complete the following procedure to enforce
security policy using the client IP address in the XFF header.
In
Microsoft Azure, by default, an application gateway inserts the original
source IP address and port in the XFF header. To use XFF headers
in policy on your firewall, you must configure the application gateway
to omit the port from the XFF header. For more information, see Azure documentation.
- Log in to your firewall.
- Select DeviceSetupContent-IDX-Forwarded-For Headers.
- Click the edit icon.
- Select Enabled for Security Policy from the Use X-Forwarded-For Header drop-down.You cannot enable Use X-Forwarded-For Header for security policy and User-ID at the same time.

- (Optional) Select Strip X-Forwarded-For Header to remove the XFF field from outgoing HTTP requests.Selecting this option does not disable the use of XFF headers. The firewall strips the XFF field from client requests after using it to enforce policy and log IP addresses.
- Click OK.
- Commit your changes.
Display XFF Values in Logs
In addition to XFF header usage in security
policy, you can view the XFF IP address in various logs, reports,
and the Application Command Center (ACC) to aid in monitoring and
troubleshooting. You can add the X-Forwarded-For column to Traffic,
Threat, Data Filtering, and Wildfire Submissions logs.
For
non-URL Filtering logs, XFF IP logging is supported only when packet
capture is not enabled.
The X-Forwarded-For IP column does not display a value in the threat logs if
the firewall detects a threat before it inspects the XFF header, however, it
is present in the traffic logs provided the action for the relevant security
profile is configured for Allow or
Alert.
To
view the XFF IP address in your logs, complete the following steps.
- Log in to your firewall.
- Select MonitoringLogs.
- Select Traffic, Threat, Data Filtering, or Wildfire Submissions.
- Click the arrow to the right of any column header and select Columns.
- Select X-Forwarded-For IP to display the XFF IP in your log.

Display XFF Values in Reports
Predefined reports generated
by the firewall do not contain XFF values. However, the firewall
has built-in report templates that include XFF information. To view
XFF IP addresses in reports, follow the steps to generate reports
with the built-in templates.
- Log in to your firewall.
- Select MonitorManage Custom ReportsAdd.
- Click Load Template.
- Enter XFF into the search bar and click the search button to locate the built-in XFF report templates.

- Click Load.
- Configure your custom report. Click Time Frame, Sort By, and Group By to display the XFF information in the manner best suited to your needs.
- (Optional) Click Run Now to generate your report on demand instead of, or in addition to, a Scheduled Time.



