Enterprise DLP
Add an Email DLP Policy Rule
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Add an Email DLP Policy Rule
Add an Enterprise Data Loss Prevention (E-DLP) Email DLP policy rule to prevent sensitive data
exfiltration contained in outbound emails.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Add and configure an Enterprise Data Loss Prevention (E-DLP) email policy rule so Enterprise DLP to prevent sensitive data exfiltration contained in outbound emails. The Email
DLP policy rule specifies the incident severity and the action Enterprise DLP
takes when matching traffic is inspected and sensitive data is detected.
Enterprise DLP supports inspection and detection of documents containing
sensitive data that are attached to an email. Enterprise DLP does not
support inspection of document links.
- Log in to Strata Cloud Manager.(Optional) Create custom data patterns and data profiles to specify custom match criteria.Skip this step if you want to use the predefined Enterprise DLP data profiles available by default.
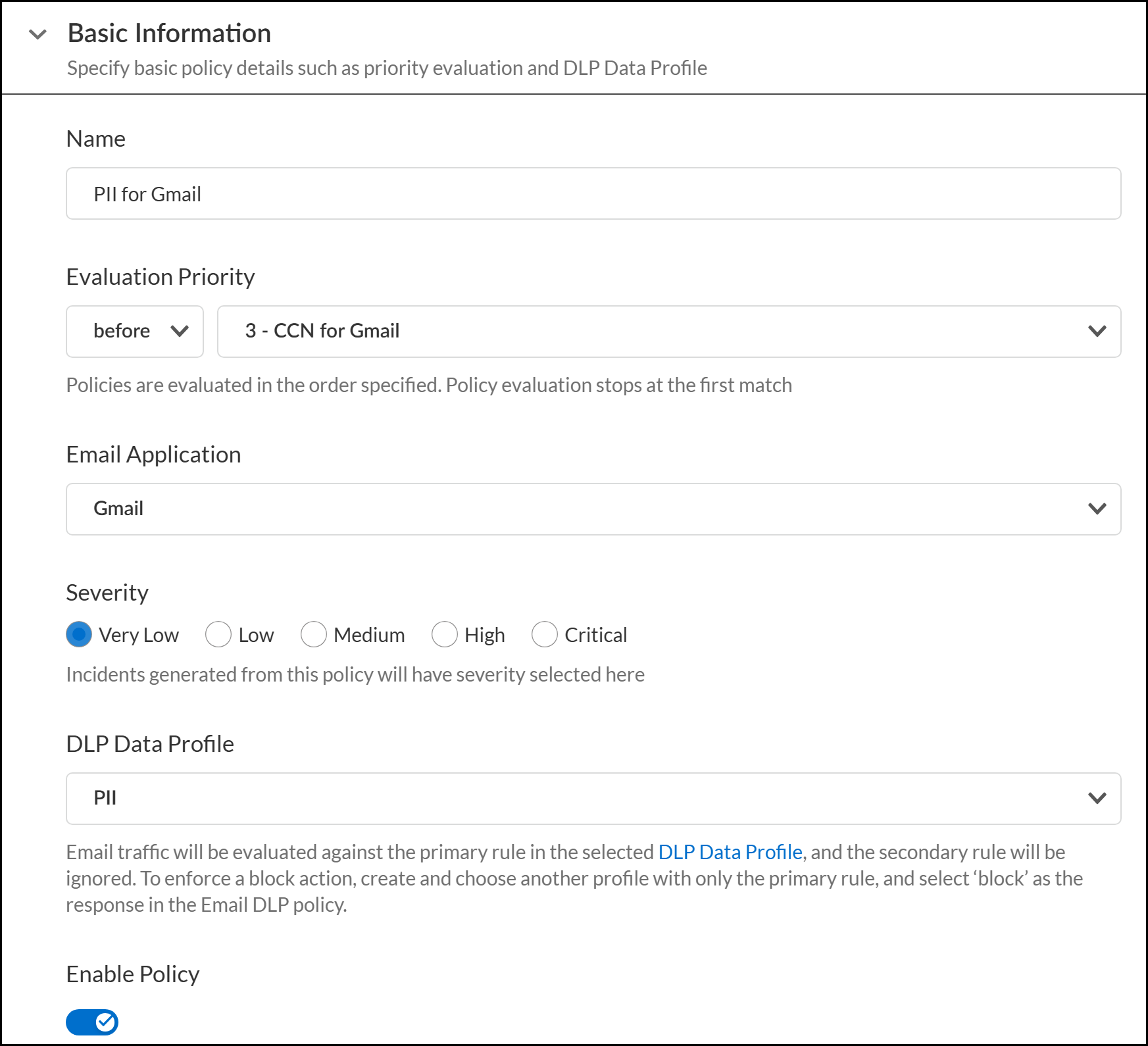
- Create custom data patterns and custom document types as needed.Create a data profile.Select ConfigurationSaaS SecurityData SecurityPoliciesEmail DLP Policies and Add Policy.Configure the Basic Information of the Email DLP policy rule.
- Enter a descriptive Name.Specify the Evaluation Priority of the Email DLP policy rule.This Evaluation Priority determines the order Email DLP policy rules are evaluated.Select whether the new Email DLP policy rule goes before or after an existing Email DLP policy rule.
- For the Email Application, select Microsoft Exchange or Gmail.Select the Enterprise DLP incident severity for when Enterprise DLP detects matching traffic.Select the DLP Data Profile to associate with the Email DLP policy rule.The DLP data profile you select is used as the traffic match criteria that Enterprise DLP evaluates inspected traffic against. The data profile can be either a predefined data profile or a custom data profile.Verify that Enable Policy is toggled on.This setting is enabled by default when you add a new Email DLP policy rule.
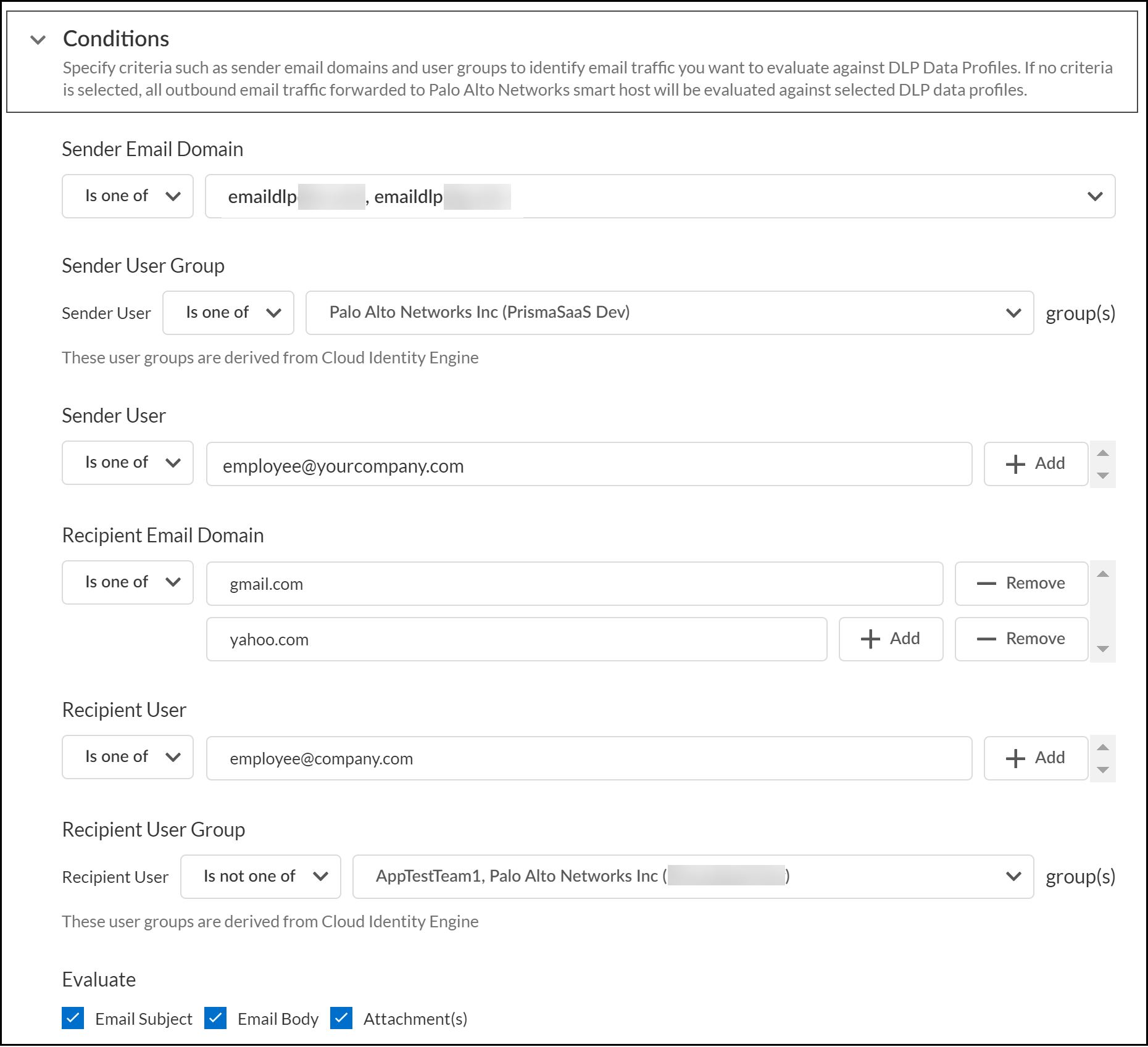
![]() Configure the Email DLP policy rule Conditions.The Email DLP policy rule conditions determine the email sender and recipient criteria for when inline inspection of email traffic should or should not be performed by Enterprise DLP. The Email DLP policy rule conditions have an AND relationship. This means that all email sender and recipient Conditions you configure must be met for Enterprise DLP to take action.You can configure all or only some of the Email DLP policy rule conditions settings as needed. If no email sender or recipient conditions are configured, then all outbound email traffic is inspected by Enterprise DLP and evaluated against the data profile you selected in the previous step.For example, you configure the Email DLP policy rule conditions to inspect for the yourcompany.com Sender Email Domain and gmail.com Recipient Email Domain only. For Enterprise DLP to take action, the email sender domain and recipient email domain must match what you have configured. In this instance, Enterprise DLP does not take action if the Recipient Email Domain is yahoo.com.
Configure the Email DLP policy rule Conditions.The Email DLP policy rule conditions determine the email sender and recipient criteria for when inline inspection of email traffic should or should not be performed by Enterprise DLP. The Email DLP policy rule conditions have an AND relationship. This means that all email sender and recipient Conditions you configure must be met for Enterprise DLP to take action.You can configure all or only some of the Email DLP policy rule conditions settings as needed. If no email sender or recipient conditions are configured, then all outbound email traffic is inspected by Enterprise DLP and evaluated against the data profile you selected in the previous step.For example, you configure the Email DLP policy rule conditions to inspect for the yourcompany.com Sender Email Domain and gmail.com Recipient Email Domain only. For Enterprise DLP to take action, the email sender domain and recipient email domain must match what you have configured. In this instance, Enterprise DLP does not take action if the Recipient Email Domain is yahoo.com.- Configure the email sender conditions.To configure the email sender conditions, you must specify whether the conditions are inclusive or exclusive of the specified email domains, user groups, or specific senders.
- Sender Email Domain
- Is one of—Email DLP matches and forwards outbound emails to Enterprise DLP for email addresses associated with selected email domains only.Email DLP does not match and forward outbound emails to Enterprise DLP if sent from an email address that's not associated with a selected email domain.
- Is not one of—Email DLP matches and forwards outbound emails to Enterprise DLP for all email addresses except for those associated with selected email domains.Email DLP does not match and forward outbound emails to Enterprise DLP if sent from an email address associated with a selected email domain.
- Sender User GroupThe sender user groups are derived from Cloud Identity Engine (CIE) that you set up when you that you connected Microsoft Exchange or Gmail.
- Is one of—Email DLP matches and forwards outbound emails to Enterprise DLP for email addresses associated with selected user groups only.Email DLP does not match and forward outbound emails to Enterprise DLP if sent from an email address not associated with a selected user group.
- Is not one of—Email DLP matches and forwards outbound emails to Enterprise DLP for all email addresses except for the email addresses associated with selected user groups.Email DLP does not match and forward outbound emails to Enterprise DLP if sent from an email address associated with a selected user group.
- Sender UserThe sender user addresses are derived from Cloud Identity Engine (CIE) that you set up when you that you connected Microsoft Exchange or Gmail.Click add () to include additional sender email addresses.
![]()
- Is one of—Email DLP matches and forwards outbound emails to Enterprise DLP for only selected sender email addresses.Email DLP does not match and forward outbound emails to Enterprise DLP if sent from a sender email address that's not selected.
- Is not one of—Email DLP matches and forwards outbound emails to Enterprise DLP for all sender email addresses except for the sender email addresses you selected.Email DLP does not match and forward outbound emails to Enterprise DLP if sent from a selected sender email address.
Configure the email Recipient conditions.To configure the email recipient conditions, you must specify whether the conditions are inclusive or exclusive of the specified email domains, user groups, or specific recipients.- Recipient Email DomainEnterprise DLP supports all valid email domains. The email domain is the web address that follows the @ symbol in an email address. For example, gmail.com or yahoo.com.Click add () to include additional recipient email domains.
![]()
- Is one of—Email DLP matches and forwards outbound emails to Enterprise DLP for email addresses associated with selected recipient email domains only.Email DLP does not match and forward outbound emails to Enterprise DLP if the recipient email address isn't associated with the specified recipient email domain.
- Are all one of—Email DLP policy rule matches and forwards outbound emails to Enterprise DLP only if all the specified recipient email addresses in the outbound email are associated with a specified email domain.Email DLP does not match and forward outbound emails to Enterprise DLP if any of the recipient email addresses associated with the recipient email domain are not included in the outbound email.
- Are all not one of—Email DLP policy rule matches and forwards outbound emails to Enterprise DLP only if all the specified recipient email addresses associated with the specified email domain are not included in the outbound email.Email DLP does not match and forward outbound emails to Enterprise DLP if any of the recipient email addresses associated with the recipient email domain are included in the outbound email.
- Is not one of—Email DLP matches and forwards outbound emails to Enterprise DLP for all email addresses except for those associated with selected email domains.Email DLP does not match and forward outbound emails to Enterprise DLP if any of the recipient email addresses associated with the recipient email domain are included in the outbound email.
- Recipient UserClick add () to include additional recipient email addresses.
![]()
- Is one of—Email DLP policy rule matches and forwards outbound emails to Enterprise DLP for only the specified recipient email addresses.Email DLP does not match and forward outbound emails to Enterprise DLP if the recipient email address isn't included in the outbound email.
- Are all one of—Email DLP policy rule matches and forwards outbound emails to Enterprise DLP only if all the specified recipient email addresses are included in the outbound email.Email DLP does not match and forward outbound emails to Enterprise DLP if any of the recipient email addresses aren't included in the outbound email.
- Are all not one of—Email DLP policy rule matches and forwards outbound emails to Enterprise DLP only if all the specified recipient email addresses are not included in the outbound email.Email DLP does not match and forward outbound emails to Enterprise DLP if any of the recipient email addresses are included in the outbound email.
- Is not one of—Email DLP policy rule matches and forwards outbound emails to Enterprise DLP for all email addresses except for the email addresses associated with the selected user groups.Email DLP does not match and forward outbound emails to Enterprise DLP if the recipient email address is included in the outbound email.
Configure the email components Enterprise DLP needs to Evaluate.Enterprise DLP can inspect and evaluate the Email Subject, Email Body, and Email Attachment(s) as needed. You can select one, two, or all available evaluation criteria. At least one evaluation criterion must be selected to save the Email DLP policy rule.![]() Configure the Email DLP policy rule Response.The Email DLP policy rule response configuration specifies the action Enterprise DLP takes when inspected traffic matches the data profile associated with the policy rule.
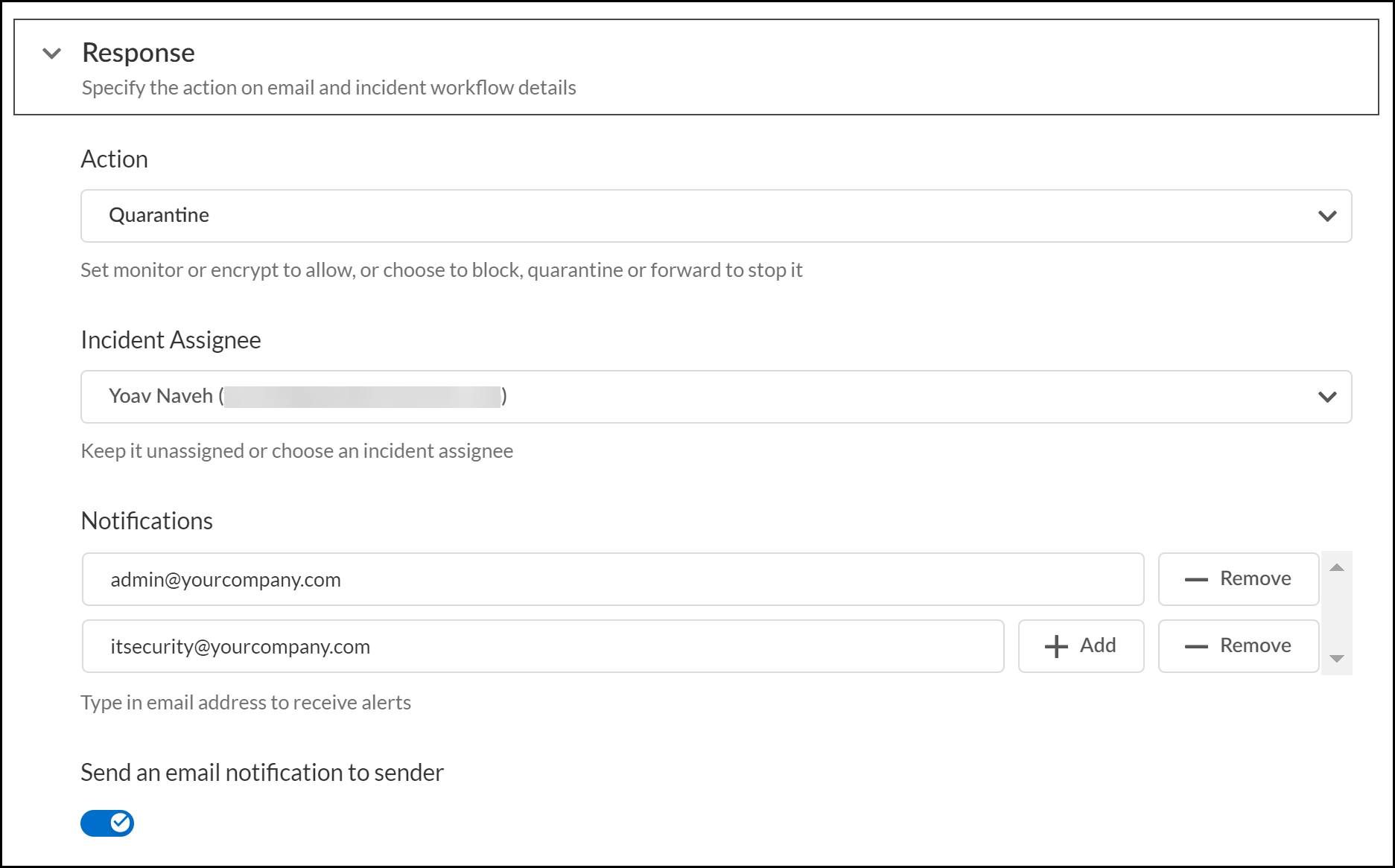
Configure the Email DLP policy rule Response.The Email DLP policy rule response configuration specifies the action Enterprise DLP takes when inspected traffic matches the data profile associated with the policy rule.- Specify the Action Enterprise DLP takes when inspected traffic matches the data profile associated with the policy rule.
- Monitor—Outbound email is allowed to leave your organization to the intended recipient. Enterprise DLP generates a DLP incident.
- Block—Outbound email is blocked from leaving your organization's network.The action Microsoft Exchange or Gmail takes on a Block verdict rendered by Enterprise DLP is based on the block transport rule you created.
- Quarantine—Outbound email is transported back to the email server and quarantined. The email is forwarded to the hosted quarantine spam inbox and requires review by an email administrator before the email is allowed to leave your organization's network.The action Microsoft Exchange or Gmail takes on a Quarantine verdict rendered by Enterprise DLP is based on the quarantine transport rule you created.
- (Microsoft Exchange only) Forward email for approval by end user's manager—Outbound email is transported back to Microsoft Exchange and sent to the sender's manager for approval. Independent review is required by the sender's manager before the email is allowed to leave your organization's network.The action Microsoft Exchange takes on a Forward email for approval by end user's manager verdict rendered by Enterprise DLP is based on the transport for manager approval rule you created.
- (Microsoft Exchange only) Forward email for approval admin—Outbound email is transported back to Microsoft Exchange and sent to the specified email admin for approval. Independent review is required by the specified email administrator before the email is allowed to leave your organization's network.The action Microsoft Exchange takes on a Forward email for approval admin verdict rendered by Enterprise DLP is based on the transport for admin approval rule you created.
- Encrypt—Outbound email is allowed to leave your organization but is encrypted before continuing its path to the intended recipient.The action Microsoft Exchange takes on a Encrypt verdict rendered by Enterprise DLP is based on the encrypt transport rule you created.For Microsoft Exchange, the email is transported back to Microsoft Exchange for encryption.For Gmail, the email is transported to your Proofpoint server for encryption.
(Optional) Automatically assign an Incident Assignee when Enterprise DLP renders a Block or Quarantine verdict on matching traffic.Strength your security posture by assigning an incident assignee to follow up on and resolve events where Enterprise DLP detects outbound emails that contain sensitive information.(Optional) Add emails to send Notifications to receive alerts when Enterprise DLP renders Block or Quarantine verdicts on inspected outbound traffic.Click add () to include additional emails to receive notifications.![]() (Optional; Microsoft Exchange only) Enable Send an email notification to sender.If enabled, an email is sent to the email sender if Enterprise DLP detects sensitive data and the Email DLP policy rule Action is any of the following:
(Optional; Microsoft Exchange only) Enable Send an email notification to sender.If enabled, an email is sent to the email sender if Enterprise DLP detects sensitive data and the Email DLP policy rule Action is any of the following:- Forward email for approval to end user's manager
- Forward email for approval to admin
- Quarantine
![]() Save Policy.
Save Policy.