Enterprise DLP
Enable Existing Data Patterns and Filtering Profiles
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Enable Existing Data Patterns and Filtering Profiles
Enable existing data patterns and filtering profiles not configured using Enterprise Data Loss Prevention (E-DLP).
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
After you successfully install the Enterprise Data Loss Prevention (E-DLP)
plugin on Panorama, existing data patterns and filtering profiles are no
longer displayed but you can still reference them in your Security policy rules. If
you have existing data filtering patterns and profiles
configured that you need to edit after installing the Enterprise DLP plugin,
you can display them again in your Panorama web interface.
Existing data patterns and data filtering profiles aren’t hidden if you’re using Enterprise DLP for Prisma Access (Managed by Panorama).
- Enable existing data patterns and filtering profiles on Panorama.
- Log in to the Panorama CLI.Enable the existing data patterns and filtering profiles.admin> request plugins dlp hide-old-config noPanorama returns a pass message to confirm the existing data patterns and filtering profiles are now displayed.Enter the following command to disable the displaying of existing data patterns and filtering profiles.admin> request plugins dlp hide-old-config yes(Optional) Enable existing data patterns and filtering profiles on the managed firewall if you have any Security policy rules configured locally on the firewall.
- Log in to the firewall CLI.Enable the existing data patterns and filtering profiles.admin> request plugins dlp hide-old-config noThe firewall returns a pass message to confirm the existing data patterns and filtering profiles are now displayed.Enter the following command to disable the displaying of existing data patterns and filtering profiles.admin> request plugins dlp hide-old-config yesLog in to the Panorama web interface.Edit your existing data patterns and filtering profiles.
- Select ObjectsCustom ObjectsData Patterns and edit your data patterns.Select ObjectsSecurity ProfilesData Filtering and edit your data filtering profiles.Select PoliciesSecurity and select the Device Group to modify your Security policy rules as needed.Commit and push the new configuration to your managed firewalls.The Commit and Push command isn’t recommended for Enterprise DLP configuration changes. Using the Commit and Push command requires the additional and unnecessary overheard of manually selecting the impacted templates and managed firewalls in the Push Scope Selection.
- Full configuration push from Panorama
- Select CommitCommit to Panorama and Commit.
- Select CommitPush to Devices and Edit Selections.
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.
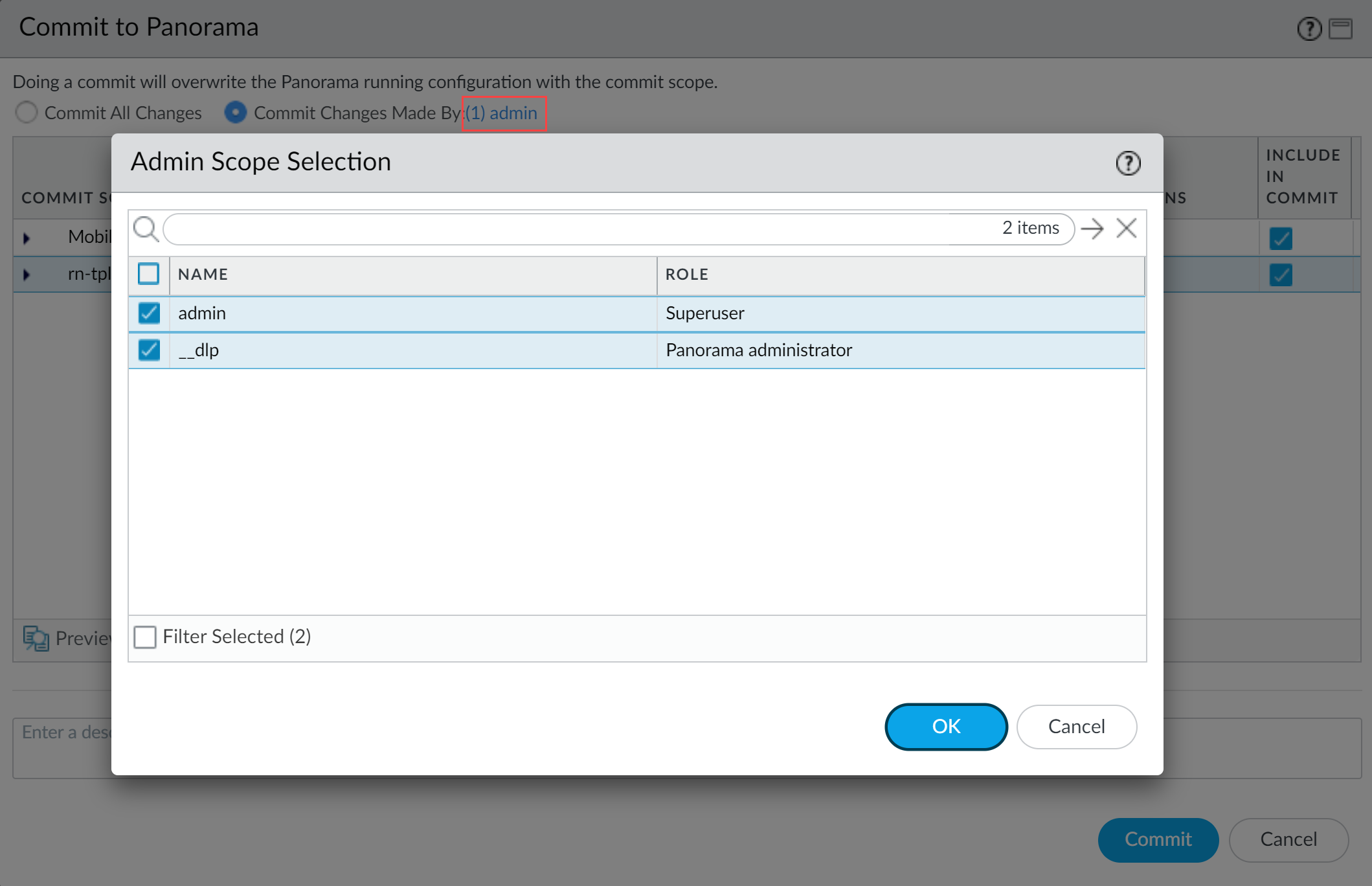
- Partial configuration push from PanoramaYou must always include the temporary __dlp administrator when performing a partial configuration push. This is required to keep Panorama and the DLP cloud service in sync.For example, you have an admin Panorama admin user who is allowed to commit and push configuration changes. The admin user made changes to the Enterprise DLP configuration and only wants to commit and push these changes to managed firewalls. In this case, the admin user is required to also select the __dlp user in the partial commit and push operations.
- Select CommitCommit to Panorama.
- Select Commit Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial commit.In this example, the admin user is currently logged in and performing the commit operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.
![]()
- Commit.
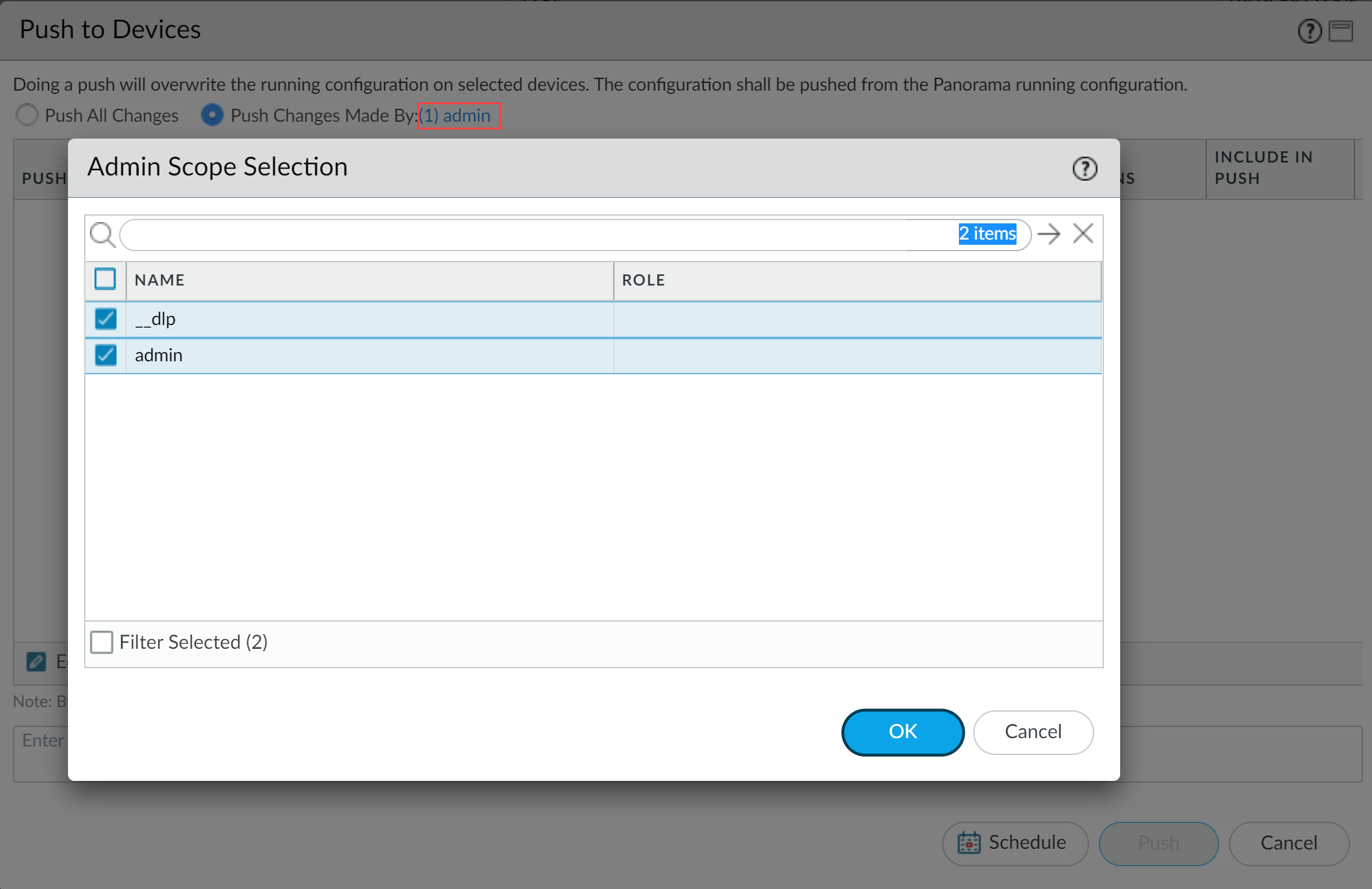
- Select CommitPush to Devices.
- Select Push Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial push.In this example, the admin user is currently logged in and performing the push operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.
![]()
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.