Network Security
Configure SSL Forward Proxy (PAN-OS & Panorama)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Configure SSL Forward Proxy (PAN-OS & Panorama)
- Confirm that the appropriate interfaces are configured as either virtual wire, Layer 2, or Layer 3 interfaces.Select NetworkInterfacesEthernet, and then check the Interface Type column for Virtual Wire, Layer 2, or Layer 3. Select an Interface to modify its configuration.Configure the Forward Trust certificate that the NGFW presents to clients after a trusted CA signs the server certificate.
- (Best Practice) Use an enterprise CA-signed certificate as the Forward Trust certificate:
- Create a certificate signing request (CSR) for the enterprise CA:
- Select DeviceCertificate ManagementCertificatesCustom Certificates (Device Certificates in PAN-OS 11.2 and earlier), and then click Generate.
- Enter a unique Certificate Name.
- Enter a Common Name. This should be the IP address or FQDN that appears in the certificate. Avoid using spaces in this field.
- For Signed By, select External Authority (CSR).
- (Optional) Add Certificate Attributes, such as Country or Department, to identify the NGFW.
- To save the CSR, click Generate.The Custom Certificates list displays the CSR with a Status of pending.
- Export the CSR.
- From the Custom Certificates list, select the pending certificate, and then click Export Certificate.The CSR downloads.
- Save the CSR.
- Submit the certificate request to the enterprise CA.After receiving the signed certificate, save it to your system.
- (Required for Clients Running Windows or Windows Server) Generate a subordinate CA certificate.
- Submit a certificate request that uses the Subordinate Certification Authority certificate template based on the CSR that you previously exported.
- Download the certificate chain.
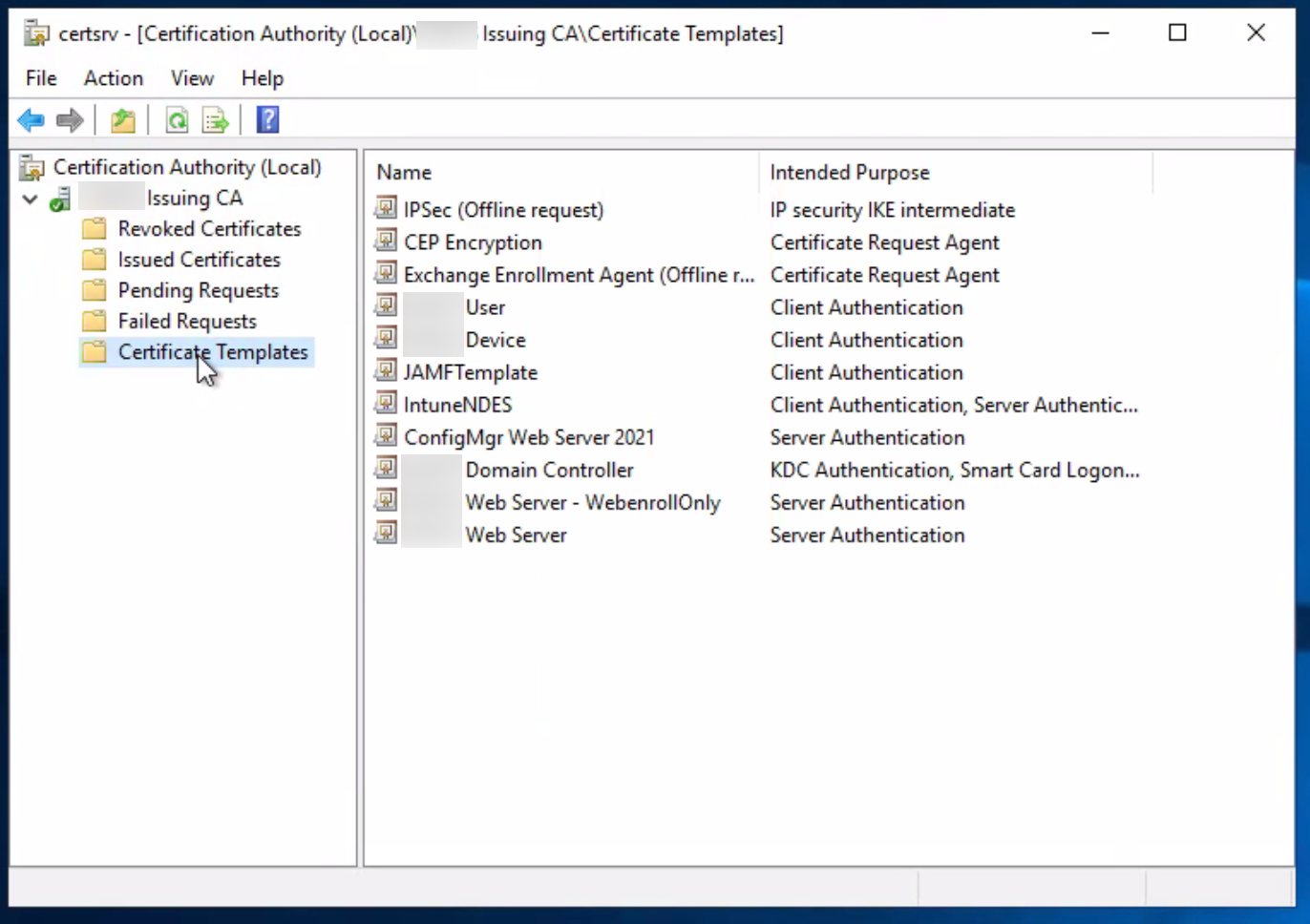
Configure Missing Subordinate Certificate Authority TemplateThe Subordinate Certificate Authority template may be unavailable for reasons such as a failed migration or missing permissions. Try the following procedure to configure the missing template:- Launch the Certificate Manager tool. From the Command Line, PowerShell, or Run, enter certsrv.msc.
![]()
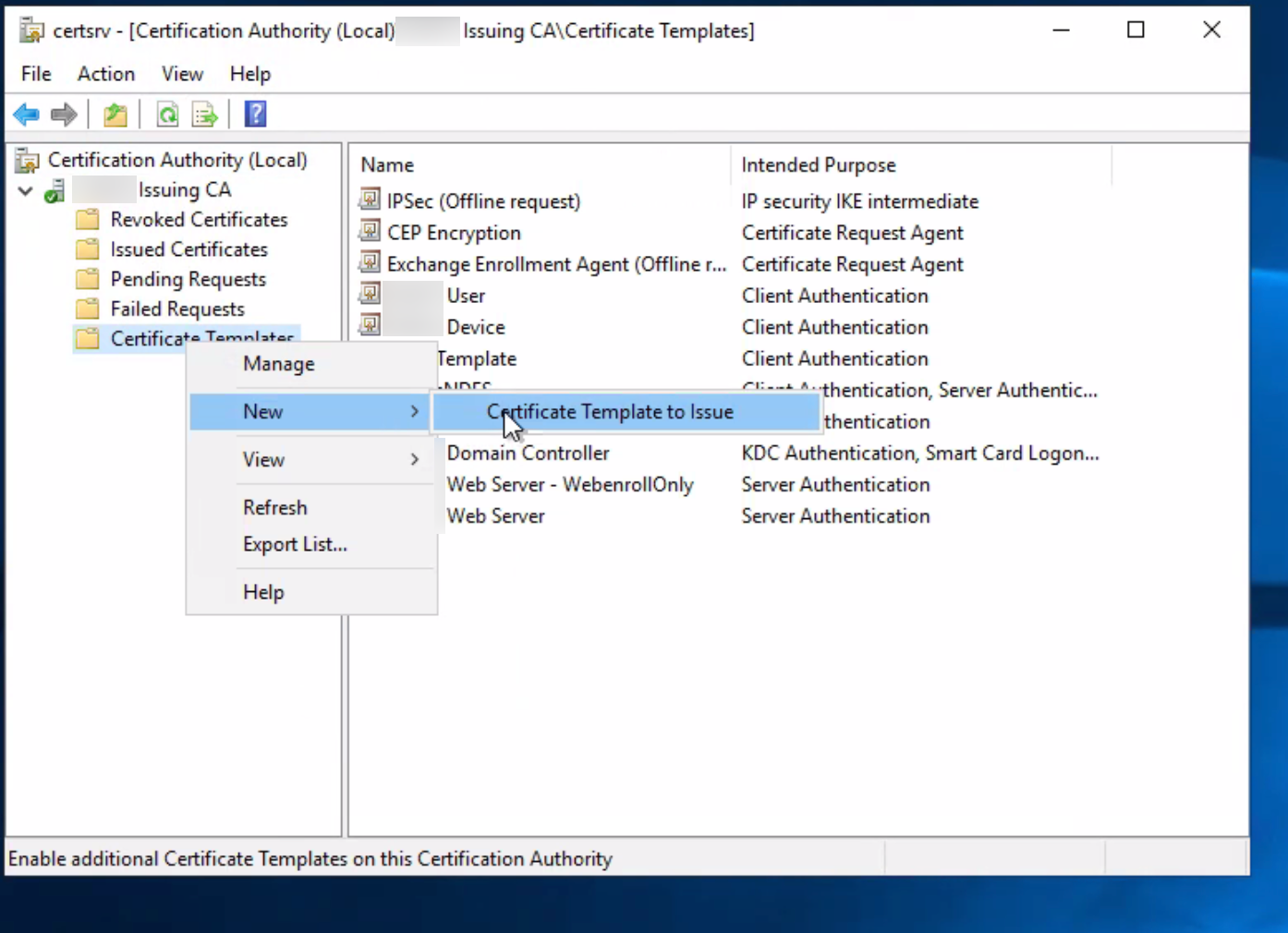
- Under the Certificate Authority (Local) header, right-click Certificate Templates. Then, click New Certificate Template to Issue.
![]() The Enable Certificate Templates dialog appears.
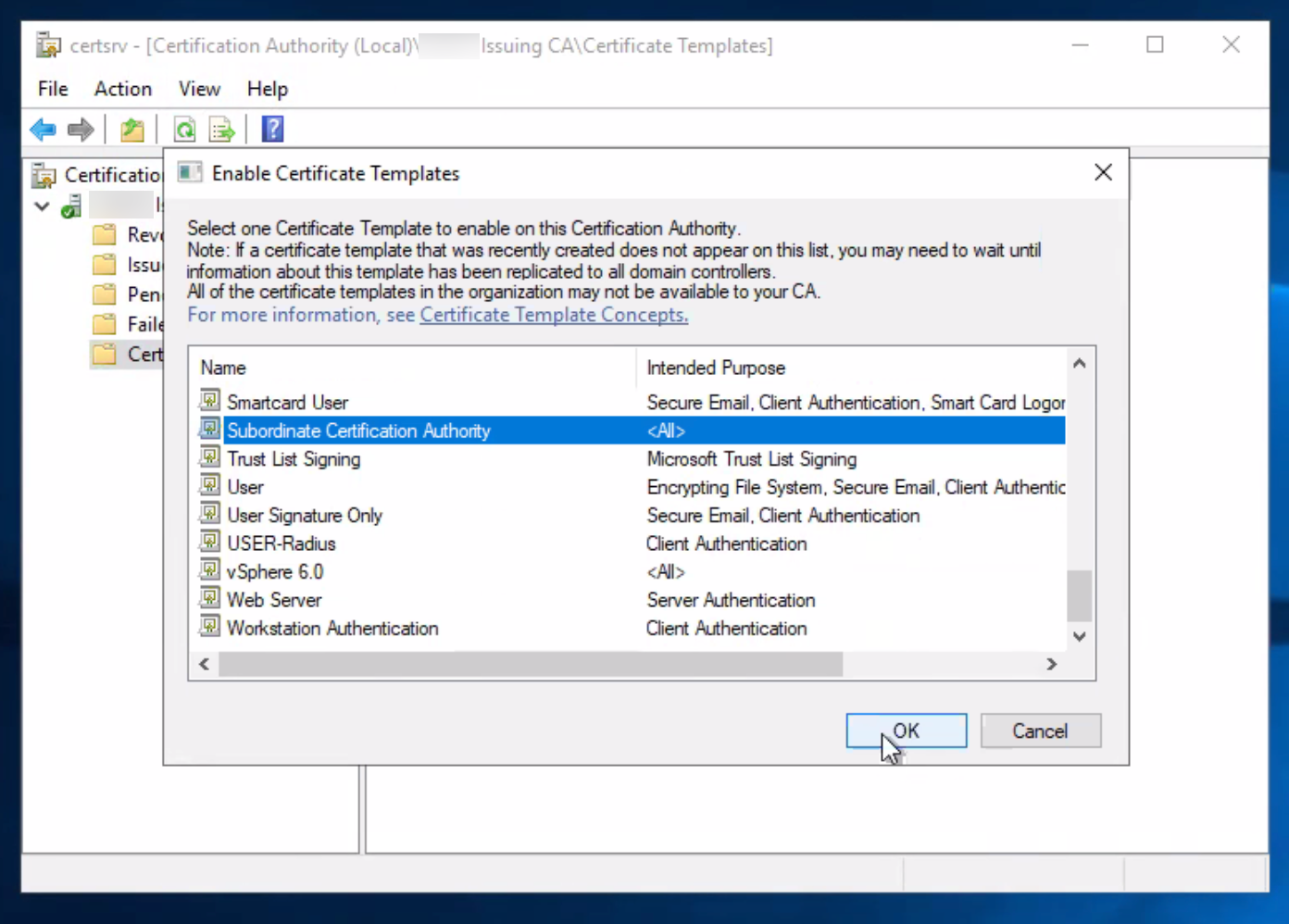
The Enable Certificate Templates dialog appears. - Select Subordinate Certificate Authority from the list of templates, and then click OK.
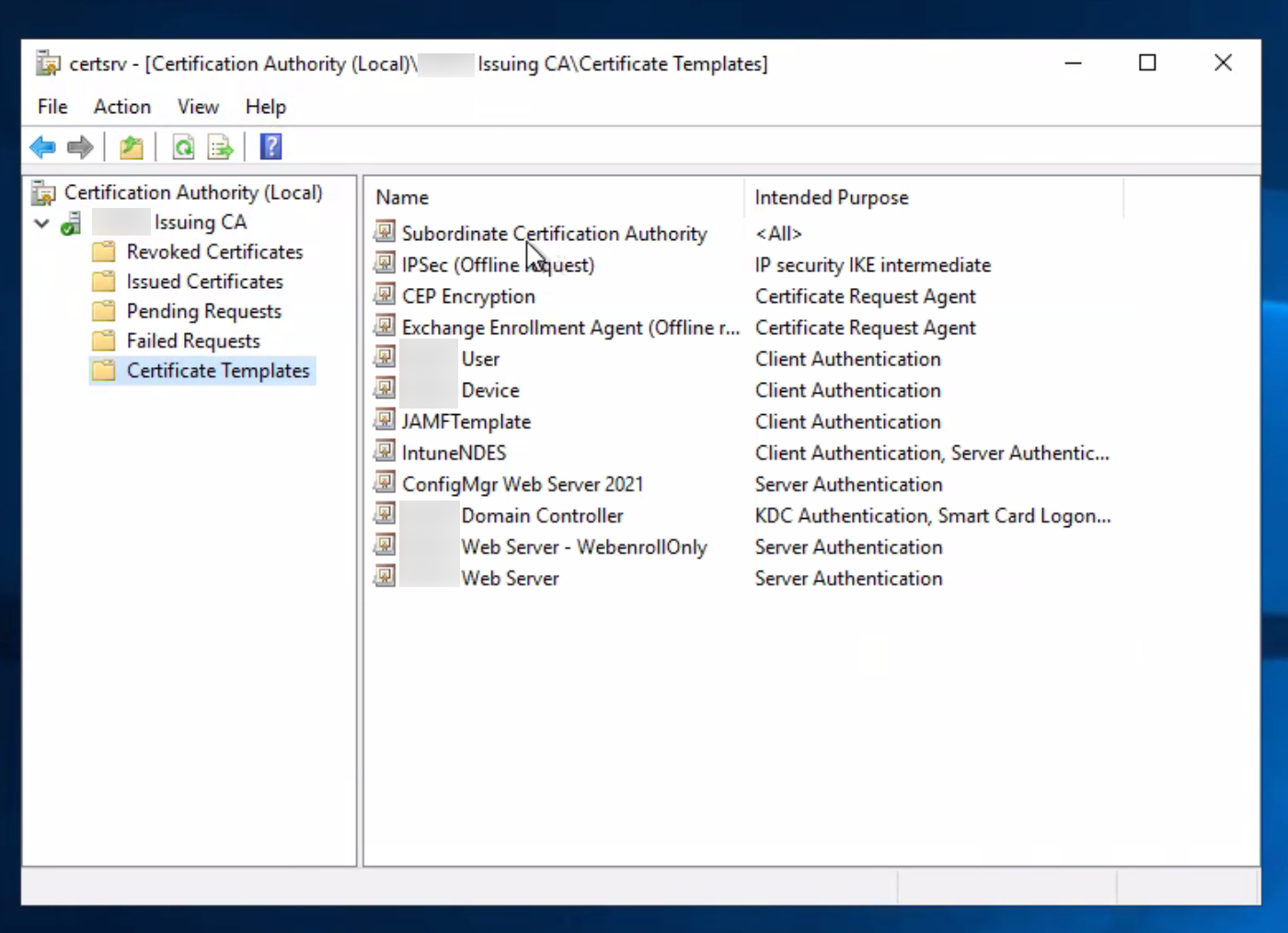
![]() The Subordinate Certificate Authority gets added to the list of certificate templates.
The Subordinate Certificate Authority gets added to the list of certificate templates.![]()
- Import the enterprise CA-signed certificate and subordinate CA certificate (if applicable) onto the NGFW.
- Select DeviceCertificate ManagementCertificates Custom Certificates, and then click Import.An Import Certificate dialog appears.
- Enter the Certificate Name as it appears in the CSR. For successful validation, the name must match the pending certificate name exactly.
- Browse for the Certificate File.
- Click OK.The Custom Certificates tab displays the certificate with a Status of valid and the Key and CA check boxes selected.
- Repeat the import steps for the subordinate CA certificate.
- Designate a Forward Trust Certificate.
- If you don't have a subordinate CA certificate:
- From the Custom Certificates list, select the enterprise CA-signed certificate.The Certificate information dialog opens.
- Select the Forward Trust Certificate option.
- Click OK.
- (Windows or Windows Server users) Mark only the subordinate CA certificate as the Forward Trust certificate , and then click OK.
- Use a self-signed certificate as the Forward Trust certificate:
- The certificate is automatically saved to the Custom Certificates (Device Certificates in PAN-OS 11.2 and earlier) list.
- Designate the certificate as the trusted root CA certificate.
- Select the self-signed certificate from the Custom Certificates list (DeviceCertificate ManagementCertificatesCustom Certificates).The Certificate information dialog opens.
- Select the Trusted Root CA option.
- Click OK.
- Generate a new subordinate CA certificate for each NGFW:
- Select DeviceCertificate ManagementCertificates Custom Certificates, and then click Generate.
- Enter a unique Certificate Name.
- Enter a Common Name. This should be the IP address or FQDN that appears in the certificate. Avoid using spaces in this field.
- For Signed By, select the self-signed root CA certificate.
- Select the Certificate Authority option.This option enables the NGFW to issue the certificate.
- Generate the certificate.
- Repeat for each NGFW.
Distribute the Forward Trust certificate to client system certificate stores.SKIP THIS STEP if you're using an enterprise-CA signed certificate as the Forward Trust certificate and the client systems already have the enterprise CA installed in their local trusted root CA list. (The client systems trust the subordinate CA certificates generated on the NGFW because the enterprise trusted root CA has signed them.)If you don't install the Forward Trust certificate on client systems, users see certificate warnings for each SSL site they visit.- On an NGFW configured as a GlobalProtect portal:This option is supported with Windows and Mac client OS versions, and requires installation of GlobalProtect app 3.0.0 or later on the client systems.
- Select NetworkGlobalProtectPortals, and then select an existing portal configuration or Add a new one.
- Select Agent, and then select an existing agent configuration or Add a new one.
- Add the self-signed trusted root CA certificate to the Trusted Root CA section.After GlobalProtect distributes the trusted root CA certificate to client systems, the client systems trust the NGFW's subordinate CA certificates because the clients trust the root CA certificate.
- Install in Local Root Certificate Store to enable the GlobalProtect portal to automatically distribute and install the certificate in the certificate store on GlobalProtect client systems.
- Click OK twice.
- Without GlobalProtect:
- Export the NGFW trusted root CA certificate so you can import it to client systems. Highlight the certificate, and then Export it in PEM format.Don't select the Export private key checkbox. The private key should remain on the NGFW and not be exported to client systems.
- Import the trusted root CA certificate into the browser Trusted Root CA list on the client systems.When importing, ensure that you add the certificate to the Trusted Root Certification Authorities certificate store. On Windows systems, the default import location is the Personal certificate store. You can also simplify this process by using a centralized deployment option, such as an Active Directory Group Policy Object (GPO).
Configure the Forward Untrust certificate.Use the same Forward Untrust certificate for each NGFW. Clients receive a certificate warning when attempting to access sites with untrusted certificates.- Don't export the Forward Untrust certificate to the certificate trust lists of your network devices.
- Don't install the Forward Untrust certificate on client systems. Installing the Untrust certificate in the Trust List results in devices trusting websites that the NGFW doesn't trust. In addition, users won’t see certificate warnings for untrusted sites, so they may access those sites, which could expose your network to threats.
- Select DeviceCertificate ManagementCertificates Custom Certificates, and then click Generate.Enter a Certificate Name.Enter a Common Name. Leave Signed By blank.Select the Certificate Authority option.Generate the certificate.Designate the certificate as the Forward Untrust certificate.
- Select DeviceCertificate ManagementCertificatesCustom Certificates, and then select the Forward Untrust certificate.The Certificate information dialog opens.
- Select the Forward Untrust Certificate option.
- Click OK.
(Optional) Configure the key size for the SSL Forward Proxy server certificates that the NGFW presents to clients.By default, the NGFW determines the key size to use based on the key size of the destination server certificate.Create a decryption policy rule for SSL Forward Proxy.- Select PoliciesDecryption, add or modify an existing rule, and define traffic to be decrypted.Select Options and:
- For Action, select Decrypt.
- For Type, select SSL Forward Proxy.
- (Optional but a best practice) Configure or select an existing Decryption Profile to block and control various aspects of the decrypted traffic.For example, create a decryption profile or select one that performs certificate checks and blocks weak cipher suites and protocols from allowing questionable traffic on your network.
Click OK.Commit your changes.Choose your next step:- Enable users to opt out of SSL decryption.
- Configure decryption exclusions to disable decryption for certain types of traffic.
- (Advanced WildFire® subscriptions only) Forward decrypted SSL traffic for WildFire analysis.