Network Security
Policy Object: Regions
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Policy Object: Regions
Define regions to apply policy to specified countries or locations. Applying policy based
on region is a great way to control traffic between branch offices.
Enhance your security posture by limiting exposure to potential threats from
high-risk regions, bolster your defense against malicious activities such as
cyberattacks or data breaches, and compliance with regulatory frameworks that mandate
restricted or monitored access to and from specific geographic areas.
In today's interconnected world, you might sometimes face distinct security
challenges that vary based on the regions from which network traffic originates. The
Region policy object provides a fine-grained control
mechanism that aligns security measures with specific geographic regions or
countries.
Use Region to define rules and restrictions based on the
geographic source of traffic, enabling a more tailored approach to network security.
This may include allowing or denying traffic from certain countries, regions, or
continents based on your security requirements and regulatory compliance
obligations.
Region is available as an option when specifying source and
destination for security rules, decryption security rules, and DoS security rules.
You can choose from a standard list of countries or use the region settings described in
this section to define custom regions to include as options for Security rules.
Keep reading to learn how to add geographical regions for applying
policy.
Add a Region
Add a Region (Strata Cloud Manager)
Define regions to apply policy to specified countries or locations. Applying policy
based on region is a great way to control traffic between branch offices.
Regions, along with Addresses and Address Groups allow you to group specific
source or destination addresses that require the same policy enforcement. The
address object can include an IPv4 or IPv6 address (single IP, range, subnet), an IP
wildcard address (IPv4 address/wildcard mask) or the FQDN. Alternatively, a region
can be defined by the latitude and longitude coordinates or you can select a country
and define an IP address or IP range. You can then group a collection of address
objects to create an address group object. You can also use dynamic
address groups to dynamically update IP addresses in environments where
host IP addresses change frequently.
Here, we're going to show you how to use Regions to get better
control over the flow of traffic between your branches. Follow these steps to
specify a geographical region to apply policy to.
- Go to ConfigurationNGFW and Prisma AccessObjectsAddressRegions.Select Add Region to add a new region to apply policy to.Configure the settings in this table:Region SettingsDescriptionNameSelect a name that describes the region. This name appears in the address list when defining security security rules. Typing text into this field to narrow down a standard list of countries for you to choose from.Geo LocationTo specify latitude and longitude, select this option and specify the values (xxx.xxxxxx format). This information is used in the traffic and threat maps for App-Scope.AddressesUsing any of the following formats, specify an IP address, range of IP addresses, or subnet to identify the region:x.x.x.xx.x.x.x-y.y.y.yx.x.x.x/nSave your configuration.
Add a Region (PAN-OS & Panorama)
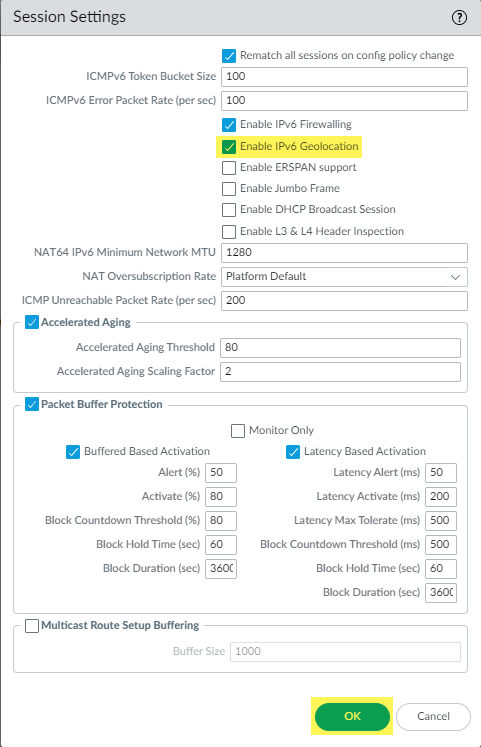
Define regions to apply policy to specified countries or locations. Applying policy based on region is a great way to control traffic between branch offices.Regions, along with Addresses and Address Groups allow you to group specific source or destination addresses that require the same policy enforcement. The address object can include an IPv4 or IPv6 address (single IP, range, subnet), an IP wildcard address (IPv4 address/wildcard mask) or the FQDN. Alternatively, a region can be defined by the latitude and longitude coordinates or you can select a country and define an IP address or IP range. You can then group a collection of address objects to create an address group object. You can also use dynamic address groups to dynamically update IP addresses in environments where host IP addresses change frequently.Here, we're going to show you how to use Regions to get better control over the flow of traffic between your branches. Follow these steps to specify a geographical region to apply policy to.- Go to ObjectsRegions.Select Add to add a new region to apply policy to.Configure the settings in this table:Region SettingsDescriptionNameSelect a name that describes the region. This name appears in the address list when defining security security rules. Typing text into this field to narrow down a standard list of countries for you to choose from.Geo LocationTo specify latitude and longitude, select this option and specify the values (xxx.xxxxxx format). This information is used in the traffic and threat maps for App-Scope.AddressesUsing any of the following formats, specify an IP address, range of IP addresses, or subnet to identify the region:x.x.x.xx.x.x.x-y.y.y.yx.x.x.x/n(IPv6 or Dual Stack Deployments [PAN-OS 12.1 and later]) Enable IPv6 geolocation support on the firewall.The following platforms configured with less than 9GB do not support IPv6 geolocation:
- Hardware NGFWs: PA-410, PA-410R, PA-410R-5G, PA-415, and PA-415-5G
- VM-Series: Software NGFW Credits and VM-Series models with less than 9GB (e.g. VM-100, VM-50, etc)
- Select DeviceSessions and edit the Session Settings.
- Select the Enable IPv6 Geolocation option and click OK to save your settings.You must also Enable IPv6 Firewalling in addition to Enable IPv6 Geolocation.
- Commit your changes.
![]()
Select OK to save your configuration.