Enterprise DLP
Enable Role Based Access
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Enable Role Based Access
Configure role-based access for Enterprise Data Loss Prevention (E-DLP) to control administrative
access.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Enterprise DLP license
|
Configure and assign administrative privileges to control access to Enterprise Data Loss Prevention (E-DLP). Role based access gives you granular control of who has
access to Enterprise DLP and which aspects of Enterprise DLP they have
access to.
(Strata Cloud Manager) Identity and access management for Enterprise DLP is controlled through Common Services. You can assign a
predefined or custom role for All Apps & Services active
on your Strata Cloud Manager tenant, a role for the Enterprise DLP app, or assign a role for both. When a user is
assigned a role for both All Apps & Services and the
Enterprise DLP app, the access privileges
granted by the app-specific role take priority over the access privileges granted by
the All Apps & Services role.
For example, you have both Prisma Access (Managed by Strata Cloud Manager) and Enterprise DLP active on your
tenant. For Prisma Access, you assign a user the View Only
Administrator role. Later, you assign the same user the
DLP Policy Manager for Enterprise DLP. In this
instance, the user has read-only access to Prisma Access (Managed by Strata Cloud Manager) but both read and
write access to the majority of Enterprise DLP for configuration purposes.
(Panorama) Role based access to Enterprise DLP is defined
using a custom Panorama
admin role associated with a Panorama administrator account. The admin role defines the system access
available to the particular admin. If your Panorama administrator already
has an admin role associated with their admin account, you can update it to define
granular access privileges Enterprise DLP. If you want to grant access to only
Enterprise DLP, you can Disable all other UI nodes
except for those describes below.
Strata Cloud Manager
Configure role-based access for Enterprise Data Loss Prevention (E-DLP) on Strata Cloud Manager.
Strata Cloud Manager supports the following roles to grant access privileges for the
Enterprise DLP app specifically. Review the predefined roles and permissions available
on Strata Cloud Manager for details.
|
Predefined Role
|
Privileges
|
|---|---|
|
Data Security Admin
For All Apps & Services
|
Full read and write to Enterprise DLP and Data Security (SaaS API).
This role also includes access to Strata Logging Service logs,
dashboards, create custom dashboards, and download, share, and
schedule reports. Includes read-only access to logs. This role
includes a small subset of privileges included in the Security
Admin role. Assign this role to administrators who manage only
decryption rule configurations.
|
|
DLP Incident Manager
For Enterprise DLP only
|
Read and Write Access — Data Risk dashboard
and settings, Data Asset Explorer,
Incidents, Health & Telemetry, Audit Logs
Read Only Access—Data patterns, profiles, DLP Rules, EDM
data sets, OCR setting, and all DLP settings
|
|
DLP Policy Manager
For Enterprise DLP only
|
Read and Write Access — Data patterns, profiles, DLP
Rules, EDM data sets, OCR setting, health and telemetry, audit
logs, alerts, and all DLP settings
No Access— Incidents and reports
|
|
Multitenant Superuser
For All Apps & Services or Enterprise DLP
|
Full read and write privileges to Enterprise DLP for all
tenants in the particular multitenant hierarchy where the role
is assigned
|
|
Superuser
For All Apps & Services or Enterprise DLP
|
Full read and write privileges for Enterprise DLP
|
|
View Only Administrator
For All Apps & Services or Enterprise DLP
|
Read-only privileges for Enterprise DLP
|
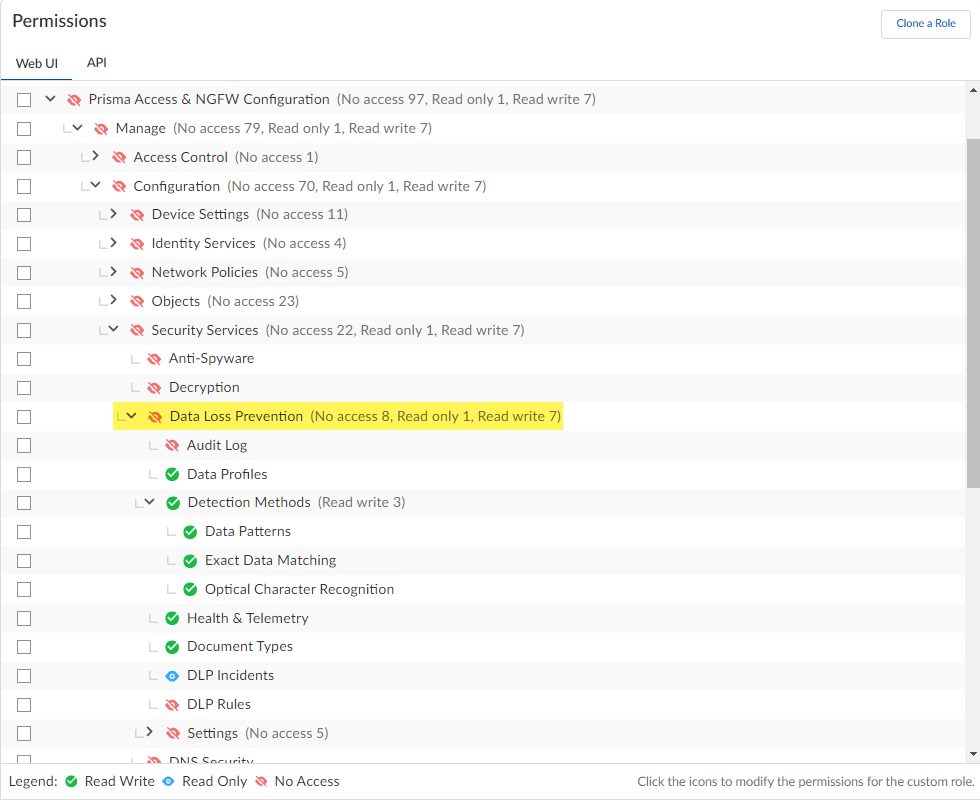
- Log in to Strata Cloud Manager.Use one of the various ways to access Identity & Access.Add Access to your tenant where Enterprise DLP is active.This step is required only if the user for which you’re granting Enterprise DLP access isn’t already registered with the Palo Alto Networks Customer Support Portal (CSP).Select Prisma Access & NGFW ConfigurationManageConfigurationSecurity ServicesData Loss Prevention and configure the custom role.You can use custom roles allow to define which permissions are enforced for your users and allow more granular access control to Enterprise DLP than predefined roles.The access permissions applied to the Data Loss Prevention parent node determines the lowest access privilege you can assign to any of its child nodes. For example, if you want to provide No Access and Read Only to some areas of Enterprise DLP, you must first assign No Access to the Enterprise DLP application.Below is an example of a custom Enterprise DLP role. The custom role is configured with no access privileges to Audit Logs or any of the Enterprise DLP settings. However, read-only access is configured for the Health & Telemetry and DLP Incidents, and full read and write privileges are configured for Data Profiles, all Detection Methods, Document Types, and DLP Rules.
- Enterprise DLP RBAC MappingThe mapping below maps the Enterprise DLP RBAC permissions to the Enterprise DLP configuration in Strata Cloud Manager.Review the list of predefined Enterprise DLP roles to grant a user access to the Data Risk and Data Asset Explorer dashboards.
- Audit Log—ConfigurationData Loss PreventionAudit Log
- Data Profiles—ConfigurationData Loss PreventionData Profiles
- Detection Methods—All detection methods in ConfigurationData Loss PreventionDetection Methods
- Data Patterns—ConfigurationData Loss PreventionDetection MethodsData Patterns
- Exact Data Matching—ConfigurationData Loss PreventionDetection MethodsExact Data Matching
- Optical Character Recognition—ConfigurationData Loss PreventionDetection MethodsOptical Character Recognition
- Health & Telemetry—ConfigurationData Loss PreventionHealth & Telemetry
- Document Types—ConfigurationData Loss PreventionDocument Types
- DLP Incidents—ConfigurationData Loss PreventionDLP Incidents
- DLP Rules—ConfigurationData Loss PreventionDLP Rules
- Settings—All Enterprise DLP settings in ConfigurationData Loss PreventionSettings
- Alerts—ConfigurationData Loss PreventionSettingsAlerts
- API Tokens—N/A; deprecated.
- Data Filtering—N/A; deprecated.
- Data Transfer—ConfigurationData Loss PreventionSettingsData Transfer
- Sensitive Data—ConfigurationData Loss PreventionSettingsSensitive Data
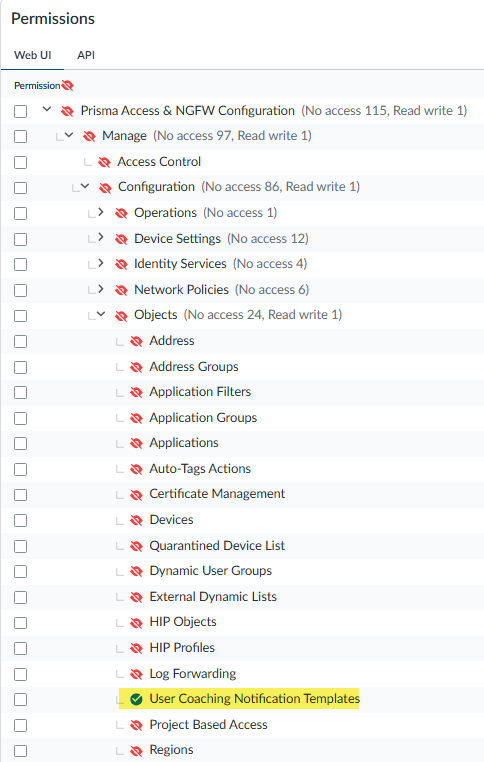
![]() Configure access privileges to allow a data security administrator to create End User Coaching notification templates.End User Coaching enables Enterprise DLP to display notifications to your end users when they generate an Enterprise DLP or Endpoint DLP incident. The end user notification template defines which DLP rules generate a notification and the contents of the notification.Select Prisma Access & NGFW ConfigurationManageObjects and configure the access privileges for User Coaching Notification Templates.
Configure access privileges to allow a data security administrator to create End User Coaching notification templates.End User Coaching enables Enterprise DLP to display notifications to your end users when they generate an Enterprise DLP or Endpoint DLP incident. The end user notification template defines which DLP rules generate a notification and the contents of the notification.Select Prisma Access & NGFW ConfigurationManageObjects and configure the access privileges for User Coaching Notification Templates.![]() Assign role-based access for Enterprise DLP.You don’t need to configuring a tenant role for a user if access to only Enterprise DLP is required.
Assign role-based access for Enterprise DLP.You don’t need to configuring a tenant role for a user if access to only Enterprise DLP is required.- Select User and for the Identity Address, enter the email address for which you granted access in the previous step.For Apps & Services, select Enterprise DLP.
Panorama
Configure role-based access for Enterprise Data Loss Prevention (E-DLP) on your Panorama® management server.Panorama allows you to define 1 of 3 different access privileges for any given UI node:- Enable—Admin has full read and write access.
- Read Only—Admin has read only access. Admin cannot make any configuration changes.
- Disable—Admin has no access to the UI node and it is not displayed in the Panorama web interface when they are logged into Panorama.
- Log in to the Panorama web interface.An administrator with access privileges to create an admin role and commit to Panorama is required.Select PanoramaAdmin Roles and Add a new admin role.If you want to modify an existing admin role, select that admin role instead of creating a new one. Only one admin role profile can be associated with an administrator account.Configure the Enterprise DLP admin role.
- Enter a descriptive Name for the admin role.For the Role, select Panorama.In the Web UI, define the Enterprise DLP access privileges you want to grant the Panorama administrator.
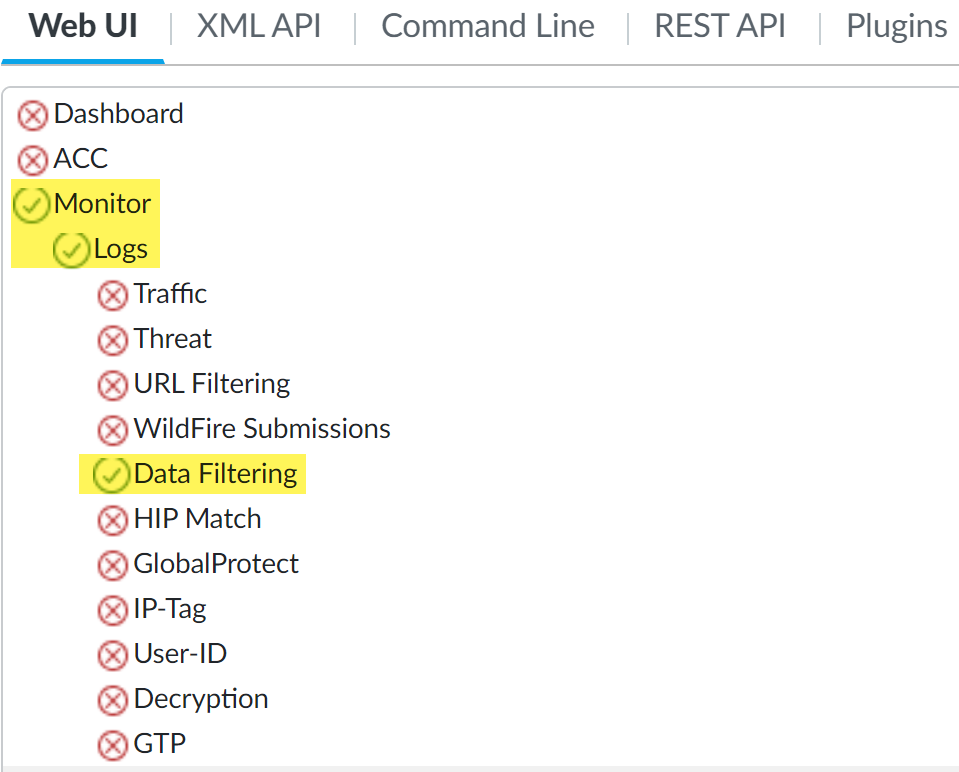
- MonitorLogsData Filtering—Access privileges to data filtering logs. You must Enable or give Read Only access to data filtering logs to allow the administrator to view DLP incidents.
![]()
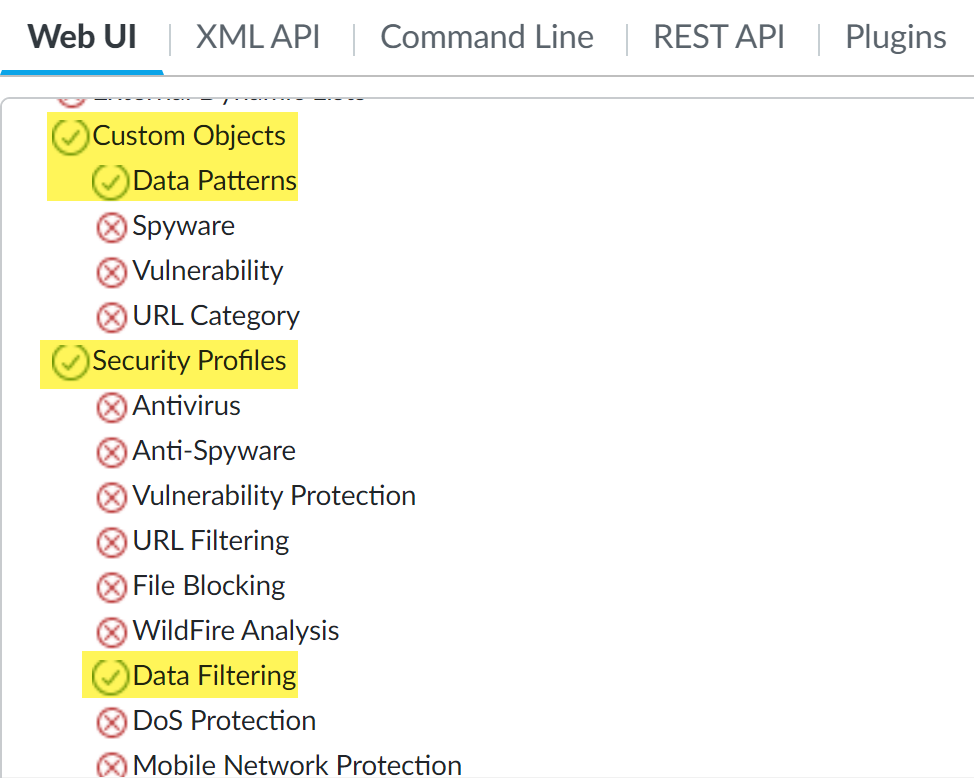
- ObjectsCustom ObjectsData Patterns—Access privileges to Enterprise DLP data patterns.
- ObjectsSecurity ProfilesData Filtering—Access privileges to Enterprise DLP data profiles.
![]()
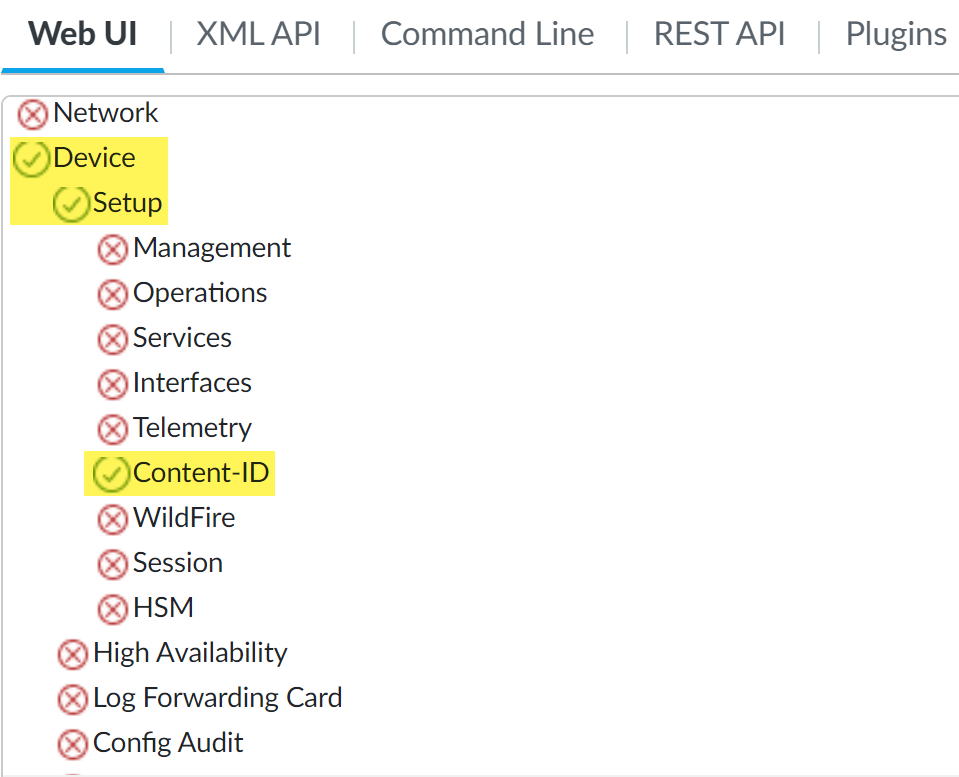
- DeviceSetup—To grant read and write access to the Enterprise DLP data filtering and Cloud Content settings, you must enable read and write access to the Content-ID tab and disable access for the remaining settings.
![]()
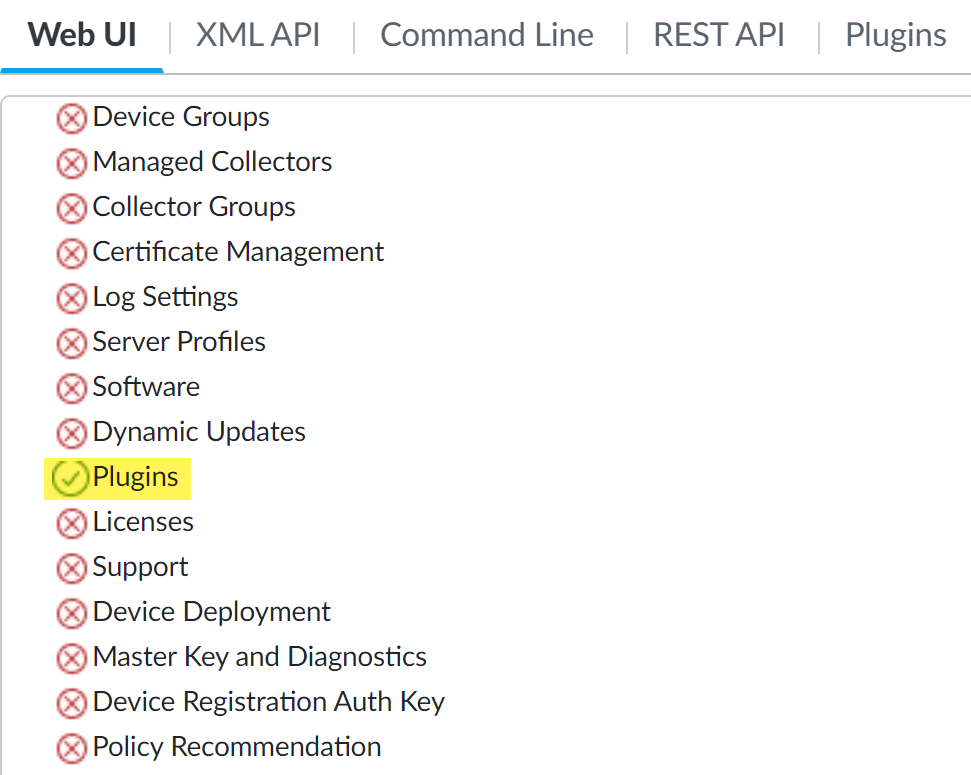
- PanoramaPlugins—Access privileges to upgrade the Enterprise DLP plugin on Panorama and read and write access to the Enterprise DLP snippets settings.If you have other Panorama plugins installed, this will enable access to those configuration nodes in the Panorama tab as well.
![]()
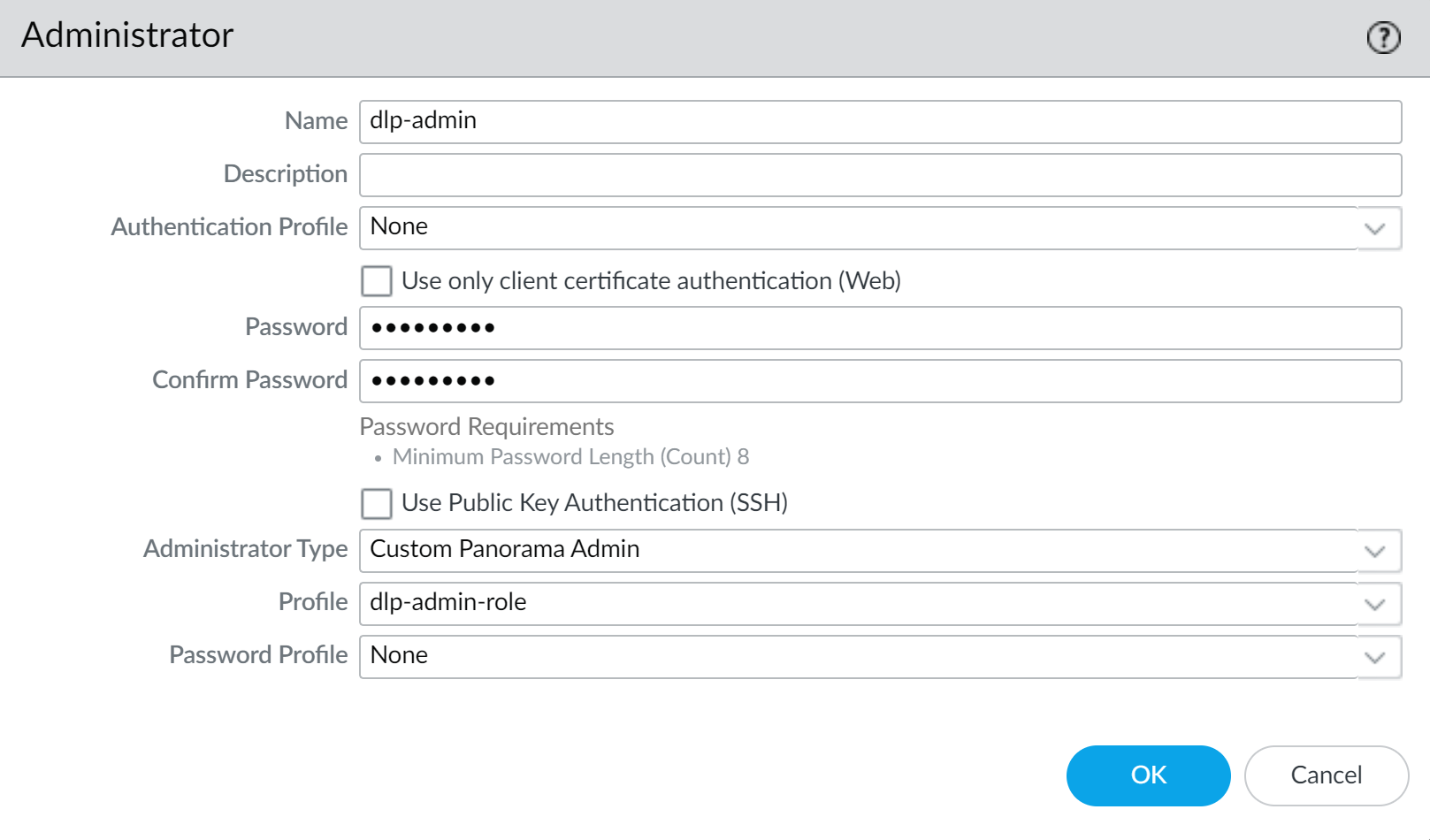
Configure any additional admin role access privileges as needed.For example, you can enable Push All Changes, CommitPanorama, and Tasks to allow the administrator to commit and push Enterprise DLP changes from Panorama to managed firewalls and then view the job status in the Task Manager.Click OK.Create an Enterprise DLP administrator account.Skip this step if you modified an existing admin role already associated with an administrator account.- Select PanoramaAdministrator and Add a new administrator.Enter a descriptive Name for the Enterprise DLP administrator account.Configure the authentication method for the administrator account using one of the following methods.
- Enter the Password and Confirm Password.
- Check (enable) Use Public Key Authentication and click Import Key to import the SSH key.
For the Administrator Type, select Custom Panorama Admin.For the Profile, select the admin role you created in the previous step.Click OK.![]() Select CommitCommit to Panorama and Commit.Verify the Enterprise DLP administrator account is correctly configured.In this example, access to the data filtering logs, data patterns, data profiles, and the plugin tabs are enabled.
Select CommitCommit to Panorama and Commit.Verify the Enterprise DLP administrator account is correctly configured.In this example, access to the data filtering logs, data patterns, data profiles, and the plugin tabs are enabled.- Log in to the Panorama web interface using the Enterprise DLP administrator account you created in the previous step.Select Monitor and confirm only the Data Filtering logs are displayed.Select ObjectsDLP and confirm that Data Filtering Profiles and Data Filtering Patterns are displayed and configurable.Custom Objects and Security Profiles are also displayed but the Enterprise DLP is not able to configure these.Select DeviceSetup and confirm only the Content-ID and DLP tabs are displayed and configurable.