Dynamically Quarantine Infected Guests
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable ZRAM on the VM-Series Firewall
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Install a License API Key
- Use Panorama-Based Software Firewall License Management
-
- Maximum Limits Based on Memory
- Activate Credits
- Create a Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a FW-Flex License
- Transfer Credits
- Renew Your Software NGFW Credit License
- Deactivate License (Software NGFW Credits)
- Create and Apply a Subscription-Only Auth Code
- Migrate to a Flexible VM-Series License
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
-
-
- VM-Series Firewall for NSX-V Deployment Checklist
- Install the VMware NSX Plugin
- Apply Security Policies to the VM-Series Firewall
- Steer Traffic from Guests that are not Running VMware Tools
- Dynamically Quarantine Infected Guests
- Migrate Operations-Centric Configuration to Security-Centric Configuration
- Add a New Host to Your NSX-V Deployment
- Use Case: Shared Compute Infrastructure and Shared Security Policies
- Use Case: Shared Security Policies on Dedicated Compute Infrastructure
- Dynamic Address Groups—Information Relay from NSX-V Manager to Panorama
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
- Use Migration Coordinator to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
-
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
-
- What Components Does the VM-Series Auto Scaling Template for AWS (v2.0) Leverage?
- How Does the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1) Enable Dynamic Scaling?
- Plan the VM-Series Auto Scaling Template for AWS (v2.0 and v2.1)
- Customize the Firewall Template Before Launch (v2.0 and v2.1)
- Launch the VM-Series Auto Scaling Template for AWS (v2.0)
- SQS Messaging Between the Application Template and Firewall Template
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.0)
- Modify Administrative Account and Update Stack (v2.0)
-
- Launch the Firewall Template (v2.1)
- Launch the Application Template (v2.1)
- Create a Custom Amazon Machine Image (v2.1)
- VM-Series Auto Scaling Template Cleanup (v2.1)
- SQS Messaging Between the Application Template and Firewall Template (v2.1)
- Stack Update with VM-Series Auto Scaling Template for AWS (v2.1)
- Modify Administrative Account (v2.1)
- Change Scaling Parameters and CloudWatch Metrics (v2.1)
-
-
- Enable the Use of a SCSI Controller
- Verify PCI-ID for Ordering of Network Interfaces on the VM-Series Firewall
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Enable Azure Application Insights on the VM-Series Firewall
- Set up Active/Passive HA on Azure
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
End-of-Life (EoL)
Dynamically Quarantine Infected Guests
Threat and traffic logs in PAN-OS include
the source or destination universally unique identifier (UUID) of
guest VMs in your NSX-V deployment. This allows the VM-Series for
NSX-V to support the tagging of guest VMs with NSX-V security tags. With
the guest VMs’ UUID now included in the log events, the firewall,
based on the filtered log events, can tag the affected guest VM
via NSX-V Manager API. This allows for automatic location of compromised
VMs in the NSX-V environments. NSX-V can then put all associated
UUIDs under policies to quarantine those VMs from the rest of the
network.
Panorama includes predefined payload formats for
threat and traffic logs in the HTTP Server Profile. These payload
formats correspond to predefined security tags in NSX-V. When a
guest VM is found in the threat or traffic logs, Panorama makes an
API call to NSX-V Manager telling NSX-V Manager to tag the guest
VM with the tag specified in the HTTP Server Profile. When the guest
VM becomes tagged, NSX-V Manager dynamically moves the tagged guest
VM into the quarantine security group, which places the guest VM
into the quarantine dynamic address group.
- Confirm that you have content update version 636 or later installed on Panorama.
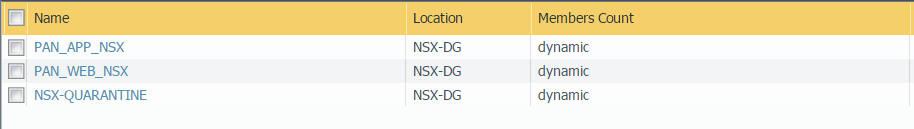
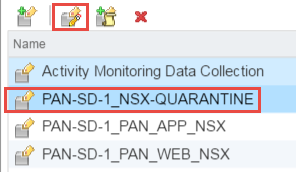
- Create a dynamic address group to be your
quarantine dynamic address group.
![]()
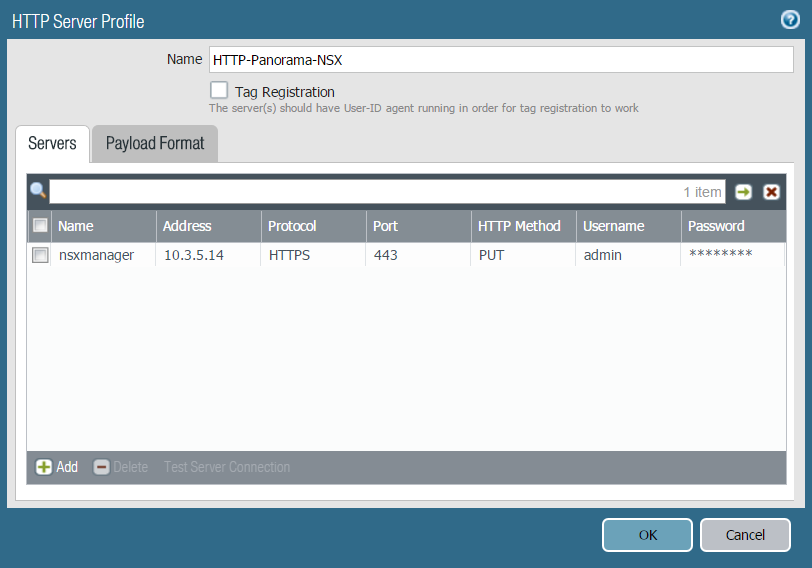
- Create
an HTTP Server Profile to send API calls to NSX-V Manager.
- Select PanoramaServer ProfilesHTTP and Add a new HTTP Server Profile.
- Enter a descriptive Name.
- Select Add to provide the details of NSX-V Manager.
- Enter a Name for NSX-V Manager.
- Enter the IP Address of NSX-V Manager.
- Select the Protocol (HTTP or HTTPS). The default Port is 80 or 443 respectively.
- Select PUT under the HTTP Method column.
- Enter the username and password for NSX-V Manager.
![]()
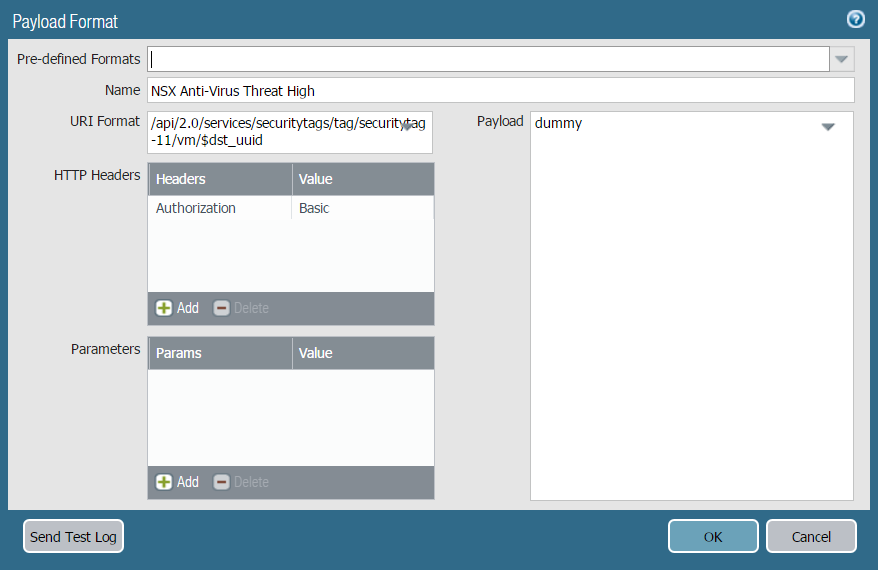
- Select Payload Format and choose
an NSX-V payload format from the Pre-defined Formats drop-down.
This populates the URI Format, HTTP Headers, and Payload fields
with the correct information to send the HTTP API call to NSX-V
Manager. Additionally, the chosen format determines which security
tag NSX-V Manager applies to infected guest VMs. In the example
below, NSX-V Anti-Virus Threat High is selected which corresponds
to the ANTI_VIRUS.VirusFound.threat=high security tag on
NSX-V Manager.
![]()
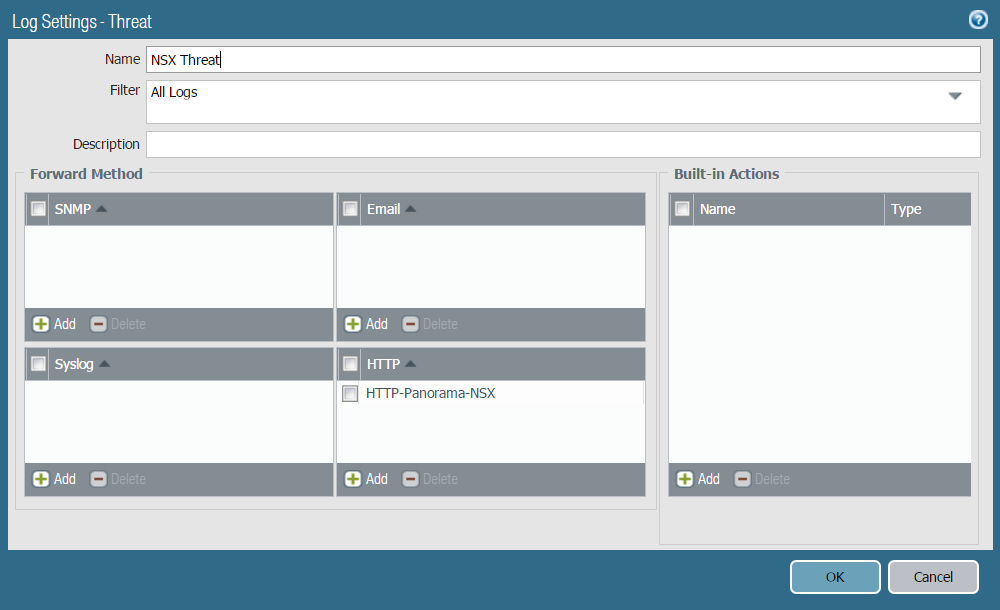
- Define the match criteria for when Panorama will forward
logs to the NSX-V Manager, and attach the HTTP server profile to
use.
- Select PanoramaCollector GroupsCollector Log Forwarding for Threat or Traffic logs.
- Click Traffic or Threat and Add.
- Enter a descriptive name for the new log settings.
- (Optional) Under Filter, you can add filters such as severity to narrow the logs that are forwarded to NSX-V Manager. If All Logs is selected, all threat or traffic logs that meet the criteria set in the HTTP Server profile are sent to NSX-V Manager.
- Click Add under HTTP and select the HTTP Server Profile configured in Step 3.
- Click OK.
![]()
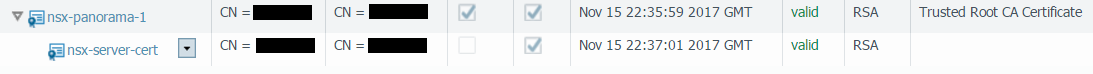
- Configure an NSX-V server certificate for Panorama to
forward logs to NSX-V manager.
- Select PanoramaCertificate ManagementCertificates.
- Create a root CA certificate with CN=IP address of Panorama.
- Create a signed certificate with CN=IP address of NSX-V Manager.
- Export the root CA certificate in PEM format without a private key.
- Export the signed certificate
in PEM format with a private key.
![]()
- Using a tool such as OpenSSL, concatenate the exported
certificates into a single PEM file for upload to NSX-V manager.
Use the following commands in OpenSSL to complete this step.
cat cert_NSX_Root_CA.crt cert_NSX_Signed1.pem > cert_NSX_cert_chain.pem openssl pkcs12 -export -in cert_NSX_cert_chain.pem -out cert_NSX_cert.p12
- Log in to NSX-V Manager and select Manage Appliance SettingsSSL CertificatesUpload PKC#12 Keystore. Click Choose File, locate the p12 file you created in the previous step, and click Import.
- Associate a security group with a security tag in vCenter.
- Log in to vCenter.
- Select Networking & SecurityService ComposerSecurity Groups.
- Select a security group that is counterpart to the
quarantine dynamic address group you created previously and click Edit
Security Group.
![]()
- Select Define dynamic membership and click the + icon.
- Click Add.
- Set the criteria details to Security Tag Contains
and then enter the NSX-V security tag that corresponds to the NSX
payload format you chose in 3. Each of
the predefined NSX-V payload formats corresponds to an NSX-V security
tag. To view the NSX-V security tags in NSX-V, select Networking & SecurityNSX ManagersNSX Manager IPManageSecurity Tags.In this example, NSX Anti-Virus Threat High is used in the HTTP Server Profile so ANTI_VIRUS.VirusFound.threat=high is the NSX-V Security Tag that is used here.
- Click Finish.
![]()
- After the guest VM is cleared for removal from quarantine,
manually remove the NSX-V security tag from the guest VM in NSX-V.
- Log in to vCenter.
- Select VMs and Templates and choose the quarantined guest.
- Select SummarySecurity TagsManage.
- Uncheck the security tag used by the quarantine security group and click OK.
- Refresh the page and the quarantine security will no longer be listed under SummarySecurity Group Membership.
Source and destination UUID fields in threat and traffic logs may be blank after a guest VM is removed from quarantine. This can occur when running NSX-V 6.2.3 or earlier or if NSX-V steering rules do not use the inout direction. You can resolve this by upgrading NSX-V to 6.2.4 or issue an NSX Config-sync under PanoramaVMwareNSX-VService Manager and reboot the PA-VM to resolve this issue.