SaaS Security
View Details for the Most Risky Users
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
View Details for the Most Risky Users
Get visibility into the most risky users on your tenant, based on the number and
severity of threat incidents logged by Behavior Threats.
View the Most Risky Users
The Behavior Threats dashboard displays the most risky users on your tenant. The
most risky users are those with the highest risk scores for your organization.
Investigate these most risky users to determine if they pose a threat to your
organization.
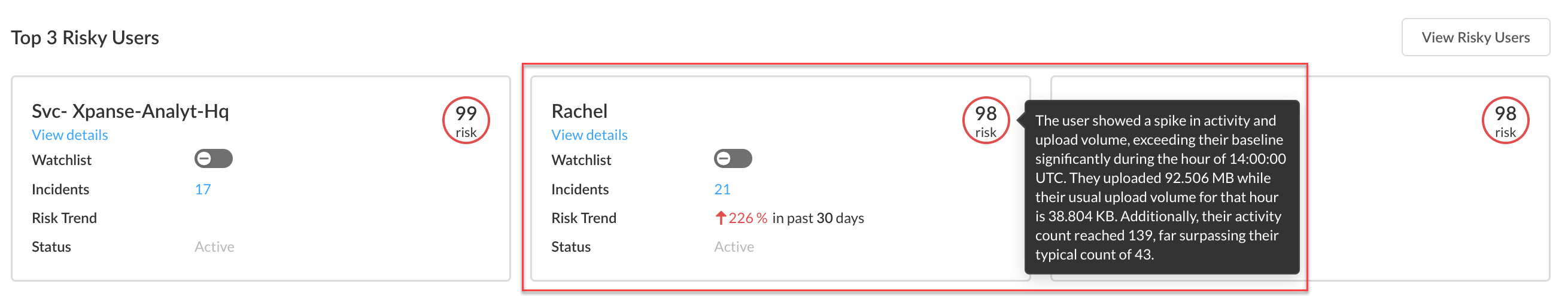
- Log in to Strata Cloud Manager.Select to ConfigurationSaaS SecurityBehavior Threats.View details for each of the Top 3 Risky Users. The details include more information about the threat incidents associated with the user. Investigate any suspicious activity and take action as needed.LLM Powered User Risk SummaryBehavior Threats provides an LLM-powered user risk summary of the top 0.1% of risky users. This summary provides detailed insights into unusual activities, data access patterns, and potential security concerns even when incidents are not generated, enabling security administrators like you to understand and assess user risk more effectively.In the following example, a mouse hover on Rachel's risk score displays the LLM-powered risk summary.
![]() If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can View All Risky Users. View details for these users and take action as needed.
If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can View All Risky Users. View details for these users and take action as needed.View the Most Risky Users for Individual Policies
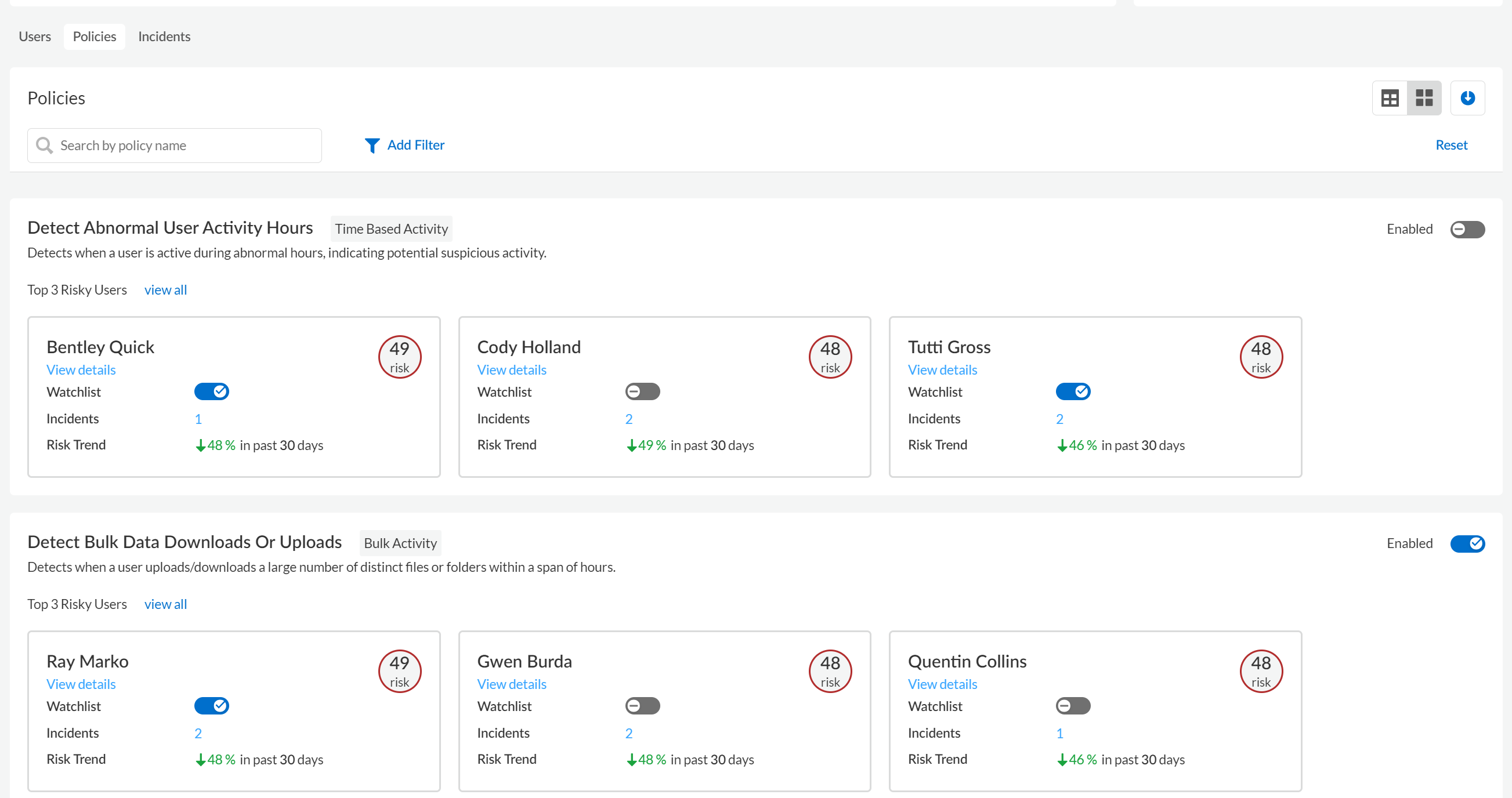
The Policies tab on the Behavior Threats dashboard shows the most risky users for each policy. These risky users are the users with the highest risk scores who are associated with threat incidents for the policy.- Log in to Strata Cloud Manager.Select to ConfigurationSaaS SecurityBehavior ThreatsPolicies.You can display the Policies in a grid view or a list view. By default, the policies display in a grid view.In the Policies grid, locate the policy that you're interested in and view the Top 3 Risky Users for the policy.The displayed information includes the user's risk score and the number of threat incidents associated with the user for the policy.
![]() View details for each of the Top 3 Risky Users. The details include more information about the threat incidents associated with the user. Investigate any suspicious activity and take action as needed.If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can view all risky users for the policy. View details for these users and take action as needed.
View details for each of the Top 3 Risky Users. The details include more information about the threat incidents associated with the user. Investigate any suspicious activity and take action as needed.If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can view all risky users for the policy. View details for these users and take action as needed.