SaaS Security
Tag Discovered SaaS Apps
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Tag Discovered SaaS Apps
Learn how to categorize discovered SaaS apps on SaaS Security Inline as either
trusted or untrusted.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the SaaS Security Inline license:
|
SaaS Security Inline enables you to categorize discovered SaaS apps on Data Security to monitor users of SaaS apps more efficiently and filter SaaS apps.
Tags are local only to Data Security and won’t be applied to your NGFW
or Prisma Access.
There are two ways to apply tags to SaaS apps on SaaS Security Inline:
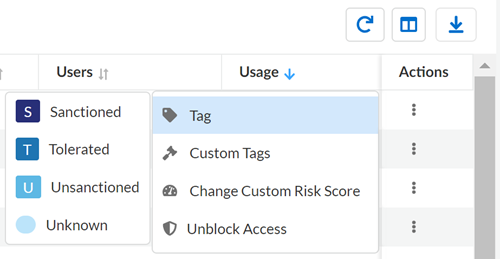
- Default Tags—Apply predefined tags (for example, Unsanctioned or Sanctioned) to reflect whether or not your organization approves of the SaaS app.
- Custom Tags—Create and apply custom tags to group apps with common attributes to reflect how your organization views SaaS apps. For example, create and apply a Communication tag to Gmail.
If you activated the Cloud Identity Engine on your tenant, and
configured directory sync in Cloud Identity Engine for Azure AD or Okta Directory, SaaS Security Inline
can also provide tagging recommendations.
Specifically, SaaS Security Inline uses information from the Cloud Identity Engine to determine if a detected app is an enterprise app accessible through your
identity provider. If the app is an enterprise app, SaaS Security Inline will
recommend that you tag the app as Sanctioned. You can also
open the Tag Recommendations window from the Discovered
Applications view. The Discovered Applications view displays the Tag Recommendations
action only if the Cloud Identity Engine available with the necessary directory syncs
configured.
Apply Default Tags
Based on a SaaS app’s risk factors, use the default
tags available to categorize a SaaS app as sanctioned or unsanctioned so that
you can differentiate unsanctioned SaaS apps from the other SaaS apps that are
being used by employees in your organization.
- Sanctioned—App sanctioned by your organization and being used by employees in your organization.
- Tolerated—App that isn’t trusted like a sanctioned app, but that is allowed to be used by employees until your organization is able to replace it with a more secure app so as not to inhibit the productivity of your users. However, consider creating SaaS policy rule recommendations for tolerated SaaS apps to implement restrictions on specific actions (for example, upload or download).
- Unsanctioned—App unsanctioned by your organization for use by employees in your organization.
- Unknown—Default for SaaS apps that you have not tagged.
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityDiscovered AppsApplications.Apply a default tag:
- (Single App) Locate the SaaS app that you want to tag. In the Actions column, select
Tag and choose the default tag.
![]()
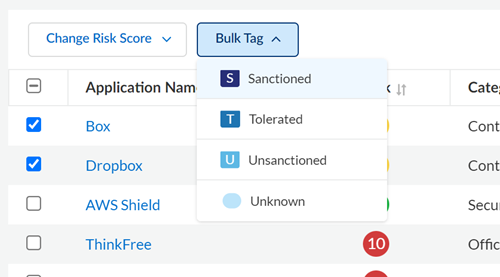
- (Multiple Apps) Locate and select the SaaS apps that you want to bulk tag. Select the
Bulk Tag that you want to apply to the apps.
![]()
Create and Apply Custom Tags
SaaS apps in the Application Dictionary belong to an application category and subcategories to enable filtering, but you cannot modify these attributes. However, you can create your own categorization with custom tags. You can rename or delete a custom tag at any time. When you do, SaaS Security Inline updates or removes the tag from all SaaS apps that use that tag. You can create up to 100 custom tags. Custom tags display alongside default tags.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityDiscovered AppsApplications.Create the custom tag.
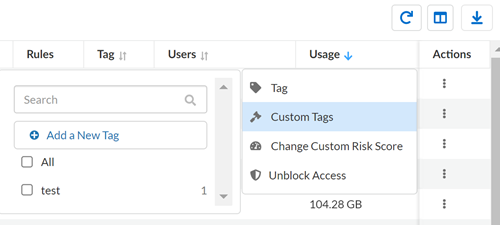
- Locate a SaaS app that you want to tag with a custom tag. In the Actions column, select Custom Tag.Add a New Tag by providing a descriptive name for the tag.
![]() Apply a custom tag.
Apply a custom tag.- Locate a SaaS app that you want to tag with a custom tag.In the Actions column, select Custom Tag, and select the custom tag.